Win32/Exmann.A (virus) - Free Instructions
Win32/Exmann.A Removal Guide
What is Win32/Exmann.A?
Win32/Exmann.A is the trojan detection name linked with a malicious tool that can take control of the machine
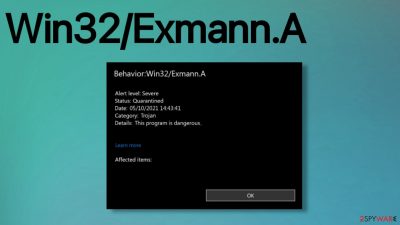
Win32/Exmann.A and other silent malware like trojans, keyloggers, worms can be sued to earn profit for the malicious actor. Dangerous programs like this can obtain credit card information, online account credentials, logins, gather other valuable information. Worms[1] and other threats that manage to get dropped on the system silently can launch various actions and programs that run only in the background but affect the performance and security of the system significantly.
The particular threat is reported[2] as one of many threat detections involved in the attacks of Microfost Exchange Servers. In such attacks, flaws and security vulnerabilities get used to gain access to particular servers and enable access to accounts, data on the machine, install other malware, trigger additional damage.
This detection can appear in your AV solution reports and indicate that there are some associated files or programs. You shouldn't panic if you see any detection name of the threat that is listed as a trojan, exploit, or malware. These are heuristic names, and not every time these reports are on actual infection found on the machine.
You can encounter various names listed on that detection results, false positives, as well as these threats like Trojan:Win32/Mamson!MSR,Trojan Win32/Conteban.B!ml,Trojan.Win32.Cometer.gen, Trojan:Win32/Dex@hot, are pretty common. So pay attention to the performance of the PC too. The best reaction to any warning or the detection alert of the virus – scan with the anti-malware tool. It is best to run the elimination with the solution that reported the detection and follow up with another tool that can double-check or even find the malicious intruder hidden somewhere else on the system.
| Name | Win32/Exmann.A |
|---|---|
| Type | Trojan, malware |
| Issues | The infection creates speed and performance problems, crashes and errors can indicate that the infection is present on the machine, suspicious activities, direct background processes |
| Distribution | P2p sharing platforms, torrent sites, pirating services include files with malware. Also, email attachments and links in messages can lead to infections like this |
| Damage | Trojans can be used to spread other infections and gather data from the user directly. There are many uses to such malware because actors can have different goals |
| Elimination | Anti-malware tools are needed for the proper system cleaning, so you can run SpyHunter 5Combo Cleaner or Malwarebytes and remove the trojan |
| Repair | Silent infections can trigger issues with performance and cause serious damage. Make sure to run a tool like FortectIntego to find and repair affected system data |
Behavior:Win32/Exmann.C is the infection that can be used to act as a vector. It is a common criminal activity that various actors can use to spread other viruses like ransomware. The way this infection is spread allows the code to get activated and hidden in various parts of the system. These activities allow the trojan to run without causing particular symptoms.
Experts[3] not that users often cannot see the issues that this threat causes and remain clueless. In the meantime, malware can run all the needed processes, mine cryptocurrency, infect the machine and leave the machine. Sometimes leftovers of the virus can trigger these warnings and alerts from AV tools, so you need to clear those pieces thoroughly.
Messages with the heuristic names of detections like Win32/Exmann.A can be scary, but in many cases, these detections are not indicating the existing threat that is active. However, anti-malware tools are the ones that can find and remove such infections thoroughly for you, so cleaning the machine is not a bad idea, especially, when trojans can be accompanied by additional threats.
Major issues related to trojan and malware infections
Vulnerabilities and security flaws get exploited very often, and using these instances criminals can obtain data from the machine directly or released data-gathering code to steal information that can be useful later on. These threats can often be set to install other malware besides the Win32/Exmann.A because users cannot notice the infiltration that way.
The behavior of these related files can trigger the detection and AV tools aim to catch the infection or potentially malicious files. If you downloaded anything recently or received the email from an unknown source it is possible that trojan is present. However, the common symptoms of the cyber infection may not appear at all:
- the slowness of the machine;
- performance issues;
- background processes;
- ransom apps installed;
- other programs running.
