Asd ransomware (Virus Removal Guide) - Recovery Instructions Included
Asd virus Removal Guide
What is Asd ransomware?
Asd ransomware is a computer infection that blocks access of all personal files on the infected computers and demands a ransom in Bitcoins
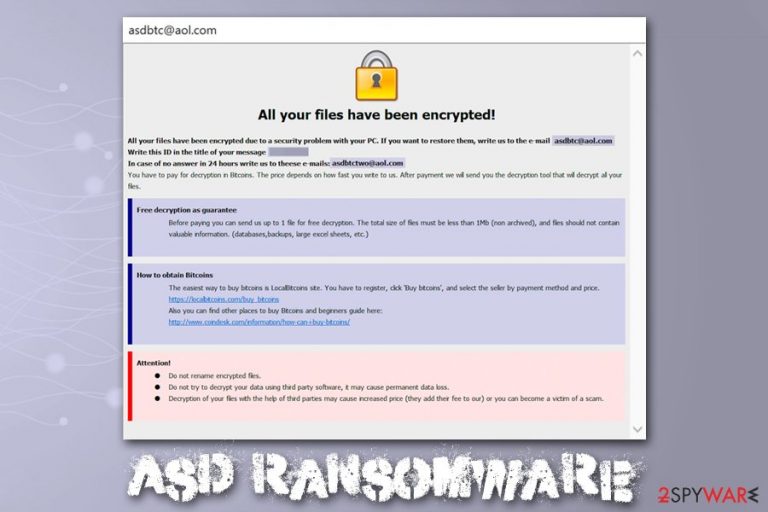
Asd ransomware is malware that focuses on money extortion by encrypting all personal files on the targeted Windows systems. Suchlike modified files can no longer be accessed, and are marked with .asd file extension, among other changes that are performed to data. To retrieve access to files, victims require an AES and RSA-generated key that is only accessible to cybercriminals. As evident, hackers ask for Bitcoins for the Asd ransomware decryptor, although the precise sum is not provided.
To explain the situation more clearly to victims, Asd ransomware developers provide a ransom note which is dropped in two formats – FILES ENCRYPTED.txt, as well as a .hta file. These notes also contain contact details of cybercriminals – asdbtc@aol.com and asdbtctwo@aol.com – which can be used for Asd ransomware decryptor price negotiation.
| Name | Asd ransomware |
| Type | Cryptomalware, File locking virus |
| Family | Malware belongs to one of the leading ransomware families – Dharma/Crysis |
| Distribution | Most commonly used distribution methods include malicious spam email attachments, Remote Desktop intrusions, as well as pirated software installers and cracks |
| File extension | Each of non-system and non-executable files are appended with .id-[ID].[asdbtc@aol.com].asd file extension. Example of an encrypted file: filename.jpg.id-3T743R20.[asdbtc@aol.com].asd |
| Ransom note | Two ransom notes are dropped folders where locked files are located – FILES ENCRYPTED.txt and info.hta |
| Contact | For ransom negotiation purposes, cybercriminals provide two email addresses: asdbtc@aol.com and asdbtctwo@aol.com |
| File decryption | The only secure method to decrypt files is by using data backups prepared prior to the infection. Other methods include using third-party recovery software or paying cybercriminals – the latter is risky. |
| Virus removal | To delete malicious software safely from the computer, access Safe Mode and perform a full system scan with powerful anti-malware software |
| OS recovery | Ransomware not only encrypts all personal files on the system but also changes various settings and intercepts system files. After malware removal, you might experience system crashes or errors because of that. To remediate your Windows OS, scan it with FortectIntego |
The Asd virus derived from one of the most prominent families – Dharma/Crysis and was first spotted by researcher Jakub Kroustek in the first half of December 2019. Victims who previously paid ransom for the decryption tool said that malware authors often ask for extra money after payment, so trusting them is not recommended. Before using alternative file recovery solutions, users should backup the encrypted files and remove Asd ransomware from their computers.
Asd ransomware operation and file encryption specifics
It is important to note that Asd ransomware also makes several changes to the host machine after the intrusion, which usually happens after users open a malicious spam email attachment, do not protect their RDP connections, or downloading software crack like KMSpico or a fake installer. Nevertheless, hackers might use other attack vectors for propagation to increase the infection rate.
As ransomware performs the following changes to the system:
- Deletes all Shadow Volume Copies with the help of “vssadmin delete shadows /all /quiet” command;
- Modifies Windows registry to enable boot every time Windows is launched;
- Contacts a C2 server and delivers computer's name and some other information;
- In some cases, uninstalls security software to complicate Asd ransomware removal.
