Cceq ransomware (virus) - Free Instructions
Cceq virus Removal Guide
What is Cceq ransomware?
Cceq ransomware is a dangerous malware that blocks access to all personal files until the ransom is paid
Cceq ransomware is a malicious program designed for Windows operating systems. Its main purpose is to encrypt all personal files on the system, including pictures, videos, documents, databases, etc. Suchlike data is modified in a way (but not destroyed!) that only a unique key can retrieve its functionality – a special marking also becomes visible, as .Cceq extension is appended at the end.
In order to restore data, users require the said key, which is stored on the cybercriminals' servers. They are obviously not willing to give it for free and demand that a ransom of $980 is paid in bitcoin, a digital currency often used by cybercriminals behind ransomware.[1] They provide two contact emails – support@bestyourmail.ch and supportsys@airmail.cc – for communication purposes, although contacting hackers is not advisable. All this information can be found in a ransom note dropped on the desktop, titled _readme.txt.
Cceq ransomware stems from the notorious Djvu malware family with hundreds of variants already in circulation. For example, we described Cceo, Ccyu, and Ccew just recently. While there is no guaranteed method of recovering your files, there are several things you can try instead of paying for a decryption key – we list all the methods below.
| Name | Cceq ransomware |
| Type | Ransomware, file-locking virus |
| Family | Djvu |
| Encryption | RSA is used to lock all personal files on the infected Windows computer |
| File extension | .cceq |
| Ransom note | _readme.txt |
| Contact | support@bestyourmail.ch and supportsys@airmail.cc |
| File recovery | While data recovery without paying cybercriminals is not impossible, it may be difficult. Check the solutions we provide below |
| Malware removal | To perform a full ransomware removal effectively, use powerful SpyHunter 5Combo Cleaner, Malwarebytes anti-malware software |
| System fix | Malware can seriously tamper with Windows systems, causing errors, crashes, lag, and other stability issues after it is terminated. To remediate the OS and avoid its reinstallation, we recommend scanning it with the FortectIntego repair tool |
The ransom note
A ransom note is the first communication tool between the attackers and victims. Most ransomware is designed to show the note as soon as the file encryption process is finished. This guarantees that users would see what they can do to recover their data, increasing the chance of a successful payment.
Crooks also often use additional tricks to make them feel more trustworthy, for example, they offer a 50% discount, which reduces the payment to $490, as long as it is made within 72 hours of the infection. This is a typical trick to make users feel like they are running out of time, pushing them to pay the ransom. Here's the full message you would receive after being infected with the Cceq virus:
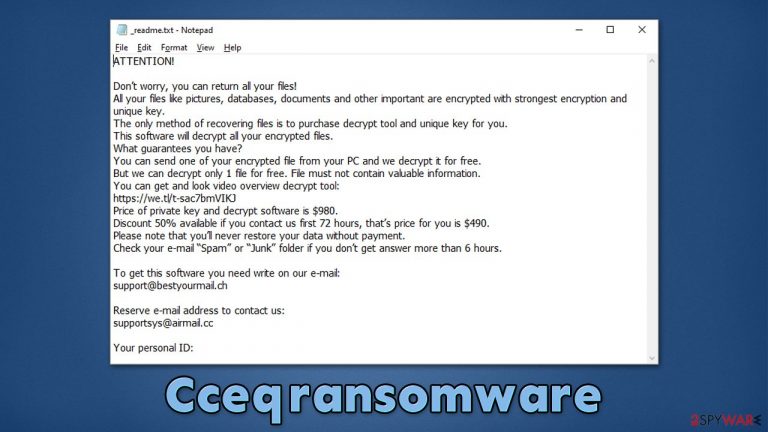
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-sac7bmVIKJ
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
support@bestyourmail.chReserve e-mail address to contact us:
supportsys@airmail.ccYour personal ID:
Despite the friendly demeanor, these people are not your friends, and they don't particularly care whether or not you restore your files after paying them money. While it is true that victims get recovery software, this outcome is never guaranteed. Besides, paying cybercriminals only enforces their position in the cybercrime world and justifies infecting more people, as it brings enough profits.

