Wesker ransomware (Virus Removal Guide) - updated May 2019
Wesker virus Removal Guide
What is Wesker ransomware?
Wesker ransomware is a cryptovirus that adds no extension to encrypted files and demands 0.75 Dash for the decryption tool
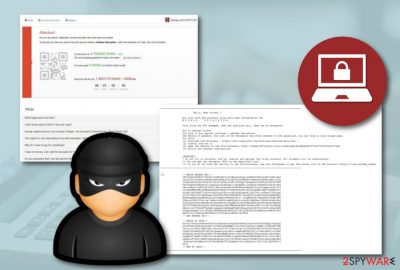
Wesker ransomware is a file locking malware that was first spotted mid-May 2019. The cryptovirus does encrypt data with the help AES cipher but does not append any extensions. Instead, the hex of the file is modified by adding WESKER_ENC mark at the end, which consequently prevents victims from opening pictures, music, video, and other personal data.
As soon as the encryption is complete, Wesker Encrypter ransomware drops a ransom message !!! INSTRUCTION_RNSMW !!!.txt which explains to users what to do next in order to regain access of all the encrypted files. Inside the note, victims are directed to the Tor browser link wesker7b27uikjn3.onion/index.php?6b1AAdbb9d737C529783cf7eec9703dA where cybercriminals demand 0.75 Dash[1] (which is approximately $100), and if the ransom is not paid within a week, the price is doubled.
Interestingly, Albert Wesker[2] is a captain of U.S. police team STARS from Capcom's Resident Evil series and is one of the main characters. Wesker Encrypter ransomware is not currently decryptable, although we provide alternative recovery methods at the end of this article.
| Name | Wesker |
|---|---|
| Type | Ransomware |
| Category | Malware |
| First spotted | At the beginning of May 2019 |
| Appendix | No extension is added to locked files |
| Cipher | AES |
| Ransom note | !!! INSTRUCTION_RNSMW !!! |
| Price | 0.75 Dash (~$100) |
| Target | English speakers |
| Distribution | Email spam and infectious attachments |
| Removal | FortectIntego can find malicious objects |
Wesker ransomware is another dangerous ransom-demanding infection that was first discovered at the start of May this year. Its operating principle is the same – to encrypt files and demand money. However, things such as a unique ransom price and no identifiable appendix make the ransomware different from others of its kind.
There is a big variety of documents and files that can be touched and blocked by Wesker Encrypter ransomware. These components include Microsoft Word documents, Excel data, PowerPoint presentations, audio and video files, archives, etc. Once the data is locked, users are provided with this type of ransom-demanding message:
the Hello, dear friend Eツ
the All your work and personal files is have Been encrypted by the
the W R. The Esker ENCRYPTE
Your files is damaged are the NOT, for They are modified only. They can be decrypted.
How to decrypt files?
You have to buy special software – “Wesker Decryptor”.
The method of payment of the decryptor
For this:
[1] Download Tor-browser (https://www.torproject.org/download/download-easy.html)
[2] Install and run it
[3] Open the website in the Tor-browser “: Http://wesker7b27uikjn3.onion/index.php?6b1AAdbb9d737C529783cf7eec9703dA
[4] Follow the further instructions.
IMPORTANT:
* Do not try to reinstall the OS, restore and decrypt the files yourself. All attempts will be unsuccessful.
** You can get the decryptor ONLY on the specified link.
*** If you don’t have the ability to use the Tor-browser, use the Telegram to get the actual list of web mirrors: https://t.me/tor2web_wesker
_________________________________________________
— BEGIN WESKER KEY– –
3EfCC66625B0B3C77Ed0d1135BE86B00zf79Fme9lOEqwb 5VXmSPV95FnuZZHY0 + + PWnldmJ
*** Bei CMkTFlvFj8Nw4 +
— the END Wesker the KEY —
— — the BEGIN the PC the DATA
dC504376F3a09e99a8e60C951ad9baab3u + RqddfDoA8khQ7kuYavaKvTE *** 2Q6PUa0lCm9 / a
— the END the PC the DATA —
_________________________________________________
Wesker ransomware might include a big variety of damaging features that might not be recognized from the first view. However, these threats can not only encrypt targeted files but they also might inject other infections such as trojans or spyware into the computer system. This will just harden the elimination process.
