BTCWare ransomware / virus (Removal Instructions) - updated Dec 2017
BTCWare virus Removal Guide
What is BTCWare ransomware virus?
BTCWare locks files with .shadow and .wallet file extensions since December
BTCWare ransomware family is known since April 2017 when the first variant of the file-encrypting virus has been released. During the lifetime, malware was updated several times. Each of the version appends a unique file extension to targeted files and uses different contact email address to communicate with victims who want to obtain decryption software. The latest versions emerged in December using .[paydayz@cock.li]-id-id.shadow and .wallet file extensions.
Some experts say that BTC Ware is derived from CrptXXX ransomware family. It is supposed to be a second version of the CrptXXX.[1] However, it does not stand out among other ransomware threats. Some versions of the virus are already decryptable, thus after the attack users should remove BTCWare first and think about data recovery later.
Different variants of BTCWare virus act similarly. However, they differ from each other by appended file extensions. Currently, the virus locks files with these extensions:
.payday, .xfile, .onyon, .blocking, .theva, .cryptobyte, .cryptowin, .btcware, .master, .aleta, .gryphon, .anubi, .nuclear, .wyvern, .shadow, and .wallet.
The name of the ransom note also might change. Depending on the version, crypto-malware might provide data recovery instructions in:
- #_HOW_TO_FIX_!.hta.htm,
- !#_READ_ME_#!.inf,
- !#_RESTORE_FILES_#!.inf,
- !#_READ_ME_#!.hta,
- HELP.inf,
- !## DECRYPT FILES ##!.txt,
- _READ_ME_.txt,
- HELP.hta;
- !! RETURN FILES !!.txt;
- ! FILES ENCRYPTED.txt.
Nevertheless, the names of the ransom note change; the instructions remain the same. Victims have to contact criminals via provided email address due to the set amount of time. Developers also use numerous different email address, including, keyforyou@tuta.io, decryptorx@cock.li, assistance@firemail.cc, newnintendoss@qq.com, pardon1@bigmir.net, pardon@cock.li, help@onyon.info, paydayz@cock.li, arkana@tuta.io etc.)
This virus is not modest – it requires at least 0.5 BTC, which equals 1,815 USD.[2] Regardless of how important files are, it is not recommended to assist the cyber villains with money. There are no reports whether the individual who remitted the payment retrieved his or her files. Likewise, we recommend looking at this situation rationally and focusing on BTCware removal. For that, you can use FortectIntego or SpyHunter 5Combo Cleaner.
During the encryption process, you may not notice any particular signs except slower PC performance and odd UAC messages. However, typically the virus encrypts files so quickly that the user simply does not notice anything suspicious[3].
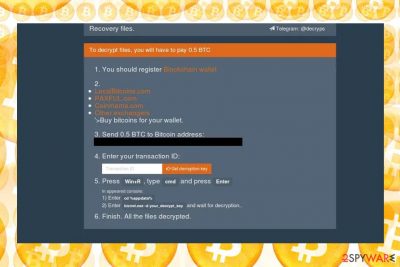
The ransom note, which the virus provides contains an explanation how to pay a ransom to restore files. It manifests a sign of complaisance as it provides links to several links which instruct victims how to purchase a Bitcoin wallet.
When you transfer the indicated amount of ransom, the offenders will supposedly transfer the key which you have to enter in Command Prompt window in such form: with biznet.exe-d [your_decrypt_key]. According to the ransom note, the virus also places its malicious files in AppData Roaming folder. Therefore, we suggest making a move and remove BTCware immediately.
Victims of BTCWare can decrypt files without paying the ransom
Malware researcher Michael Gillespie released a decryption software at the beginning of May 2017 and since then another breakthrough happened – an anonymous user under a nickname checker123 posted the master key of the malware on Internet forums. Whether the key was released by the malware creators themselves or their opponents, it only benefits the users.
Nevertheless, crooks presented new variants of malware; decryption software was updated as well. The updated version of BTCWare decryptor to support ransomware versions featuring .theva and .onyon extensions. Gillespie worked in collaboration with Francesco Muroni – an enthusiast malware researcher and computer engineer by profession.
The work of these two security experts has led to the creation of a tool which now allows thousands of BTCWare ransomware victims to recover their files completely free of charge and cuts a large portion of profit for the malware creators.