Instead, we recommend following through with the instructions below in order to restore .cceq files without paying money to cybercriminals. However, it is vital that the process is performed in the correct order.
Malware removal
Your first task is to ensure that the virus is removed from the system. While Djvu variants are known to self-destruct after performing the data encryption, they have been previously found with additional data-stealing modules, which need to be eliminated for sure. Likewise, ransomware may also be bundled with other infections, which are important to eliminate.
While manual removal can be possible, it is not recommended for regular users, as the risk of deleting incorrect files or failing to remove all malicious ones remains high. Thus, we recommend you employ a trustworthy solution instead – run a scan with SpyHunter 5Combo Cleaner or Malwarebytes security software. This will ensure that all the malicious ransomware components are deleted, along with any secondary infections installed on the device.
Before you proceed with Cceq ransomware removal, you should first ensure that your system is terminated from a network and/or the internet. Proceed with the following steps:
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet

- Click Network and Sharing Center

- On the left, pick Change adapter settings

- Right-click on your connection (for example, Ethernet), and select Disable

- Confirm with Yes.
Recover your data
There are a lot of misconceptions about ransomware and the way it works – these are especially common among people who get infected with it for the first time. While some people believe they can restore their files back to normal after they remove the virus with anti-malware software, others think that the files have been permanently corrupted because they can't be opened at the time. Neither of these statements is true.
Ransomware uses a sophisticated encryption algorithm RSA[2] to lock files, which is extremely secure. The applied key is essentially a long string of alphanumeric characters which simply can't be guessed. The key is unique, so none of the affected users can share it to restore their files. So, malware removal will not affect the state of the encrypted data, and it will remain unusable.
Unfortunately, only ransomware authors have access to the decryption key. Using alternative known methods is the only way to go around this, and we strongly recommend you try them. First of all, you should make backups of the encrypted files, as they might get corrupted during the recovery process.
First, we recommend trying data recovery software that may work for at least some of your files:
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders which you want the files to be recovered from.
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

