Matrix ransomware (Virus Removal Instructions) - updated Oct 2020
Matrix virus Removal Guide
What is Matrix ransomware?
Matrix ransomware is a data locker that has been encrypting users' files since late 2016
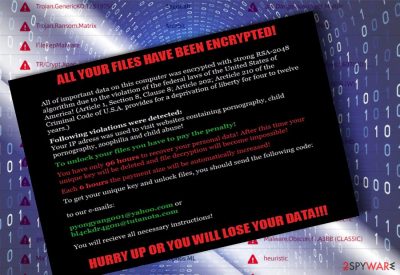
Matrix ransomware[1] is a crypto-malware that was first designed as a screen locker accusing users of illegal activities (such as viewing child pornography or downloading copyrighted material). While the virus did not modify personal data on the computer at the beginning of its functionality, hackers behind the Matrix virus eventually decided to add more advanced functions.
Currently, malware is operating as fully-functional ransomware and releases several new variants monthly. It uses a combination of AES and RSA encryption algorithms to lock up data and modifies its structure by adding numerous extensions. Initially, either .Matrix or .MATRIX!!! extensions were used, and MATRIX-Readme.rtf ransom note (written in Russian and English languages), dropped on the desktop on other locations.
However, as the years went by, new malware versions also used new extensions, including .S996, .AW46, .DEUS, and .TG33. Unfortunately, even after many years of operation, the Matrix ransomware virus remains undefeated by security researchers, as none of the versions are currently decryptable. As a result, those who get infected are likely to lose their personal files permanently.
| Name | Matrix |
|---|---|
| Malware type | Ransomware |
| Distribution | Hacker Remote Desktop Service, spam |
| Encryption method | AES-128 and RSA-2048 |
| Versions | TheMatrixHasYou, 2017 Matrix version, [Files4463@tuta.io] file extension virus, [RestorFile@tutanota.com] virus, [BatHelp@protonmail.com].-.CORE virus, Matrix, KOK08, NEWRAR, FASTBOB, ITLOCK, EMAN, NOBAD, GMAN, RELOCK, FOX, GMPF, FASTA, SPCT, GRHAN, GMBN, PEDANT and other versions. |
| Ransom note |
matrix-readme.rtf, !ReadMe_To_Decrypt_ |
| Danger level | High. Encrypts personal files, initiates malicious system's changes |
| Decryptable? | No. Nonetheless, in some rare cases, you might be able to recover at least some part of locked files – follow the instructions in the recovery section below |
| virus removal | You need to delete the infection from your computer in order to prevent the incoming files from being encrypted as well. The elimination should always be performed with a robust security application, such as SpyHunter 5Combo Cleaner |
| system fix | If you experience any side-effects post-infection, we recommend fixing damaged system parts with FortectIntego |
According to the research, Matrix ransomware is still active in 2020, and it seems like hackers will not stop the releases of new versions. It has been receiving updates to avoid detection and to affect more victims.
The malware has been spreading via hacked Remove Desktop Services (RDS) brute forcing the password. Nonetheless, it can also be dispersed in spam email attachments and fake updates. Since the developers have started employing RIG exploit kit to boost distribution of this ransomware, there is a great danger of getting this threat. It is targeting English-speaking countries, Russia, Spain, Poland, Italy and many other countries from all around the world.
As soon as such malware compromises a computer, it scans for important data and encodes them with AES and RSA ciphers to make them inaccessible. After that, it marks them with .matrix, [Files4463@tuta.io], [RestorFile@tutanota.com], or another extension. Some variants are also known not to append anything at all, although files remain locked.
Few versions of this malware are not changing files' names and only drop #What_Wrong_With_Files#.rtf, #CORE_README#.rtf, #README_FASTA#.rtf, and other ransom notes on every folder to inform the victim about the attack and its outcomes.
In the beginning, the virus was relying on the ransom message called matrix-readme.rtf. Unlike other ransomware strains such as Djvu, Matrix crypto-malware authors seem to change the names of the ransom note consistently. Typically, they include the name of the extension added to all the personal files.
