French researchers release a free WannaCry decryption tool
WannaCry ransomware shook the entire world on May 12, 2017[1], when cybercriminals used in a massive cyber attack that affected hundreds of thousands computers worldwide. Although the attack was temporarily stopped[2] the next day, attackers quickly fixed the flaw in ransomware's code and continued its distribution. The virus demands $300 in three days or $600 until the deadline – 7th day. If the victim doesn't pay the ransom in a week starting from the day of infection, the virus threatens to delete all files. Therefore, it means that victims who were hit by the ransomware on May 12-13 and haven't deleted the virus yet are trying to decide whether to pay the ransom or not[3]. However, French security researchers from Quarkslab[4] came up with a solution right on time. They have some pretty exciting news for all WannaCry ransomware victims – they have just published their discovery that allows decrypting .WNCRY file extension files for free. The first steps were made by researcher Adrien Guinet[5], who released a tool called WannaKey. The tool works on Windows XP and recovers the RSA key used for data encryption. The utility checks prime numbers in memory to recompute the key rather than searching for an actual one. However, due to a file format issue, the exported key wasn’t compatible with tools like WanaDecrypt (by Benjamin Delpy). However, this didn’t stop researchers from creating WannaCry decryption tool.
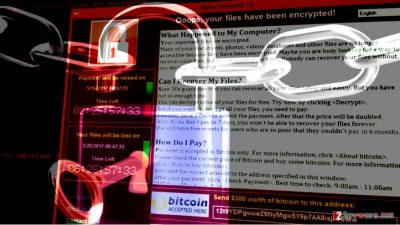
The final tool, which is dubbed WanaKiwi, is Benjamin’s reworked tool that is compatible with Windows XP (x86), Windows 2003 (x86) and Windows 7 (x86). So far it is unclear how the tool works on x64 OS versions. According to the developer Benjamin Delpy, the tool uses the key recovery method used in WannaKey and is based on Wanadecrypt, which gives the following result:
- Wanakiwi recovers private key and saves it as 00000000.dky;
- The private key is used to decrypt all files encrypted by WannaCry.
Of course, the tool is not perfect yet, and there are some limitations. The tool scans the address space of the process that generated the keys, and if such process had been ended by a computer reboot, the original process memory would no longer be available. Therefore, the tool can work only if the infected computer has not been restarted after the infection. Besides, victims should try the decrypter as soon as possible because the prime numbers are only kept in the address space until reused by the process.
If you have been attacked by the infamous ransomware that is also known as Wana Decrypt0r, WannaCrytor or just WNCRY, download WanaKiwi tool right now and try to decrypt your files. The decryptor will not modify the encrypted .WNCRY files but generate the decrypted copies as separate files.
- ^ Julia Carrie Wong, Olivia Solon. Massive ransomware cyber-attack hits nearly 100 countries around the world. The Guardian. News, Sport and Opinion.
- ^ Lily Hay Newman. How an Accidental ‘Kill Switch’ Slowed Friday’s Massive Ransomware Attack. WIRED. In-depth Coverage of Current and Future Trends in Technology.
- ^ Keith Collins. Victims of the WannaCry ransomware attacks have stopped paying up. Quartz. Digital Global Business News Publication.
- ^ Matt Suiche. WannaCry — Decrypting files with WanaKiwi + Demos. Comae Technologies Blog. Posts about IT Security.
- ^ Adrien Guinet. wannakey. GitHub. The World's Leading Software Development Platform.