You can also become a victim of Win32/Exmann.A when it is used in exploit campaigns and other malicious attacks. Attackers get access to the system and can launch anything on the machine or the network. Once the code is active, malware creators can ensure persistence on servers they have already compromised or obtain user credentials and steal data during these attacks.
Malware can only be set to compromise networks, so access to the system is given to the additional remote attackers. Trojans are universal and silent, so even the patches or mitigations are failing to protect from an infection like this. Ransomware attacks pose some of the biggest security risks for organizations today, and attackers behind these devastating acts have been quick to take advantage of vulnerabilities.
Successfully exploiting this flaw gives them access not only to your data but also control over any machine in use through human-operated ransomware campaigns. Even if the trojan that users get is more focused on system damage and issues caused to performance, you need to remove it as soon as possible.
Often it is too late when the Behavior:Win32/Exmann virus already disabled tools and security features. You can run SpyHunter 5Combo Cleaner or Malwarebytes and remove the infection. If malware is not letting you use antivirus in normal mode, access Safe Mode and perform a full system scan from there.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
![Windows XP/7 Windows XP/7]()
Windows 10 / Windows 8
- Right-click on Start button and select Settings.
- Scroll down to pick Update & Security.
![Update & Security Update & Security]()
- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.
![Recovery Recovery]()
- Select Troubleshoot.
![Choose an option Choose an option]()
- Go to Advanced options.
![Advanced options Advanced options]()
- Select Startup Settings.
- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.
Avoiding malicious content can help with malware-fighting later on
Exploit:Script/Exmann can be delivered via phishing attacks and similar campaigns where the email is used to spread malicious files with the direct code for the infection. Phishing is a type of cyber attack where the mail looks legitimate and tricks people into believing it to be something they want or need.
Phished emails may come in many different forms, such as messages asking for bank account information which can then result in theft if given away without hesitation by clicking on links. It would be hard to find someone who has never been fooled by a phishing email. It can result in a PUP infiltration direct to the scam site. However, there are major differences between a PUP and a Trojan.
The attackers disguise Exploit:Win32/Exmann.A!MTB files in emails with claims that may show criminals as trustworthy individuals or companies and try their best not just to impersonate them. This type of cyber attack dates all back into the 1990s when hackers first started using this technique in order to lure unsuspecting victims. It gets more advanced and dangerous these days.
It is possible to avoid such instances and direct malware installations, so you do not need to remove the malware yourself. It is related to anti-malware tool detections and security tools like SpyHunter 5Combo Cleaner or Malwarebytes that can indicate insecure file. Even though you cannot notice the direct drop of the code for Exploit:Win32/Exmann.A!MTB virus, you can avoid the security issue overall. Pay attention to particular details related to subject lines and senders, so you can be more suspicious and avoid opening links, downloading files from such messages.
Getting rid of Win32/Exmann.A. Follow these steps
Repair damaged system components
Once a computer is infected with malware, its system is changed to operate differently. For example, an infection can alter the Windows registry database, damage vital bootup and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by malware, antivirus software is not capable of doing anything about it, leaving it just the way it is. Consequently, users might experience performance, stability, and usability issues, to the point where a full Windows reinstall is required.
Therefore, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it is also capable of removing malware that has already broken into the system thanks to several engines used by the program. Besides, the application is also capable of fixing various Windows-related issues that are not caused by malware infections, for example, Blue Screen errors, freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

By employing FortectIntego, you would not have to worry about future computer issues, as most of them could be fixed quickly by performing a full system scan at any time. Most importantly, you could avoid the tedious process of Windows reinstallation in case things go very wrong due to one reason or another.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Win32/Exmann.A and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting malware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Computer worm. Wikipedia. The free encyclopedia.
- ^ Behavior:Win32/Exmann.A report. Microsoft. Security intelligence blog.
- ^ Semvirus. Semvirus. Spyware news.