In fact, at the moment of writing the tool has already been downloaded over 920 times and that’s just over the span of a week. Besides from decrypting files with the mentioned .theva and .onyon extensions, this tool covers versions that feature .[< email address >].btcware; .[< email address >].cryptobyte and .[< email address >].cryptowin extensions as well.
So, if you have had your files encrypted by this ransomware, go to the end of this article where you will find the decryptor download link along with other data recovery suggestions.
Chronology of BTCWare updates
Master ransomware virus. Master ransomware is a virus that emerged in April 2017. The ransomware drops #HOW_TO_FIX.inf file after locking all files and marking them with [criminal's email address].master file extensions. The current ransomware variant was noticed to use a long list of email addresses, including: newnintendoss@qq.com, pardon1@bigmir.net, pardon@cock.li, help@onyon.info, westnigger@india.com, stopstorage@qq.com, support_config@protonmail.com, predatorthre@bigmir.net, predator3@gmx.us or teroda@bigmir.net.
It is unknown how much do cyber criminals ask in exchange for a decryption software, as well as whether they actually provide it after receiving the payment. Sadly, BTCWare Master virus has a slightly improved source code that prevents experts from reversing the malware, therefore previous decryption tools won't be able to restore files marked with .master file extensions.
OnyonLock ransomware virus. This BTCWare variant is known to be using .onyon file extensions to mark files it encrypts. After encoding private user's files, the virus creates a ransom note called !#_DECRYPT_#!.inf. The ransom note contains instructions on how to decode locked files.
The ransom price is unknown, because the criminals do not state it in the ransom note. They, however, suggest writing to them via one of the provided email addresses: decrypter@onyon.su or tk.btcw@protonmail.ch. Files locked by this ransomware can be decrypted for free.
.blocking file extension virus. This ransomware version emerged in June, 2017. It was spotted to be using [criminal's email address].blocking file extensions for encrypted files. The email address used by cyber criminals is 3bitcoins@protonmail.com.
The email address suggests that victims should pay 3 Bitcoins for data decryption software, and that equals 7710 USD. We do not recommend paying the ransom because the decryptor provided at the end of this article might help you to recover some files.
.theva file extension virus. BTCWare Theva ransomware virus has been spotted in April 2017 and it was using [email].theva extensions for encrypted data. Currently known email address associated with this ransomware version is sql772@aol.com.
There is no information on how much .theva file extension virus demands from its victims, however, paying up would be meaningless since there is a free decryptor available.
Cryptobyte ransomware virus. The ransomware is one of the earliest BTCWare versions that drops #_HOW_TO_FIX.inf as a ransom note on victim's PC. Cryptobyte tends to add .[btc.com@protonmail.ch].cryptobyte or [no.xm@protonmail.ch].cryptobyte file extensions to files and include the given email addresses in the ransom note as well.
Luckily, you do not have to pay for data decryption since a free decryption tool is available. You can find its download link below.
.cryptowin file extension virus. Cryptowin ransomware appeared in spring 2017, encrypting data on target computers at full speed. Luckily, it was quickly defeated by malware researchers who released a free decryption tool. The ransomware used to append .[no.btc@protonmail.ch].cryptowin file extensions to locked files or .[decrypter@protonmail.ch].cryptowin. These files are 100% decryptable – you just have to remove the ransomware and use a free decryption tool.
Aleta ransomware virus. BTCWare Aleta virus is one of the newer member of this malware family, and it typically adds such file extension to encrypted files: .[black.mirror@qq.com].aleta. Although the email address can differ depending on the version of the malware, you will notice the name of the virus' version right after it.
In addition, the virus uses a different ransom note name: !#_READ_ME_#!.inf. Victims report that criminals demand 2 Bitcoins as a ransom for data decryption, although there is no news whether the crooks fulfill their promises after receiving the ransom. An immediate ransomware removal is required to protect your PC from further damage. To restore files, we suggest using data backups.
BTCWare Gryphon virus. This BTCWare script-based infection was discovered in late July, 2017, spreading around as payload.exe file. The virus uses [decr@cock.li].gryphon extensions to mark the encrypted files. Victims, who wish to recover their files are required to send the criminals a considerable amount of money in Bitcoins. Only after they make the payment victims are promised a decryption key.