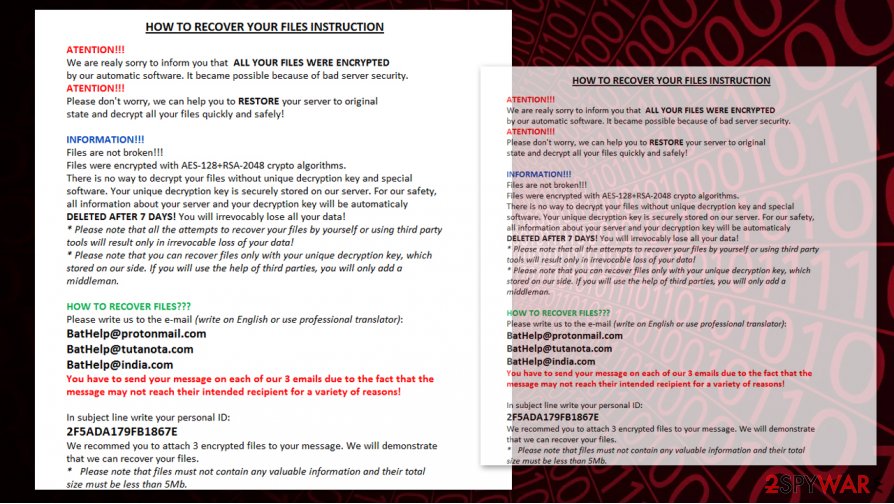
Here are the contents of a ransom note TG33_INFO.rtf, delivered by the TG33 variant:
HOW TO RECOVER YOUR FILES INSTRUCTION
ATENTION!!!
We are realy sorry to inform you that ALL YOUR FILES WERE ENCRYPTED by our automatic software. It became possible because of bad server security. ATENTION!!!
Please don’t worry, we can help you to RESTORE your server to original state and decrypt all your files quickly and safely!
INFORMATION!!!
Files are not broken!!!
Files were encrypted with AES-128+RSA-2048 crypto algorithms.
There is no way to decrypt your files without unique decryption key and special software. Your unique decryption key is securely stored on our server. For our safety, all information about your server and your decryption key will be automaticaly DELETED AFTER 7 DAYS! You will irrevocably lose all your data!
* Please note that all the attempts to recover your files by yourself or using third party tools will result only in irrevocable loss of your data!
* Please note that you can recover files only with your unique decryption key, which stored on our side. If you will use the help of third parties, you will only add a middleman.
HOW TO RECOVER FILES???
Please write us to the e-mail (write on English or use professional translator):
BatHelp@protonmail.com
BatHelp@tutanota.com
BatHelp@india.com
You have to send your message on each of our 3 emails due to the fact that the message may not reach their intended recipient for a variety of reasons!
In subject line write your personal ID:
2F5ADA179FB1867E
We recommed you to attach 3 encrypted files to your message. We will demonstrate that we can recover your files.
* Please note that files must not contain any valuable information and their total size must be less than 5Mb.
Please, do not follow these commands, as you might You should take care of Matrix ransomware removal right after finding encrypted files on your computer. Additionally, use data recovery options that we provided at the end of this post to recover your encrypted data.
List of extensions used by Matrix ransomware
| .[Files4463@tuta.io] .[RestorFile@tutanota.com] .[BatHelp@protonmail.com].-.CORE .FOX .[KOK8@protonmail.com].-.KOK8 .KOK08 .FASTBOB .ITLOCK .EMAN .NOBAD .GMAN .GMPF .FASTA .SPCT .GRHAN .GMBN .PEDANT |
.AG88G .SNTG .ATKL .MKES .FDFK .PSAFE .BWNG .BDDY .TMS5 .MT88 .DRSC .PSAFE .YDH3 .ABAT .DECP .YDHM .MDRL |
.TG33 .DEUS .AW46 .S996 .BG85 .FDFK22 .MH24 .AB89 .RE78P .AL8P .JB78 .AL8G .QH24 .RAD |
List of contact email addresses used by Matrix ransomware
| TheMatrixHasYou9643@yahoo.com matrix9643@yahoo.com redtablet9643@yahoo.com noliberty9643@yahoo.com nobad@tutamail.com thematrixhasyou9643@yahoo.com cremreihanob1979@yandex.ru pyongyang001@yahoo.com bl4ckdr4gon@tutanota.com PabFox@protonmail.com FoxHelp@cock.li FoxHelp@tutanota.com KOK08@protonmail.com FastBob@protonmail.com TRU888@QQ.COM tru8@protonmail.com tru8@tutanota.com rescompany19@qq.com rescompany19@yahoo.com rescompany19@cock.li pedantback@protonmail.com AlanRed@criptext.com RobertEvan@criptext.com AdamBrown89@criptext.com Mayth24@aol.com FridaFarko@yahoo.com BatHelp@protonmail.com BobGreen85@criptext.com BobGreen85@aol.com |
maihoandcryp@qq.com Kromber@tutanota.com Quickhelp24@protonmail.com MyDataRestore@protonmail.com YourDataHere@protonmail.com deccrypasia@yahoo.com abat2019@yahoo.com YourDataHere333@protonmail.com SafeGman@protonmail.com DataRescue@protonmail.com MarkTrue88@protonmail.com TomSoyer5@protonmail.com Buddy@criptext.com billwong73@yahoo.com SafeGman@protonmail.com FridaFarko@yahoo.com MarkEvans333@criptext.com atomickule@cock.li SantaGman@criptext.com AlanRed@criptext.com JamesBaker78@criptext.com BobGreen85@tutanota.com John91Doe@yahoo.com Sidmouleux996@aol.com alexwind46@yahoo.com alexwind46@protonmail.com alexwind46@aol.com Deus69@criptext.com PabFox@protonmail.com |
If you’re looking for Matrix decryption tool, you should know that currently there is none. It is extremely hard to decrypt files without knowing the decryption key, and that is why ransomware developers have put every effort to hide it from the computer user. Typically, they keep the decryption key in the hidden servers, so the first step after finding out that the system is infected is very simple: remove Matrix virus to make sure that there are as little encrypted files as possible.
