CRYPTCAT ransomware (virus) - Free Guide
CRYPTCAT virus Removal Guide
What is CRYPTCAT ransomware?
CRYPTCAT ransomware is a malicious computer program designed by criminals for the purpose of extortion
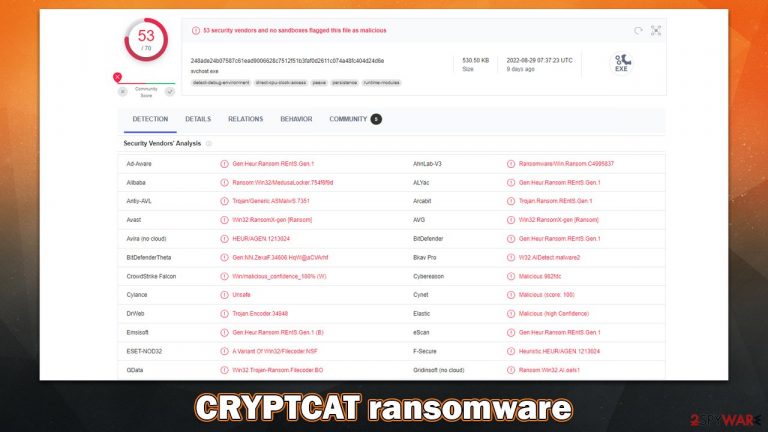
CRYPTCAT is a ransomware-type virus designed to infect Windows computers and lock all personal files on them. The ultimate goal of the attackers is to make people pay the ransom in digital currency, and the more people do so, the more illegal profits they get. Of course, this is really damaging to users, as they are risking not only losing their personal files but also the money they might pay as a ransom.
Upon infiltration of the system, CRYPTCAT ransomware immediately encrypts[1] all pictures, documents, databases, videos, and other valuable files, appending the .crxxx extension to each of them (contact email and victim's ID are also present on each of the altered files). This way, all the data can no longer be opened, regardless of which program is used to do so; for example, a picture won't open regardless if the Photos app or Paint is used.
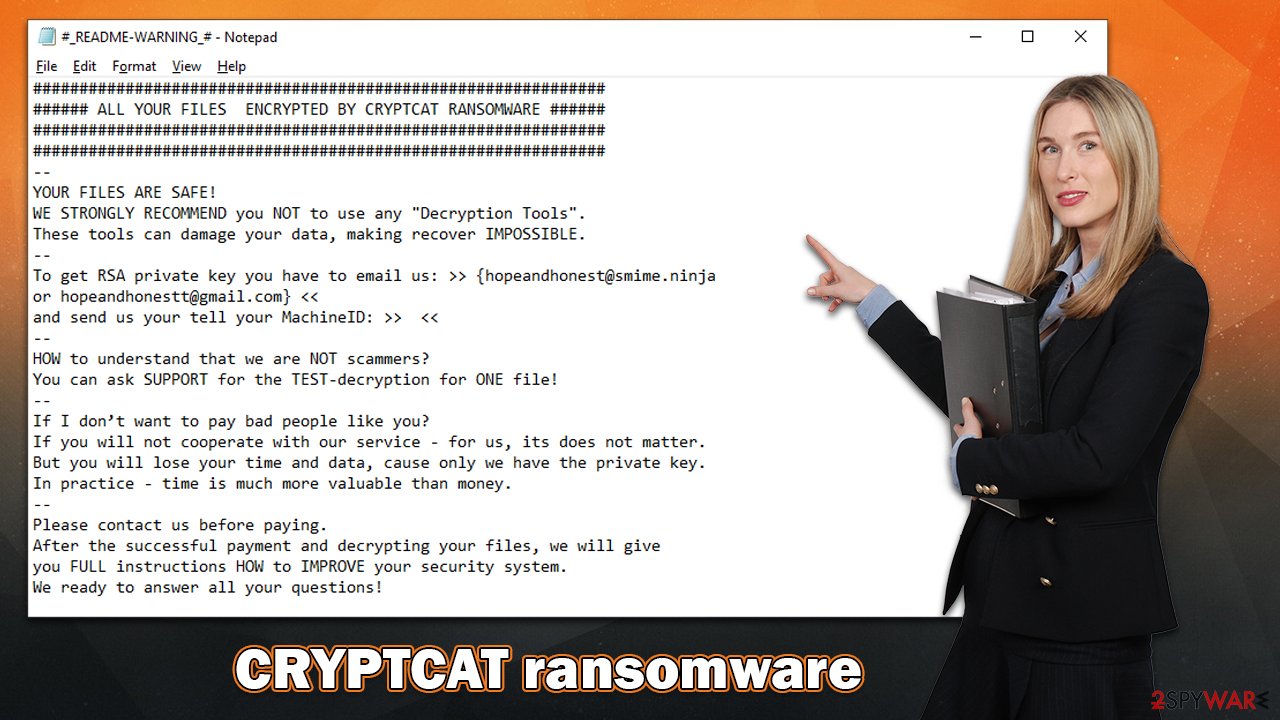
In the #_README-WARNING_#.TXT ransom note, crooks explain in detail what has happened and how users can allegedly remediate the situation – pay the ransom. For communication, they provide hopeandhonest@smime.ninja and hopeandhonestt@gmail.com emails.
| Name | CRYPTCAT virus |
|---|---|
| Type | Ransomware, file-locking malware |
| File extension | .crxxx |
| Ransom note | #_README-WARNING_#.TXT |
| Contact | hopeandhonest@smime.ninja and hopeandhonestt@gmail.com |
| File Recovery | If you want to guarantee the safety of your files, the only secure way to restore them is by using data backups. If you don't have any available or they were encrypted as well, options for recovery are very limited – see all possible solutions below. |
| Malware removal | Disconnect the computer from the network and internet and then perform a full system scan with SpyHunter 5Combo Cleaner security software |
| System fix | If malware manages to infect your device, it might severely damage or delete some vital system files – which often leads to crashes, errors, and other stability issues. You can use FortectIntego PC repair software to automatically fix any such damage by replacing corrupted files |
The note from the ransomware authors and how to react to it
CRYPTCAT virus is new in the cybersecurity landscape – it is yet another way to monetize via the illegal ransomware business. Since malware operation is highly anonymous and there don't seem to be any similarities with more established ransomware strains like Djvu or Zeppelin, it is likely to be yet another group of people willing to monetize the incredibly lucrative ransomware business.
Just like any other malware of this type, it seeks to profit from ransom payments. The only way victims will pay is if they are provided with the information on how to do so, and that's precisely what the #_README-WARNING_#.TXT ransom note is there for. Here's the full text shown within the text file:
##############################################################
###### ALL YOUR FILES ENCRYPTED BY CRYPTCAT RANSOMWARE ######
##############################################################
##############################################################
—
YOUR FILES ARE SAFE!
WE STRONGLY RECOMMEND you NOT to use any “Decryption Tools”.
These tools can damage your data, making recover IMPOSSIBLE.
—
To get RSA private key you have to email us: >> {hopeandhonest@smime.ninja
or hopeandhonestt@gmail.com} <<
and send us your tell your MachineID: >> <<
—
HOW to understand that we are NOT scammers?
You can ask SUPPORT for the TEST-decryption for ONE file!
—
If I don’t want to pay bad people like you?
If you will not cooperate with our service – for us, its does not matter.
But you will lose your time and data, cause only we have the private key.
In practice – time is much more valuable than money.
—
Please contact us before paying.
After the successful payment and decrypting your files, we will give
you FULL instructions HOW to IMPROVE your security system.
We ready to answer all your questions!
In a typical fashion of trying to convince victims to pay the ransom, crooks even declare they can provide a free decryption service of one or a few files which hold no valuable information in order to prove that the decrytpion is actually possible. In fact, they even affirm to users that they are indeed not scammers.
However, we recommend not taking these words at face value, as there is simply no guarantee that hackers would deliver the decryption tool that would restore the encrypted CRYPTCAT virus files back to normal. Instead, we recommend choosing an alternative route and trying the other methods we show below, although don't forget that malware elimination should always come first.
Removal of ransomware
For first-time ransomware victims, the malware can be especially confusing and difficult to understand. Ransomware usually involves data encryption, which means that even after the virus is gone, your data may still be corrupted. There are also many characteristics that users don't know about ransomware, so making mistakes could result in permanent data loss in some cases.
Thus, it is critical to use the proper methods when removing malware. To begin, you must ensure that the virus is unable to communicate with a remote Command & Control[2] server, which attackers frequently employ in order to issue commands for execution. In certain circumstances, additional payloads may be delivered to your computer, resulting in even more damage.
Therefore, your first task is to make sure that the connection between malware and the remote server is broken, and the only way of doing that is by disconnecting the system from the internet and network. Here's how:
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet

