Waystriling.com ads (spam) - Free Instructions
Waystriling.com ads Removal Guide
What is Waystriling.com ads?
Waystriling.com tries to convince people that their browser is blocking video autoplay
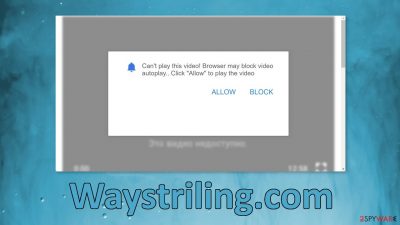
Waystriling.com is a bogus website that tries to trick people into subscribing to push notifications. It is made to look like there is a video available to watch behind the prompt saying that the browser is blocking it. Users are asked to click the “Allow” button which grants permission for the site to start spamming them with pop-up ads.
The other problem is that the creators of the site do not care about user privacy or security so the ads that start showing up can lead to dangerous pages where people can get tricked into providing their personal information, downloading PUPs (potentially unwanted programs),[1] or even malware.
The pop-ups show up at different time intervals depending on the setting set by the owner. They can get very annoying and disturb the browsing experience. Sometimes they show up even when the browser is closed so people might think that they have been infected by a virus.
| NAME | Waystriling.com |
| TYPE | Push notification spam; adware |
| SYMPTOMS | Pop-up ads start appearing in the corner of the screen after people click the “Allow” button |
| DISTRIBUTION | Shady websites, deceptive ads, sneaky redirects, freeware installations |
| DANGERS | Ads and links to sites displayed by the website might be dangerous. Users might suffer from financial losses, disclose their sensitive information to unknown parties or install malware/PUPs on their systems |
| ELIMINATION | Notifications can be disabled via the browser settings; in case you experience more ads and redirects to suspicious sites, you should also get rid of adware by using anti-malware tools |
| FURTHER STEPS | FortectIntego is a maintenance tool that should be used after the removal is complete to get rid of any remaining damage and optimize the system |
It is unusual for people to find pages like Waystriling.com in search results. Oftentimes people get redirected to it by other shady pages. Once it opens, users see this message:
Can't play this video! Browser may block video autoplay.. Click “Allow” to play the video
In reality, there is no video on the page and it is a false message meant to get users to do what the fraudsters want. If you click the “Allow” button, most likely nothing will happen right away. Pop-ups can start showing up after a while, so users do not connect the dots and do not understand the reason behind their appearance.
Keep in mind that all prompts of similar nature are false. Your browser cannot block any video, and you do not have to give anyone any permissions. Besides, you can read about everything you are asked to do. The prompt where you have to click the button says that the page wants to send you push notifications. If you do not want to receive them, find another page that does not force you to click the button.
There are many other messages crooks use to try to get you to click the button. Here are the most common ones:
- Click Allow to verify that you are 18+
- Click Allow to watch the video
- Download is ready. Click Allow to download your file
- Press Allow to verify that you are not a robot
As you can see, many of these messages remind users of standard procedures that are common online, like captcha verification, or having to click “Yes” or “No” to a question if you are an adult if you want to access explicit content. But none of the legitimate pages force you to subscribe to push notifications to be able to use them.
