Ako ransomware (Virus Removal Instructions) - updated May 2020
Ako virus Removal Guide
What is Ako ransomware?
Ako ransomware is cryptomalware that targets entire networks of businesses and organizations
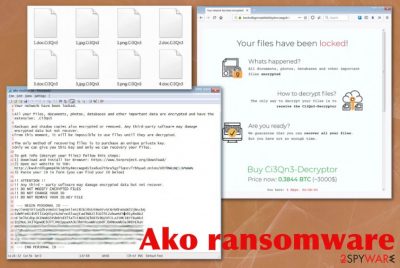
Ako ransomware is the new strain of ransom-demanding threats that mainly targets corporate networks instead of regular consumer machines. Initially discovered after a company's Windows 2011 server of an anonymous company was encrypted, researchers identified it as a new, never-before-seen strain of malware in January 2020. However, it later became clear that malware stems from MedusaLocker. Since then, several versions of Ako ransomware were released, and the attackers took on the data leaking technique, which is employed by all major ransomware operators.
The initial release of Ako ransomware showed the ransom-demanding message and asked victims to contact criminals via email (davidgoldman@cock.li, portedhiggens@firemail.cc). Later, cybercriminals changed the primary communication method that relies on the Tor anonymous network. Both versions deliver the file named ako-readme.txt on the system after the encryption that contains the ransom note, which demands 0.5 – 1 Bitcoin for data release, although this sum can vary from company to company. During encryption, files are appended with a random string of alphanumeric characters.
A few samples detected by victims gave the opportunity for researchers to analyze the threat in-depth.[1] After the investigation, it was discovered that Ako ransomware starts the attack by deleting shadow volume copies, clearing backups, disabling file recovery options, and other security functions. Also, to make matters worse and the file recovery less possible, ransomware is set to create registry entries, alter existing keys, and then start encrypting the targeted data.
| Name | Ako ransomware |
|---|---|
| Symptoms | The virus encodes files and makes them useless, so the ransom gets demanded, and developers can make money from the victim. The threat also alters settings, disables functions and installs other programs on the system to control more than encoded data |
| File marker | Ako makes a random character extension unique for each victim |
| Versions | Two separate versions of the threat got discovered from samples released by victims. (Samples 1[2] and 2[3]) The only difference is that one variant directly redirects to payment site and other offers to contact criminals first |
| Possible relation | Researchers found that the strain is heavily based on MedusaLocker due to similarities in coding, behavior, and ransom notes. However, ransomware developers stated that this is their own creation, not associated with previous ransomware releases |
| Ransom note | ako-readme.txt – a file that delivers initial instructions and possible solutions to victims |
| Ransom amount | The amount asked from victims starts with 0.5 Bitcoin but can go up to 1 BTC and even more |
| Targets | Large businesses, networks of organizations and companies |
| Distribution | The threat most likely infects machines through hacked Remote Desktop services or malicious emails and websites filled with malware |
| Contact emails | davidgoldman@cock.li, portedhiggens@firemail.cc |
| Elimination | You need to remove Ako ransomware with anti-malware tools that can detect the threat itself and clean the machine from applications and files associated with the threat |
| Repair | Since ransomware runs on the machine and disables functions, deletes particular files, you need to change a lot of the settings and fix the damage. When the virus is removed, go through the system with a PC repair look like FortectIntego and make sure that registry entries and system files get recovered and fixed |
Like other cryptocurrency-extortion based threats, Ako virus avoids program files, system data, and application-related files when choosing what to encode. When commonly used data gets encrypted, all files become useless and get marked using the random extension generated to signify which files are affected. Once that is done on the particular machine, the virus performs a scan that shows any devices responding to the network connection, so the whole network can get encrypted.
Ako ransomware places the ransom note on the desktop in the text file named ako-readme.txt that contains URL to the Tor payment site where the ransom payment can get transferred. The page also shows the statement “Your network have been locked” that fully determines the particular target of virus developers -networks.
The said ransom note also has a Personal ID that contains the extension, network configuration settings, encrypted key that is needed for decryption. This ID is required on the Tor site when Ako ransomware victims want to access the payment form and see the particular ransom amount, further instructions. The chat service can also be found these, so the person can submit one file for test decryption.
Ako ransomware ransom message displays the following:
Your network have been locked.