Your other chance is by using the dedicated decrytpion software from Emsisoft. Keep in mind that it only works if your files were encrypted with an offline ID, which is usually not the case.
- Download the app from the official Emsisoft website.
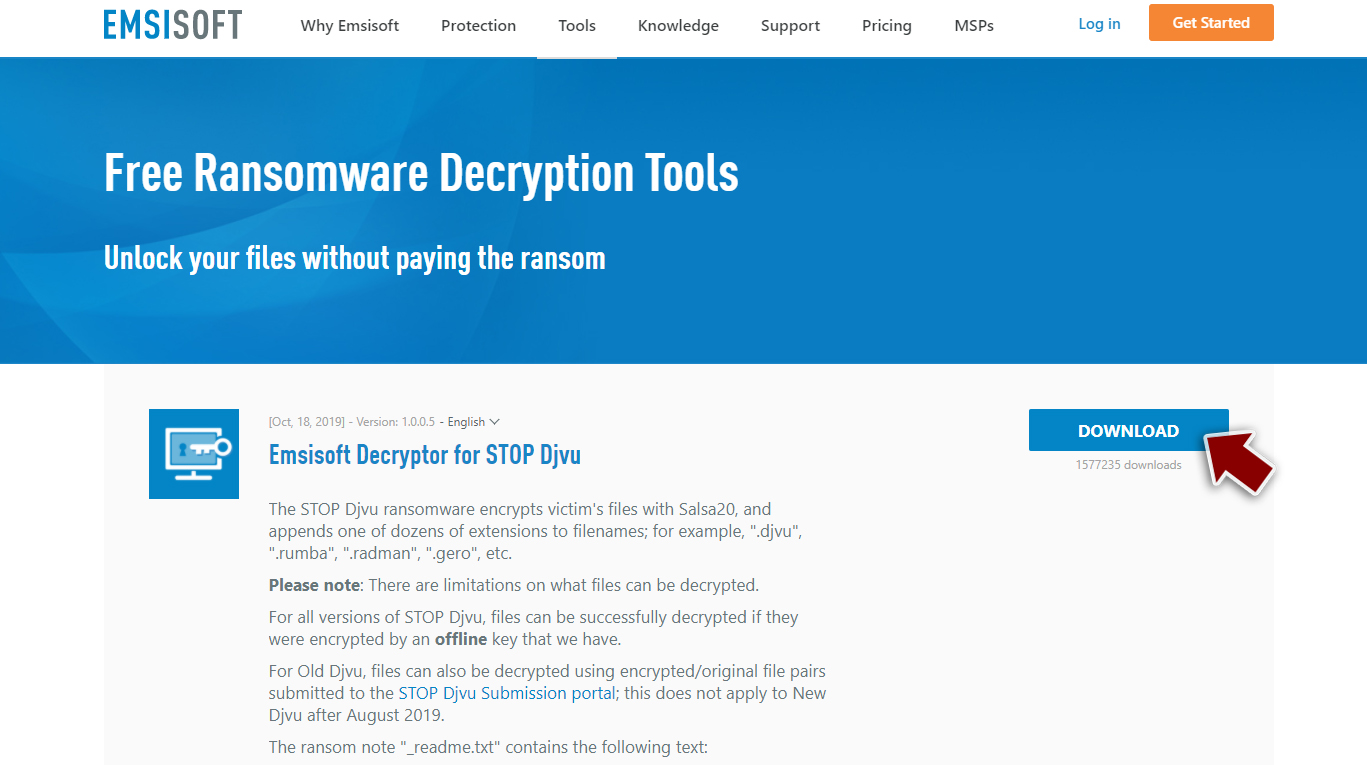
- After pressing the Download button, a small pop-up at the bottom titled decrypt_STOPDjvu.exe should show up – click it.

- If User Account Control (UAC) message shows up, press Yes.
- Agree to License Terms by pressing Yes.
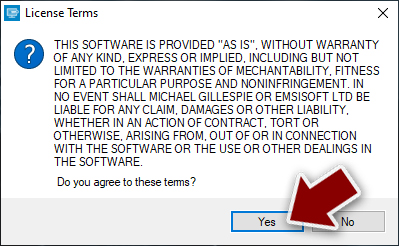
- After Disclaimer shows up, press OK.
- The tool should automatically populate the affected folders, although you can also do it by pressing Add folder at the bottom.

- Press Decrypt.

From here, there are three available outcomes:
- “Decrypted!” will be shown under files decrypted successfully – they are now usable again.
- “Error: Unable to decrypt file with ID:” means that the keys for this version of the virus have not yet been retrieved, so you should try later.
- “This ID appears to be an online ID, decryption is impossible” – you are unable to decrypt files with this tool.
Other tips
Once you are done with the other steps above, there are a few other tips that could result in a better outcome. First of all, you should remove the blocks that could have been applied via the hosts file – it may prevent visiting security-related websites.
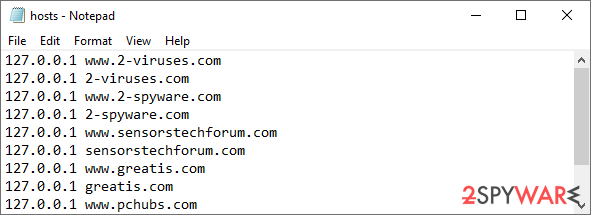
To restore your ability to access all websites without restrictions, you should either delete the file (Windows will automatically recreate it) or remove all the malware-created entries. If you have never touched the “hosts” file before, you should simply delete it by marking it and pressing Shift + Del on your keyboard. For that, navigate to the following location:
C:\Windows\System32\drivers\etc\
You should also employ FortectIntego to repair any damage that could have occurred during the ransomware infection stage. Otherwise, you might start receiving BSODs,[3] registry errors, crashes, and similar issues once the infection is terminated.
We also recommend reporting the ordeal to your local authorities – it would help the investigation that could potentially lead to the malware creators' capture. This would also mean that all the encryption keys would be released to the victims for free. To avoid being a victim of a ransomware attack in the future, please make use of the data backup process.
Getting rid of Cceq virus. Follow these steps
Create data backups to avoid file loss in the future
One of the many countermeasures for home users against ransomware is data backups. Even if your Windows get corrupted, you can reinstall everything from scratch and retrieve files from backups with minimal losses overall. Most importantly, you would not have to pay cybercriminals and risk your money as well.
Therefore, if you have already dealt with a ransomware attack, we strongly advise you to prepare backups for future use. There are two options available to you:
- Backup on a physical external drive, such as a USB flash drive or external HDD.
- Use cloud storage services.
The first method is not that convenient, however, as backups need to constantly be updated manually – although it is very reliable. Therefore, we highly advise choosing cloud storage instead – it is easy to set up and efficient to sustain. The problem with it is that storage space is limited unless you want to pay for the subscription.
Using Microsoft OneDrive
OneDrive is a built-in tool that comes with every modern Windows version. By default, you get 5 GB of storage that you can use for free. You can increase that storage space, but for a price. Here's how to setup backups for OneDrive:
- Click on the OneDrive icon within your system tray.
- Select Help & Settings > Settings.

