Audacity.de virus (Removal Instructions) - Free Guide
Audacity.de virus Removal Guide
What is Audacity.de virus?
Audacity.de virus is the page that leads to suspicious file installations instead of the legitimate program
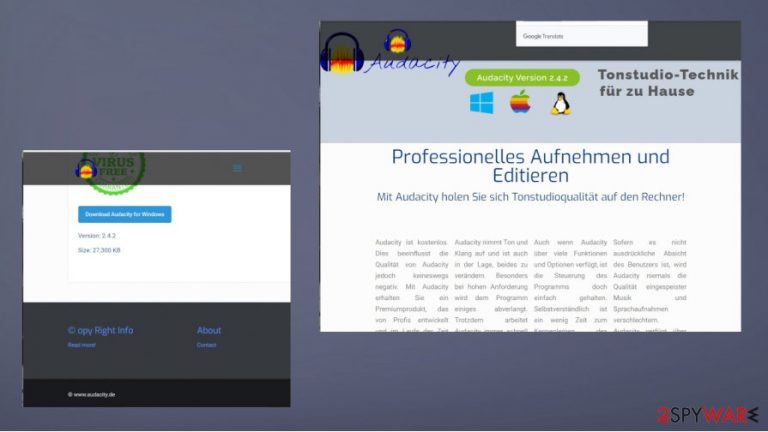
Audacity.de is one of the different sites that redirect users to shady platforms and promote legitimate installations of programs like Audacity. It promotes and claims to distribute the official product. However, this site is not delivering the real files and programs. Users[1] complain all over the internet forums about the malware of various types that end up installed instead of the wanted application.
It is a Germany-based site, but there are various versions of the same page with different area redirects like Audacity.fr. The false installer comes as a virus, and various AV tools, security software indicate the executable other files as trojans, PUPs, other types of infections. This activity leaves people scared and frustrated. Especially when some reports state[2] that links to suspicious sites came directly from official sources.
This issue is serious because people get tricked into thinking that their devices got affected by the company, real program file. This is how names of legitimate platforms, social media, applications get wrecked. Audacity is not a virus, and the program is safe to use. Unfortunately, the name of the legit software and the company got used to spreading malware. You can encounter various Audacity virus pages and get redirected to a malicious download page out of nowhere. We offer a few methods below that can help you remove any infection from the machine and get more in-depth about these possible intruders in this article.
| Name | Audacity.de virus |
|---|---|
| Type | Fake download site |
| Possible symptoms | The page itself can look legitimate enough, so people don't question the source of the application, but the malware gets installed instead of the real program. Particular symptoms and issues created on the machine depend on the type of infection. Specific trojan and PUP indications listed below |
| Issues | The rogue site uses the name of a legitimate application and diminishes the trust with the official tool |
| Similar malicious campaigns | You can find sites that promote and provide adware instead of these legitimate apps like 7Zip, Paint.net, Inkscape, Scribus, GParted, Celestia, ABlock |
| Danger | Trojans and more severe malware can damage the machine and even lead to losses of money or files |
| Distribution | Various tactics get used. You might end up redirected to this site or visit the page when tricked by the identical features compared to the official site |
| Elimination | You need to remove Audacity.de virus by running a thorough AV tool on the machine. Further steps are needed but differ based on the type of infection. Instructions can be found below |
| Repair | System damage is likely because silent threats can trigger various processes in the background. Make sure to clear infections and repair any issues using FortectIntego |
When people get the Audacity.de virus, those detections appear out of nowhere because users have no idea that the install is malicious and not official or legitimate. People state that AV tools stop the download process or indicate the threat once the program is already installed. Those misleading sites can sometimes trigger downloads, and AV tools do not detect any issues.
You should be concerned if the process of file or program download is blocked by the security tool. It is possible that AV tools deliver false positives, but be suspicious to avoid Audacity.de virus infection or any other threats. Unfortunately, there are many researchers that report such fake sites that promote downloads of programs when in reality, people get adware or more crucial threats.
People that report encountering the need to remove Audacity.de virus from their devices state that malicious files indicate detections with PUP.Optional motives or even Trojan.Agent and similar heuristic names. These infections that users get from rogue sites or download platforms and misleading pages can display some symptoms or none at all. It depends on the type, and the time a particular infection runs on the machine.