It would be unwise to remit the payment as there are no guarantees that the developers will play fair and return them. There have also been doubts about their decrypter and if it is functioning properly. If it is a program, it may contribute to future crypto-malware hijack. Therefore, remove Matrix ransomware virus in a hurry. You can use anti-malware tools, such as SpyHunter 5Combo Cleaner or Malwarebytes, for the ransomware elimination.
We suggest you create a backup of encrypted data and keep it safe until someone releases a free decryption tool – if you have heard about TeslaCrypt[2] or PrincessLocker[3] cases, you probably understand that it is possible to decrypt files once they're encrypted; however, malware reversers need to spend a lot of time to create malware decryptors, so please be patient!
Finally, if you experience any type of inadequate Windows behavior (lag, freezes, crashes, errors, and other issues), we suggest you employ FortectIntego repair software to remediate the operating system and fix system files that might have been negatively affected during the Matrix ransomware virus infection.
After staying still, the virus came back in October 2017
In October 2017, Matrix ransomware made its first comeback[4]. The authors continue relying on RIG exploit kit. There are no crucial changes except a couple of new email addresses. One of them refers to North Korea's capital Pyongyang.
The fact that the malware is placed in .saz folder suggests it may be distributed via email attachments. Fortunately, the latest version is already detectable (TR/Crypt.Xpack.vdzpt, Trojan.Ransom.Matrix, etc.) by security tools. The virus may hide in 1q0NOiyA.exe or alternative executable file.
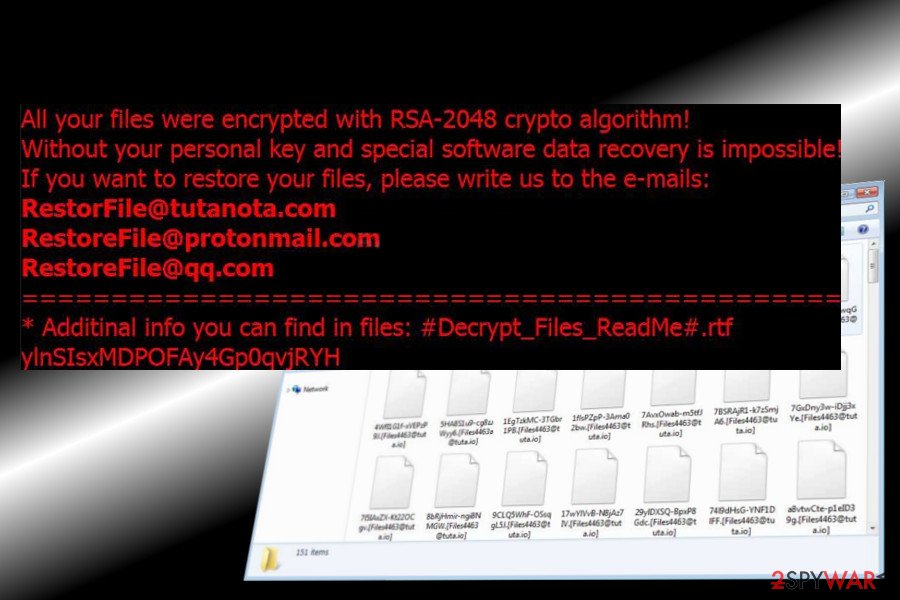
Another variant can be recognized by the file extension [RestorFile@tutanota.com]. In comparison to the previous version, this one is a bit more elaborate in terms of debugging messages and cipher command. Its ransom note is named as #Decrypt_Files_ReadMe#.rtf. The victim is asked to send a unique identification number via one of the following email addresses:
- RestorFile@tutanota.com
- RestoreFile@protonmail.com
- RestoreFile@qq.com
The list of the most prominent Matrix ransomware versions
FASTA ransomware
FASTA ransomware is a Matrix ransomware version discovered on November 14th, 2018. Also known as Fastbk@qq.com ransomware, this particular cryptovirus is a slightly altered version of the Matrix ransomware. Developers still rely on spam email attachments with infected MS documents as the main virus distribution technique because it allows hackers to spread their malicious product all over the world.
