Z61yt ransomware (virus) - Recovery Instructions Included
Z61yt virus Removal Guide
What is Z61yt ransomware?
Z61yt ransomware is a file-locking virus that holds personal files hostage until a ransom is paid
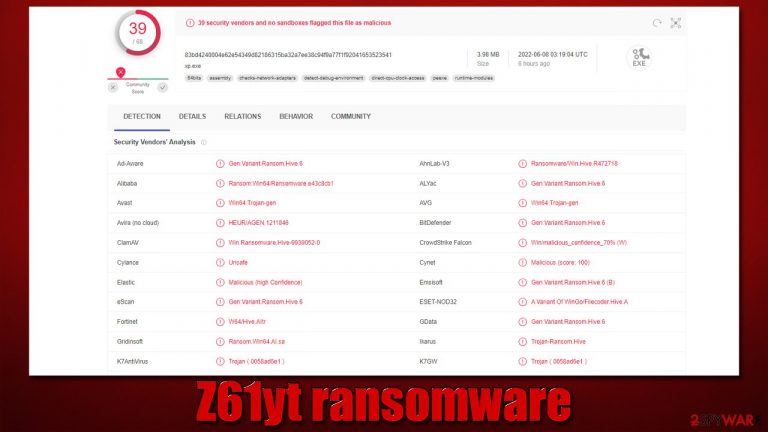
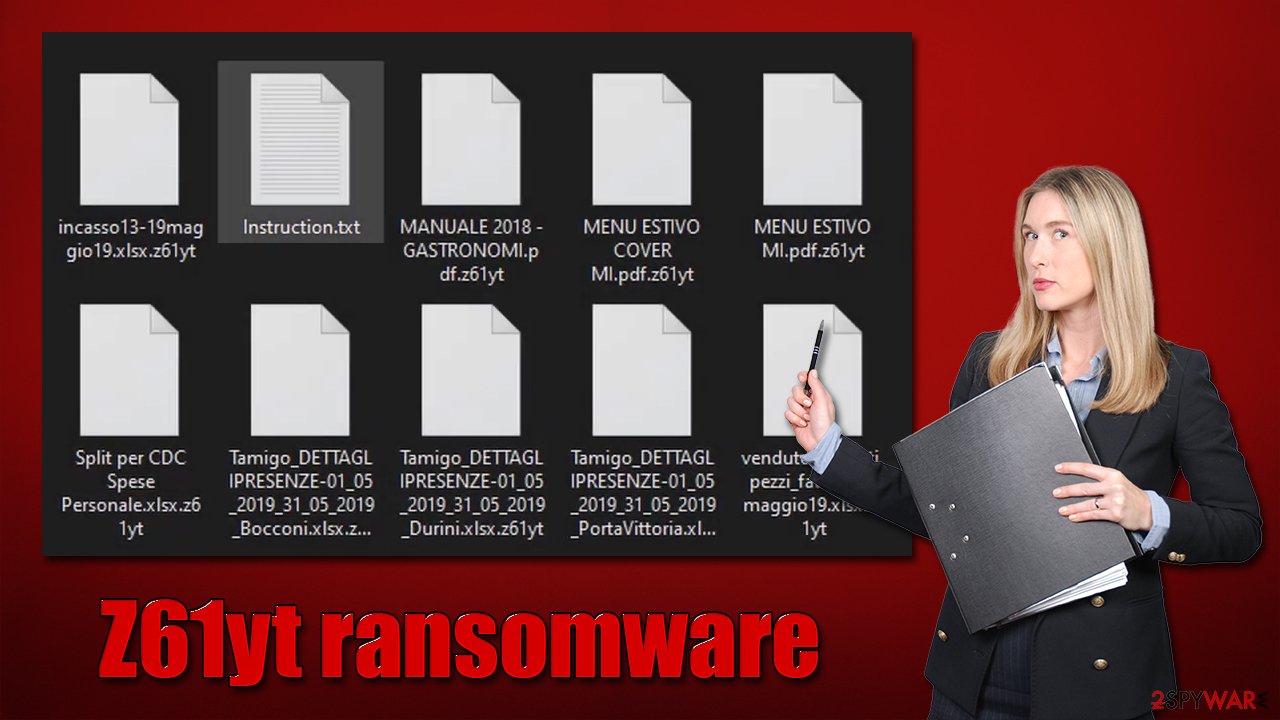
Z61yt ransomware is a malicious Windows program written in the Go programming language. The main goal of the attack is to ensure that all the files on the computer or its network are encrypted with strong RSA + AES encryption algorithms.[1] Once this task is complete, all the files acquire a .z61yt extension, which is also accompanied by a random string.
Suchlike data can no longer be modified or used in any other way, essentially making the information on the locked files useless. It is noteworthy that they are not corrupted by locked by a unique encryption key, which is stored on the attackers' servers. Evidently, cybercriminals don't want to provide a decryptor for free, so victims are being forced to pay.
According to the ransom note 1uZ5_HOW_TO_DECRYPT.txt, users should contact the crooks via WhatsApp +1 (845)682-0537, which we do not recommend doing. Instead, follow the alternative solutions we provide below.
The Z61yt virus stems from a family known as Hive ransomware, which is predominantly known for attacking organizations, businesses, and other corporate entities. It does not exclude home users from getting infected with this malware, however.
| Name | Z61yt virus |
|---|---|
| Type | Ransomware, file-locking malware |
| File extension | A random string plus the .z61yt extension |
| Contact | +1 (845)682-0537 on WhatsApp |
| Ransom note | 1uZ5_HOW_TO_DECRYPT.txt |
| File Recovery | The only secure way to restore files is by using data backups. If such is not available or were encrypted as well, options for recovery are very limited – we provide all possible solutions below |
| Malware removal | Disconnect the computer from the network and internet and then perform a full system scan with SpyHunter 5Combo Cleaner security software |
| System fix | Once installed on the system, malware might seriously damage some system files, resulting in crashes, errors, and other stability issues. You can employ FortectIntego PC repair to fix any of such damage automatically by replacing system corruption |
Operates as doxware
The main goal of Z61yt ransomware authors is to extort money from their victims. Usually, file-locking malware that attacks home users makes file encryption its main focus – cybercrooks ensure that the encryption process is not bugged and that the ransom note (which is used for communication purposes) is always delivered upon infiltration.