There are various system issues that these threats can create, so you might need to run FortectIntego to repair altered functions. Audacity.de virus might also disable some programs needed for the system security, so you can benefit from Safe Mode and other options listed below.
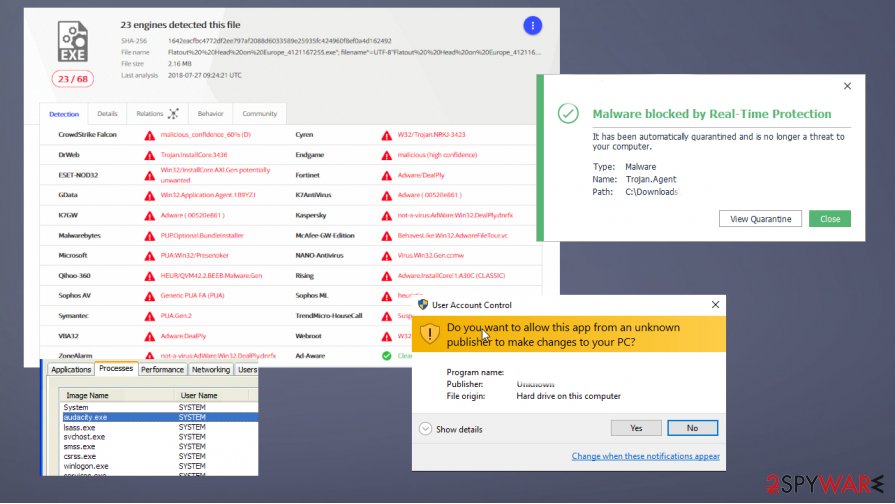
Some of the symptoms that trojans and more dangerous threats can display:
- disabled AV tools or different programs;
- crashes, freezes, or BSOD errors;
- installations of different apps;
- increased usage of resources.
You can find additional issues with your web browsing tools and online activities. If you find browsing online difficult and redirect filling your screen, you might have a PUP-type intruder. It is easier to perform Audacity.de virus removal when the program is freshly installed, so you need to run tools like SpyHunter 5Combo Cleaner or Malwarebytes as soon as possible, so you can eliminate the infection fully.
There is a possibility that you end up with the Audacity.de virus infection by visiting the clone website that triggered the legitimate-looking download of the tool you need and intended to install. Experts[3] always talk about those issues with sites that mislead users by showing material resembling the real download sites and platforms.
The malicious PUPs and trojans from Audacity.de can infiltrate the system without users' interaction, unfortunately. It is important to note that there are various versions of such sites and other rogue platforms that show various misleading material to trick people into downloading executables, installation packages.
Pay attention to details like the version of the application you search for and particular domain names, typos there, and redirects caused immediately after visitation. The official site for Audacity products is audacityteam.org.
Fake downloader sites with misleading material trigger many silent processes
There are tons of p2p platforms,[4] other sites and services that rely on providing versions of legitimate programs and applications online. However, there are many sites involved in adware delivery campaigns that use legitimate programs and clones official domains to trick people into installing popular applications that are, in fact PUPs or even more dangerous threats.
These sites can be used to spread silent infections without the use of bundling or other third-party offers that PUP developers commonly use. You might still see offers and accept them or decline when installing the program. Tons of such websites have been discovered over the years, so you can encounter these malicious pages without even knowing.
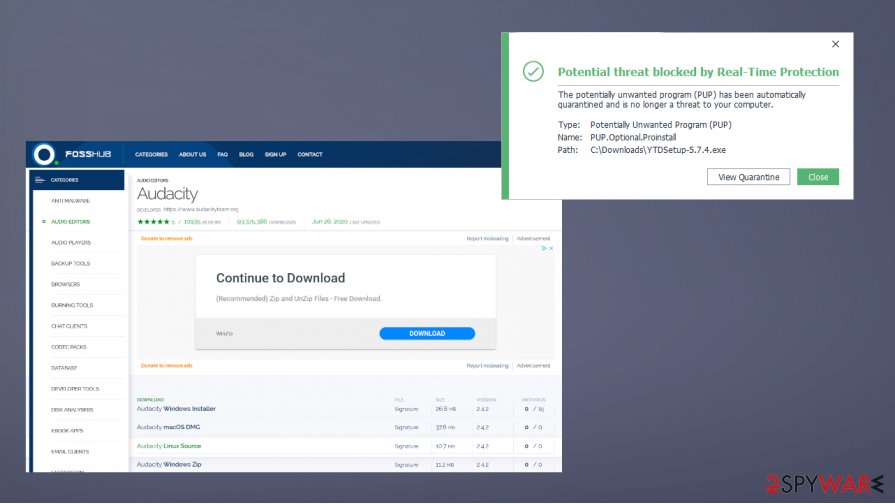
Make sure to avoid any sites with .fr; .de; .es register TLDs. Contents can be in various languages too, so these adware-infested apps get pushed around the world. Be suspicious and cautious. Stay away from the installation if a pop-up like this occurs:
“Unknown Publisher. This file does not have a valid digital signature that verifies its publisher”
Make sure to clear any traces of the Audacity.de virus by running a professional anti-malware tool
Audacity.de virus removal procedure is important. Fors of all, do not think that the Audacity program its developers have anything to do with this issue. There are many fake downloader pages that push adware or even other rogue tools, programs, malicious software.
You can be saved from the threat and remove Audacity.de virus by running a tool like an anti-malware tool, security software. Applications like SpyHunter 5Combo Cleaner or Malwarebytes can run through various parts of the machine and indicate threats that affect your machine. Fortunately, this installer gets detected by AV tools, so people can run those applications and clear possible infections easily.
The issue with this Audacity virus is not related to any legitimate sources or developers of the known audio editing program. So do not panic and think that the application is related to these infection issues. It is a harmful campaign using the name of the safe-to-use tool. make sure to get rid of any pieces and possibly additional threats and rely on FortectIntego, AV tools, and instructions that show how to properly eliminate malware and reset browsers if those get affected.
Getting rid of Audacity.de virus. Follow these steps
Uninstall from Windows
Instructions for Windows 10/8 machines:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