This version also uses a difficult pattern for the file extension, .[FASTBK@QQ.COM].users' ID.FASTA file marker gets at the end of every encrypted file. When all targeted data gets locked virus places a ransom note in a form of #README_FASTA#.rtf. In this file, developers generated a ransom message which directs users to contact hackers via fastbk@qq.com to get their decryption keys. However, this is not recommended, especially when it comes to notorious ransomware like Matrix. Paying the ransom or even contacting these hackers may lead to more severe damage or permanent data loss.
GMPF ransomware
GMPF ransomware is the product of the notorious crypto-extortionist team that was released at the end of October 2018. At the moment of writing, it is the latest version of Matrix ransomware, so there is no surprise that there is very little information known. However, it is known that encrypted files receive the following appendix: [GetMyPass@qq.com].user ID (random letters and numbers).GMPF and that their encryption is performed by using AES-128 + RSA-2048 encryption algorithms.
Based on the pattern the ransom note developed after the file-locking should be placed on the system if a form of TXT or RTA file. The ransomware attack starts with a full system scan but not with the encryption itself. Cryptovirus first checks if the system was encrypted before and makes additional changes to system files and folders to make the threat more persistent. It is the reason that before scanning the system with FortectIntego you may need to enter the Safe Mode with Networking.
EMAN ransomware
EMAN ransomware is a cryptovirus that was spotted during the first weeks of October 2018. This is the variant that uses AES-128 and RSA-2048 encryption methods to lock users data and later on marks them with [EncodeMan@qq.com].[gibberish].EMAN appendix.
This cyber threat introduces #README_EMAN#.rtf file as a ransom note that suggests people contacting developers for a file decryption key. EncodeMan@qq.com; EncodeMan@protonmail.com; EncodeMan@tutanota.com are emails provided in a lengthy ransom message which also contains the note that your files are going to be deleted after seven days.
NOBAD ransomware
NOBAD ransomware is one of the many variants released in October 2018. As well as other more recent versions, this cryptovirus uses both AES and RSA encryption algorithms to lock photos, documents, archives and other types of data that user stores on the device. It marks encoded data in a similar pattern as the versions before and after – [email].[random_combination].NOBAD.
No significant difference from other variants except ransom note placed on the system as a file named #NOBAD_README#.rtf, still no certain ransom amount but the preferred currency is Bitcoin.
GMAN ransomware
GMAN ransomware — yet another matrix variant released mid-October of 2018. Another version that uses both encryption methods and locks data until it is inaccessible. It affects any format of the file even archives and databases, backup files too if the victim enters an external device on the infected system.
This version brings !README_GMAN!.rtf and #README_GMAN#.rtf ransom note patterns to the mix. However, the ransom note itself looks almost identical to previous versions and states the following:
Files are not broken!!!
Files were encrypted with AES-128+RSA-2048 crypto algorithms.
There is no way to decrypt your files without unique decryption key and special software. Your unique decryption key is securely stored on our server. For our safety all information about your server and your decryption key fill be automaticaly DELETED AFTER 7 DAYS! You will irrevocably lose all your data!
*Please note that all the attempts to recover your files by yourself or using third party tools will result only in irrevocable loss of your data!
*Please note that you can recover files only with your unique decryption key, which stored on our side. If you will use the help of third parties, you will only add a middleman.
As previous versions and many other crypto-demanding threats, GMAN spreads using spam email attachments disguised as invoices, receipts, order information or another financial document. The minute victim downloads and opens the attached file on the system ransomware payload infiltrates the system and starts the encryption process.
RELOCK ransomware
RELOCK ransomware emerged in 2017. As various other versions, it encrypts files and marks them with _[RELOCK001@TUTA.IO].* file extension. Hackers behind this threat are stating in their ransom note hat every 12 hours the ransom amount is going to increase. This file is named as !OoopsYourFilesLocked!.rtf.