All the instructions how to obtain Bitcoins and where to transfer them are listed in documents labeled as HELP.inf or !## DECRYPT FILES ##!.txt. Essentially, the victims must contact the criminals via decr@cock.li or decrsup@cock.ll email addresses, sending them a proof of transaction and their personal ID number.
BTCWare Blocking virus. This is the new BTCWare virus version you should beware of. Like most BTCWare-based infections, this piece of malware is also built using the original virus code. Nevertheless, extortionists have supplemented it with a few changes of their own.
This version uses [avalona.toga@aol.com].blocking extensions to indicate encrypted files. Additional documents including Info.hta and !#_READ_ME_#!.hta are dropped on the computer to inform the victims about their current situation and to propose a solution — purchasing the decryption tool from the virus creators.
Since the ransomware uses strong encryption to render files unintelligible, obtaining the decryptor may seem like a rational thing to do. Thus, it is not surprising that there might be people who would follow the extortionists demands: make the payment and send their personal ID number to the hackers email avalona.toga@aol.com. But this may easily leave them without their files and penniless as the hackers often tend to dissappear as soon as they receive the payment.
Anubi NotBTCWare ransomware virus seems to be the latest version of the BTCWare malware which encodes files and attaches .[anubi@cock.li].anubi file extension. In its _READ_ME_.txt message, the perpetrators indicate further instructions how to contact them via anubi@cock.li. In order to reaccess encoded files, victims should purchase bitcoins and transfer to the developers of the malware.
They also try to win users' trust by offering decrypting three files for free. As common for ransomware developers, they urge victims to contact them via 36 hours. Otherwise, the key will be lost. They also warn users not to use any third party decryption tools.
Nuclear ransomware virus. This version of the virus was spotted at the end of August 2017. Hungary, Italy, and Iran are in the target eye of the ransomware. It combines RA and AES encryption ciphers to corrupt files on the hijacked computer. During data encryption, it appends .[black.world@tuta.io].nuclear file extension. Once it’s done, users can find ransom note in HELP.hta file.
This time criminals demand to contact them via black.world@tuta.io email within 36 hours in order to get data recovery instructions. According to crooks, using third-party software won’t help to restore files for free. Thus, victims should rush follow their instructions (not recommended).
.[assistance@firemail.cc].nuclear file extension virus. At the beginning of September, malware researchers reported that BTCWare started using .[assistance@firemail.cc].nuclear file extension. It seems that it’s an updated version of Nuclear ransomware. The virus spreads as an obfuscated Underkeeper2 file and after infiltration starts data encryption procedure.
Once targeted files are safely locked, the virus drops a ransom note where victims are asked to contact criminals via assistance@firemail.cc email. They are supposed to respond with detailed recovery instructions and the size of the ransom that needs to be paid.
Wyvern ransomware virus. At the end of September 2017, researchers spotted a new version of BTCWare spreading. The recent piece of malware appends .[decryptorx@cock.li]-id-.wyvern extension. As you can see from the name of the extension, cyber criminals use decryptorx@cock.li email address to communicate with the victims.
The ransom note displayed by the virus does not state a definite price of the decryption software, but urges the victim to write to the provided email as fast as possible as this ostensibly guarantees lower ransom price. Since there are no news about working decryption methods, we suggest removing Wyvern as fast as possible.
PayDay ransomware virus. BTCWare PayDay virus is a newly discovered ransomware sample. It was first detected by a researched Michael Gillespie on October 3rd, 2017. The initial analysis of the virus shows that it is derived from BTCWare malware.
Once installed, the ransomware renders victim's files useless and adds specific file extensions to them. Afterward, it creates and saves !! RETURN FILES !!.txt file on the desktop. The text file contains short message:
all your files have been encrypted
want return files?
write on email: keyforyou@tuta.io
Currently, it is unknown whether files encrypted by PayDay file extension virus can be restored back to their original state. One thing is sure – you must remove PayDay malware from the system as soon as possible to prevent additional data loss. According to Losvirus.es IT professionals, this version should be handled professionally, so using a professional anti-malware software is simply a must.[4]
Shadow ransomware. On December 2017, a new variant of ransomware was released. Technical details haven't changed; however, ransomware now appends a new file extension and uses different contact email address. Shadow BTCWare adds .[paydayz@cock.li]-id-id.shadow file extension.
