Bortet.live ads (scam) - Free Instructions
Bortet.live ads Removal Guide
What is Bortet.live ads?
Bortet.live attempts to mimic warnings of legitimate security software to trick users
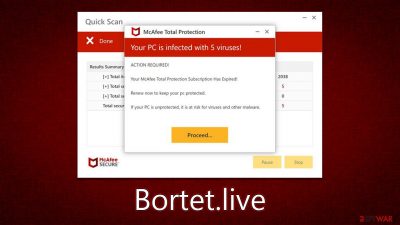
Bortet.live is a website that operates as a scam. Created by malicious actors, it attempts to mislead users into believing that their systems are infected with dangerous viruses and that they are in great danger. The main plot device used here is the name of a popular security vendor McAfee, although it obviously has nothing to do with these fake warnings shown to users.
If you have encountered Bortet.live, please do not download any offered software or click on links, as you might be tricked into installing potentially unwanted programs or even malware on your device. Even though the scan results shown on the page are completely fake, we do recommend users check their system for infections as per our instructions below.
| Name | Bortet.live |
| Type | Scam, fraud, phishing, redirect |
| Operation | Claims that viruses have been found on the system and that the security software has expired. Asks to purchase a license and enable push notifications |
| Distribution | Redirects from other malicious websites, adware |
| Risks | Loss of finances due to fake subscriptions; redirects to other malware-laden, scam websites; installation of potentially unwanted or malicious software |
| Removal | Make sure you scan your system with SpyHunter 5Combo Cleaner – especially if you downloaded and installed software from a scam site |
| Other tips | We recommend scanning the system with FortectIntego to clean browser caches and repair virus damage automatically after eliminating PUPs and malware |
How to spot fraudulent content online
Beware of the consequences when accessing websites with questionable origins; it is likely that you will be exposed to malicious content like malware and phishing links, gambling sites, or even worse. For example, those who are tempted to download illegal software knowingly put themselves in harm's way.
Staying safe online is pivotal, yet sometimes it can be difficult to avoid dubious websites. If you do come across them, here are some things to keep in mind: First and foremost, the website's URL should always raise a red flag if it looks suspicious – sites such as Bortet.live aren't part of any legitimate security vendor organization represented on these types of web pages.
As soon as you enter the page, you will be shown several pop-ups and something that looks like the user interface of McAfee security software. During this time, you would see detection triggers of a fake scan, which would ultimately return the following result (all users are shown the same thing, by the way):
Your PC is infected with 5 viruses!
ACTION REQUIRED
Your McAfee Subscription Has Expired!
Renew now to keep your PC protected.
If your PC is unprotected, it is at risk for viruses and other malware.
Beyond the typical pop-up message, users may encounter a blue notification that mimics Windows BSOD in purposeful design. This warning alerts them of their system's infection and suggests they take action to protect it from further harm; otherwise, leaving the computer unprotected could have dire consequences. While this statement is partly true, it is shown in a misleading manner with the intent to confuse and frighten victims.
It's vital to remember that any online scanners claiming they can detect viruses are fake, and the only dependable way of detecting and removing malware is through trusted security software installed on your device. Furthermore, messages claiming Flash Player or other software needs updating should not be acted upon as these may also result in virus infection.
Same scam techniques used on multiple websites
The prevalence of scams masquerading as Norton or McAfee security scans has been steadily rising. We've touched on the likes of Maveks.live, Bikemolktwo.xyz, and Webaddictremind.xyz, to name a few – all utilizing similar strategies to Safeprotect.info with identical structure and functionality too.
Scammers will intentionally choose names for their websites that evoke security, such as “scan,” “repair,” and “clean.” They try to make these sites appear reliable and official, yet in reality, they are anything but. Thus, if you encounter any websites of this sort, please disregard what they are claiming and leave them immediately.
Get rid of adware and clean your browsers from infections
To ensure that your PC is free of adware after being exposed to a fraudulent website, you should quickly and easily run an adware check with the help of SpyHunter 5Combo Cleaner or Malwarebytes security software. This will eliminate all malicious components from your system in no time. While manual removal may be tedious and time-consuming, you can have unwanted programs removed quickly with automatic tools. Moreover, it is possible that deleting helpful applications might do more harm than good.
After verifying your device is free from malware and adware, an important step to take next would be cleaning out cookies and other trackers in your browser – either by using FortectIntego for convenience or following the methods listed below.
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
Take care of push notifications from Bortet.live
Scammers often employ deceitful tactics to make money and turn a profit, including manipulating users' computer status and displaying false information on websites. They will attempt to sell unwarranted software or request that users enable push notifications immediately upon entering the website.
If one accepts these push notifications, criminals can gain additional monetary benefits through ads shown directly on their desktops via the browser's Push Notification API at any given time – even when they're not actively browsing the internet. It is, therefore, essential to be very careful when accessing websites that claim to offer scanning services or other computer-related features, as well as to pay close attention to the permissions these websites request at any time.
Keep in mind that if you have enabled push notifications from Bortet.live, malicious links and messages would inevitably reach your screen – do not interact with these. Instead, follow the instructions below to get rid of these intrusive pop-ups:
Google Chrome
- Open the Google Chrome browser and go to Menu > Settings.
- Scroll down and click on Advanced.
- Locate the Privacy and security section and pick Site Settings > Notifications.
- Look at the Allow section and look for a suspicious URL.
- Click the three vertical dots next to it and pick Block. This should remove unwanted notifications from Google Chrome.
![Stop notifications on Chrome PC 2 Stop notifications on Chrome PC 2]()
Mozilla Firefox
- Open Mozilla Firefox and go to Menu > Options.
- Click on Privacy & Security section.
- Under Permissions, you should be able to see Notifications. Click the Settings button next to it.
- In the Settings – Notification Permissions window, click on the URL's drop-down menu.
- Select Block and then click on Save Changes. This should remove unwanted notifications from Mozilla Firefox.
![Stop notifications on Mozilla Firefox 2 Stop notifications on Mozilla Firefox 2]()
MS Edge (Chromium)
- Open Microsoft Edge, and go to Settings.
- Select Site permissions.
- Go to Notifications on the right.
- Under Allow, you will find the unwanted entry.
![Stop notifications on Edge Chromium Stop notifications on Edge Chromium]()
- Click on More actions and select Block.
Safari
- Click on Safari > Preferences…
- Go to the Websites tab and, under General, select Notifications.
- Select the web address in question, click the drop-down menu and select Deny.
![Stop notifications on Safari Stop notifications on Safari]()
How to prevent from getting adware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.