Stop the intrusive pop-ups
Below you will find a manual guide on how to take care of your Chrome browser. Instructions for MS Edge, Chromium, Internet Explorer, Mozilla Firefox, and Safari are available at the end of this post. Because push notifications are subscription-based, you will have to disable them yourself:
Google Chrome (desktop):
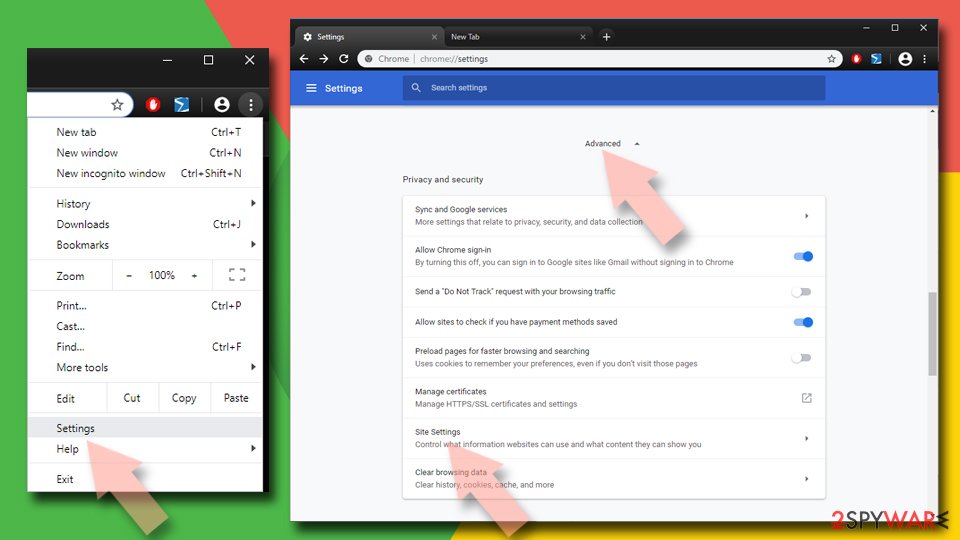
- Open Google Chrome browser and go to Menu > Settings.
- Scroll down and click on Advanced.
- Locate the Privacy and security section and pick Site Settings > Notifications.
![Stop notifications on Chrome PC 1 Stop notifications on Chrome PC 1]()
- Look at the Allow section and look for a suspicious URL.
- Click the three vertical dots next to it and pick Block. This should remove unwanted notifications from Google Chrome.
![Stop notifications on Chrome PC 2 Stop notifications on Chrome PC 2]()
Google Chrome (Android):
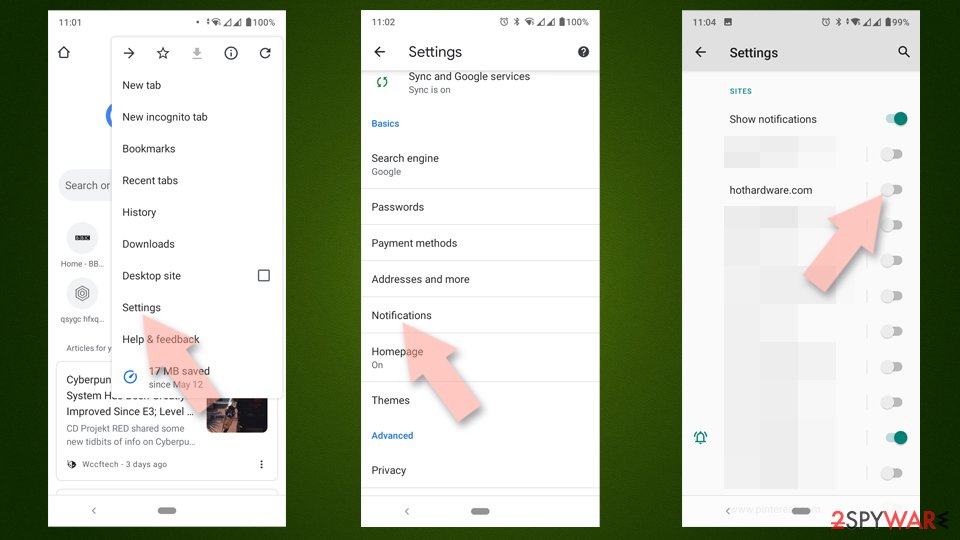
- Open Google Chrome and tap on Settings (three vertical dots).
- Select Notifications.
- Scroll down to Sites section.
- Locate the unwanted URL and toggle the button to the left (Off setting).
