Zeropadypt ransomware (Removal Instructions) - Decryption Steps Included
Zeropadypt virus Removal Guide
What is Zeropadypt ransomware?
Zeropadypt ransomware is the cryptovirus that uses asmo49@asmodeus.us email address to keep contact with victims
The common ransomware file markers come after the original file name and start with a dot, in this case, there is no dot, and the appendix comes immediately after the original file extension. The pattern includes victims' ID and contact email of cybercriminals, so your file may get renamed in this pattern – OriginalFile.jpg[id=xxxxxxxxxx][Email=asmo49@asmodeus.us].
After all of these alterations, Zeropadypt ransomware virus delivers a ransom note in the text file READ-Me-Now.txt that states about the alleged file encryption and offers test decryption of one file that is 1MB large. Any contacting between the victim and criminals can lead to more damage to your device or even permanently corrupted data, so avoid writing them via provided email and remove malware instead.[1]
| Name | Zeropadypt |
|---|---|
| Type | Ransomware |
| Symptoms | Locks files, makes them useless by filling the content with zeros, demands payment |
| Distribution | File attachments with infected files |
| Contact email | asmo49@asmodeus.us |
| File marker | [id=xxxxxxxxxx][Email=asmo49@asmodeus.us] |
| Ransom note | READ-Me-Now.txt |
| Elimination | Use anti-malware tool and remove Zeropadypt ransomware |
| Virus damage termination | Clean the system with FortectIntego and eliminate possible damage |
Zeropadypt ransomware virus claims to have encrypted your files, but there is no encryption process, according to researchers that have analyzed the malware sample. However, this threat works like a typical cryptovirus since the ransom is demanded in cryptocurrency.[2]
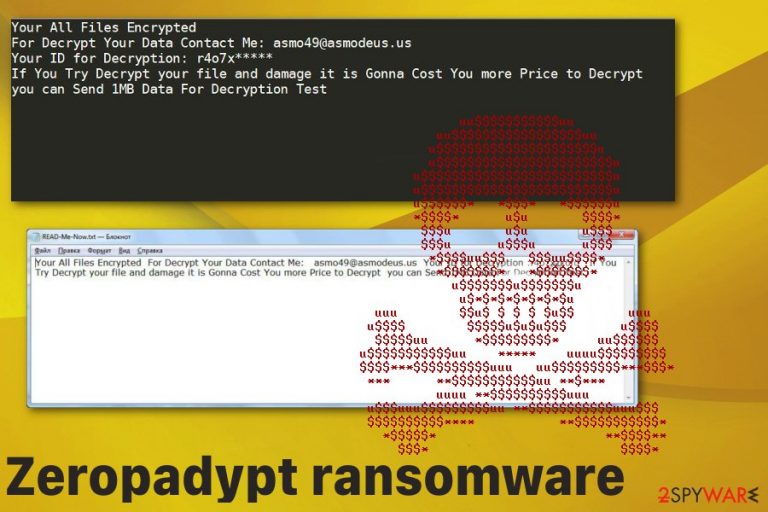
The ransom message that Zeropadypt ransomware delivers in a text file named READ-Me-Now.txt reads the following:
Your All Files Encrypted
For Decrypt Your Data Contact Me: asmo49@asmodeus.us
Your ID for Decryption: r4o7x*****
If You Try Decrypt your file and damage it is Gonna Cost You more Price to Decrypt
you can Send 1MB Data For Decryption Test
Although paying the ransom shouldn't get you anywhere since files get filled with zeros instead of locked by changing the original code. Zeropadypt ransomware makes data useless like this and affects various files:
- photos;
- videos;
- audio files;
- documents;
- archives;
- cloud;
- databases.
Cybercriminals are the one who develops this Zeropadypt ransomware. Although there is no relation with any hacker group, 0kilobypt virus family is possibly associated with this cryptovirus. Any association with known criminals indicates that malware is more dangerous than any newly developed virus since hackers already have experience.
