PayDay ransomware / virus (Removal Guide) - updated Feb 2019
PayDay virus Removal Guide
What is PayDay ransomware virus?
PayDay ransomware is a cryptovirus that delivers a new version of file-encrypting malware in 2019 that demands for 200$
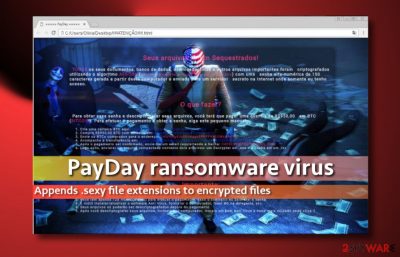
PayDay ransomware is a malicious program spotted spreading at the end of 2016 and continuously releasing new versions up til 2019. Originally, it targets Portuguese computer users. However, hackers keep releasing this crypto malware all over the world. One of the variants – Sexy ransomware was discovered in November 2017 but after that more versions have surfaced. Payday virus is based on the HiddenTear[1] and uses AES cryptography. While the first version appends .sexy, other version attaches .[email]-id-id.payday file extension or appendix formed in a ransom character pattern with 6 letters to each encoded file. You may recover access to your data by using either standard or brute-force HiddenTear decryptor. But malicious actors modify their products to make them immune to previously released decryption tools. The newest variant of PayDay ransomware delivers HOW_TO_DECRYPT_MY_FILES.txt file as a ransom note and demands 200$ for decryptor.
| Name | PayDay ransomware |
|---|---|
| Type | Cryptovirus |
| Ransom note | HOW_TO_DECRYPT_MY_FILES.txt; !! RETURN FILES !!.txt |
| Known since | 2016 |
| Ransom amount | 200$ |
| File extension | .[email]-id-id.payday; .sexy; .random-6-letters |
| Cryptography | AES encryption algorithm |
| Distribution | Spam email attachments |
| Elimination | Use powerful antivirus to remove PayDay virus and clean the system using FortectIntego |
While PayDay encrypts data, you might notice system slowdowns. The computer can slow down for many different reasons, and ransomware is definitely not the first thing that comes to mind.
Once the PayDay ransomware virus renders all target files into useless pieces of data, it creates a HyperText Markup Language format file called !!!!!ATENÇÃO!!!!!.html and saves it on user’s desktop. The ransom note opens via a web browser and explains (in Portuguese) that files have been encrypted, and now the victim needs to pay up if he/she wants to see or use them ever again.
The PayDay malware asks for R$950, which is approximately 286 USD. The virus refuses to receive the ransom in any other currency but Bitcoins, as this way authors of this ransomware can receive money and stay anonymous. Perpetrators leave a contact email address in case the victim wants to ask something – CatSexy@protonmail.com.
You shouldn’t fall for ransomware threats and get rid of this virus as soon as you can because it is yet another decryptable HiddenTear variant. Remove PayDay using guidelines given below and then prepare for data decryption process, which will convert all .sexy files into normal ones.
To eliminate this crypto-malware, you have to obtain a professional antivirus or malware removal tool, such as FortectIntego or Malwarebytes. However, you should also check PayDay ransomware removal guide at the end of the article to learn how to succeed in this task.
Sexy ransomware might be an offspring of the latter malware
Sexy virus attaches .sexy file extension to the encoded data as well. While the amount of the ransom remains not indicated, the cybercriminals insist on contacting via sexy_chief@aol.com e-mail address to settle the price for a decryption tool.
Besides, victims are allowed to send one file for a free decryption that doesn't contain any valuable information. Even though crooks try to earn people's trust, we recommend you to focus on the Sexy removal instead. It is clear that they are not going to stop their malicious activity. Thus, do not motivate them by paying the ransom to develop new versions similar to the PayDay ransomware or updating this one.
Introduction to the variants of the Pay Day ransomware
Cybersecurity experts from NoVirus.uk[2] have noticed an example of the crypto-malware that appends .[]-id-.payday file extension at the end of the file-name. It is believed that the ransomware is inextricably linked to BTCWare together with PayDay virus.
After finishing data encryption, the virus delivers !! RETURN FILES !!.txt file which briefly informs about ransomware attack:
all your files have been encrypted
want return files?
write on email: keyforyou@tuta.io
Later on, the malware opens payday.hta file with further instructions. The latest version includes new email addresses: checkzip@india.com and payday@cryptmaster.info. The malware has been spotted spreading via spam email entitled as Schedule_order.r03. Though the malware developer pretends to be a representative of KAVITA company, take a look at the message content:
Dear Sir,
Attached, please find attached Memo in the folder for purchase requests
Kindly issue requested Order confirmation at your earliest.
Looking forward to your cooperation in the matter for which thank you beforehand.
The malware felons did not bother themselves to write the message in correct English. Ample of grammar mistakes and lack of punctuation marks already suggest the deceptive origin of the message. Furthermore, this PayDay ransomware version employs a brute-force attack strategy, specifically looks for weak Remote Desktop protocols. There are third-party tools which help you manage them and change them into more complex ones.
In order to reduce the probability of ransomware encounter, these recommendations might be of use:
- set a limit for failed log-in attempts
- activate two-step verification
- update security apps and crucial software such as Java and Adobe Flash Player once the updates are issued
- set up complex passwords comprised of letters, punctuation marks, characters and numbers (avoid using full dictionary form words)
In any case, make a rush to eliminate crypto-virus from the system and try either BTCWare or HiddenTear decryption software.