![Stop notifications on Chrome Android Stop notifications on Chrome Android]()
Mozilla Firefox:
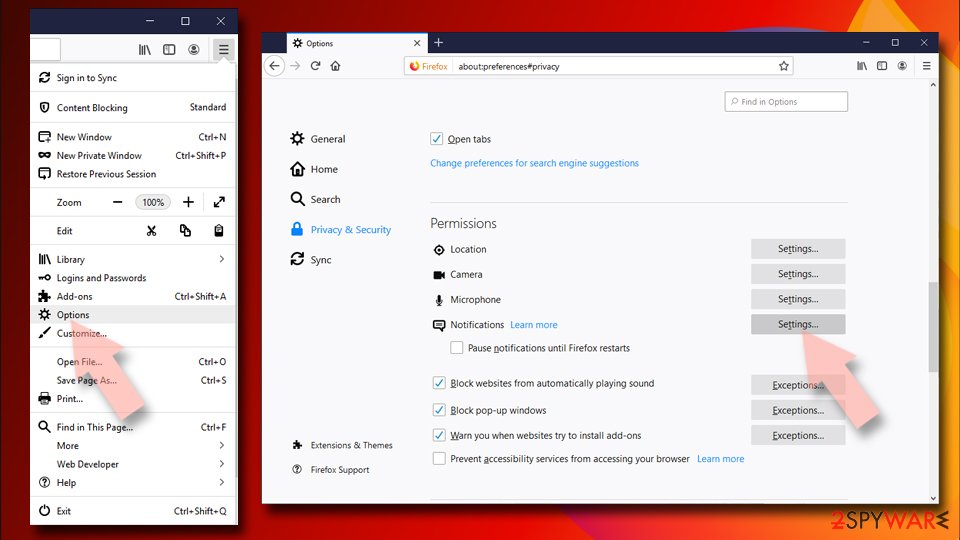
- Open Mozilla Firefox and go to Menu > Options.
- Click on Privacy & Security section.
- Under Permissions, you should be able to see Notifications. Click Settings button next to it.
![Stop notifications on Mozilla Firefox 1 Stop notifications on Mozilla Firefox 1]()
- In the Settings – Notification Permissions window, click on the drop-down menu by the URL in question.
- Select Block and then click on Save Changes. This should remove unwanted notifications from Mozilla Firefox.
![Stop notifications on Mozilla Firefox 2 Stop notifications on Mozilla Firefox 2]()
Safari:
- Click on Safari > Preferences…
- Go to Websites tab and, under General, select Notifications.
- Select the web address in question, click the drop-down menu and select Deny.
![Stop notifications on Safari Stop notifications on Safari]()
MS Edge:
- Open Microsoft Edge, and click the Settings and more button (three horizontal dots) at the top-right of the window.
- Select Settings and then go to Advanced.
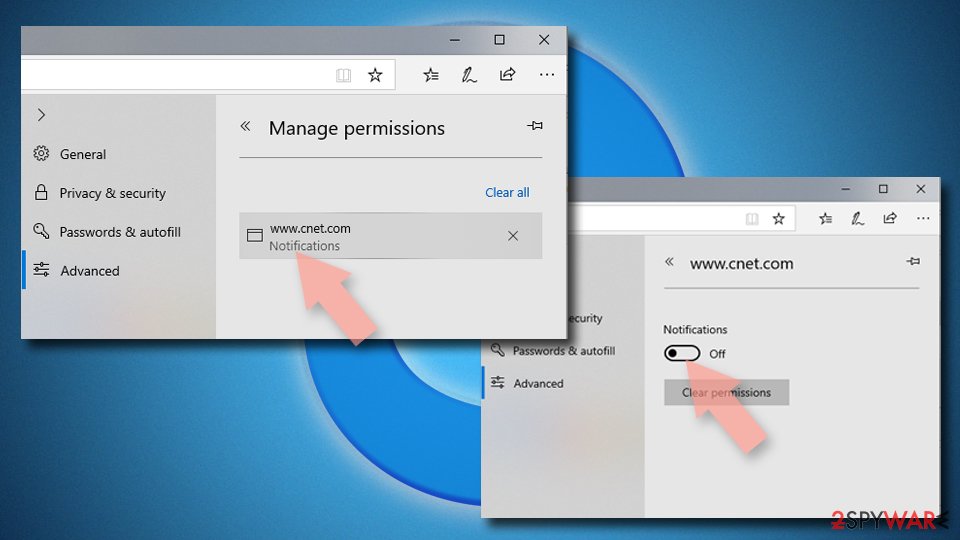
- Under Website permissions, pick Manage permissions and select the URL in question.
- Toggle the switch to the left to turn notifications off on Microsoft Edge.
![Stop notifications on Edge 2 Stop notifications on Edge 2]()
MS Edge (Chromium):
- Open Microsoft Edge, and go to Settings.
- Select Site permissions.