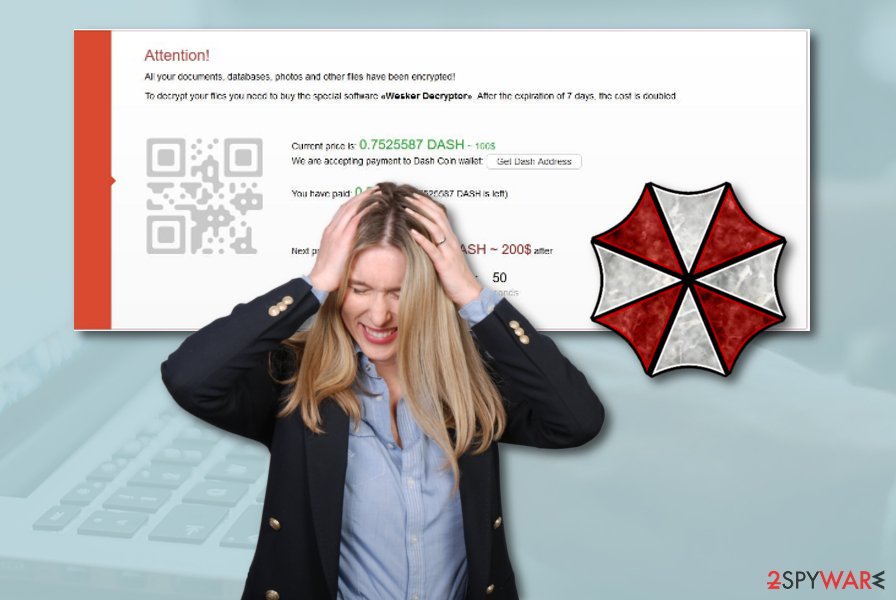
Nevertheless, this cyber threat might be capable of eliminating Shadow Volume Copies of encrypted data to prevent users from trying to unblock their data. You need to immediately remove Wesker Encrypter ransomware from the infected computer system without postponing this process, otherwise, you will supposedly have to deal with unpleasant consequences.
Wesker ransomware removal is a very responsible thing to carry out so it should not be done on your own. We recommend downloading and installing a reputable computer tool such as FortectIntego to scan the entire system and find all possible malware traces. Keep in mind that all infection sources need to be terminated, otherwise, the ransomware will return within the next computer reboot.
Distribution sources of ransomware cyber threats
According to cybersecurity experts from Virusai.lt,[3] ransomware infections can reach various operating systems, however, the most infected one is Windows. As more users have Windows computers, criminals mostly target this kind of OS. Ransomware infections are installed on the targeted machines by launching infectious executables.
These infected files come attached to spam email messages.[4] We recommend all users to stay careful and scan all received attachments with antivirus protection. If you do that, you will be warned about possible threats before opening the rogue message or file. Moreover, ransomware-related payload comes injected in suspicious hyperlinks that can be provided in the email message itself.
Last but not least, there is a big variety of unsafe websites lurking out in the cybersphere. Pages such as peer-to-peer ones often lack protection and are unsafe to visit. By clicking on them or downloading content that is posted there, you might accidentally start the installation of a ransomware infection or other type of malware.

Wesker ransomware virus needs to be terminated from all system locations permanently
If you have ever spotted activities on your computer that relate to Wesker Encrypter ransomware, you should take quick actions without any hesitation. Using anti-malware programs, for example, FortectIntego, SpyHunter 5Combo Cleaner, or Malwarebytes is necessary as these tools will search for malware-laden objects and show where there are located in so you could terminate the infection properly.
Manual Wesker ransomware removal is not a possibility in this case. Cyber threats such as this need to be taken care of safely, otherwise, even more damage can be caused to the computer system. However, you can proceed with some computer rebooting steps that are shown below this article and created to help you.
Once you remove Wesker virus, check our below-provides data recovery steps some of which might appear to be very helpful if you take care of each step exactly as shown in the helping guide. Moreover, taking care of your future data is also a necessity. What you can do is store all important documents on remote servers or USB drives.
Getting rid of Wesker virus. Follow these steps
Manual removal using Safe Mode
Activating the Safe Mode with Networking feature might help you to disable the activity of Wesker ransomware virus and bring your system back to its previous state. Follow these steps to enable the function:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Wesker using System Restore
Use System Restore to deactivate the serious infection on your Windows computer system by following the below-given instructing steps:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Wesker. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Wesker from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Wesker, you can use several methods to restore them:
Try using Data Recovery Pro to restore some of your files:
Use this software if you are likely to recover some of your documents that have been locked or corrupted by the dangerous computer infection.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Wesker ransomware;
- Restore them.
Windows Previous Versions feature might allow you to recover some data:
Try using this method if you have some files that were encrypted. However, note that it will be successful only if you have enabled the System Restore function in the past.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Shadow Explorer tool might be successful in data restoring purposes:
Use this tool to bring back some files if their Shadow Volume Copies were not damaged or deleted by Wesker ransomware virus.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
No official Wesker ransomware decryption tool has been released yet.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Wesker and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ What is Dash?. We Use Coins.
- ^ Albert Wesker. Wikipedia. The free encyclopedia.
- ^ Virusai.lt. Virusai. Spyware and security news.
- ^ Margaret Rouse. Email Spam. Search Security. Tech Target.





















