ACCDFISA v2.0 ransomware / virus (Removal Guide) - Mar 2018 update
ACCDFISA v2.0 virus Removal Guide
What is ACCDFISA v2.0 ransomware virus?
ACCDFISA v2.0 virus – ransomware that keeps spreading in 2018
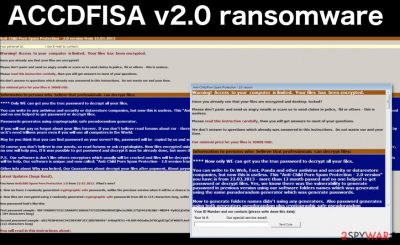
ACCDFISA v2.0 is a dangerous ransomware[1] which is closely related to ACCDFISA virus family. Just like its predecessor, it infiltrates users' devices via Remote Desktop Protocol (RDP) ports. First signs of the malware have been detected in 2016. Though the malware developers provide their own ACCDFISA Decryptor, it is not recommended to use it. Instead, remove ACCDFISA v2.0 as soon as possible. FortectIntego or Malwarebytes might be of service in this process.
After a year of silence, the perpetrators decided to strike again. On October 2017, IT experts[2] detected a hype in virus activity. Several months later, malware is still using brute-force RDP ports to break into target computer systems. Brazil and Spanish[3] users are considered to be primary targets of ACCDFISA v2.0.
Alternatively known as Anti-Child Porn Spam Protection virus, this ransomware operates differently than the majority of threats. It does not employ specific cipher to encode data. In fact, it compresses the targeted files into .rar files and locks them with a password.
Each affected file is transformed into .exe file bearing the name of the original file name, IR number and perpetrator's email address, e.g. filename.format type(!! to get password email id 1449462382 to allhelp16@gmail.com !!).exe. Since ACCDFISA v2.0 is active again, latest version promotes these email addresses that should be used to contact its developers.
- bracode17@gmail.com
- uscodes17@gmail.com
- eucodes17@gmail.com
However, we highly NOT recommend using these email addresses while trying to perform ACCDFISA v2.0 decrypt procedure as there is no guarantee that hackers won't take the money from you and leave you with nothing.
ACCDFISA v2.0: screen locker, crypto-virus and decryptor
Before beginning the encryption process, certain conditions should be fulfilled. Firstly, the malware is downloaded as .rar or .zip folder. It contains a specific script which executes ACCDFISA v2.0 malware. This command also extracts virus components into C:\Windows\System32 folder (in 64-bit systems) or C:\Windows\SysWOW64 (in 32-bit systems). The infection is also known to modify registry files and place multiple of its own files. Some of them are[4]:
- C:\ProgramData\local\svchost.exe
- C:\ProgramData\local\undxkpwvlk.dll
- C:\ProgramData\local\vpkswnhisp.dll
- C:\Decrypt\Decrypt.exe (decryption tool)
Besides modifying the data, Anti-Child Porn Spam Protection malware functions as a screenlocker. Try cancelling it with ALT+F4. In case it does not help, move on to the access recovery instructions found under the last section discussing ACCDFISA v2.0 removal options.
The developers also urge to pay for ACCDFISA Decrypter which would supposedly help you restore affected documents and other important files. Other than considering this possibility, we suggest another data recovery method. 
Decrypting files affected by ACCDFISA v2.0
When you get infected with ransomware viruses, it is no wonder that the first thing that comes to mind is data recovery. At the moment, no security tool has created the decryption tool for this particular version. On other hand, a malware enthusiast by the name of Piotr Karwowski created the the tool which can decode the files modified due to ACCDFISA v2.0 hijack.
Further instructions are provided in the link. Note that you should follow attentively, otherwise, data decryption will be unsuccessful. Some users have reported that the tool helped them recover their files.[5] Before executing the keygen, scan it with the updated anti-virus tool.
Ransomware prevention measures
Since the malware mainly looks for weak RDP passwords, changing them is a necessity.
- During Remote Desktop session, press CTRL+ALT+END key combination. This command launches task menu on the remote server instead of on your local computer.
- Click on Change a Password menu option to alter the password.
This action will decrease the risk of encountering ACCDFISA in the future. Alternatively, be vigilant while surfing the web. Do not download any Flash Player updates promoted in random pages. When downloading a new application, check its reviews in different forums, EULA and privacy policy. Make sure the surce website is secure. Lastly, treat incoming emails with attached supposedly very important invoice and package information notices.
Eliminate ACCDFISA v2.0 virus completely
As we have mentioned previously, there are several ways you can try to recover the files encrypted by ACCDFISA v2.0 ransomware. But what you should be aware before you dive into the data recovery is that the infection must be fully eliminated from your computer before you attempt any of the suggested recovery solutions.
You can remove ACCDFISA v2.0 virus from your computer safely using virus-fighting utilities. Keep in mind, though that ransomware viruses are not your regular browser hijacker or adware infection and may put up a fight before you manage to get rid of them.
In case your antivirus utility struggles with ACCDFISA v2.0 removal, check out the detailed instructions at the end of the article. After you finally get rid of the virus, only then you can try data recovery.
Getting rid of ACCDFISA v2.0 virus. Follow these steps
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove ACCDFISA v2.0 using System Restore
In case Safe Mode did not help access the computer, opt for System Recovery option. Then, you should be able to access the computer and remove ACCDFISA v2.0 virus.
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of ACCDFISA v2.0. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove ACCDFISA v2.0 from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by ACCDFISA v2.0, you can use several methods to restore them:
Data Recovery Pro method
This program might be one of options to restore modified files. Though the software is created for recovering data after a system crash, it might be of service in this case.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by ACCDFISA v2.0 ransomware;
- Restore them.
ACCDFISA v2.0 Decrypter
Here is the link to the above-discussed tool. On other hand, consider the risks of lanching it since it is not an approved program.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from ACCDFISA v2.0 and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Dell Cameron. Ransomware Markets Are Exploding, Study Finds. Gizmodo. We come from the future.
- ^ Toffee. A big-ish ACCDFISA v2.0 campaign targeting Brazil but also some Spanish speaking countries. Usually criminals running this bruted forced RDP. Twitter. Online source for communication and news.
- ^ Eliminate computer threats. Losvirus. Security news and malware removal guidelines.
- ^ Fabian. The ACCDFISA malware family – Ransomware targeting Windows servers. EMSISOFT blog.
- ^ ACCDFISA v2.0 Ransomware Support Topic. BleepingComputer. News, reviews and tech support.





