- Go to Notifications on the right.
- Under Allow, you will find the unwanted entry.
- Click on More actions and select Block.
![Stop notifications on Edge Chromium Stop notifications on Edge Chromium]()
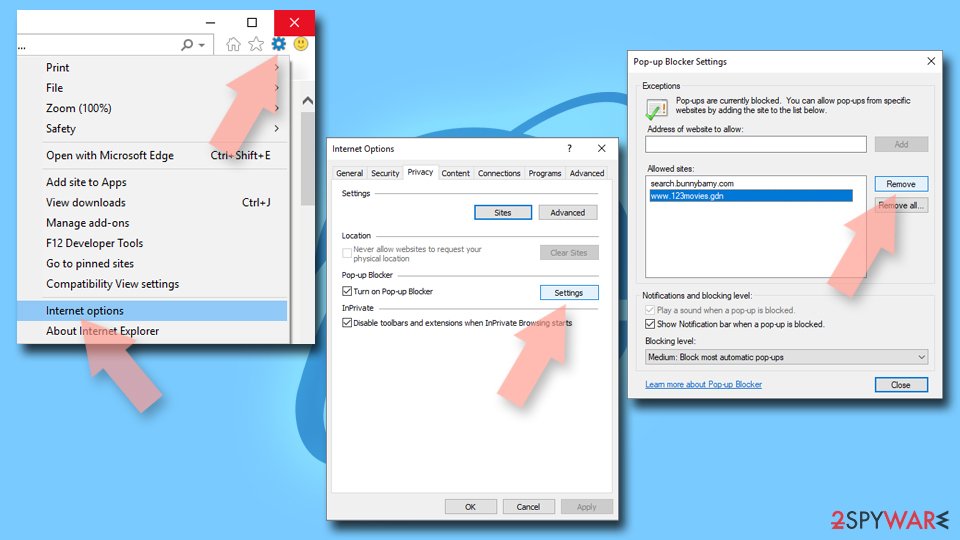
Internet Explorer:
- Open Internet Explorer, and click on the Gear icon at the top-right on the window.
- Select Internet options and go to Privacy tab.
- In the Pop-up Blocker section, click on Settings.
- Locate web address in question under Allowed sites and pick Remove.
![Stop notifications on Internet Explorer Stop notifications on Internet Explorer]()
If blocking ads via browser settings worked for you, we recommend taking care of your browser by clearing cookies[2] and cache. They are used by almost every website to track your activity. Cookies can be sold to advertising networks or hacked by threat actors if the website does not have necessary security protocols in place. Because you were probably browsing through shady sites, this step is essential. We also have an automatic solution for this if you do not want to do it yourself – FortectIntego.
Remove adware from your system
If you notice an increased amount of commercial content like pop-ups, banners, surveys, and others, or you often get redirected to strange websites, you may have adware[3] installed in your system. PUPs are most commonly spread on unofficial sites that distribute freeware.
Because the owners of these pages provide programs for free, they need to make money in other ways, so they include additional programs in the installers that perform tasks in the background. People do not notice that other files were installed because they normally rush through the installation process.
If you want to avoid PUAs, you have to pay attention:
- Always choose “Custom” or “Advanced” installation methods and go through all the steps.
- Read the Terms of Use, and Privacy Policy
- The most important part is checking the file list and seeing if there is anything that you do not need. If you see them, just untick the boxes next to the names.
It is unclear which app could be causing the problems, so we suggest using SpyHunter 5Combo Cleaner or Malwarebytes anti-malware tools that can automatically scan your machine and eliminate it completely. If you know what you are doing and want to do it yourself, here are the guides for Windows and Mac machines:
Windows 10/8:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
Windows 7/XP:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.
![Uninstall from Windows 7/XP Uninstall from Windows 7/XP]()
- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Mac:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)
![Uninstall from Mac 1 Uninstall from Mac 1]()
To entirely remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any suspicious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
![Uninstall from Mac 2 Uninstall from Mac 2]()
How to prevent from getting adware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Potentially unwanted program. Wikipedia. The Free Encyclopedia.
- ^ What are Cookies?. Kaspersky. Home Security Blog.
- ^ Adware. Malwarebytes. Cybersecurity Basics.