Criminals have also been encouraging people to contact them for the alleged decryption tool via relock001@tuta.io and relock001@yahoo.com e-mail addresses. Developers suggest sending three files for test decryption. However, this is only for fake trust to build.
TheMatrixHasYou ransomware
The new version of Matrix ransomware does not highly differ from the original version. It is also designed to encrypt the most valuable information, including videos, music, photos, documents and audio files. The victim can no longer open and use encrypted information.
The only noticeable difference between the initial version of the ransomware and TheMatrixHasYou virus is that the latter provides different contact emails: TheMatrixHasYou9643@yahoo.com and noliberty9643@yahoo.com, and leaves information about the attack in <victim’s id=””>.MATRIX-KEY.RTF file.</victim’s>
This version is also still very dangerous, and there is no antidote for its poison. If your files have been encrypted, you should restore them from backup or remain patient until reverse-malware engineers discover a way to crack it and create a free decryptor.
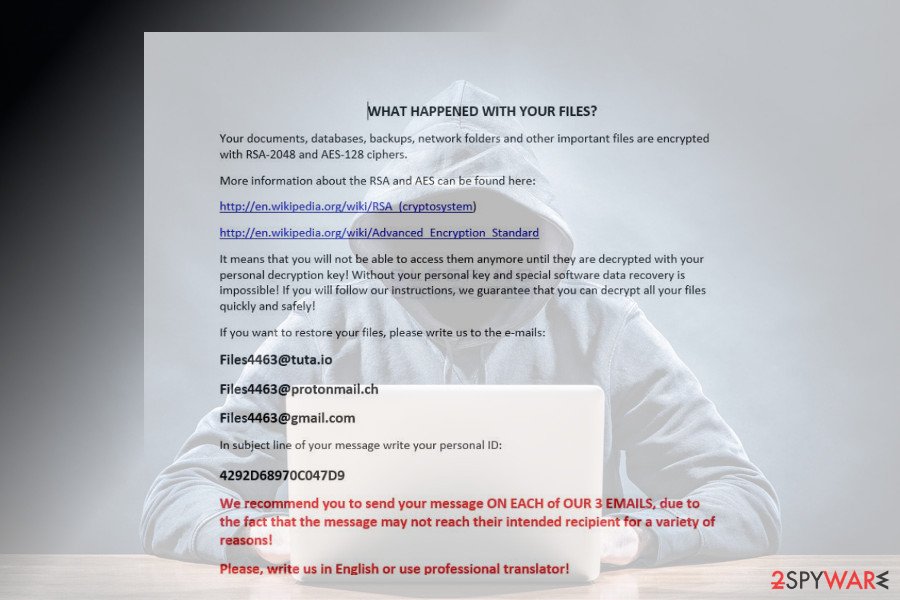
[Files4463@tuta.io] file extension virus
This version of Matrix ransomware was detected in the first half of April 2018. Researchers detected it spreading via hacked Remote Desktop services. It uses RSA-2048 and AES-128 encryption algorithms and creates a !ReadMe_To_Decrypt_
The note describes the current situation and contains a personal identification number, which has to be indicated in the subject line of the email and sent to one of the following addresses:
- Files4463@tuta.io
- Files4463@protonmail.ch
- Files4463@gmail.com
Unfortunately, this variant does not have a free decryptor, at least not yet. Nevertheless, we do not recommend paying the ransom as it's not clear whether the paid Matrix decryptor is reliable.
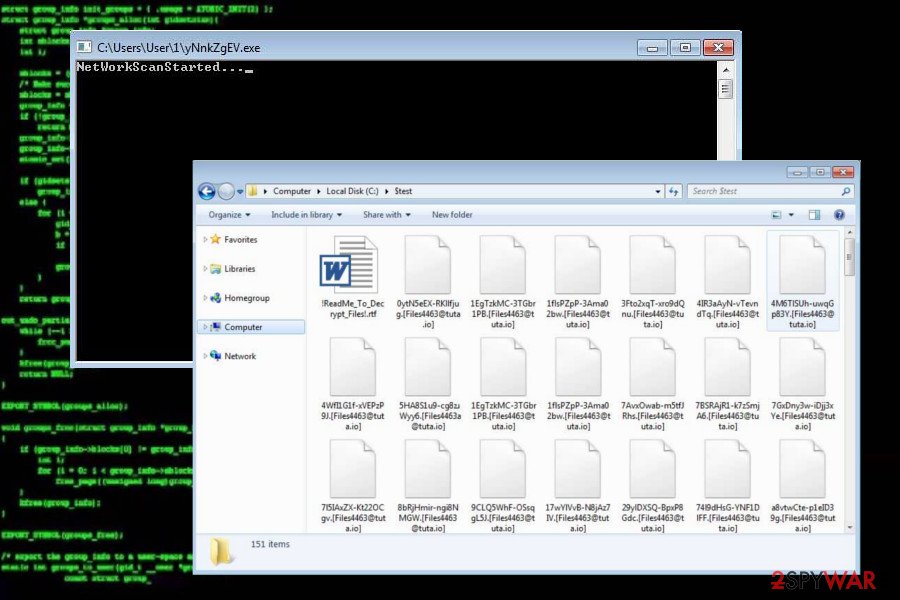
[RestorFile@tutanota.com] file extension virus
This Matrix ransomware version is almost identical to the previous one. Nevertheless, it has been developed in a more professional way as it uses a more complex debugging messaging and cipher commands.
