Jigsaw ransomware virus. 48 variants listed. 2021 update
Jigsaw virus Removal Guide
What is Jigsaw ransomware virus?
Jigsaw ransomware is the malware piece that can be distributed with the help of other threats like worms and trojans
Jigsaw ransomware is a dangerous ransomware, which encrypts files using AES encryption and demands a ransom in exchange for alleged decryption software. The virus is using numerous extensions to mark encrypted files where the latest ones are .data, .fun, .YOLO, .btc. However, there are over 65 versions of this ransomware spreading around the globe in total.
According to cyber experts, in 2016 people hiding behind this virus collected $450 000 from ransoms. Nevertheless, at the moment this cryptovirus has a low detection rate. Experts claim that the main targets are German, Spanish, English, French, Turkish, Portuguese, and Vietnamese users who all receive ransom notes translated to their languages.
Despite the fact that the ransomware has been cracked, it's service hasn't been closed down. Crooks behind this strain have started distributing it via LokiBot Trojan[1]. The campaign has been detected in April 2020 when experts spotted a malspam campaign with infected email attachments. The latest ransomware variant uses .btc file extension and demands to pay the ransom of $1499 in Bitcoin within 24 hours. This was released in July 2020. It seems that every few moths creators release a new member of the family into the wild.
Although the ransomware can be easily decrypted for a while, it remains dangerous due to a tendency to remove a part of encrypted files if the victim does not pay the ransom within a dedicated time. The ransom notes that include messages from creators claim that at least 1000 of those files can get deleted “as punishment”. Therefore, immediate malware removal is required.
IMPORTANT: most of the the ransomware variants can be decrypted using a free Jigsaw decryptor developed by Michale Gillespie in 2016. The tool is being updated regularly making it able to crack the renewed ransom scheme down. According to the developers, the free decryption software is capable of unlocking all the latest file types, including .zemblax, .venom, .hacked.by.Snaiparul, .lockedgood, .pleaseCallQQfile, .black007, .choda, .booknish virus.
| Threat Summary | |
| Name | Jigsaw |
|---|---|
| Discovered | March 2016 |
| Type of malware | Ransomware |
| Systems affected | Windows |
| Infects systems as | moi petite.exe, OscarRansomware.exe |
| Short Description | The main target – personal users' files stored in the system. It encrypts files and later demands a ransom for a decryption key. |
| Symptoms | Personal files locked encrypted and marked with .#### CONTACT_US_pablukl0cker638yzhgr@2tor.com####, .## ENCRYPTED_BY_pablukl0cker ##, .FUCKMEDADDY, .CryptWalker, .LOCKED_BY_pablukl0cker, .justice, .locked, .contact-me-here-for-the-key-admin @adsoleware.comTest, .Bitconnect, .jes, .email-[powerhacker03@hotmail.com].koreaGame, .fun, .onion, .LolSec, .booknish, .pay, .paytounlock, .choda, .coder007@protonmail.com, .black007, .tedcrypt , .## ___ POLICJA !!! ___ TEN_PLIK_ZOSTA, .data, .hacked.by.Snaiparul, .lockedgood, .pleaseCallQQ, .venom, .YOLO, .btc and similar extensions. Desktop wallpaper is replaced. Ransom note created on the desktop. Severe system's slowdowns. High CPU consumption. |
| Distribution Method | Malicious spam email attachments, LokiBot trojan |
| Translated into languages | English, German, French, Vietnamese, Turkish, Spanish, Korean, Portuguese |
| Amount of ransom | 150 USD |
| Traits | The virus can be differentiated from the others by a fact that it steadily eliminates encrypted files if the victim fails to pay the ransom. For that, it sets a timer to 24 hours. |
| Decryptable | Yes. Free decryption software is available on the Internet for free. |
| rEMOVAL | The ransomware can be eliminated with the help of a professional anti-virus program only. Since AV engine may be blocked, restart PC into Safe Mode with networking |
| Fix virus damage | Virus damage can be fixed using a tool like FortectIntego. Run a full scan with it after the ransomware removal. |
Earlier this year, the Jigsaw virus was noticed appending.FUCKMEDADDY, .LOCKED_BY_pablukl0cker, .justice, and .# file extensions. The good news is that the majority of emerged versions are decryptable for free. Therefore, there's a chance to get back access to encrypted files even if you do not have backups.
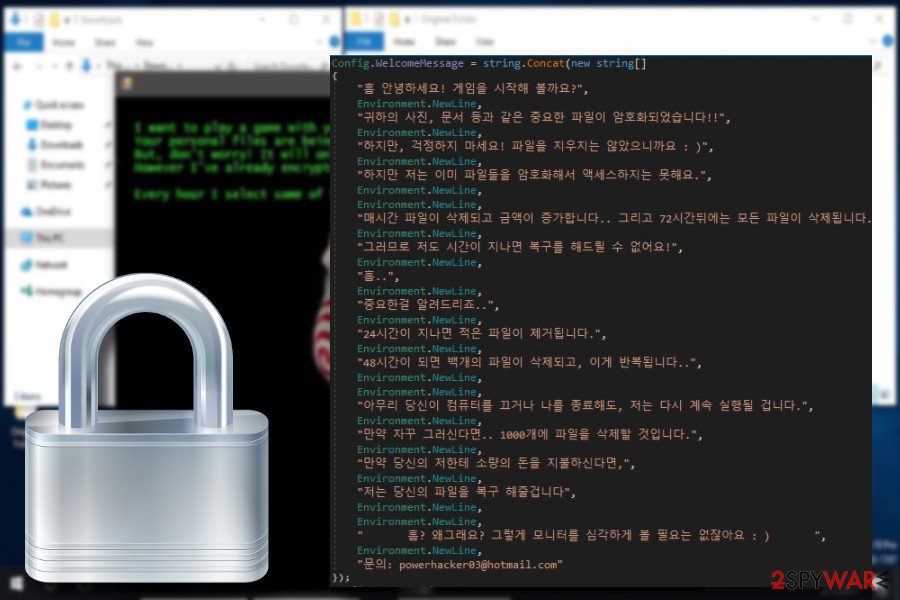
One of the variants found at the end of March 2018 was targeting Korean PC users. It is known for appending .email-[powerhacker03@hotmail.com].koreaGame file extension.
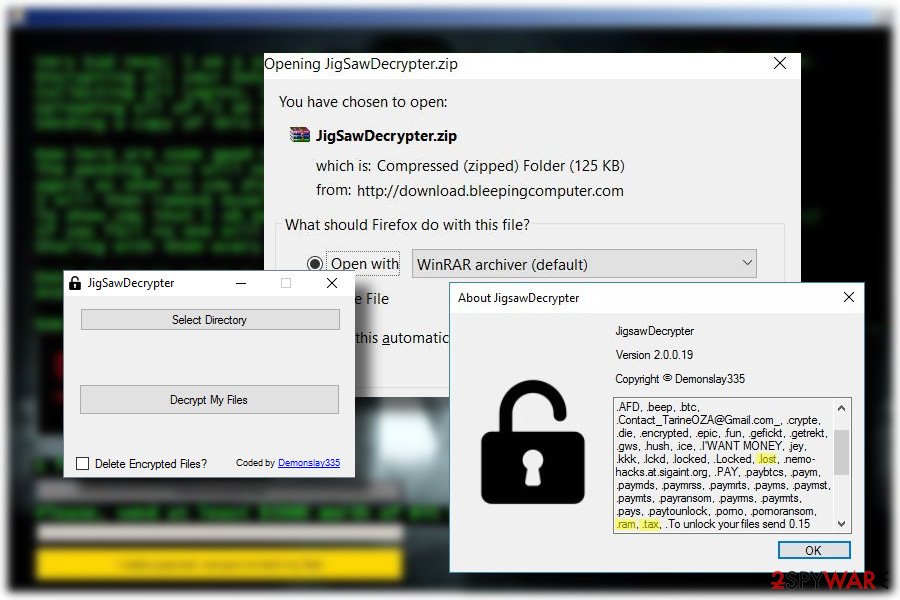
Apart from creating new versions that are aimed at the English-speaking computer users, ransomware has also started using German, French[2], Vietnamese, and Turkish languages. The newest virus version found by Michael Gillespie has been translated into the Spanish language. Up until now, the following extensions have been attributed to this malware group:
.dat, .tedcrypt, .booknish, .fun, .pabluk300CrYpT!, .pablukCRYPT, .kill, .korea, .kkk, .gws, .btc, .hush, .paytounlock, .nemo-hacks.at.sigaint.org, .uk-dealer@sigaint.org, .gefickt, .ghost, .pay, .payms, .paymst, .porno, .xyz, .versiegelt, .encrypted, .epic, .Locked, .locked, .Contact_TarineOZA@Gmail.com_, .tdelf, .lost, .R3K7M9, .rat, .jigsaw, .pabluklocker, .beep, .CryptWalker, .FUCKMEDADDY, .LOCKED_BY_pablukl0cker, .justice, .#, .Bitconnect and .contact-me-here-for-the-key-admin@adsoleware.com, .jes, .email-[powerhacker03@hotmail.com].koreaGame, .fun, .hac, .zemblax.