However, ransomware that targets businesses and organizations works quite a bit differently, especially as of late. Corporate entities almost always have working backups prepared, which guarantees that, in a case of a disaster, hardware failure, or malware attack, all the relevant information is not lost. This is a huge disadvantage for ransomware operators, as most companies would not pay the ransom if they could restore files from backups instead.
Thus, a few years ago, malware developers came up with a new scheme, one that would increase the probability of money being paid regardless of whether backups are available or not. We are talking about double extortion, where the attackers would steal sensitive information from the company before deploying ransomware and later threaten to release corporate secrets for other malicious parties or everyone to access.
This type of extortion method is known as doxware[2] and has been extremely prevalent due to its efficiency. Companies have to treat each such attack as a data breach and are inclined to pay for the attackers not to publish the sensitive information. Z61yt ransomware is a perfect example of this practice.
Why you shouldn't pay
The FBI and security researchers always advise against paying or even contacting cybercriminals.[3] Crooks may never send the decryptor or deliver one that doesn't work (or even an infected tool that would install other malware on the device), which would end up with victims losing not only their files but also money. Likewise, paying cybercriminals only encourages them to develop their ransomware and infect more users/companies worldwide, as it proves that their illegal money-making scheme works as intended.
It is understandable though, why victims would decide to pay despite all this. Sensitive data disclosure can end very badly, and they're even have been establishment closures due to the devastating consequences of a ransomware attack. Nonetheless, the risks are great when paying, as hackers may target victims again later, knowing they are willing to pay.
Malware removal
Evidently, we recommend not paying the ransom and instead, dealing with a ransomware attack in a different, more secure way. The first task is to remove malware from the system and all the networked machines if such were present. In order to prevent malware from communicating with the attackers, the first step is to sever the internet and network connection:
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet

- Click Network and Sharing Center

- On the left, pick Change adapter settings

- Right-click on your connection (for example, Ethernet), and select Disable

- Confirm with Yes.
Once there are no longer connections, it is time to remove Z61yt ransomware from the system. While manual virus elimination is possible, it is not recommended – security software is the way to go. SpyHunter 5Combo Cleaner or Malwarebytes can be used to automatically find and remove all the malicious components from the system. Besides, security software is your first line of defense when it comes to malware attacks, as the best thing to do is not to get infected in the first place.
After the infection is terminated, we recommend using the FortectIntego PC repair tool. Once affected by some type of malware, Windows system files might get corrupted, and security software would not be able to deal with that. As a result, after malware removal, users might experience system crashes, BSODs, errors, and other common technical issues. The repair tool can target damaged system files and replace them with brand new ones.
Data recovery
Fine encryption is a complicated matter, as a complex string is used to lock and unlock the data. This password is accessible only to crooks, and deciphering it without having access to it is almost impossible. Even supercomputers would struggle with calculating such a complex string. Thus, recovering data after a ransomware attack without having backups is rather difficult, if not impossible.
However, we recommend trying alternative methods that could be effective for some victims. Data recovery software might sometimes be useful if the encryption process was not performed optimally. Waiting some time might also be effective, as security researchers constantly work on delivering free decryptors for victims of ransomware. Note that you should make backups of your locked files if you do not have proper backups available before proceeding with the instructions below.
Getting rid of Z61yt virus. Follow these steps
Restore files using data recovery software
Since many users do not prepare proper data backups prior to being attacked by ransomware, they might often lose access to their files permanently. Paying criminals is also very risky, as they might not fulfill the promises and never send back the required decryption tool.
While this might sound terrible, not all is lost – data recovery software might be able to help you in some situations (it highly depends on the encryption algorithm used, whether ransomware managed to complete the programmed tasks, etc.). Since there are thousands of different ransomware strains, it is immediately impossible to tell whether third-party software will work for you.
Therefore, we suggest trying regardless of which ransomware attacked your computer. Before you begin, several pointers are important while dealing with this situation:
- Since the encrypted data on your computer might permanently be damaged by security or data recovery software, you should first make backups of it – use a USB flash drive or another storage.
- Only attempt to recover your files using this method after you perform a scan with anti-malware software.
Install data recovery software
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

Find a working decryptor for your files
File encryption is a process that is similar to applying a password to a particular file or folder. However, from a technical point of view, encryption is fundamentally different due to its complexity. By using encryption, threat actors use a unique set of alphanumeric characters as a password that can not easily be deciphered if the process is performed correctly.
There are several algorithms that can be used to lock data (whether for good or bad reasons); for example, AES uses the symmetric method of encryption, meaning that the key used to lock and unlock files is the same. Unfortunately, it is only accessible to the attackers who hold it on a remote server – they ask for a payment in exchange for it. This simple principle is what allows ransomware authors to prosper in this illegal business.
While many high-profile ransomware strains such as Djvu or Dharma use immaculate encryption methods, there are plenty of failures that can be observed within the code of some novice malware developers. For example, the keys could be stored locally, which would allow users to regain access to their files without paying. In some cases, ransomware does not even encrypt files due to bugs, although victims might believe the opposite due to the ransom note that shows up right after the infection and data encryption is completed.
Therefore, regardless of which crypto-malware affects your files, you should try to find the relevant decryptor if such exists. Security researchers are in a constant battle against cybercriminals. In some cases, they manage to create a working decryption tool that would allow victims to recover files for free.
Once you have identified which ransomware you are affected by, you should check the following links for a decryptor:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

If you can't find a decryptor that works for you, you should try the alternative methods we list below. Additionally, it is worth mentioning that it sometimes takes years for a working decryption tool to be developed, so there are always hopes for the future.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Z61yt and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Ron Franklin. AES vs. RSA Encryption: What Are the Differences?. Precisely. Data security blog.
- ^ Doxware. Techopedia. Technology encyclopedia.
- ^ D. Howard Kass. FBI Director Wray Tells Ransomware Victims Not to Pay Up. ASSP Alert. A Cyber Risk Resource.
