How to remove Google Critical Security Alert
Critical Security alert Removal Guide
What is Critical Security alert?
Google Critical Security alert – a scam notification that you might receive via your Gmail
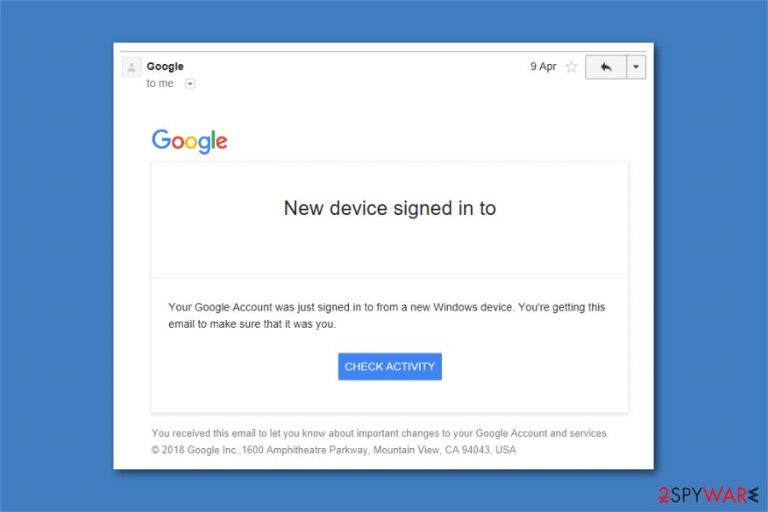
Google Critical Security alert is a fraudulent message which has been actively spreading around within the Gmail inbox. The email from no-reply@accounts or similar email addresses claims that someone just used your password to try to sign in to your account. Users are also advised to check the activity by clicking a button below the text. However, experts warn that the alert is set to trick users into revealing their email account credentials to cybercriminals or installing malicious software on their devices. Therefore, you should never click on the embedded links inside, regardless of how realistic and believable the buttons look and feel (especially if it comes from an unrecognized account).
Nevertheless, the tech giant uses sophisticated technology to recognize and warn users about an illegitimate login attempt from a different device. For that reason, many warnings from Google are legitimate and should not be ignored. Those who use such services as VPN and Proxy[1] might encounter several Google security alert email messages due to a different IP login, so the case is not always related to phishing.
| Name | Google Critical Security alert |
|---|---|
| Type | Malware/scam/fake alert |
| Also known as | Critical Security alert; Gmail Security Alert |
| Danger level | Medium. Users can be tricked into exposing their account credentials or lured into downloading malicious programs |
| Symptoms | Victims receive an email in their Gmail inbox which warns about unauthorized sign-in; they are encouraged to take precautionary measures to prevent unauthorized activity |
| Distribution | Malicious spam emails |
| Elimination | If you clicked on a suspicious link, you should scan your device with anti-malware software and then change your passwords immediately |
| System fix | In case security software flagged something malicious on your device, use FortectIntego to attempt to fix the registry database and other system parts to remediate the machine after the infection |
It is not new that attackers are creating legitimate-looking emails to trick people into compromising their systems. Note that the email contains a fake logo and appears as a real notification. Unfortunately, people should be aware of this alert and learn how to identify this phishing[2] scam.
The message displayed by the Critical Security alert scam contains the following text:
Someone just used your password to try and sign in to your account. Google blocked them, but you should check what happened.
[CHECK ACTIVITY]
Furthermore, if you click on the “CHECK ACTIVITY” button included in the email, there is a substantial risk that you will be redirected to a malicious site. In this case, hackers can develop another spoofed Gmail log-in page where you would submit your credentials directly to the attackers without even knowing it.
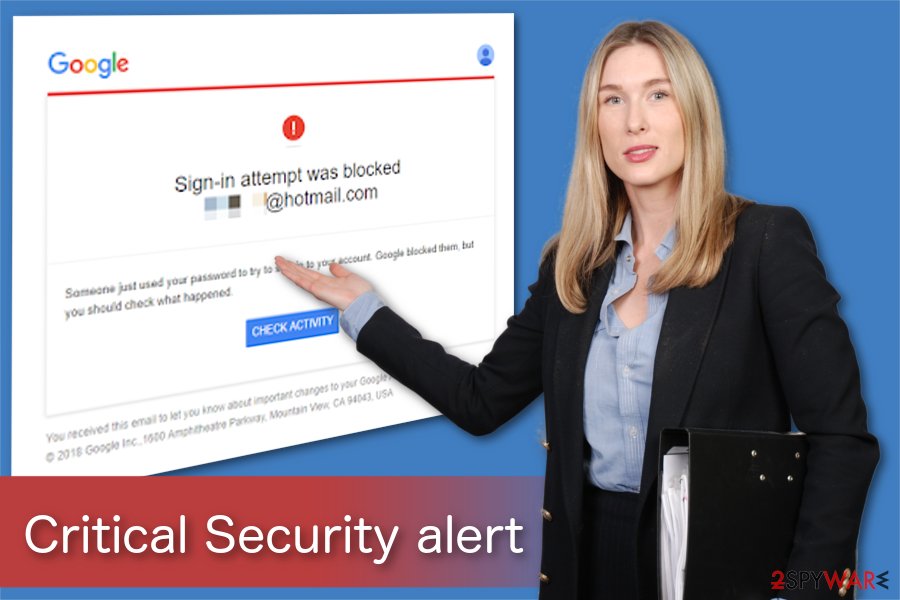
Additionally, the scam email might be used to distribute other malicious programs and aim to infect computers worldwide. Likewise, experts warn about potential ransomware[3] or malware attacks if you click on the content included in the fake alert.
