Dark ransomware (virus) - Recovery Instructions Included
Dark virus Removal Guide
What is Dark ransomware?
Dark ransomware is a VoidCrypt variant that demands ransom payment for a decryption tool
Dark ransomware is a data-encrypting virus that was made by cybercriminals for money extortion. This Windows virus enters users' machines using some kind of phishing methods, such as spam emails or repackaged software installers. Once on the system, it immediately looks for documents, databases, pictures, and other valuable files and ends up locking them with sophisticated encryption algorithms RSA and AES.[1]
From this point in time, users can no longer open personal data on the system, although it is important to note that it's not corrupted. Each of the files is appended with .(ID)((Darksight@tutanota.com).dark extension, and are stripped from their default icons – blank icons are used instead. In order to unlock these files, the cybercriminals behind the attack are asking to pay a ransom in bitcoin, a highly anonymous digital currency.
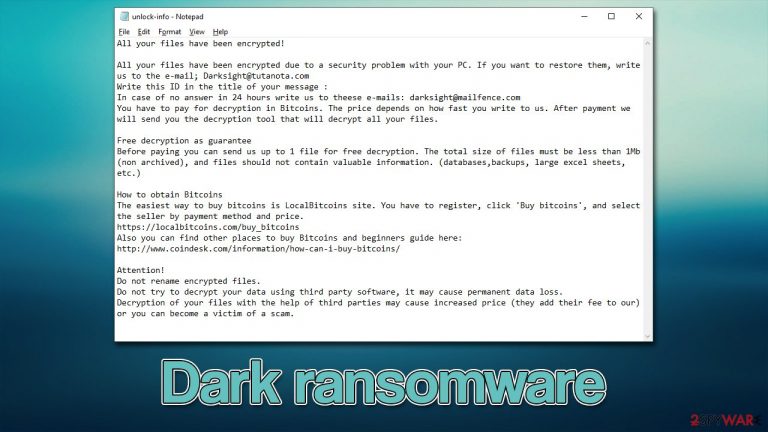
For information purposes, the Dark ransomware virus delivers a ransom note titled unlock-info.txt. In it, users can find out the communication emails (Darksight@tutanota.com, darksight@mailfence.com) and what they need to do to recover their files. We recommend avoiding any contact with malicious actors, as the chance of being scammed remains relatively high.
| Name | Dark virus |
|---|---|
| Type | Ransomware, file-locking malware |
| File extension | .(ID)((Darksight@tutanota.com).dark |
| Malware family | VoidCrypt |
| Ransom note | unlock-info.txt |
| Contact | Darksight@tutanota.com and darksight@mailfence.com |
| File Recovery | The only secure way to restore files is by using data backups. If such is not available or were encrypted as well, options for recovery are very limited – we provide all possible solutions below |
| Malware removal | Disconnect the computer from the network and internet and then perform a full system scan with SpyHunter 5Combo Cleaner security software |
| System fix | Once installed on the system, malware might seriously damage some system files, resulting in crashes, errors, and other stability issues. You can employ FortectIntego PC repair to fix any of such damage automatically by replacing system corruption |
VoidCrypt and its characteristics
Dark ransomware virus stems from quite a prominent malware family known as VoidCrypt, which first appeared on the web in the spring of 2020 from its predecessor Ouroboros malware. These ransomware variants have already been described by us previously and include names such as 1more, Linda, Moonshadow, and many others. Not all victims that pay the ransom receive the decryption tool, so cooperating with crooks behind this strain is quite risky.
This malware family is known for its usage of rather extensive combinations of extensions that are appended to the affected files. They usually incorporate a unique user ID, a contact email, and an extension such as Dark. While initial versions use a combination of AES and RSA to lock data, the encryption method may vary slightly from version to version.
The ransom note
The ransom note unlock-info.txt is delivered right after the file encryption process is complete. This is a very typical ransomware behavior – once the main job is finished, the malware authors are keen to let victims know what has happened to their files so they can hurry with the payment. Here's the full message of the Dark ransomware:
All your files have been encrypted!
All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail; Darksight@tutanota.com
Write this ID in the title of your message :
In case of no answer in 24 hours write us to theese e-mails: darksight@mailfence.com
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the decryption tool that will decrypt all your files.Free decryption as guarantee
Before paying you can send us up to 1 file for free decryption. The total size of files must be less than 1Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)How to obtain Bitcoins
The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click 'Buy bitcoins', and select the seller by payment method and price.
https://localbitcoins.com/buy_bitcoins
Also you can find other places to buy Bitcoins and beginners guide here:
http://www.coindesk.com/information/how-can-i-buy-bitcoins/Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
While the attackers are talking about being scammed, they are the people who can scam you. The illegal business practices alone should warrant you not trusting them, so we highly advise you not to communicate with them. If you agree to pay, it will show crooks that their operations work as intended and prompt them to exploit more innocent people. Instead, we advise trying alternative data recovery solutions we provide below.
Remove the virus
You should never attempt to recover your data straight away, as the infection could still be very active in your system to encrypt all the incoming files. While many ransomware infections self-destruct after performing the data locking process, they are also very well known for being spread along other malware or could use additional modules for data stealing or other malicious purposes.
Therefore, the first thing you should do is download and install SpyHunter 5Combo Cleaner, Malwarebytes, or another reputable security software and perform a full system scan. It would be best to disconnect your device from the network first – you can simply pull out your internet cable or disconnect the Wi-Fi connection. If this attempt is unsuccessful, you can access Safe Mode and remove the virus from there:
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on the Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find the Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.

How to recover .dark files without paying?
Those infected by ransomware have never had it happen before, hence they often don't know where to start. There are also a lot of assumptions about how ransomware and its encryption process works, a lot of which are not quite correct.
For example, some users believe that their personal files would be reverted to normal as soon as they perform a full system scan with security software. This is not correct at all, as anti-malware is not designed to restore ransomware-locked files – its main goal is to remove infected files from the system to ensure its integrity.
Likewise, some people believe that ransomware-affected data is permanently damaged, which is not true either. There is a chance of restoring it, either by acquiring a unique decryption key (which is in possession of cybercriminals) or by applying alternative methods – waiting for a free decrytpion software to be developed is one of the options. Below you will find links that could be useful to find a decryption tool if such were created in the future:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

While it is unlikely to restore all encrypted files using recovery software, it is not impossible. For some users, this option may work very well, while for others – not so much. Nonetheless, we recommend trying it:
Note: Make sure you make backups of locked files before you proceed, or you might corrupt them beyond repair
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
Malware can cause serious damage to Windows systems to the point where a full reinstallation could be required. For example, an infection can alter the Windows registry[2] database, damage bootup, and other sections, delete or corrupt DLL files,[3] etc. Antivirus software can't repair damaged files, and a specialized app should be used instead – FortectIntego is one of the best choices out there.
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Ron Franklin. AES vs. RSA Encryption: What Are the Differences?. Precisely. Data security blog.
- ^ Tim Fisher. What Is the Windows Registry?. Lifewire. Tech News, Reviews, Help & How-Tos.
- ^ Tim Fisher. What Is a DLL File?. Lifewire. Tech News, Reviews, Help & How-Tos.