Once all the preparations are complete, the malware starts its encryption routine by using a combination of AES and RSA ciphers, which makes it even more difficult to break (in fact, the algorithm used in the newest versions is so strong that many security experts say that decrypting them is impossible,[1] as it would require thousands of years of mathematical calculations performed by the most advanced computers). Only system and malware files are skipped by Asd ransomware – everything else gets encrypted and becomes inaccessible.
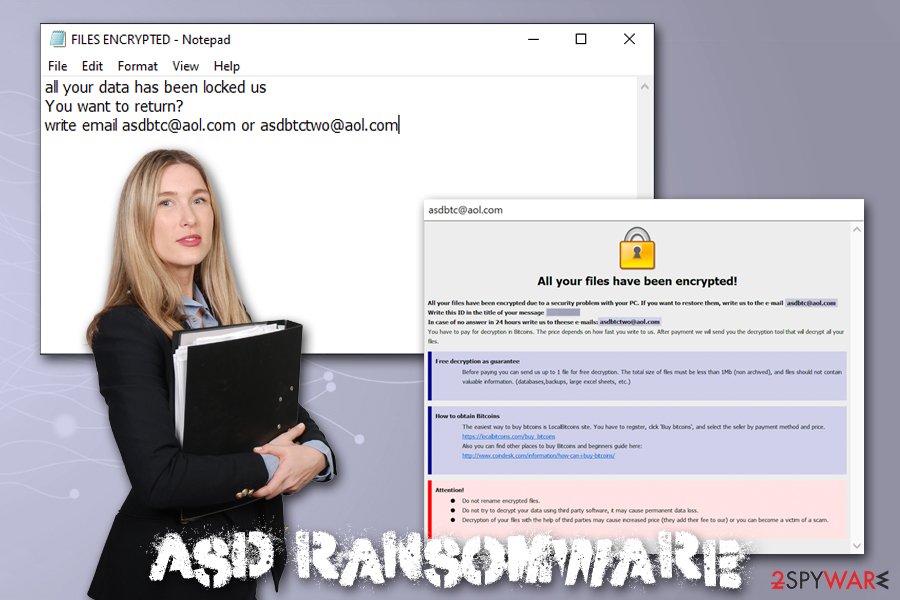
The message in the shorter version of the Asd virus ransom note states:
all your data has been locked us
You want to return?
write email asdbtc@aol.com or asdbtctwo@aol.com
Far more details are included in the other ransom note – it indicates that users might send one file for test decryption to ensure that Asd ransomware decryptor works. However, experts[2] advise not to trust cybercriminals, as they might send a fake tool, or might ask for more money.
The ransom size is never provided by any Dharma versions, as the amount highly depends on various factors, such as if the infected computer comes from an organization or is a regular user, as well as how soon victims contact attackers. In the known cases, companies were asked for around 1 BTC, while regular users might be asked for a much smaller sum.
If you happened to be a victim of Asd ransomware, you should make a copy of all the encrypted files and then terminate the infection. Alternative methods for file recovery are listed in the recovery section below, although you should be aware that chances for successful decryption are low. In case you have problems post-termination and Windows are crashing or returning errors, you should perform a scan with FortectIntego – it will remove virus damage, and you will not have to reinstall the OS.
Perform necessary protection steps to avoid ransomware attacks
Dharma/Crysis ransomware is so prevalent due to the distribution methods that the attackers use. While some malware families like Djvu stick to pirated software installers, others employ a variety of attack vectors to ensure a large number of infections, consequently increasing the chances of victims paying the ransom. Unfortunately, it also increases hackers' will to make new viruses, as it is simply profitable – this is why ransomware has been on the rise in 2018 and 2019.[3]
Therefore, the best way to stop cybercriminals is not to get infected with ransomware in the first place. Here are the most used distribution methods of Dharma developers:
- Spam email attachments and hyperlinks. In some cases, hackers use double file extensions to make it look like the attached file is not executable. Additionally, it was also observed that malicious actors insert hyperlinks that lead to self-extracting and password-protected file, which also includes the installer of a well-known anti-virus vendor, diminishing the suspicions for recipients. To mitigate the attack, treat each email with suspicion and never open attachments or click on links unless you are sure that the email came from a legitimate source.
- RDP connections. Malware developers often abuse Remote Desktops that use a default TCP port 3389 and apply leaked credentials to access the machine remotely.[4] After the intrusion, they install malware manually, sometimes uninstalling anti-malware solutions in the process. To stop RDP-based attacks, you should use a different RCP port and use a strong password.