- Click Network and Sharing Center

- On the left, pick Change adapter settings

- Right-click on your connection (for example, Ethernet), and select Disable

- Confirm with Yes.
Once you've confirmed the system isn't connected to any network, use sophisticated anti-malware software to perform a full system scan. Programs like SpyHunter 5Combo Cleaner or Malwarebytes can detect and remove all malicious components from the system as well as any secondary payloads that might be present.
How to recover data without paying
After the malware is eliminated from a system and its affected network, the encrypted data will not be reverted to its previous condition. This is because decrypting involves the use of a unique key, which is held by ransomware perpetrators on the said remote server.
The best way to prevent your personal data from being held captive in a ransomware attack is to have backups of all your important files. If you don't have any backups prepared, recovering your CRYPTCAT ransomware-encrypted data might prove to be quite difficult.
Without backups, you can either use data recovery software or wait for a decryptor tool to become available. Keep in mind that if you don't already have working backups, it's advisable that you make copies of all encrypted files so as not accidentally corrupt them during the process of trying to recover them.
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

Experts in the field of digital forensics are frequently employed on decryption tools for prominent ransomware variants. In some circumstances, flaws in the encryption method may be identified or criminal servers seized by law authorities agencies. Regardless, you can check for decryptors on the following pages, but keep in mind that it might take a long time before there's a working one available.
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

Fix your damaged system times
After virus infection, Windows is no longer the same; certain system files could be damaged or even deleted. This can lead to system instability, including crashes, program launches that fail to complete properly, BSODs,[3] and other problems. If you're having difficulties launching programs or experiencing other issues after removing the malware, utilize data recovery software as described below.
- Download FortectIntego
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ What is encryption? Data encryption defined. IBM. Security research.
- ^ Marc Dahan. What are command and control attacks and what can you do to avoid them?. Comparitech. Tech researched, compared and rated.
- ^ Chris Hoffman. Everything You Need To Know About the Blue Screen of Death. How-to Geek. Site that explains technology.