Although the ransomware has been switching from one extension to other, malware researchers have already managed to crack the code and created a decryption software (you can find it at the end of this article). Check Point[3] was the first to crack the code and present the victims with the free decryptor. According to the company's spokesperson:
When the user presses the ‘I made a payment, now give me back my files!’ button, the program makes an HTTP GET request to: btc.blockr[.]io/api/v1/address/balance/. This got us thinking – what if we change the request, so it queries a different account? Perhaps one that holds the necessary amount of Bitcoins to decrypt our files? Or even better- what if we change the response to say we have the necessary amount?
Note that ransomware researchers have been updating Jigsaw decryptor regularly. Usually, they officially inform the cybersecurity community about the decryptor updated to encrypt the particular version of the virus. This is necessary since criminals who are working behind this virus have been threatening users to delete the encoded data if the ransom is not paid.
Unfortunately, it’s true. Once the virus encrypts the files, it sets a timer[4] for the victim to pay the required sum of money. If the transaction is not carried out within the given hour, one file is deleted from the computer.[5]
Any attempt to initiate ransomware removal is said to lead the victim to the loss of around a thousand files[6]. The pressure of not being able to turn the computer off and the countdown timer ticking on the screen push the users into paying the special amount of BitCoins[7]. Even though this virus may seem frightening, you should still start with the removal because it’s still possible. For that, you can use FortectIntego.
The behavior of the Jigsaw virus
Typically, this ransomware spreads and enters the system with the help of malicious spam emails. Once inside, it hides from the victim. Some minor system slowdowns and errors might give the virus away, but it is really difficult to catch this virus in action.
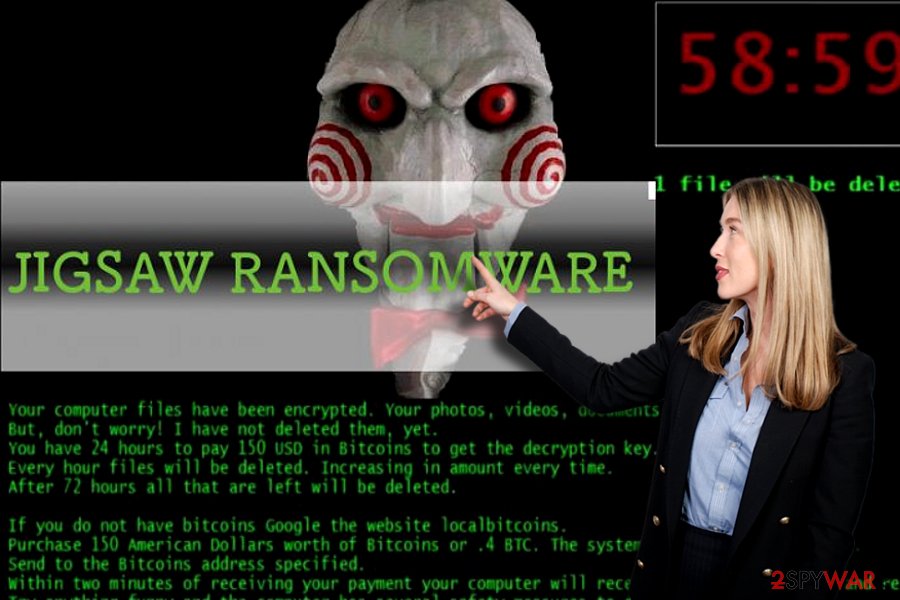
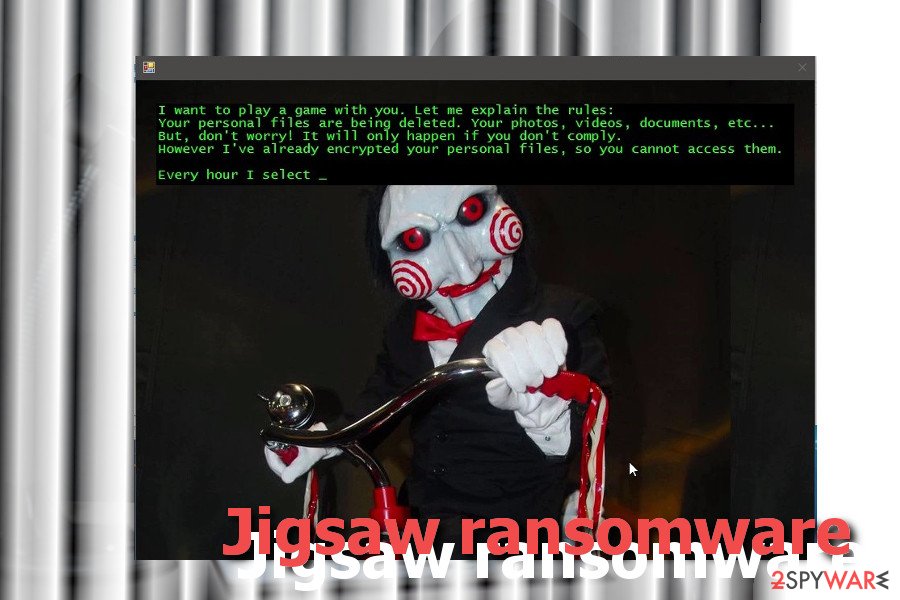
The virus silently encrypts data using the AES cipher and appends one of the specific extensions. Furthermore, it leaves a ransom note with a famous character from the movie “Saw” in the background. The note explains the current situation and asks to pay the $150 ransom:
Your computer files have been encrypted. Your photos, videos, documents, etc…
But, don’t worry! I have not deleted them, yet.
You have 24 hours to pay 150 USD in Bitcoins to get the decryption key.
Every hour files will be deleted. Increasing in amount every time.
After 72 hours all that are left will be deleted.If you do not have bitcoins Google the website localbitcoins.
Purchase 150 American Dollars worth of Bitcoins or .4 BTC. The system will accept either one.
Send to the Bitcoins address specified.
Within two minutes of receiving your payments your computer will receive the decryption key and return to normal.
Try anything funny and the computer has several safety measures to delete your files.
As soon as the payment is received the crypt files will be returned to normal.Thank you.
The ransom note might slightly differ based on the version of Jigsaw ransomware. However, the instruction remains the same – the victims are asked to pay the ransom; otherwise, their files will be deleted. However, you should not be threatened by criminals and focus on malware removal.
New versions that have been created of Jigsaw virus
Zemblax ransomware
In April 2020, cybersecurity experts reported about a new strain of the ransomware, which has been found distributed as a second payload of LokiBot info-stealer trojan. Likewise its predecessors, this variant uses the AES encryption algorithm and targets personal files stored on the host machine. Upon successful infiltration, a victim can recognize this threat from a .zemlax file extension appended to documents, videos, Excel sheets, music, and other files.
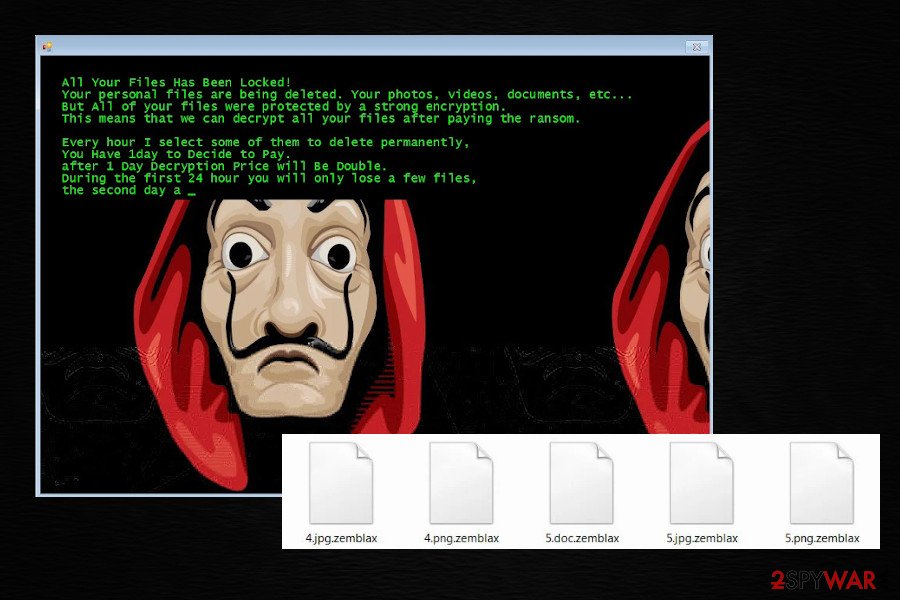
Zemblax ransomware demands its victims to pay the ransom within 24 hours. In the case of nonpayment, criminals threaten to delete a part of locked files and double the price for the decryption key. However, we highly do not recommend paying the ransom. If your files have been encrypted by .zemlax virus, immediately open Task Manager and disable drpbx.exe process.