It also renders RSA-2048 and AES-128 ciphers and targets personal files just like its predecessor. Upon encryption, locked files exhibit [RestorFile@tutanota.com] file extension. PC's desktops background is replaced by Matrix lock screen and the victim is represented with a ransom note named #Decrypt_Files_ReadMe#.r
The victim is demanded to provide a unique ID number to get payment instructions. For this purpose, they have to write down an email message and send to RestorFile@tutanota.com, RestoreFile@protonmail.com, and RestoreFile@qq.com email addresses. The [RestorFile@tutanota.com] file extension is not decryptable for free.
Fox ransomware
Fox ransomware was discovered in August 2018 as the latest version of Matrix virus. The encryption process is done using AES-128 and RSA-2048 methods. Every modified file gets an extension in this pattern: [hacker's email].[random_ID].FOX. Fox virus places a ransom note #FOX_README#.rtf, containing the instructions for further actions, on every folder that has modified data. In this note, virus developers provide contact emails: PabFox@protonmail.com; FoxHelp@cock.lt; FoxHelp@tutanota.com. It spreads while breaking through RDS.
There is no official decryption tool, so we do recommend to remove Fox Matrix ransomware using proper anti-malware tools. Only then you can focus on the important data recovery process. DO NOT contact cybercriminals and DO NOT pay the demanded ransom. This may lead to permanent data or money loss.
KOK08 ransomware
At the beginning of September 2018, researchers have spotted a new version of Matrix malware. It executes encryption codes to compromise valuable data and appends .KOK08 file extension afterward. Note, that this version is similar to .KOK8 file extension virus as the used suffix is almost identical.
Victims receive the ransom note named as #KOK08_README#.rtf file which informs about data encryption as any other message of this virus. Hackers merely indicate KOK08@protonmail.com email address for contact purposes. Likewise, victims suppose to write to the provided email. Although, experts do not recommend doing so.
FASTBOB ransomware
Just in a few day difference, researchers discovered another updated variant of Matrix ransomware. Similar to other upgrades, criminals haven't changed anything essential except the extension and the name of the ransom note.
This new version of Matrix malware appends .FASTBOB file extension after data encryption. Users receive instructions on how to decrypt information in #_#FASTBOB_README#_#.rtf ransom note. The message urges to contact the crooks via FastBob@protonmail.com email address.
ITLOCK ransomware
The .ITLOCK variant showed up in mid-September and was discovered by independent security researchers.[5] The malware uses AES and RSA to lock files up and demands a ransom to be paid via the !ITLOCK_README!.rtf message. Crooks demand users to contact them using itcompany2018@qq.com to receive instructions on how to recover encoded files. As usual, we do not recommend contacting cybercriminals and use alternative methods for file recovery after ITLOCK ransomware removal is complete using reputable security tools.