All your files, documents, photos, databases and other important data are encrypted and have the extension: .2Zrl5j
Backups and shadow copies also encrypted or removed. Any third-party software may damage encrypted data but not recover.
From this moment, it will be impossible to use files until they are decrypted.
The only method of recovering files is to purchase an unique private key.
Only we can give you this key and only we can recovery your files.
To get info (decrypt your files) follow this steps:
1) Download and install Tor Browser: https://www.torproject.org/download/
2) Open our website in TOR:xxxx: //kwvhrdibgmmpkhkidrby4mccwqpds5za6uo2thcw5gz75qncv7rbhyad.onion/AHXYFYBKTAXNGRZB
3) Paste your ID in form (you can find your ID below)
!! ATTENTION !!
!! Any third – party software may damage encrypted data but not recover.
!! DO NOT MODIFY ENCRYPTED FILES
!! DO NOT CHANGE YOUR ID
!! DO NOT REMOVE YOUR ID.KEY FILE
— BEGIN PERSONAL ID —
eyJleHQiOiIuMlpybDVqIiwgImtleSI6InozNWRzcEZaOFltMEs0bW4xQVNrZE0
*** [556 characters in total]
— END PERSONAL ID —
Ako ransomware uses the AES encryption algorithm[4] and seems to have no flaws in the coding, so decryption is not possible at the time. However, paying is not recommended because cybercriminals cannot be trusted. Many companies that have suffered such infections before, didn't pay also.[5] If you are related to the company that suffered this attack, rely on professional IT specialist that can recover the network and get rid of the intruder. 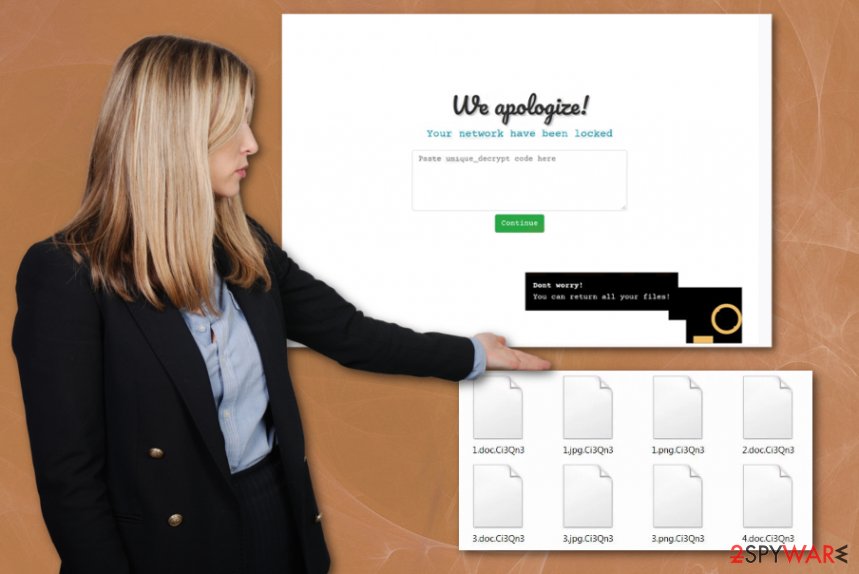
To reverse those changes that Ako cryptovirus have already made on the system, you should rely on the proper antivirus program that can safely delete registry entries, recover affected ones, repair system files, and settings. If you try to make those changes yourself, functions and settings can get damaged further and possibly get unrepairable. Automatic cleaners like FortectIntego, or PC repair tools, system optimizers can do that for you and without causing additional issues.
Even though ransomware creators stated that their target networks only, you as an individual user can also experience such infection on the machine. As for Ako ransomware removal or data recovery, individual machines and networks need to be cleaned from all the traces of the virus before any file restoring.