If you are Windows 7/XP user, proceed with the following instructions:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.

- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Delete from macOS
Remove items from Applications folder:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

Remove from Microsoft Edge
Delete unwanted extensions from MS Edge:
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.

Clear cookies and other browser data:
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.

Restore new tab and homepage settings:
- Click the menu icon and choose Settings.
- Then find On startup section.
- Click Disable if you found any suspicious domain.
Reset MS Edge if the above steps did not work:
- Press on Ctrl + Shift + Esc to open Task Manager.
- Click on More details arrow at the bottom of the window.
- Select Details tab.
- Now scroll down and locate every entry with Microsoft Edge name in it. Right-click on each of them and select End Task to stop MS Edge from running.

If this solution failed to help you, you need to use an advanced Edge reset method. Note that you need to backup your data before proceeding.
- Find the following folder on your computer: C:\\Users\\%username%\\AppData\\Local\\Packages\\Microsoft.MicrosoftEdge_8wekyb3d8bbwe.
- Press Ctrl + A on your keyboard to select all folders.
- Right-click on them and pick Delete

- Now right-click on the Start button and pick Windows PowerShell (Admin).
- When the new window opens, copy and paste the following command, and then press Enter:
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register “$($_.InstallLocation)\\AppXManifest.xml” -Verbose

Instructions for Chromium-based Edge
Delete extensions from MS Edge (Chromium):
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.

Clear cache and site data:
- Click on Menu and go to Settings.
- Select Privacy, search and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

Reset Chromium-based MS Edge:
- Click on Menu and select Settings.
- On the left side, pick Reset settings.
- Select Restore settings to their default values.
- Confirm with Reset.

Remove from Mozilla Firefox (FF)
Remove dangerous extensions:
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

Reset the homepage:
- Click three horizontal lines at the top right corner to open the menu.
- Choose Options.
- Under Home options, enter your preferred site that will open every time you newly open the Mozilla Firefox.
Clear cookies and site data:
- Click Menu and pick Settings.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

Reset Mozilla Firefox
If clearing the browser as explained above did not help, reset Mozilla Firefox:
- Open Mozilla Firefox browser and click the Menu.
- Go to Help and then choose Troubleshooting Information.

- Under Give Firefox a tune up section, click on Refresh Firefox…
- Once the pop-up shows up, confirm the action by pressing on Refresh Firefox.

Remove from Google Chrome
Delete malicious extensions from Google Chrome:
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Clear cache and web data from Chrome:
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Change your homepage:
- Click menu and choose Settings.
- Look for a suspicious site in the On startup section.
- Click on Open a specific or set of pages and click on three dots to find the Remove option.
Reset Google Chrome:
If the previous methods did not help you, reset Google Chrome to eliminate all the unwanted components:
- Click on Menu and select Settings.
- In the Settings, scroll down and click Advanced.
- Scroll down and locate Reset and clean up section.
- Now click Restore settings to their original defaults.
- Confirm with Reset settings.

Delete from Safari
Remove unwanted extensions from Safari:
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Clear cookies and other website data from Safari:
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

Reset Safari if the above-mentioned steps did not help you:
- Click Safari > Preferences…
- Go to Advanced tab.
- Tick the Show Develop menu in menu bar.
- From the menu bar, click Develop, and then select Empty Caches.

Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Audacity.de using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Audacity.de. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
How to prevent from getting viruses
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Audacity.de virus?. Gutefrage. Online community.
- ^ Audacity 2.4.2 download infected with Trojan virus [SOLVED]. Audacityteam. Official forum for Audactity users.
- ^ Avirus. AVirrus. Spyware related news.
- ^ p2p. Wikipedia. The free encyclopedia.