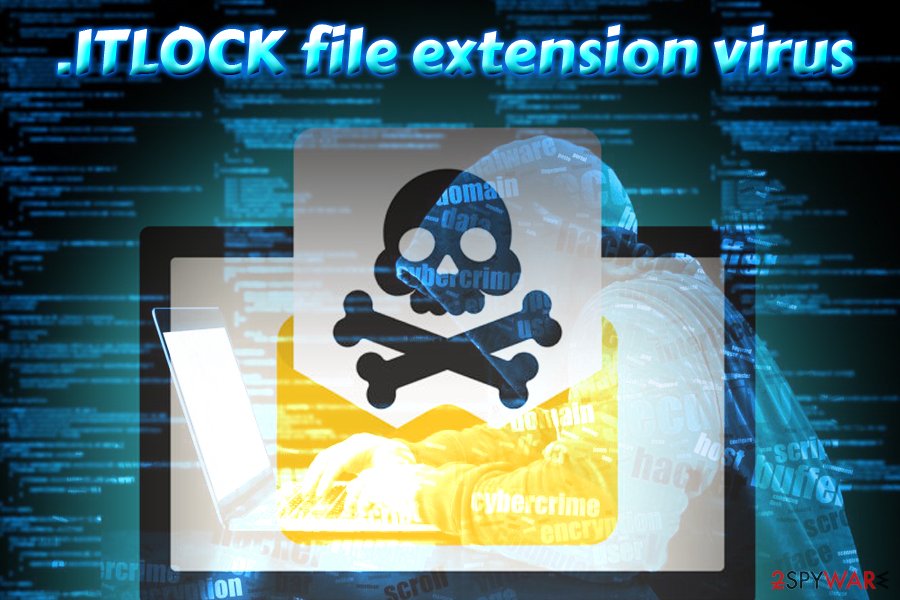
At the end of January 2019, hackers released a new version of ITLOCK ransomware. Not to be confused with the previous versions, this one drops !README_ITLOCK!.rtf ransom note that does look very similar to last virus variants. However, it contains different contact addresses: rescompany19@qq.com, rescompany19@yahoo.com, and rescompany19@cock.li.
This version of matrix appends the extension in the following way:
[rescompany19@qq.com].[random]-[random].ITLOCK
GRHAN ransomware
GRHAN ransomware is the latest variant of Matrix virus. Discovered on 14th of January by Michael Gillespie,[6] the malware has been spotted attacking Italian users.
The variant of Matrix uses .GRHAN file extension for all databases, music, videos, pictures and other data. After the infiltration, the virus contacts a remote server to upload the !README_GRHAN!.rtf ransom note, which informs victims about the file encryption and a ransom demands.
Users are asked to email Greenelephan@qq.com to agree how much they will have to pay for the decryptor. Victims can be asked to pay in Bitcoin or Ethereum cryptocurrency. Please do not contact hackers and instead remove GRHAN ransomware using reputable security tools.
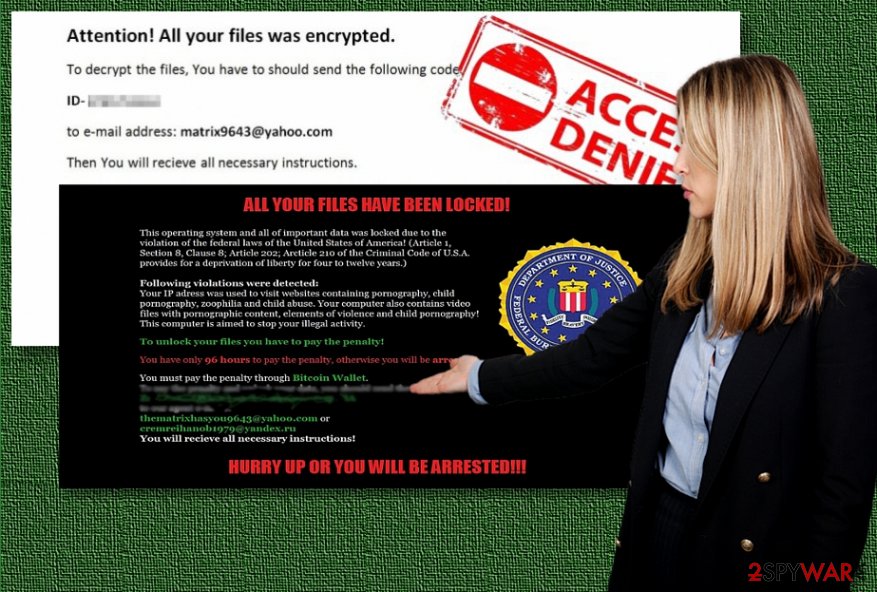
Crooks behind Matrix virus impersonate law enforcement agencies
As notices from law enforcement agencies, including Federal Bureau of Investigation (FBI), National Security Agency (NSA) and others might be intimidating, hackers try to take advantage of puzzled people and employ social engineering tactics to obtain illegal profits.
The current version of Matrix virus frightens users into thinking that their computer and data have been locked due to the US law violation. The counterfeited messages claim that their devices have been blocked due to the detected content of child pornography and similar criminal activities.