You can try to remove Ako ransomware with anti-malware tools and run the scan on the network, machine, or particular device to find the virus-related files and malicious programs. After this, data backups are the best option for such encoded data and possibly damaged files. You can find a few more options for file recovery below. 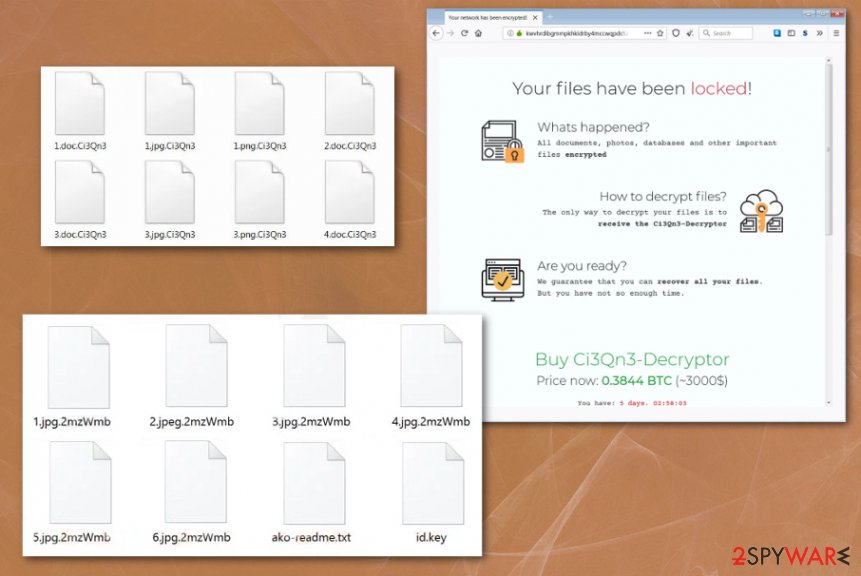
Weakly protected RDP connections – one of the main attack vectors for company-targeting ransomware
Hackers target valuable information that can be accessed by entering the system with the help of devices and tools. When the system is not properly secured, and vulnerabilities allow breaking through the protection, there are bigger chances that machine gets affected by malware like ransomware.
Breaking in the vulnerable network, server, or device becomes easy when RDP hacking is used. It is a common technique used by attackers. Another method used by ransomware developers is payload droppers included on malicious sites or attached as files to emails.
When you receive any suspicious email, pay close attention to important details like the sender, attachments, and typos, or grammar mistakes. Malicious actors pose as companies or services to make people less suspicious. Also, keep the system secured and up-to-date by using system tools, security software, and patch needed flaws more often.
Get rid of Ako ransomware virus from the system
You need to note that the Ako ransomware virus is dangerous and can make other changes on your device besides directly affecting those files during encryption. Many system folders, essential files, and crucial program-related data get directly affected by the threat, so you cannot reverse those setting changes.
You need to remove Ako ransomware completely from the machine, including planted malicious files, installed programs, and other malware that keeps the cryptovirus persistent. This is achievable if you go for proper anti-malware tools and scan the machine fully.
Such Ako ransomware removal method allows detecting all traces and cleaning the machine from the virus. You should note that all those system changes require attention too. Rely on SpyHunter 5Combo Cleaner or Malwarebytes and check the machine for any ransomware traces and virus damage. Then go through methods below that show how to restore files.
Getting rid of Ako virus. Follow these steps
Manual removal using Safe Mode
Reboot the machine in Safe Mode with Networking so you can eliminate Ako ransomware fully
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Ako using System Restore
Ako ransomware termination can be achieved with System Restore feature that allows recovering the machine in a previous state
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Ako. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Ako from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Ako, you can use several methods to restore them:
Recover your files after Ako ransomware encryption using Data Recovery Pro
You can restore encoded data with tools like Data Recovery Pro
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Ako ransomware;
- Restore them.
Windows Previous Versions can help you with encrypted files
When you enable System Restore, Windows Previous Versions can be used to restore Ako virus-encoded data
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer is the possible method for encrypted data
You can use this method when Shadow Volume Copies are not affected by the ransomware
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Ako ransomware is not decryptable yet
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Ako and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Abeerah Hashim. One more threat for organizations - the Ako ransomware. Latesthackingnews. Cybersecurity news.
- ^ Malware sample No.1 detection. VirusTotal. Online malware scanner.
- ^ Malware sample No.2 detection. VirusTotal. Online malware scanner.
- ^ Advanced Encryption Standard. Wikipedia. The free encyclopedia.
- ^ Jeff Adelson. New Orleans still struggling to recover from ransomware attack. Securityinfowatch. Security news and insights.





















