Antivirus 360 (Removal Guide) - Free Instructions
Antivirus 360 Removal Guide
What is Antivirus 360?
Antivirus 360 – a fake antispyware program with evil intent
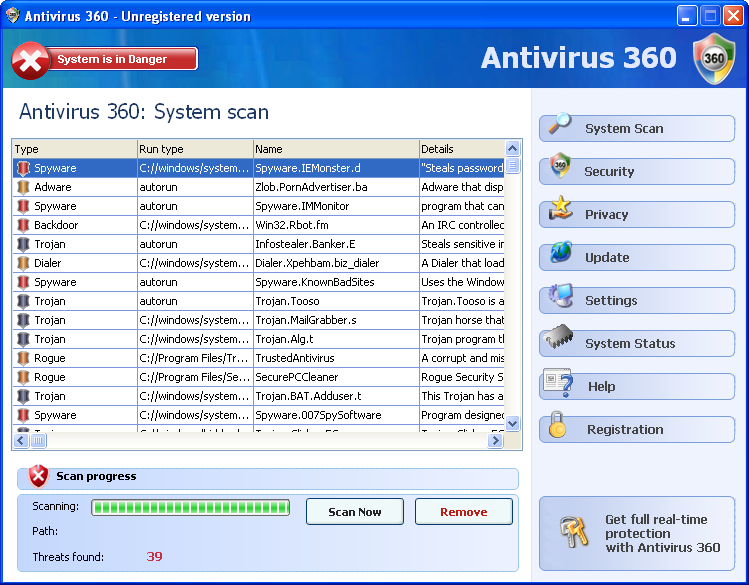
Antivirus 360 is a rogue system tool. Like many of its kind, this parasite tries to push users into purchasing a licensed version with falsified threats. Its name sounds very similar to the respected security tool Norton 360 developed by Symantec. The application makes its own way into the user’s computer via Trojan Zlob or by manual download.
This potentially unwanted program floods users with numerous pop-ups with imaginary virus infections and system risks after installation. Afterward, Antivirus360 advertises itself as an effective program that is able to fix all these fake problems, and of course, you have to pay for it. Please don't install this fake anti-malware tool, or if you already did – remove it with our instructions below.
| name | Antivirus 360 |
|---|---|
| Type | PUP, rogue antispyware tool, fake anti-malware software |
| Purpose | Convince users to purchase its paid version by showing misleading notifications and predetermined scan results |
| Risks | Malware infections, privacy issues, monetary losses |
| Distribution | Deceptive ads, freeware, Trojans, fake Flash Player updates, software bundles |
| Elimination | Remove this worthless program by running a full system scan with proper, time-proven anti-malware software |
| System repair | After any infection removal, a system tune-up is in order. Do it with the powerful FortectIntego system diagnostics tool to ensure your device runs smoothly |
This software is very dangerous, as it marks Windows files as infectious or serious threats. The main purpose of it is to show deceptive pop-ups and draw out money. It wasn't created to stop malware or PUPs. As a parasite, Antivirus360 can cause many serious problems for users: slow down computers, limit the internet connection, corrupt system files, infect the device with malware, etc.
Thus Windows computer users should never download or install this fake antispyware software. Unfortunately, it can be installed on your device without your direct consent through Trojans, software bundles, and other sneaky techniques used by threat actors.
If you spotted that Antivirus 360 virus is appeared on your device out of nowhere, or you've installed it willingly, please remove the cyber threat immediately. We recommend you scan your system with reputable anti-malware software such as SpyHunter 5Combo Cleaner or Malwarebytes to safely and forever eliminate this fake antispyware tool.
Once the removal is finished, you must perform a system tune-up to revert any damage that your device's system files and settings sustained from the PUP. You can entrust the robust FortectIntego system diagnostics tool will this task as it will repair any system-related inconsistencies automatically and within minutes.
Fake Flash Player updates spread PUPs and malware
Cybercriminals have lots of ways to infect your device with their vile creations, including software bundling, file-sharing platforms, deceptive ads, drive-by downloads, etc. But one of the most popularly used methods is camouflaging PUPs and malware as Flash Player updates.
Pop-ups suggesting that you need to install or update this software can be encountered on high-risk, questionable, or hacked sites. If you ever see such a pop-up, please don't believe it, as the support for Flash Player was ceased late last year. Close the tab, clear your browsing history and cookies, and never visit that page again.
Remove Antivirus 360 virus with proper anti-malware software
Fake spyware tools can do a lot of harm to you and your device by leaving it unprotected and vulnerable to various cyber threats, like Trojans, ransomware, keyloggers, etc. Thus we advise not installing or removing Antivirus 360 immediately. The best way to do it is to use a time-proven security tool.
Perform a full system scan, and the threat should be identified and removed automatically. If the article's culprit prevents you from launching a new AV engine, do that in Safe Mode. Please run system diagnostics to undo any changes the infection might have caused to system directories and settings when all is said and done.
You may remove virus damage with a help of FortectIntego. SpyHunter 5Combo Cleaner and Malwarebytes are recommended to detect potentially unwanted programs and viruses with all their files and registry entries that are related to them.
Getting rid of Antivirus 360. Follow these steps
Uninstall from Windows
Instructions for Windows 10/8 machines:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

If you are Windows 7/XP user, proceed with the following instructions:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.

- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
After uninstalling this potentially unwanted program (PUP) and fixing each of your web browsers, we recommend you to scan your PC system with a reputable anti-spyware. This will help you to get rid of Antivirus 360 registry traces and will also identify related parasites or possible malware infections on your computer. For that you can use our top-rated malware remover: FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting rogue antispyware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