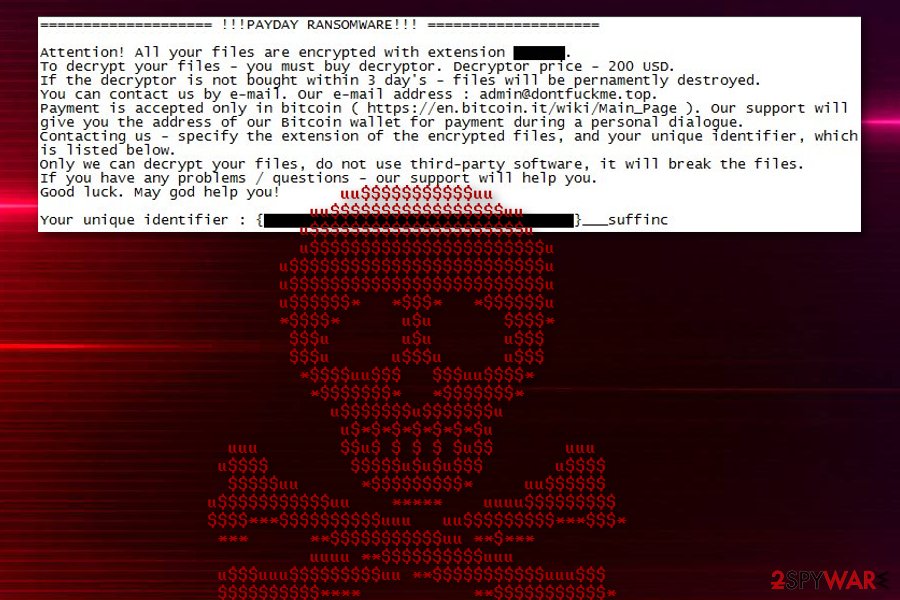
At the beginning of February 2019, MalwareHunterTeam discovered new PayDay ransomware version that has a few different features that first versions of the malware.
This virus still uses AES encryption and focuses on file-locking process as the first step in the attack. According to various analysis, it seems that developers focus on specific locations in different campaigns.
When files get encrypted, random six letter marker gets at the end of every document, photo or database file and ransom note – HOW_TO_DECRYPT_MY_FILES.txt gets placed in every folder containing these encoded files. The note shows that the ransom amount is 200$ and reads the following:
============== !!!PAYDAY RANSOMWARE!!! ==============
Attention! All your files are encrypted with extension ***.
to decrypt your files – you must buy decryptor. Decryptor price – 200 USD.
If the decryptor is not bought within 3 day’s – files will be pernamently destroyed.
You can contact us by e-mail, our e-mail address : admin@dontfuckme.top.
Payment is accepted only in bitcoin ( https://en.bitcoin.it/wiki/Main_Page ). Our support will give you the address of our Bitcoin wallet for payment during a personal dialogue.
Contacting us – specify the extension of the encrypted files, and your unique identifier, which is listed below.
Only we can decrypt your files, do not use third-party software, it will break the files.
If you have any problems / questions – our support will help you.
Good luck. May god help you!
Your unique identifier : {**************}___suffinc
As per usual, ransomware creators demand payments in cryptocurrency, in this case, Bitcoin, but you should avoid any contact with these criminals and remove PayDay ransomware instead. You can do that using anti-malware tools but don't forget to clean the system further using FortectIntego or similar PC repair programs.
Pay more attention before opening spam e-mails
Common distribution method employed is to send phishing e-mails that download the executable files of the malware. Spam e-mails look extremely genuine. Thus, victims are tricked to open the attachments, which are designed to infiltrate the ransomware into the system. Besides, the file-encrypting virus might spread via malware-laden advertisements and through exploit kits[3] as well.
Therefore, we suggest you stay away from advertisements that promise too good to be true offers. It is also a good idea to ignore ads from questionable third-party sites, especially if they urge you to install “required updates.” Such updates are typically bundled with malicious components. Finally, beware of exploit kits, who waylay in compromised or simply infectious websites and try to exploit software vulnerabilities in visitors’ computers.
PayDay virus termination procedure involves professional help
You are advised to remove PayDay ransomware with a reputable security software since it will save you time and eliminate other malicious programs which might be disrupting your computer's performance. We also want to warn you that the malware might prevent you from downloading the antivirus software. You can circumvent it by booting your PC into Safe Mode before.
Additionally, you should know that manual PayDay ransomware removal is also possible, but not recommended. If you are not experienced enough, you can easily delete wrong files or Registry Keys, which can cause a lot of stability-related computer problems.
Therefore, we suggest you clean the system using FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes (or antivirus that you have). If PayDay ransomware virus prevents from installing or using security software, you should find the instructions below handy.
Getting rid of PayDay virus. Follow these steps
Manual removal using Safe Mode
The presented instructions will show you how to prevent Payday ransomware from blocking you to download the security software.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove PayDay using System Restore
Some victims report that the guide mentioned above doesn't seem to help. In such a case, you should try the alternative method:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of PayDay. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove PayDay from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by PayDay, you can use several methods to restore them:
When you need an alternative for data backups, you should use Data Recovery Pro
When you are dealing with encrypted or accidentally deleted files, Data Recovery Pro allows you to recover them
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by PayDay ransomware;
- Restore them.
Try HiddenTear BruteForcer together with Decryptor to help you retrieve the most important data
Luckily, security experts have developed alternative recovery tools for the victims of different HiddenTear's versions. You should start by downloading HiddenTear BruteForcer and uploading a file with .PNG extension into it. Shortly after, search for the HiddenTear in the Mode menu and launch BruteForce. Afterward, install HiddenTear Decryptor and use the decryption code generated by the BruteForce to recover your data.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from PayDay and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Hidden Tear Project: Forbidden Fruit Is the Sweetest. Tripwire. IT Compliance and Advanced Threat Protection.
- ^ NoVirus. NoVirus. Security and Spyware News.
- ^ Nadia Kovacs. Ransomware- When Cybercriminals Hold Your Computer Hostage. Norton Community. Protection Blog.





