This process will shut down the ransomware allowing you to run a full system scan with an anti-malware program to remove Zemblax and prevent the file from removal after 24 hours. Finally, download a free Jigsaw decryptor and try to recover compromised data.
Payransom ransomware
According to the experts, Payransom is using AES algorithms to encrypt important files and demands $150 for the decryption. Similar to other versions, this one also threatens to get rid of files if the victim fails to pay the ransom within the given time. The threatening ransom message of the Payransom virus informs that the ransom price will be doubled after 24 hours of non-payment and tripled after 48. If you do not want to lose your files, it is better to remove Payransom immediately as this way your data will be encrypted, but not deleted. This way, you might be able to recover them after some time. Unfortunately, it seems that the decryption tool has not been discovered yet. The virus is appending .payransom file extension.
Payms ransomware
Payms ransomware appears to be a different virus which was developed by using the code of the main virus. Therefore, these viruses act similarly. This virus asks for the same amount of money as the Payransom virus does – 150 USD. If the victim does not pay up the ransom within 24 hours, the price of the decryption software increases to 225 USD.
This malware adds .pay, .payms or .paymst file extensions while encrypting the data. Luckily, you do not have to pay the ransom to retrieve your data – you can recover it with the help of this decryption tool. Before you use it, you must delete the virus from the computer.

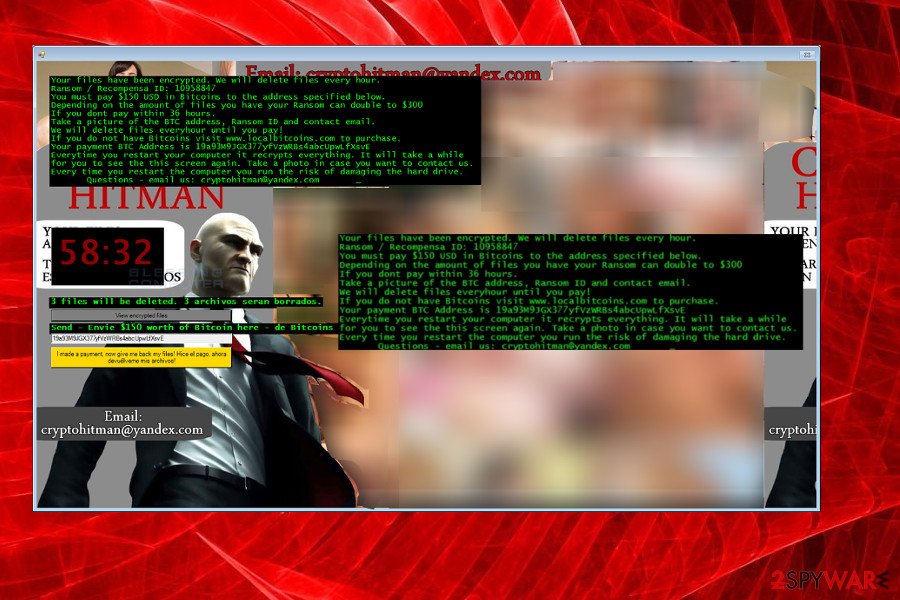
CryptoHitman
CryptoHitman ransomware appears to be a terrible virus that can cause you problems at work or home. This nasty virus stands out of other ransomware variants because it changes desktop wallpaper with a pornographic picture and appends .porno file extension to encrypted data.
Fortunately, you do not have to pay the ransom that CryptoHitman demands, as a free decryption tool for this virus has been already released. You can download it here. If you have become a victim of this computer threat, remove it using a powerful anti-malware software and start decrypting your files with the help of the aforementioned decryption tool.
We Are Anonymous ransomware virus
“We are Anonymous. We Are Legion. We do not forget. We do not forgive. Expect us.” This is how the virus greets the victim after it finishes encrypting all files on a compromised computer. The variant of infamous ransomware locks victim's data using advanced encryption technology and appends .xyz file extension to each file.
The user is asked to transfer 250 USD to a provided Bitcoin address to receive a decryption tool. Luckily, data can be decrypted charge-free with the help of this We Are Anonymous Jigsaw ransomware decryption tool. As always, do not forget to delete the ransomware before you run the decrypter.
German Jigsaw
This variant surfaced around the Internet at the end of October. Once inside the system, it encrypts the victim's files and adds the .versiegelt extension to each of them. In exchange for the decryption service, it asks its victim to pay 100 euro in Bitcoins.
It is not a big amount of money when compared with other ransomware threats. It is also worth mentioning that the language of its warning message is written in German, so there is a high possibility that it spreads only in German-speaking countries. Make sure you remove the versiegelt virus before it damages your files.
French Jigsaw virus
The French version of the virus was discovered in the middle of November 2016 and at the beginning of 2019. These ransomware viruses encrypt victims' files by adding one of these extensions: .encrypted and .fun. The first variant is displaying a ransom note that says: “Vos fichiers ont été cryptés et vous ne pourrez les récupérer que si vous vous acquittez de la somme demandée.” […] However, the newest French Jigsaw version is showing Anti-Capitalist sign and is full of grammar and typo mistakes.
If you can see this warning message on your desktop, stay calm, and don't even think about paying the ransom. You can use one of the methods in our “Data recovery” section to decrypt your encrypted files. However, before you do so, you need to remove Anti-Capitalist and other ransomware versions from your computer.
Turkish Jigsaw ransomware virus
This version of the virus was detected by well-known ransomware hunter Michael Gillespie[8] at the beginning of February 2018. In general, this new ransomware features the same behavioral traits as its predecessors, the file extension that it attaches hasn't been seen before. Currently, all the locked files get the .justice attachment. Besides, the extortionists updated the decrypter.
According to VirusTotal test,[9] Turkish ransomware can evolve the detection of the most powerful AV engines. Only 39 AV engines out of 68 detected the malicious file. The information regarding ransom payment is the same, but the initial “greeting” differs. The extortionists say (translated from Turkish): “If the program is open, then all of your (system) folders are locked. To unlock them, all you need to do is to give us the money that you have stolen from other people. Don't worry. If the folder does not mean anything to you, fine.”
Epic ransomware
Epic ransomware is the newest version of the ransomware which, once again, operates under the name of the Anonymous hacktivist group. The lock screen and ransom note of this virus can be seen below. The virus follows the typical pattern of the ransomware: it gives the victim an hour to pay for the files. After this time runs out, 1-5 files are deleted from the computer. If the victim tries to fight the virus and turns off the computer.
The next time it is booted, the virus may delete not five but 1,000 files. What is more, the hackers demand an outrageous 5000 dollars for the data recovery, but just like with the rest of the ransomware versions, the outcome of such collaboration is completely unpredictable. Thus, it is better to get rid of the virus instead of playing according to the hackers' rules.
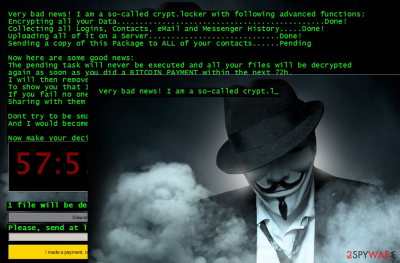
Crypt.Locker ransomware
Crypt.Locker ransomware is another name for Epic ransomware version. As the image below shows, the virus addresses the victim with such lines: “Very bad news! I am a so-called crypt.locker with the following advanced functions.” The virus appends .epic extensions to encrypted records and asks to pay a ransom of $5000 in Bitcoin currency. Such an amount of money is enormously huge, and you shouldn't give it away for some cybercriminals.
We suggest you remove the virus and restore at least part of your data from backups. Please ignore all these claims about leaking your data to your contacts – the virus is trying to convince you to pay up, but the first thing you should do is to complete Crypt.Locker removal.
If you're thinking about paying the ransom, you should know that there are lots of cases when victims paid the ransom but never obtained the decryption software. The same can happen with the crypt.locker decryptor that criminals suggest buying.
HACKED ransomware
HACKED ransomware. Currently, the parasite's distribution is quite low. Nevertheless, the virus does not seem to be any less dangerous than the previous versions.
Though it does not require the victims to pay appalling amounts of money, it now gives less time, only 24 hours to issue the payment of 0.25 or 0.35 Bitcoins. Besides, the new version of the virus now adds .Locked and .locked extensions to the affected files which stokes speculations about a potential new project between Jigsaw and Locky virus developers.