Large-scale infection caused by this notorious Zeropadypt ransomware is not focusing on file locking only. The threat is set to affect more parts of the targeted device, to make sure the needed processes are running on the machine. Windows registry changes, data removal, and boot options get altered to achieve persistence
You need to remove Zeropadypt ransomware as soon as possible, so all those changes can be reversed and damage fixed. The more time you give for this virus,, the more changes can be made without your permission. All those unwanted system changes can be fixed back to default by scanning the machine with optimization tools like FortectIntego.
However, you first should perform a full Zeropadypt ransomware removal with proper anti-malware tools. This method is the best and recommended by many experts[3] because of automatic virus termination during a thorough device scan. These programs can indicate possible intruders, and dangerous malware lurking on the machine and remove them all at once in a few steps.
Remember that Zeropadypt ransomware is more dangerous than typical PUP or cyber threat and it can not only track your browsing preferences but also steal information stored on the machine, in files on the computer. This personal data can be especially valuable in the Drak Web, so criminals make a profit from victims.[4]
In many cases, malware as such gets delivered with the help of other viruses like trojans or worms. However, Zeropadypt ransomware can install malicious programs after the initial infiltration and run those intruders on the machine automatically. For that, you also need a thorough system scan with anti-malware tool. You should benefit from Safe Mode, so check additional removal tips below the article.
Ransomware spreads using the help of spam email campaigns and other malware
Email phishing messages are the most common vectors used for malware distribution, especially ransomware. These campaigns manipulate people into thinking that they received a legitimate notification from a company or service. However, the interactive content or file attachments include the direct payload of malware or opening the file/hyperlink leads to the automatic installation of the trojan or malware.
Malware-filled sites can also be designed to pose as known pages and deliver download pages of the malicious script. Popular formats of files like documents, executables or PDFs get delivered without your permission and malicious macros triggered by one click of the mouse. Then payload gets loaded on the machine.
It is avoidable if you pay more attention to the content delivered to you. Many malware creators have dangerous goals and can use your private information for identity theft. Delete emails with suspicious subject lines and sent from unknown sources. Keep antivirus program running on the machine, so threats get blocked in advanced.
Terminate Zeropadypt ransomware by scanning the machine entirely with AV tool
Zeropadypt ransomware virus can be set to find and steal valuable information that gets stored on your device. The threat also changes preferences of your PC boot settings, adds files that run various processes, or even disables security functions and programs on the computer.
You can reverse these alterations with anti-malware tools that you should use for Zeropadypt ransomware removal. FortectIntego, SpyHunter 5Combo Cleaner, or Malwarebytes can help to terminate this and other threats and fix possible damage on the machine.
It is especially important to remove Zeropadypt ransomware as soon as possible, so all the changes get reversed and your affected files can be replaced with safe and useful ones from the backup. Sometimes people haven't backed their data, and file backups have no value after the ransomware attack. For that reason, special data recovery software gets developed. You can find a few suggestions below.
Getting rid of Zeropadypt virus. Follow these steps
Manual removal using Safe Mode
Get rid of Zeropadypt ransomware with anti-malware tools and Safe Mode with Networking feature:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Zeropadypt using System Restore
You can recover the system of your PC to a previous state with System Restore feature
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Zeropadypt. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Zeropadypt from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Zeropadypt, you can use several methods to restore them:
Data Recovery Pro is the program that helps you restore files affected by any malware or accidentally deleted data
Try Data Recovery Pro if you have no files backed up on cloud services or external devices
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Zeropadypt ransomware;
- Restore them.
Windows Previous Versions feature is helpful after Zeropadypt ransomware removal
You can use this feature for file recovery when System Restore gets enabled
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer restores your files
Data affected by Zeropadypt ransomware can be recovered with ShadowExplorer because it uses Shadow Volume Copies
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Decryption tool is not developed for Zeropadypt ransomware yet
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Zeropadypt and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Paying for ransomware could cost you more than just the ransom. Trendmicro. Simply security blog.
- ^ Cryptovirology. Wikipedia. The free encyclopedia.
- ^ Virusai. Virusai. Spyware related news.
- ^ Value of your data on the dark web. Peerless. Tech solutions.