Following data encryption, it delivers a ransom note where victims are asked to send an email to the paydayz@cock.li and include their ID number. Additionally, they can add up to three files for free decryption. However, it might be just a trickery to convince people into paying the ransom. Once the payment is received, crooks may never allow using decryption software.
.wallet file extension virus. Security experts reported about the new version of BTCWare appending .wallet file extension. Indeed, the same extension has been used by several file-encrypting viruses in the past. Despite the confusion that might cause familiar extension, malware delivers the same ransom note in “! FILES ENCRYPTED.txt” file where victims are asked to contact them via arkana@tuta.io in order to obtain decryption software.
Even though malware is not decryptable yet, accepting developers' offer and paying demanded sum of Bitcoins in order to use their decryption software is not recommended.
Developers distribute crypto-malware using several distribution methods
The initial version of this virus was distributed in a form of a deceptive program called Rogers Hi-Speed Internet. This obfuscated program was actually BTCWare's executable.
This threat is also likely to be distributed in two ways: by spam messages and trojans[5]. While in the former case, you can lower the risk of BTCware hijack; things are more serious when it comes to trojans. Arm up with anti-spyware and anti-virus tools. Malware elimination tool will help you lower the risk. Update it daily. If BTCware virus has descended on your files, such utility will assist in terminating it as well.
What is more, note that not only illegal or torrent sharing domains are likely to disguise a threat. Cyber villains more and more often target legal websites as well[6]. As for the reminder, do not get tempted to open the attachments of email even if they are addressed to you personally. Confirm the authenticity of the message and the sender and only then risk to review the attached content.
Latest variants of BTCWare also take advantage of poor remote desktop services. Therefore, setting strong passwords and limiting admin access is also needed in order to avoid infiltration of ransomware.
BTCWare ransomware removal guidelines
Despite how terrifying ransomware may look, there are also options to curb it. Let anti-spyware tool, such as FortectIntego, Malwarebytes or SpyHunter 5Combo Cleaner, remove BTCware virus. As a result of its complexity, do not get surprised if the virus shuts down some crucial computer functions. In that case, enter the computer in Safe mode and proceed with BTCware removal.
Note that malware removal programs do not decrypt the files. For that purpose, you will need other tools. In relation to this, you might find useful information below the access recovery guidelines.
Getting rid of BTCWare virus. Follow these steps
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove BTCWare using System Restore
System Restore is a second option you might try to regain the access.
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of BTCWare. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove BTCWare from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by BTCWare, you can use several methods to restore them:
Data Recovery Pro and your files
This program is one of the options to restore the files encrypted by BTCware virus.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by BTCWare ransomware;
- Restore them.
The benefits of ShadowExplorer
The key advantage of this utility is that it uses shadow volume copies to restore your files. Note that this option is only effective in case the file-encrypting threat does not delete them beforehand.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
BTCware Decryptor
Download BTCware Decryptor released by Michael Gillespie here. When downloaded, launch the program, select the partitions, folders or specific files you want to decrypt and hit decrypt! Remember that you might be asked to provide an encrypted and healthy version of the same file for the decryptor to be able to generate the file unlock key. Make sure you have these files prepared before launching the application.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from BTCWare and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Ian Barker. New version of CryptXXX ransomware is harder to decrypt. Betanews. technology News and analysis.
- ^ Bitcoin Calculator. CoinDesk. Bitcoin News, Prices, Chartsn and Analysis.
- ^ Rick Correa. How Fast Does Ransomware Encrypt Files? Faster than You Think. Barkly Endpoint Security Blog. The Latest Endpoint Security News, Tips, and Actionable Insights.
- ^ LosVirus. LosVirus. Malware Removal Guidelines.
- ^ Darlene Storm. Dridex: First banking Trojan with AtomBombing to better evade detection. ComputerWorld. IT news, business technology, reviews.
- ^ Ryan Barrett. Ransomware Is A Repeat Offender: How To Protect Your Business. Forbes. Business, Entertainment. Sports, Security.





