Jigsaw 4.6 ransomware
4.6 version of ransomware is a foolish copy of an infamous main version of the virus. Although we assume that spotted samples of this ransomware show that the virus is in-development process at the moment, it might be that it is just another poorly programmed virus.
It turns out that this ransomware does not encrypt victim's files at all, although in the program/ransom note that it launches in full-screen mode says that files were encrypted.
This ransomware version uses a different picture of John Krammer for the lock screen. However, malware analysts have spotted a couple of new malware versions that appends .nemo-hacks.at.sigaint.org file extensions to encrypted files, and we assume that might be the updated version of the 4.6 ransomware.
The fact that this new version appends file extensions indicates that the virus attempts to modify files stored on the system, so we assume that the .nemo-hacks.at.sigaint.org ransomware can encrypt victim's data, too.
DarkLocker ransomware
Also known as Monument ransomware, DarkLocker ransomware encrypts files and demands to pay the ransom. The virus also delivers a lock screen where it informs victims that their files have been encrypted because they have watched porn. The developers of the virus ask to transfer 0.15 Bitcoins within 24 hours time. Later the size of ransom will reach 0.20 Bitcoins.
However, the authors of the malware suggest paying the ransom immediately if victims do not want to lose their files entirely. According to the ransom message, the virus deletes 1-5 files each hour. What is more, after 48 hours the encrypted data will be eliminated if hackers do not receive the payment. However, following their orders are not recommended. It’s better to remove DarkLocker virus and try additional data recovery methods.
Jokers House
Jokers House is the newest member of the infamous ransomware family. This virus has emerged near the end of April 2017 and has been rapidly growing since. The virus does not fall behind its predecessor and employs a similar method of ransom extortion: the victims are given an hour to pay 100 dollars to reclaim access to their encrypted files. Failing to make the payment results in the destruction of one file.
The cycle continues until the victim transfers the money. Besides, the hackers prevent users from closing the ransom screen too and threaten to destroy 1000 files if the victim chooses to do so. Typically to most modern ransomware, Jokers House indicates the email via which the victims ought to contact them in the extensions added to the infected files. In this case, the email is TarineOZA@gmail.com
Typically to most modern ransomware, Jokers House indicates the email via which the victims ought to contact them in the extensions added to the infected files. In this case, the email is TarineOZA@gmail.com, so the extensions are .Contact_TarineOZA@Gmail.com_.
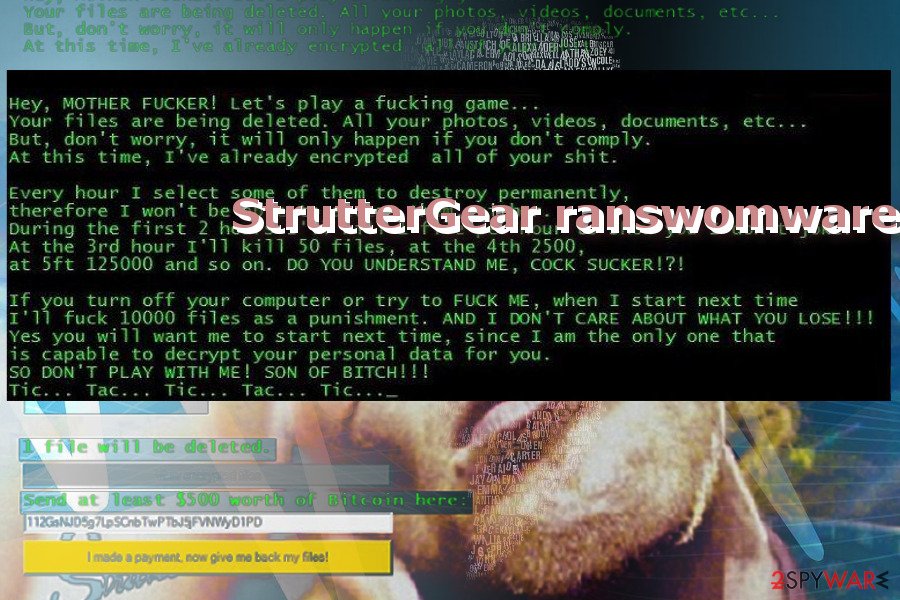
StrutterGear ransomware
StrutterGear variant attacks users the same way as its predecessors. Since the version is quite new, it is unknown what specific encryption technique it employs.
Since the title originates from an MTV show “The Strutter,” the developers address their victims in an insolent manner as well. After the encryption is done, the graphic interface app instructs victims to pay 500 dollars in bitcoins and transfer them to an indicated address. It does not append any file extensions. The malware also tends to delete one file after a specific period.
THEDARKENCRYPTOR ransomware
TheDarkEncryptor ransomware greets users with “All your files have been encrypted by THE DARK ENCRYPTOR using a military-grade encryption algorithm” ransom note. In comparison with other versions, the malware demands only 100 dollars in exchange for users' files.
If you do not remit the payment within five days, the sum of ransom is said to increase up to $350. The virus tends to append the .tdelf file extension to encoded files. Furthermore, it does not possess any intriguing features. Users should be aware of its diverse distribution methods.
Ramsey ransomware
Ramsey malware version draws inspiration from Ancient Egypt. Moreover, it prefers targeting Turkish netizens as the ransom note is written in the respective language. Besides its features to delete one file after some time, the felons also provide a specific email address – ramsey34.ramsey34@vfmail.net.
Lost ransomware
.lost file virus is a version of the virus that tends to encrypt files with the combination of RSA and AES encryption techniques. Its traffic is still low, so only a few users may run into this variant. Beware of spam emails with shady attachments.
Note that such emails may alarm you with fake charges presented by the supposed FBI or the email asking you to review intriguing information. Such a version is most likely to distribute via corrupted domains.
R3K7M9 ransomware
.R3K7M9 file extension variant is likely to be distributed in gaming and adult-content websites. Interestingly, the extension refers to the “leet” alternative alphabet popularized among hackers in the 1980s. The ransomware activates via the f*ck.exe file so it may be wrapped under the disguise of a corrupted app. Once it sneaks into the device, it may require some time to encrypt files with .R3K7M9 file extension. It demands approximately 300 dollars for ransom.
Rat ransomware
.rat file extension virus entangles the system and users' files once the Imminent Monitor remote desktop tool (RAT) file. Due to the disguise of the file, victims are unaware that they have activated the threat.
This new version also connects to a specific IP address. According to its technical specifications, the infection is detectable as Gen:Variant.Barys.2440 or Trojan.Barys.D988. It resembles another threat – CryptoDark virus. Fortunately, multiple cybersecurity tools can identify the infection and block it on time.
.Kill files virus
.kill file extension virus was discovered in July 2017. According to researchers, the virus was detected as a new variant of the infamous ransomware family that appends .kill file extension. Malware continues the work just like its predecessors: it encrypts various files, such as MS Office, image, audio, video, archives, etc. Once it’s done, it demands to pay the ransom.
Malware is most likely to enter the system with the help of malicious email attachments. Thus, it’s recommended to stay away from suspicious spam emails and avoid opening files or links included in the email sent from the unknown sender. After infiltration, it’s recommended to remove .kill file virus and try free data recovery options.
Korea ransomware
.korea file extension virus was spotted on July 14. This ransomware replaces the victim's desktop picture with a blank black screen with a white smiley on it. During the attack, this virus encrypts the victim's files and appends .korea file extensions to them.
Luckily, victims of .korea file extension virus do not need to worry about lost files because a decrypter capable of restoring them for free is already available. Therefore, if you accidentally became a ransomware victim, remove Korea ransomware and decrypt your files using the Decrypter.
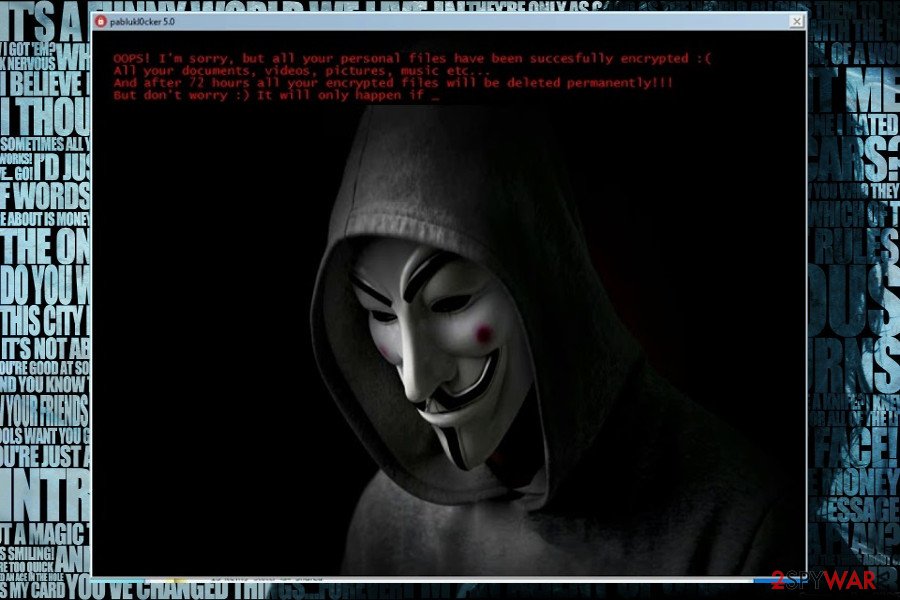
Jigsaw Polish virus
On August 2017, a Polish version of the virus has emerged. On the affected device it is executed from CMD.exe file. Then it makes several changes to the system and starts the data encryption procedure. To the targeted files it appends .pabluklocker file extension and makes them useless.