- Fake installers. Malicious actors also use fake copies of anti-virus or other trusted software in order to trick users into opening the executable. These files are usually distributed via various third-party software hosting sites as well as shared networks. To avoid fake versions of programs, you should only rely on executables coming from official websites.
As the primary countermeasure to ransomware, you should backup all their important files on a regular basis.
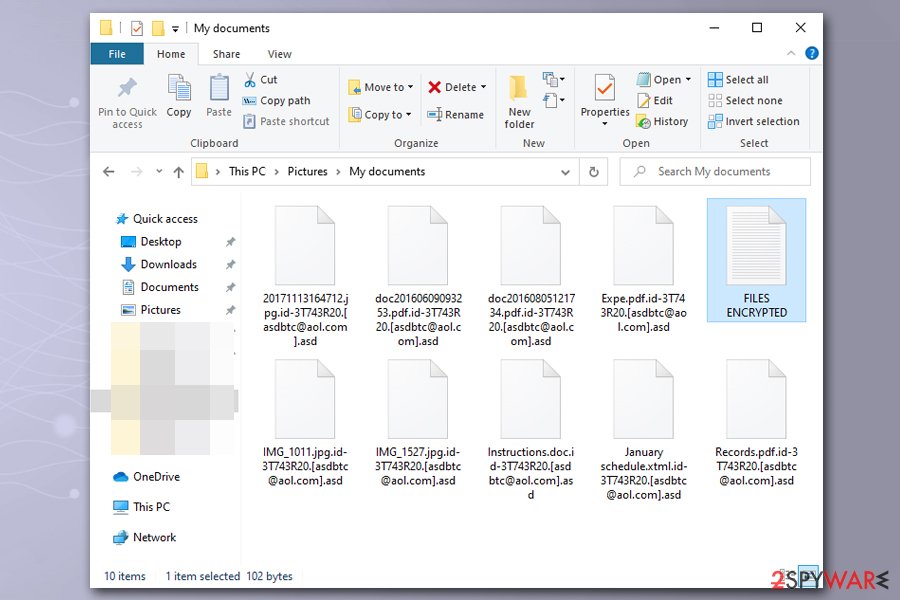
Before removing Asd ransomware, backup the encrypted files
While Asd ransomware removal is one of the first step that is required towards the recovery after the infection, you should also take into consideration your locked files. Unlike other malware, ransomware does not decrypt data after it is removed. In fact, deleting malware might sometimes damage files beyond repair and will render them permanently damaged. To avoid that, you should backup all the locked data before you uninstall Asd ransomware.
To remove Asd ransomware, you need to perform a full system scan with anti-malware software – you can try using SpyHunter 5Combo Cleaner or Malwarebytes, although any other reputable malware removal tool should suffice. If you are having troubles and the virus stops your security tool from working, access Safe Mode with Networking as explained below.
After you get rid of Asd virus, you can then attempt file recovery. Unfortunately, there is no working decryption tool created for this version of Dharma, so the only way to retrieve data is by using third-party recovery software or Windows Previous Versions feature. Note that chances of retrieving files using these methods are low, although it is not impossible. The less you use your computer post ransomware infection, the bigger the chances you can restore at least some of your data with recovery tools.
Getting rid of Asd virus. Follow these steps
Manual removal using Safe Mode
In case malware is tampering with your security software, access Safe Mode with Networking:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Asd using System Restore
System Restore can be used to delete malware:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Asd. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Asd from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Asd, you can use several methods to restore them:
Data Recovery Pro method might be efficient in some cases
Data Recovery Pro might be able to extract working copies of Asd ransomware encrypted files from your hard drive.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Asd ransomware;
- Restore them.
Try out Windows Previous Versions Feature
This method will only work if you had System Restore enabled before the virus attack.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer might be the best solution
ShadowExplorer should help if Shadow Volume Copies were not deleted for some reason.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Do decryption tool is currently available
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Asd and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Bill Toulas. Dharma/Crysis Ransomware File Decryption Scams on the Rise. TechNadu. Tech and news site.
- ^ Lesvirus. Lesvirus. Cybersecurity news and articles from France.
- ^ Brien Posey. Why Enterprise Ransomware Attacks Are on the Rise. ITPro Today. Professional insights of IT industry.
- ^ RDP Hacking: How Hackers Enter Remote Desktops & How to Be Safe. RemoteControl. Security-focused site.