We strongly advise you to stay cautious and remove Google Critical Security alert email together with related cyber threats if you clicked on anything suspicious. It might be hard to identify the malicious activity as it is usually performed in the background. Thus, scan your computer with a reliable antivirus, such as SpyHunter 5Combo Cleaner or Malwarebytes.
After Google the removal is completed, we suggest using the FortectIntego app – it might help you fix virus damage related to Windows system files. Also, if you believe that criminals might have stolen your credentials, change all your passwords immediately.
Legitimate Google warnings sparked some concerns among security experts
The community using Google services got really concerned about the issue, and many rushed to social media like Twitter to report the problem. The industry giant does not specify what security problems users are facing. So most people simply click on the link and are guided through the procedure.
Unfortunately, it is not that hard for hackers to imitate these steps, as was the case with the Google Critical Security Alert email scam. Therefore, several security analysts and social engineering experts showed concerns:[4]
It’s already in my template brochure to be used against corporates it’s that good. Unforgivable for Google to send this out en mass.
We have templates that we use to phish corporates (ethical testing) this email from Google is suitable to go straight in as it has urgency, guides to a login page, quite vague but alarming… we used to take legitimate Google emails and adapt… but this is just perfect as is.
The tech company said that these types of alerts were designed to go through a set of checks that would help users protect their accounts from hacking attempts and other dangers. Additionally, these messages cannot contain too much information about the possible security breach, as this data would only benefit the attacker.
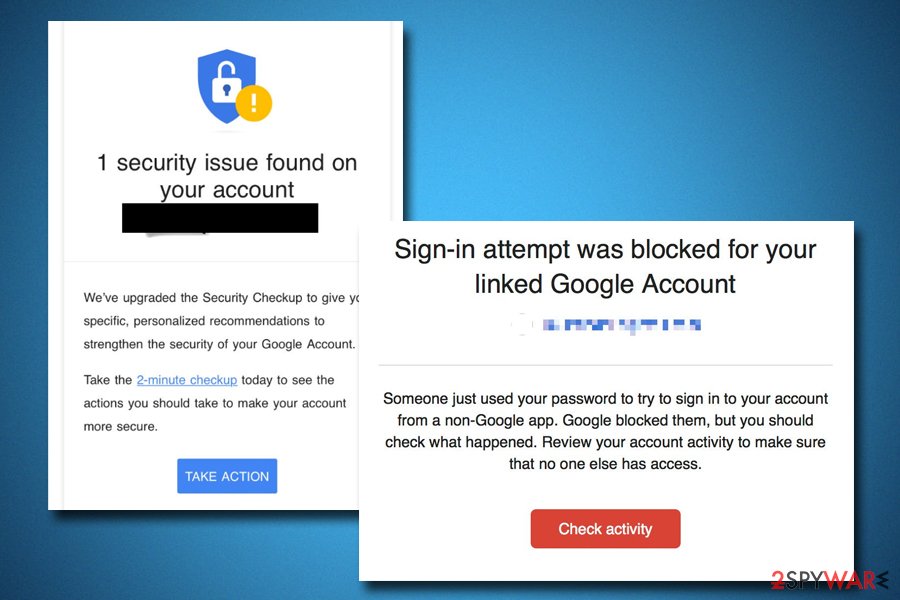
Because the email from Google might be legitimate, further investigation is required. In fact, there is a higher chance of receiving a legit email than a fake one. Regardless of the situation, each instance should be carefully examined, as careless clicking on links might lead to severe consequences (note that many scam emails are recognized and put into the Spam box).
In case you are not sure if an email from Google saying Critical Security Alert is real or not, you should navigate to the checkup page manually at myaccount.google.com/security-checkup and see what is going on there. Clicking on random links is never advisable, and cybercrooks are often very good at producing high-quality phishing emails that can compromise personal information and make users install malicious software on their devices.
Malicious spam emails might hide malware inside
A vast of cyber threats are delivered via spam emails. This is a well-known malware distribution technique that is widely employed by criminals worldwide. Unfortunately, people still lack expertise in the IT field to identify phishing emails to protect their private information, finances, and computer.
Fraudulent emails are designed to impersonate a legitimate company or governmental institution, notify about a problem, create some sort of an urge to fix it by opening an attachment or clicking on the link. However, at this point, users who click on email content do not resolve an issue rather than install a malicious program.
Experts[5] note that despite how legitimate the email looks, you should always contact the company directly and ask to confirm the email. Additionally, it would be best to use an antivirus with real-time protection to help you avoid infiltrating the system with malware.
Eliminate Critical Security alert scam and related malware
If you have clicked on any buttons or links included in the phishing email, you must remove Critical Security alert and its malicious components from your system. Keep in mind that eliminating the email from your inbox should do the trick, and you would remain safe if you do not click any links inside.
However, removing it from the inbox will not do wonders if you have already clicked on the link, especially if you downloaded something. Therefore, you should immediately perform a full system scan with powerful anti-malware, such as SpyHunter 5Combo Cleaner or Malwarebytes. To fix virus damage, we recommend trying FortectIntego.
Getting rid of Critical Security alert. Follow these steps
Manual removal using Safe Mode
If you believe that your system was attacked by malware and you can't delete it in a standard way, access Safe Mode with Networking and perform a full system scan from there:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Critical Security alert and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting malware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ JASON FITZPATRICK. What’s the Difference Between a VPN and a Proxy?. How-to Geek. Site that explains technology.
- ^ Phishing. Wikipedia. The Free Encyclopedia.
- ^ Josh Fruhlinger. What is ransomware? How it works and how to remove it. CSO. Security news, features and analysis about prevention.
- ^ The AntiSocial Engineer. Twitter. Social Network.
- ^ NoVirus. NoVirus. Security and Spyware News.