However, this variant seems to have bugs and does not work properly. Therefore, you should not be threatened by the scary wallpaper and rush to pay the ransom. Focus on .pabluklocker removal and try a free decryptor for data recovery.
Jigsaw screenlocker
This virus runs from the ransowmaro.exe file that usually arrives on the system as an obfuscated email attachment. On the affected device it starts scanning the system and encrypting targeted documents, multimedia files, and other data. Once all the files are locked with a file extension, it triggers a screenlocker window.
However, following hackers' instructions is not necessary. You have to get rid of a locked screen, remove the virus, and use the decryptor to restore corrupted files.
PablukLocker ransomware
It is an updated variant of the PablukLocker ransomware which uses a new extension to mark encrypted files – .pablukCrypt. The virus displays a message that specifies the version of the virus. This time, cybercriminals identify it as “PablukL0cker 4.0 ransomware”.
The threatening message states that the virus deletes a few files on the first day of infection, a few hundred on the next day, and a few thousand on the third day. Luckily, you do not have to worry if your files were encrypted by this ransomware – the decrypter has been updated and is capable of restoring your files for free, so all that you need to do is to remove the PablukCRYPT virus from the system.
Pabluk300CrYpT! ransomware
.pabluk300CrYpT! file extension virus emerged the next day after Pabluk Crypt's appearance. The malware uses the same threatening strategy and promises to delete more and more of a victim's files each day. The only difference between these viruses is that this new variant appends .pabluk300CrYpT! extension to encrypted files.
Files corrupted by this ransomware are decryptable, so remove .pabluk300CrYpT! ransomware today and start restoring your files right away. Do not forget to take preventative measures to keep your computer protected from similar ransomware attacks.
Fun ransomware
Malicious actors behind the strain made a return in October 2017 with an updated version of .fun file extension virus. It currently spreads in the form of a fake Steam Cracker (St3amCrack3r.pdb) program which downloads the new ransomware variant to the system and executes it.
The malicious software attempts to encrypt files but fails due to the use of a faulty encryption key. However, the malware still displays a random-demanding screen that asks to pay $500 for data decryption. It is also worth mentioning that the new version uses a different image for the background of the ransom-demanding screen. This time, it does not represent the character from the famous movie, but the well-known Anonymous mask.
However, this is not the first case of ransomware using .fun extension on encrypted files. A similar version that used to ask for 150 USD as a ransom emerged in April 2016. A year later, in April 2017, another version asking for $25 appeared. Fun ransomware (all versions of it) are typical variants of ransomware that promise to eventually delete a large number of victim's files if the victim fails to pay the ransom. However, the data destruction process can be stopped by implementing Fun ransomware removal.
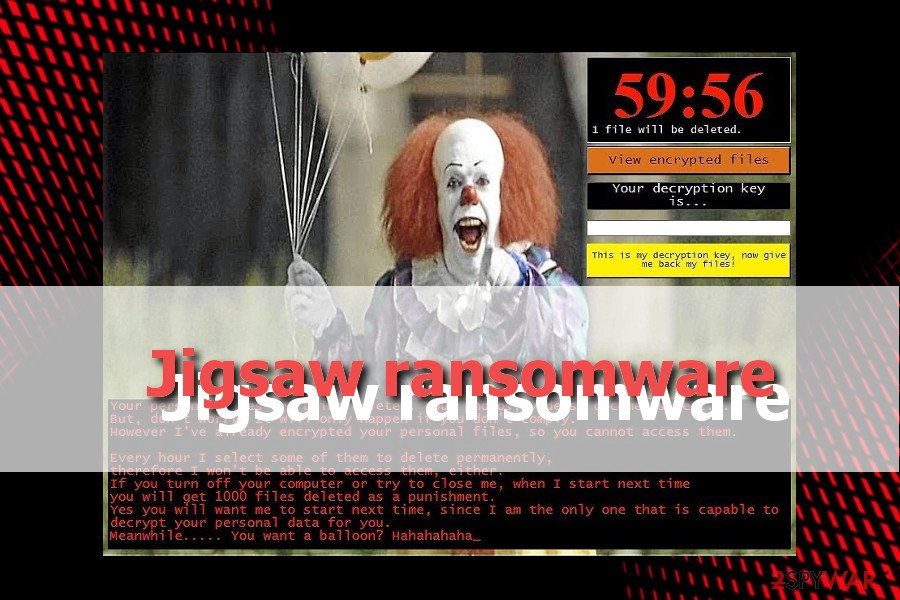
Pennywise ransomware
The malware appends .beep file extension to the encoded data. At the moment, the file-encrypting threat is still under development. It contains evident errors in the source code and does not encode data contrary to the alarms.
It displays its GUI which includes the picture of Pennywise character from It movie[10]. The note threatens users to delete some of the encoded files after each hour. If a victim tries to turn off the computer or close the GUI, the developer threatens to eliminate 1000 files.
The malware is likely to spread under setup.exe file which suggests that the malware is spread in the disguise of an app. Therefore, pay attention to what and what source you install a new application. It is detectable by the majority of security programs.
.##ENCRYPTED_BY_pablukl0cker## ransomware
.##ENCRYPTED_BY_pablukl0cker## file extension virus manifests quite amusing behavior. Since the emergence of the initial version, it was clear that generating activity is an amusing activity for the developers. This sample also proves such speculation. After the infection process, the malware sprouts multiple pictures taken from well-known movies such as Shrek. Another photo displays a protester wearing Guy Fawkes mask.
The source code of this malware contains the message greeting a “victim”[11]. It informs that all important files are locked. After each hour some of them are deleted. In case the victim fails to remit the payment within 72 hours, all encoded data will be deleted. The perpetrator also alarms the user not to shut down the PC as it will lead to the elimination of 1 000 files. Furthermore, the message indicates pablukl0cker638yzhgr@2tor.com for contact purposes.
The new version is already detectable by the majority of security applications as MSIL:Ransom-BU [Trj], HEUR:Trojan-Ransom.Win32.Generic. This version hides under LoL VIP RP HACK 4.0.exe. VirusTotal, a free malevolent URL analysis service also detects another malware variation that functions via executable.3720.exe. Thus, be mindful of this aspect when you install new programs and new extensions.
CryptWalker ransomware
In January 2018, a new version of Jigsaw emerged. The virus spreads as BitcoinBlackMailer.exe file and once executed on the targeted system, starts data encryption procedure.
The virus locks data with .CryptWalker file extension and threatens to delete files if victims do not pay the ransom. However, security experts recommend removing .CryptWalker file virus and use free decryption software for data recovery.
FUCKMEDADDY ransomware
On the 8th of January, 2018, researchers reported the debug version of the ransomware that appends .FUCKMEDADDY file extension and delivers an adult-themed ransom note where criminals provide data recovery instructions in the Polish language.
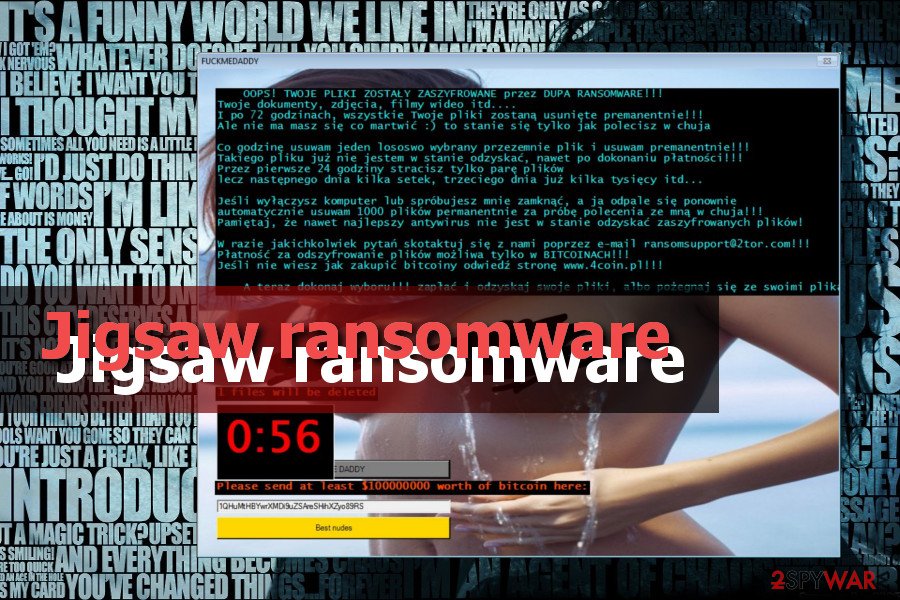
Criminals used ransomsupport@2tor.com contact email address. However, contacting them is not recommended. Malware is executed on the system from the BIG DADDY COCK.exe file.