- If you don't see your email under the Account tab, you should click Add an account and proceed with the on-screen instructions to set yourself up.

- Once done, move to the Backup tab and click Manage backup.

- Select Desktop, Documents, and Pictures, or a combination of whichever folders you want to backup.
- Press Start backup.

After this, all the files that are imported into the above-mentioned folders will be automatically backed for you. If you want to add other folders or files, you have to do that manually. For that, open File Explorer by pressing Win + E on your keyboard, and then click on the OneDrive icon. You should drag and drop folders you want to backup (or you can use Copy/Paste as well).
Using Google Drive
Google Drive is another great solution for free backups. The good news is that you get as much as 15GB for free by choosing this storage. There are also paid versions available, with significantly more storage to choose from.
You can access Google Drive via the web browser or use a desktop app you can download on the official website. If you want your files to be synced automatically, you will have to download the app, however.
- Download the Google Drive app installer and click on it.

- Wait a few seconds for it to be installed.

- Now click the arrow within your system tray – you should see Google Drive icon there, click it once.

- Click Get Started.

- Enter all the required information – your email/phone, and password.

- Now pick what you want to sync and backup. You can click on Choose Folder to add additional folders to the list.
- Once done, pick Next.

- Now you can select to sync items to be visible on your computer.
- Finally, press Start and wait till the sync is complete. Your files are now being backed up.
Report the incident to your local authorities
Ransomware is a huge business that is highly illegal, and authorities are very involved in catching malware operators. To have increased chances of identifying the culprits, the agencies need information. Therefore, by reporting the crime, you could help with stopping the cybercriminal activities and catching the threat actors. Make sure you include all the possible details, including how did you notice the attack, when it happened, etc. Additionally, providing documents such as ransom notes, examples of encrypted files, or malware executables would also be beneficial.
Law enforcement agencies typically deal with online fraud and cybercrime, although it depends on where you live. Here is the list of local authority groups that handle incidents like ransomware attacks, sorted by country:
- USA – Internet Crime Complaint Center IC3
- United Kingdom – ActionFraud
- Canada – Canadian Anti-Fraud Centre
- Australia – ScamWatch
- New Zealand – ConsumerProtection
- Germany – Polizei
- France – Ministère de l'Intérieur

If your country is not listed above, you should contact the local police department or communications center.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Cceq and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Fergus O'sullivan. How Anonymous Is Bitcoin?. How-To Geek. Site that explains technology.
- ^ Josh Lake. What is RSA encryption and how does it work?. Comparitech. Information, tools and reviews.
- ^ Blue screen of death. Wikipedia. The free encyclopedia.