It also refers to the Criminal Code to deceive users more. However, few affected netizens might check the referred article and find out the different content. Keep in mind that mentioned institutions do not urge you to pay any amount of money within a specified amount of them.
Hackers expect you to remit the payment within 96 hours in order to escape a life imprisonment sentence. It is not difficult to look through the deception since the crooks provide a Bitcoin address and thematrixhasyou9643@yahoo.com and cremreihanob1979@yandex.ru.
Be vigilant when reviewing the spam folder. Do not open any email attachments before verifying the sender. Hackers often leave grammar mistakes and typos in such messages. The hijack is performed with the assistance of JNwpM1mu.exe or matrix.exe executable files. It can occupy a device via HEUR/QVM10.1.0000.Malware.Gen, malicious_confidence_100% (D),TR/Crypt.Xpack.uhqit, and similar trojan horses.
Hackers employ exploit kits for ransomware distribution
Usually, criminals aim to infect as many computers as possible to increase their ransomware payments. For that, they not only employ social engineering tactics but also exploit kits to circumvent PC systems. One of the most popular ones is Rig Exploit kit which helps to detect system vulnerabilities and infiltrate the ransomware.
Therefore, make sure you pay attention to what sources and what programs you download from. Avoid installing software other than official sites. pay attention to the “publisher” – it should indicate the name of the official company other than “unknown.”
Safely uninstall Matrix virus from your PC
For Matrix ransomware removal, you should consider installing a reliable antivirus tool. Our top recommendations are FortectIntego, SpyHunter 5Combo Cleaner, and SpyHunter 5Combo Cleaner. These security tools can be downloaded and installed once you boot your computer into Safe Mode. You will find instructions showing how to delete Matrix ransomware and reboot system into Safe Mode at the end of this article.
Now let's discuss the ransom part. First of all, if you're willing to pay it, do not delete the infection – do it afterward. However, we strongly recommend you not to pay the ransom and remove Matrix ransomware as soon as you detect the threat on your computer. There are numerous reasons why it is not worth paying; there are insufficient possibilities that criminals will decide to give you the decryption key to unlock files[7].
Besides, if you paid, you would encourage scammers to keep going and creating more malware. This will cause the number of ransomware victims grow. Although it is not a direct way to fight with ransomware, it can help to lower the number of ransomware cases in general. If victims stopped paying ransoms, cybercriminals would no longer see a point to create them.
Getting rid of Matrix virus. Follow these steps
Manual removal using Safe Mode
Remote Matrix virus by rebooting your computer into Safe Mode with Networking:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Matrix using System Restore
Get rid of malware by using System Restore. This tip will help you disable the threat.
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Matrix. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Matrix from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If files encrypted by Matrix ransomware, you can try our suggested methods to recover them. However, we strongly advise you to create a backup of encrypted files to have an intact copy. Sometimes failure to decrypt files can completely destroy them!
If your files are encrypted by Matrix, you can use several methods to restore them:
Use Data Recovery Pro to recover lost data
If you want, you can use Data Recovery Pro to decrypt your files. You can find full instructions on how to use such tool below.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Matrix ransomware;
- Restore them.
Try Windows Previous Versions feature to recover separate files
Windows Previous Versions come in handy when the current data versions get corrupted. If you enabled System Restore function a while ago, you can try to recover your files now. Bear in mind that this method helps to fix files one by one, so if you want to restore a big number of files at once, this is not the method you should go for.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer can help you with data decryption
If you are lucky and the ransomware hasn't managed to delete or compromise Shadow Volume Copies in any way, you might get help from ShadowExplorer tool. For more information, follow these steps:
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Currently, Matrix decryptor is still in development.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Matrix and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Kim Zetter. Hacker Lexicon: A Guide to Ransomware, the Scary Hack That’s on the Rise. WIRED. In-depth coverage of current and future trends in technology.
- ^ Michael Mimoso. Master Decryption Key Released for TeslaCrypt Ransomware. Threatpost. The first stop for security news.
- ^ Olivia Morelli. Princess Locker ransomware virus. How to Remove? (Uninstall Guide). 2-Spyware. Fighting against spyware.
- ^ EKFiddle. RIGEK drops Matrix ransomware. Twitter. Online source for news and communication.
- ^ Michael Gillespie. New Matrix ransomware variant. Twitter. Social network.
- ^ Michael Gillespie. #Matrix #Ransomware. Twitter. Social Network.
- ^ Olivia Morelli. Things to consider before paying the ransom to cyber criminals. 2-Spyware. Fighting against spyware.





