MADA ransomware
MADA RANSOMWARE is another version of crypto-virus that appends .LOCKED_BY_pablukl0cker file extension to the targeted files. Ransomware spreads as Google Chrome.exe file which allows bypassing computer security quite easily.
Cybercriminals use rakolo23@gmail.com email to communicate with the victims who want to decrypt their files. However, security specialists recommend removing the virus instead of paying the ransom because it may lead to money loss only.
# ransomware
In February 2018, ransomware researchers detected a new form of ransomware. Just like most of its ancestors, it attacks random PCs via spam email when its owners open a malicious attachment. Once executed, the virus adds .# file extension and locks most of the personal files. Unfortunately, .# file extension virus does not have a free decrypter yet, so the only way to get rid of it is to use a professional anti-malware and recover data using backups.
.contact-me-here-for-the-key-admin@adsoleware.com file extension virus
In March 2018, researchers discovered a version of malware spreading as obfuscated Xbox-One-Mod-Menu.exe file. Once malware payload is downloaded on the system, it starts data encryption and makes files inaccessible by appending Xbox-One-Mod-Menu.exe file extension to each of them. However, a free decrypter can recover them.
Bitconnect ransomware
In March 2018, .Bitconnect file extension version was noticed spreading. It is executed from the JigsawRansomware.exe file and immediately starts data encryption on the affected computer. The interesting fact about this ransomware is that it asks to take a picture and upload it to Instagram:
Hold A Card With @TwistedSquad Written On It And Post It On Instagram And Tag @TwistedSquad.
However, instead of promoting suspicious accounts, you should remove .Bitconnect file extension virus with reputable anti-malware software.
Jes ransomware
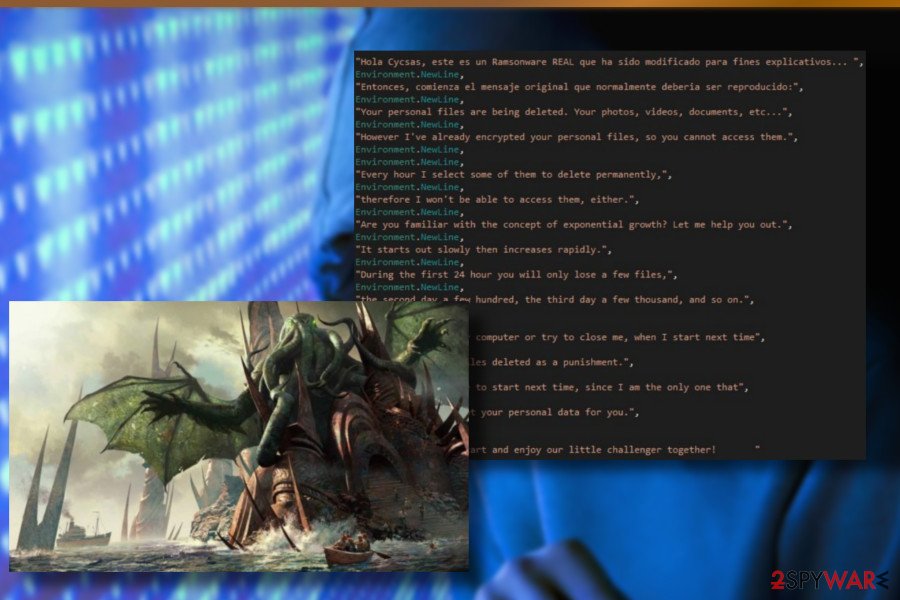
In the middle of March 2018, ransomware researchers revealed a new ransomware variant actively spreading via spam email attachments and malicious software updates. It's oriented to Spanish-speaking users. It locks files by appending the .jes file extension and hastens the victim to transfer the payment within 24 hours. Otherwise, it will delete a hundred ransom files as a punishment.
The Spanish version uses a Cthulhu background image. The Cthulhu is a cosmic entity created by Lovecraft and depicted as a combination of octopus and dragon. Such a decision can hardly be explained, but we can guess that the switch from Jigsaw to Cthulhu has been initiated to disguise their connection and trick people into purchasing the decryptor. Nevertheless, do not pay the ransom because the original decryptor has already been updated in a way to unlock files encrypted by .jes file extension virus.
.email-[powerhacker03@hotmail.com].koreaGame file extension virus
The ransomware virus developers do not waste time. Less than a week after the .jes file extension virus release, hackers rolled out a Korean version of this notorious threat, which is currently in its early distribution phase.
The virus is known for appending an .email-[powerhacker03@hotmail.com].koreaGame file extension to each locked file and instructing the victim to send them a specified ransomware package to the powerhacker03@hotmail.com email.
If you have already been attacked by the Korean virus version, do not rush to pay the ransom. Cybersecurity experts reported that a free decrypter had been updated to recognize and decrypt the .email-[powerhacker03@hotmail.com].koreaGame extension.
LolSec ransomware
This virus version was detected in the first half of April 2018. Being yet another “masterpiece in art,” LolSec features a professional lock-screen picture illustrating a femme fatale accompanied by a joker.
LolSec characteristics coincide with its ancestors, except that it appends .LolSec file extension to the locked files. Currently, the ransomware that is dependent on the BitcoinBlackmailer.exe file can be detected by 33 AV engines out of 65.
In case you found your files encrypted by LolSec ransomware, do not fall for paying the ransom. It has already been added to the decryptor's database, meaning that it can easily be cracked. All you have to do is to download a reputable anti-virus, run a scan with it to remove LolSec, and then download a decryptor, which is available at the end of this article.
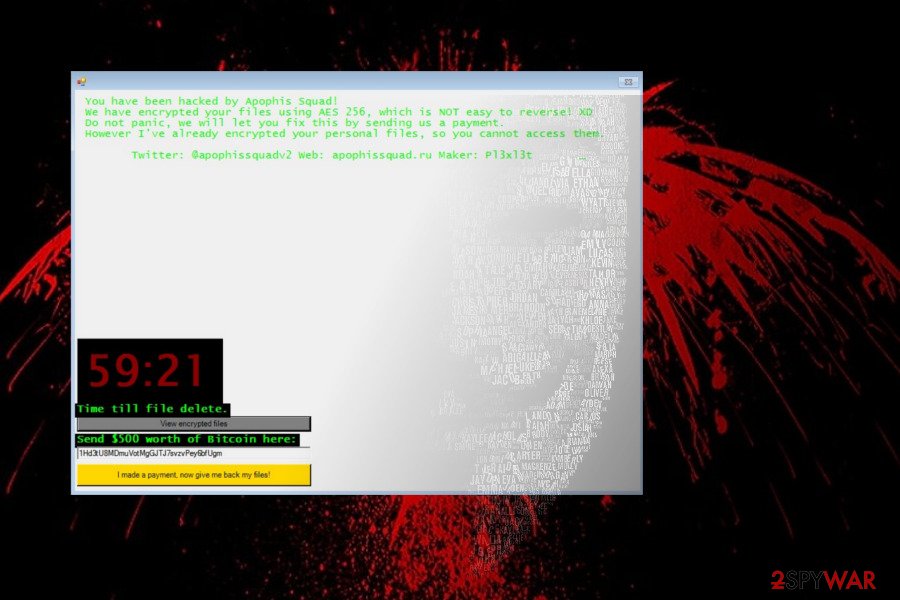
Apophis Squad
Detected in the middle of April 2018, Apophis Squad is targeting English-speaking PC users and can be recognized by .fun file extension that it appends to encrypted files. It uses AES 256 cipher to render personal files useless and demands the victim to pay $500 ransom in Bitcoin cryptocurrency within 72 hours. The ransom note says:
You have been hacked by Apophis Squad!
We have encrypted your files using AES 256, which is NOT easy to reverse! XD
Do not panic, we will let you fix this by sending us a payment.
