BNFD ransomware (Virus Removal Instructions) - Virus Removal Guide
BNFD virus Removal Guide
What is BNFD ransomware?
BNFD ransomware – cryptovirus using double military grade algorithms to encrypt victim personal data

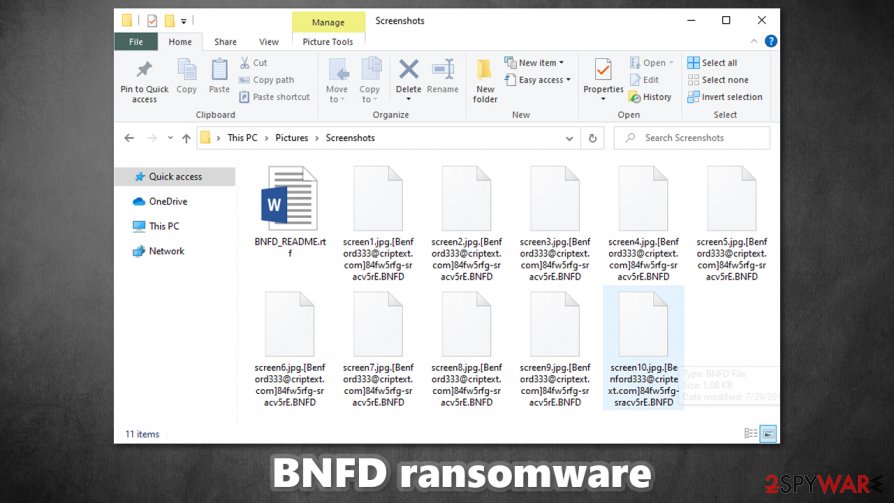
BNFD ransomware is a new cryptovirus from the Matrix ransomware family. BNFD virus' purpose is to encrypt[1] users' personal data, with military strength algorithms (AES-256 and RSA-2048), upon gaining access to the device and demand a ransom for decryption. This malware appends all non-system files with a three-part extension:
- criminal contact email in brackets – [Benford333@criptext.com]
- sequence of random characters
- and an extension – .BNFD
After the encryption is complete, a ransom note, named BNFD_README.rtf, is created. In the message, the cybercriminals state that the victims' files have been encoded and that they're the only ones that can undo this. Three email addresses are given to get in touch with the perpetrators, and owners of the contaminated devices should write to all of them instantly. Also, a unique ID is prescribed to each victim. As a gesture of good faith, the perps are offering to send them three files for a free decryption, thus proving that the decryption tool/key exists. Neither the amount of the ransom nor the probable crypto wallet isn't provided in the note.
| name | BNFD virus, BNFD ransomware, .BNDF malware |
|---|---|
| Type | Malware, Cryptoware, Ransomware |
| Family | Matrix ransomware family |
| Appended extension | All non-system files appended with three-part extensions – criminal contact email in brackets, sequence of random characters and an .BNFD extension, e.g., [Benford333@criptext.com].01234567890qwerty.BNFD |
| Ransom note | BNFD_README.rtf |
| Criminal contact details | Three emails are provided: Benford333@criptext.com, Benford333@protonmail.com, Benford333@tutanota.com |
| distribution | File-sharing platforms, spam email campaigns |
| removal | BNFD virus removal should be trusted to professionals like SpyHunter 5Combo Cleaner or Malwarebytes |
| system fix | Malware potentially does altercations to system files. We strongly advise using FortectIntego tool to automatically find and fix any changes done by the virus |
Even though contacting the cybercriminals and meeting their demands might seem like the only option to regain access to locked files, sit down and rethink what you might be getting yourself into. There are numerous cases that after the victims have paid the ransom – nothing happened, i.e., creators of the ransomware didn't send the promised decryption tool/key.[2]
Nowadays, it is strongly recommended to keep backups of sensitive information. In case of a cyberthief attack, information in an offline storage device would be safe. Also, to have a reliable anti-malware software that would detect and remove BNFD virus and malware alike.
BNFD ransomware removal might still be not enough for users' to fully enjoy their device. Matrix family ransomware is known to mess up computer system files, leading to devices irregular work. Experts[3] also advise using FortectIntego to automatically find and restore what the virus has done to your system files and system settings.

Ransom note, in BNFD_README.rtf, contains this message:
ALL YOUR VALUABLE DATA WAS ENCRYPTED!