However I've already encrypted your personal files, so you cannot access them.
Twitter: @apophissquadv2 Web: apophissquad[.]ru Maker: P13x13t[1H COUNDDOWN TIMER]
Time till file delete.
{View encrypted files|BUTTON]
Send $500 worth of Bitcoin here:
[34 RANDOM CHARCTERS]
[I made a payment, now give me back my files!|BUTTON]
Hac ransomware
.hac file extension virus is targeting Portuguese PC users in particular. It is being distributed via malicious spam email attachments infected with JigsawRansomware.exe payload. Once executed, the .exe file injects malicious processes into the system and starts data encryption using the AES cipher. Upon encoding, locked files get .hac file extension, and the victim is expected to pay a redemption in Bitcoins to get the files back.
Unlike previous versions, this version, dubbed as .hac file extension virus, features a high detection ratio. According to VirusTotal,[12] 44 AV engines out of 66 are capable of detecting and immunizing it. Thus, we strongly do not recommend paying the ransom. Instead, remove the virus and try to recover your files using the alternative methods listed below.
Booknish ransomware
This version is currently the newest one and uses .booknish file extension after encrypting the files. Once they are locked, the victim no longer can access them and is demanded to pay $100 as a ransom. All the information necessary for decryption is provided in the ransom note.
Since it spreads inside the malicious spam emails, users are tricked to open the attachment and execute the payload of the ransomware. Experts say that the attachment disguise under the Firefox name to make sure that people are deceived. Although, the executable of the ransomware is named as JigsawRansomware.exe.
Developers of the ransomware attempt to threaten the users to ensure ransom payments as indicated below:
Every hour I select some of them to delete permanently,
therefore I won't be able to access them, either.During the first 24 hour you will only lose a few files,
the second day a few hundred, the third day a few thousand, and so on.If you turn off your computer or try to close me, when I start next time
you will get 1000 files deleted as a punishment.
Choda ransomware
This is the version of the threat that particularly targeted Korean victims. It was released At the start of July 2018. It created frustration for many victims because the execution of the payload led to existing file modification and other issues with targeted machines. After file-locking that marks all files with .choda, malware added choda ransom ( 초다 랜섬 웨어 ) on the machine. The note and the message from criminals in the text file all written in Korean-language. So the target was distinct. However, a few days after this version, cybercriminals released another one aimed for English-speakers.
.coder007@protonmail.com files virus
The version for English-speaking threats was noticed on July 5th, 2018. The virus got its name from a contact email and the particular file marker that was added on all affected images, documents, archive files, videos, audio files. However, it was easy to determine that the threat is from the same developers due to the process running in the background named Jigsawransomware.exe. The threat even used the fake Firefox file, executables supposedly related to the program, so the person that is targeted cannot notice the infection.
.black007 ransomware
The same month of July was a busy time, on the 23rd the version marking files with .black007 came out. Not many changes made in the ransom note or the particular tactics, so these all variants released in the same month resembled the primary version of the ransomware. Same claims about file deletion and large ransomware payments going to thousands of dollars in the form of Bitcoin.
Data ransomware
The threat marking files with .data appendix and demanding 100 euro in Bitcoin for the alleged came out long after the previous versions. At the start of 2019, on January 14th this threat was spotted by researchers and malware experts. Things different from other threats in the family was the text file in French and the amount of redemption – 100 euro instead of the more typical thousands range.
.fun files virus
The self-named ANTI-CAPITALIST ransomware was yet another one with text files and other messages written in the French language. The threat, as typical for its variants, asks the payment of 300 euros and claims to delete all files from the machine completely. It is common for the more recent versions in this family and for other cryptovirus threats, so people think about consequences and pay up more easily.
YOLO ransomware
This was the version released also in January, but it also was the last one detected in the year 2019. The particular YOLO virus team revealed all the information in the ransom note addressed to a particular Blue team since the criminals are the red team. With the particular email contact redteam@yolosecfamework.com. The message:
Greeting and salutations, Blue Team.
Your personal files are deleting. Your company intellictual property is belonging to us now …
But, Red Team is not being so hearless. It will only happen if you don't pay ransom.
However we has encrypting so as not you can access them.
Every 10 minutes we are selects some of them to deleted permanently, therefore we cannot accessing them, either.
While Red Team is being merciful, Red Team is not without limiting patience.
We starts out slowmess then increasing delted files every 10 minutes.
This is to be helping you with the decision to pay ransom and recover datas.
the next a few hundred, and a few thousand, and so on. You are getting the breeze, no?
If you are turning off your computer or closing window, when malware start next time we will 1000 files deleted as way of punishmenting you.
You wil be wanting malware to start next time, since only way that is capable to decrypting your personal datas for you.
Please be sending all payments to redteam@yolosecfamework.com
Also including unique hash in text box below or not know who to decrypted.
Send a picture of the blue team holding sign that say 'Red Team Rules' to:
Btc ransomware
The first one that came out in the year of 2020 for this virus family – Btc files virus that marks files using .btc extension and targets English-speaking users. The typical HTA type file window with the payment system and the money-demanding message. The specific amount of Bitcoin demanded from victims is equivalent to $1499. Criminals claim to delete at least 1000 pieces of data if the person decides to skip the payment. It is crucial to remove the threat, so you can clear the infection and go for the file restoring.
Coin Adder v1.0: a tool used to deliver ransomware
Even though most of the ransomware developers stick to the primary distribution methods, experts have noticed that hackers have changed their technique in December 2016. For the new method, they employed an infamous Bitcoin stealer known as Electrum Coin Adder v1.0.
This tool is capable of stealing Bitcoins only by using a certain transaction ID. However, this tool is only baiting for people who want to earn money the easy way.
It appears that Electrum Coin Adder installs BTC stealer and also downloads and sets up ransomware on the computer. An interesting fact is that this virus has been using an interesting line in its code – config.ActiveAfterDateTime = new DateTime(2016,12,23).
If you were lucky enough to stay virus-free during Christmas, make sure you are relying on safe browsing practices in 2017 as well because this virus brings only sorrow and stress.
Make sure you have an up-to-date anti-malware tool and don't forget to scan your PC before this date if you have downloaded any suspicious programs, opened questionable email attachments, or installed the Electrum Coin Adder virus itself!
Malspam campaigns — the main ransomware attack vector
Going back to the primary distribution techniques, the ransomware is delivered inside the attachments of malicious emails. For this reason, it is important to pay attention during your browsing sessions: do not click on unknown links and avoid downloading software from suspicious websites. Usually, malware disguises as legitimate software, so it is hard to identify it before it's too late.
Try downloading your software only from reliable sources and always check if the downloaded application does not contain additional software waiting to be installed on your PC as well. As for the email, you should carefully inspect the “Spam” section. Do not open any attachments offering to reclaim won iPhone or another common trophy even if they address you directly.
Nevertheless, some rogue programs may slip through to your regular inbox as well, so the best option is to obtain reliable antivirus software to guard you against undesirable programs.
2020 update: in addition to malspam campaigns, ransomware can be distributed with the help of Trojans. The new campaign has been revealed in April pointing to the LokiBot banking trojan, which carries the payload and enables it right after stealing a sufficient amount of the victim's credentials.
The current LokiBot and Jigsaw combination is being distributed via spam emails that carry infected Excel sheets. While the theme and content of the emails may differ, typically attachments are named as follows:
- Swift.xlsx
- Orders.xlsx
- Invoice For Payment.xlsx
- Inquiry.xlsx
Opening an email requires a user's permission to enable Macros, which is, in fact, a user's permission to enable a Trojan. Therefore, before trusting any email with an attachment from an unknown sender it's advisable to scan the attachment or reply to the sender with a question if the attachment is safe to open. If it has been sent by a bot, you will never get the answer.
You can restore encrypted data after you uninstall Jigsaw virus
We understand that the ransomware attack is a frustrating process that might cause you financial losses. Although, you do not need to pay the ransom to regain access to your files. First, you should get rid of the virus, and then you will be able to get a tool for free file decryption[13].
The first thing you should do is go to your Task Manager and kill the firefox.exe and drpbx.exe processes[14]. This should ensure that no more files are deleted from your computer.
Then, run the MSConfig and terminate the firefox.exe startup which initiates the virus. Once the virus startup is terminated, you can use Malwarebytes or SpyHunter 5Combo Cleaner to scan your computer for this malware.
Do not forget to run an extra scan of your system to make sure all of the virus components are completely removed from the computer. Following these steps combined with the Jigsaw removal instructions provided below, should help you to get rid of this treacherous virus safely and without causing damage to your files.
Getting rid of Jigsaw virus. Follow these steps
Important steps to take before you begin malware removal
File encryption and ransomware infection are two independent processes (although the latter would not be possible without the former). However, it is important to understand that malware performs various changes within a Windows operating system, fundamentally changing the way it works.
IMPORTANT for those without backups! →
If you attempt to use security or recovery software immediately, you might permanently damage your files, and even a working decryptor then would not be able to save them.
Before you proceed with the removal instructions below, you should copy the encrypted files onto a separate medium, such as USB flash drive or SSD, and then disconnect them from your computer. Encrypted data does not hold any malicious code, so it is safe to transfer to other devices.
The instructions below might initially seem overwhelming and complicated, but they are not difficult to understand as long as you follow each step in the appropriate order. This comprehensive free guide will help you to handle the malware removal and data recovery process correctly.
If you have any questions, comments, or are having troubles with following the instructions, please do not hesitate to contact us via the Ask Us section.
IMPORTANT! →
It is vital to eliminate malware infection from the computer fully before starting the data recovery process, otherwise ransomware might re-encrypt retrieved files from backups repeatedly.
Scan your system with anti-malware
If you are a victim of ransomware, you should employ anti-malware software for its removal. Some ransomware can self-destruct after the file encryption process is finished. Even in such cases, malware might leave various data-stealing modules or could operate in conjunction with other malicious programs on your device.
SpyHunter 5Combo Cleaner or Malwarebytes can detect and eliminate all ransomware-related files, additional modules, along with other viruses that could be hiding on your system. The security software is really easy to use and does not require any prior IT knowledge to succeed in the malware removal process.
Repair damaged system components
Once a computer is infected with malware, its system is changed to operate differently. For example, an infection can alter the Windows registry database, damage vital bootup and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by malware, antivirus software is not capable of doing anything about it, leaving it just the way it is. Consequently, users might experience performance, stability, and usability issues, to the point where a full Windows reinstall is required.
Therefore, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it is also capable of removing malware that has already broken into the system thanks to several engines used by the program. Besides, the application is also capable of fixing various Windows-related issues that are not caused by malware infections, for example, Blue Screen errors, freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

By employing FortectIntego, you would not have to worry about future computer issues, as most of them could be fixed quickly by performing a full system scan at any time. Most importantly, you could avoid the tedious process of Windows reinstallation in case things go very wrong due to one reason or another.
Restore files using data recovery software
Since many users do not prepare proper data backups prior to being attacked by ransomware, they might often lose access to their files permanently. Paying criminals is also very risky, as they might not fulfill the promises and never send back the required decryption tool.
While this might sound terrible, not all is lost – data recovery software might be able to help you in some situations (it highly depends on the encryption algorithm used, whether ransomware managed to complete the programmed tasks, etc.). Since there are thousands of different ransomware strains, it is immediately impossible to tell whether third-party software will work for you.
Therefore, we suggest trying regardless of which ransomware attacked your computer. Before you begin, several pointers are important while dealing with this situation:
- Since the encrypted data on your computer might permanently be damaged by security or data recovery software, you should first make backups of it – use a USB flash drive or another storage.
- Only attempt to recover your files using this method after you perform a scan with anti-malware software.
Install data recovery software
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

Find a working decryptor for your files
File encryption is a process that is similar to applying a password to a particular file or folder. However, from a technical point of view, encryption is fundamentally different due to its complexity. By using encryption, threat actors use a unique set of alphanumeric characters as a password that can not easily be deciphered if the process is performed correctly.
There are several algorithms that can be used to lock data (whether for good or bad reasons); for example, AES uses the symmetric method of encryption, meaning that the key used to lock and unlock files is the same. Unfortunately, it is only accessible to the attackers who hold it on a remote server – they ask for a payment in exchange for it. This simple principle is what allows ransomware authors to prosper in this illegal business.
While many high-profile ransomware strains such as Djvu or Dharma use immaculate encryption methods, there are plenty of failures that can be observed within the code of some novice malware developers. For example, the keys could be stored locally, which would allow users to regain access to their files without paying. In some cases, ransomware does not even encrypt files due to bugs, although victims might believe the opposite due to the ransom note that shows up right after the infection and data encryption is completed.
Therefore, regardless of which crypto-malware affects your files, you should try to find the relevant decryptor if such exists. Security researchers are in a constant battle against cybercriminals. In some cases, they manage to create a working decryption tool that would allow victims to recover files for free.
Once you have identified which ransomware you are affected by, you should check the following links for a decryptor:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

If you can't find a decryptor that works for you, you should try the alternative methods we list below. Additionally, it is worth mentioning that it sometimes takes years for a working decryption tool to be developed, so there are always hopes for the future.
Create data backups to avoid file loss in the future
One of the many countermeasures for home users against ransomware is data backups. Even if your Windows get corrupted, you can reinstall everything from scratch and retrieve files from backups with minimal losses overall. Most importantly, you would not have to pay cybercriminals and risk your money as well.
Therefore, if you have already dealt with a ransomware attack, we strongly advise you to prepare backups for future use. There are two options available to you:
- Backup on a physical external drive, such as a USB flash drive or external HDD.
- Use cloud storage services.
The first method is not that convenient, however, as backups need to constantly be updated manually – although it is very reliable. Therefore, we highly advise choosing cloud storage instead – it is easy to set up and efficient to sustain. The problem with it is that storage space is limited unless you want to pay for the subscription.
Using Microsoft OneDrive
OneDrive is a built-in tool that comes with every modern Windows version. By default, you get 5 GB of storage that you can use for free. You can increase that storage space, but for a price. Here's how to setup backups for OneDrive:
- Click on the OneDrive icon within your system tray.
- Select Help & Settings > Settings.

- If you don't see your email under the Account tab, you should click Add an account and proceed with the on-screen instructions to set yourself up.

- Once done, move to the Backup tab and click Manage backup.

- Select Desktop, Documents, and Pictures, or a combination of whichever folders you want to backup.
- Press Start backup.

After this, all the files that are imported into the above-mentioned folders will be automatically backed for you. If you want to add other folders or files, you have to do that manually. For that, open File Explorer by pressing Win + E on your keyboard, and then click on the OneDrive icon. You should drag and drop folders you want to backup (or you can use Copy/Paste as well).
Using Google Drive
Google Drive is another great solution for free backups. The good news is that you get as much as 15GB for free by choosing this storage. There are also paid versions available, with significantly more storage to choose from.
You can access Google Drive via the web browser or use a desktop app you can download on the official website. If you want your files to be synced automatically, you will have to download the app, however.
- Download the Google Drive app installer and click on it.

- Wait a few seconds for it to be installed.

- Now click the arrow within your system tray – you should see Google Drive icon there, click it once.

- Click Get Started.

- Enter all the required information – your email/phone, and password.

- Now pick what you want to sync and backup. You can click on Choose Folder to add additional folders to the list.
- Once done, pick Next.

- Now you can select to sync items to be visible on your computer.
- Finally, press Start and wait till the sync is complete. Your files are now being backed up.
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Jigsaw and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Ugnius Kiguolis. LokiBot and Jigsaw tandem spreads via new malspam campaign. 2-Spyware. Virus and spyware news.
- ^ LesVirus. LesVirus. French website about malware and cyber security.
- ^ Jigsaw Ransomware Decryption. Check Point Threat Intelligence and Research.
- ^ Setup_install.exe. VirusTotal. Analyzes suspicious files and URLs to detect types of malware.
- ^ Charlie Osborne. Tick, tock: Jigsaw ransomware deletes your files as you wait. ZDNet. Technology News, Analysis, Comments and Product Reviews for IT Professionals.
- ^ Lucian Constantin. Jigsaw crypto-ransomware deletes more files the longer you delay paying. PCWorld. News, tips and reviews from the experts on PCs, Windows, and more.
- ^ Andrew Barty. Bitcoin the currency of the future: Collection of useful information, secrets and strategies.. Google Books. The world's most comprehensive index of full-text books.
- ^ Michael Gillespie. Twitter.
- ^ Genel Maliyetler.exe file. VirusTotal. A free online service that analyzes files and URLs.
- ^ Lawrence Abrams. We have a Pennywise Jigsaw Ransomware variant that appends .beep. Twitter. Online source for news and communication.
- ^ Michael Gillespie. Another Jigsaw Ransomware with extension. Twitter. Online source for news and communication.
- ^ https://www.virustotal.com/#/file/e59b98bbe5821f5873eac134a1d87f308ba8a0354ae2c7a066c331fc018f03d1. VirusTotal. A free online service that analyzes files and URLs.
- ^ Jigsaw Ransomware Decryption. Check Point Threat Intelligence and Research.
- ^ Mary-Ann Russon. Jigsaw ransomware: Saw-inspired malware deletes files bit by bit hourly until you pay. International Business Times. Provider of business news and current headlines from the US and around the world.


