All yоur filеs wеrе еnсrуptеd with strоng crуptо аlgоrithm АЕS-256 + RSА-2048.
Plеаsе bе surе thаt yоur filеs аrе nоt brоkеn аnd уоu cаn rеstоrе thеm tоdаy.If yоu rеаllу wаnt tо rеstоrе yоur filеs plеаsе writе us tо thе е-mаils:
Benford333@criptext.com
Benford333@protonmail.com
Benford333@tutanota.com
In subjеct linе writе уоur ID: –Impоrtаnt! Plеаsе sеnd yоur mеssаgе tо аll оf оur 3 е-mаil аddrеssеs. This is rеаllу impоrtаnt bеcаusе оf dеlivеrу prоblеms оf sоmе mаil sеrviсеs!
Important! If you haven't received a response from us within 24 hours, please try to use a different email service (Gmail, Yahoo, AOL, etc).
Important! Please check your SPAM folder each time you wait for our response! If you find our email in the SPAM folder please move it to your Inbox.
Important! We are always in touch and ready to help you as soon as possible!Аttаch up tо 3 smаll еncrуptеd filеs fоr frее tеst dесryption. Plеаsе nоte thаt thе filеs yоu sеnd us shоuld nоt cоntаin аnу vаluаblе infоrmаtiоn. Wе will sеnd yоu tеst dеcrуptеd files in оur rеspоnsе fоr yоur cоnfidеnсе.
Of course you will receive all the necessary instructions hоw tо dеcrуpt yоur filеs!Important!
Plеаsе nоte that we are professionals and just doing our job!
Please dо nоt wаstе thе timе аnd dо nоt trу to dесеive us – it will rеsult оnly priсе incrеаsе!
Wе аrе alwауs оpеnеd fоr diаlоg аnd rеаdy tо hеlp уоu.
Cybercriminals' creative ways of spreading their infections
Cybercriminals are a malicious but a creative bunch. They tend to camouflage their “products” as totally legit, inconspicuous files on file-sharing platforms, such as torrent sites or social media platforms. Unaware users might think that they're downloading some game cheat codes or a “crack”, when actually their computers are about to be infected.
Email spam is another popular way for cyberthieves to catch unsuspecting people. Soon to be victims don't realize that by opening a mischievous email attachment without scanning it with a powerful anti-malware tool first, they're getting themselves a major headache.
These are just a few methods the cybercriminals are using. There are plenty more naughty ways at their disposal. To stay safe, people should always use powerful antivirus software and always keep backups.
Instructions for BNFD virus removal
The longer the ransomware stays on users' device, the more harm it could do. BNFD virus removal should be almost the the first action after it is detected by anti-malware software. However, if you have no backups to restore your data from, we recommend you make a copy of your most valuable encrypted data.
To remove BNFD ransomware, use SpyHunter 5Combo Cleaner or Malwarebytes. It will automatically allocate the ransomware and all its files, isolate and remove them. Do the same thing if no such software was on the device. These trustworthy apps will protect your device from future attacks.
Matrix ransomware family viruses are known to damage, mess up, and modify computer system files. These altercations will cause the user device to exhibit abnormal behavior, such as overheating, extreme lag, crashes, etc. To restore the changes made by the virus, with a push of a button, use the FortectIntego tool as it will automatically find and repair all affected system files.
Getting rid of BNFD virus. Follow these steps
Manual removal using Safe Mode
Access Safe Mode with Networking and perform a full system scan from there:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove BNFD using System Restore
In some cases, System Restore can aid you with virus elimination:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of BNFD. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove BNFD from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by BNFD, you can use several methods to restore them:
Data Recovery Pro method might be just for you
Data Recovery Pro is a recovery tool that might be able to restore at least some of your lost files.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by BNFD ransomware;
- Restore them.
Rely on Windows Previous Versions feature
This method would only work if you had system restore point prepared and it was not deleted by the infection.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Use ShadowExplorer to recover you files
This app will only work if malware failed to delete Shadow Copies.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
No decryptor is currently available
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from BNFD and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Tarcísio Marinho. Ransomware encryption techniques. Medium. Publishing platform.
- ^ WannaCry hackers had no intention of giving users their files back even if they paid. The Conversation. In-depth analysis, research, news.
- ^ Lesvirus. Lesvirus. Cybersecurity news and articles.





















