Defender-pro-2022.xyz ads (fake) - Tutorial
Defender-pro-2022.xyz ads Removal Guide
What is Defender-pro-2022.xyz ads?
Defender-pro-2022.xyz is a fake site designed by cybercriminals to profit from software downloads and link clicks
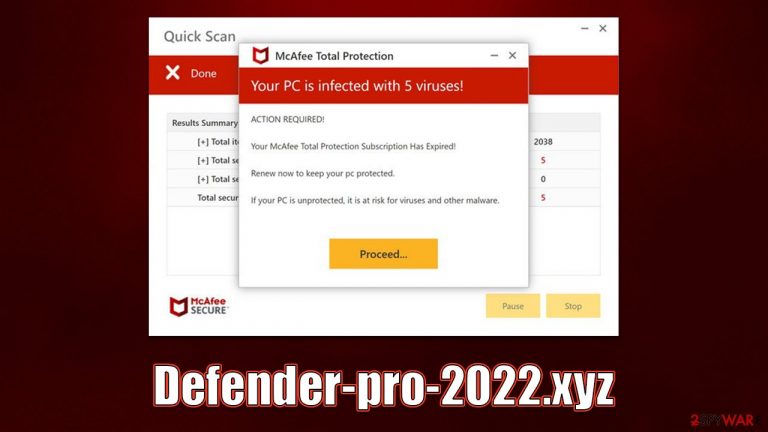
Defender-pro-2022.xyz is a website that specializes in showing misleading virus infection alerts to users. Its operation is rather straightforward: it tries to persuade users that their computers have been infected with malware and that they should get rid of it as soon as possible. It then makes a convenient recommendation to click on the link to buy security software.
Defender-pro-2022.xyz employs a number of techniques to make the scheme seem more convincing. It first makes an effort to mimic a complete system scan that is often carried out by anti-malware software. Additionally, it makes use of the well-known cybersecurity vendor McAfee; typically, it takes users to the official website's security app purchasing page.
However, scammers are behind the entire operation – they want to make money via affiliate marketing. Every time a user makes a purchase using this, fraudsters receive a commission. It goes without saying that such fake schemes should not be treated, as the fake activities would only continue, fooling more people in the future.
Furthermore, scam messages frequently encourage the installation of potentially unwanted programs, which may actually damage the computer rather than fix it. As a result, in order to prevent the system from being infected with malware or adware, we advise against clicking on the promoted links and, instead, checking your device properly with adequate tools.
| Name | Defender-pro-2022.xyz |
| Type | Scam, phishing, redirect, adware |
| Operation | The fake message claims that the system has been infected with malware, which needs to be removed with the promoted software |
| Distribution | Compromised websites, pop-up ads, potentially unwanted applications |
| Risks | Installation of PUPs or malware, sensitive information disclosure, financial losses |
| Removal | Do not click any links or download software from the scam site. If you did, immediately scan your system with SpyHunter 5Combo Cleaner security software |
| Other tips | To make sure that third parties can no longer track your online activities, we suggest clearing browser caches and other leftover PUP files with FortectIntego |
How users end up on scam sites
Online fraud has been around since the internet became more popular in the 90s – as soon as fraudsters realized that it could be used to swindle money away or infect people with malware for various reasons. Over time, the protection measures implemented by tech companies and regulators have improved the situation; for example, one can hardly get infected with malware after following a link from Google search results.
However, scam content is still very prevalent on the internet, and there are certain ways how users can easily get exposed to it, and that's insecure high-risk websites. Peer-to-peer[1] networks and similar dangerous places that distribute illegal software installers are known for their malicious ads and fake links that may immediately lead users to Defender-pro-2022.xyz or much more dangerous websites. Besides, these places are common ground for malicious executables known as cracks that often hide malicious code inside.
In other cases, people may also be rerouted to suspicious phishing[2] websites due to adware running on their systems without their knowledge. Since these potentially unwanted applications are spread using software bundles[3] or other deceptive methods, which often make users miss the entry moment. Once installed, the adware may increase the number of advertisements one sees while browsing the web, promote unsafe links and track user activity in the background.
How the scam operates
Fake online messages are typically created to generate revenue from advertisements, software downloads, or arbitrary service subscriptions. In this scenario, fraudsters are operating an affiliate program that is generally not breaking any rules. However, the advertising of the product in such a misleading way is not adequate, which is an important point here.
If people are concerned that their personal safety and computer security are in danger, they are more inclined to take action and buy a security software license. Thus, a somewhat convincing scam scheme is produced.
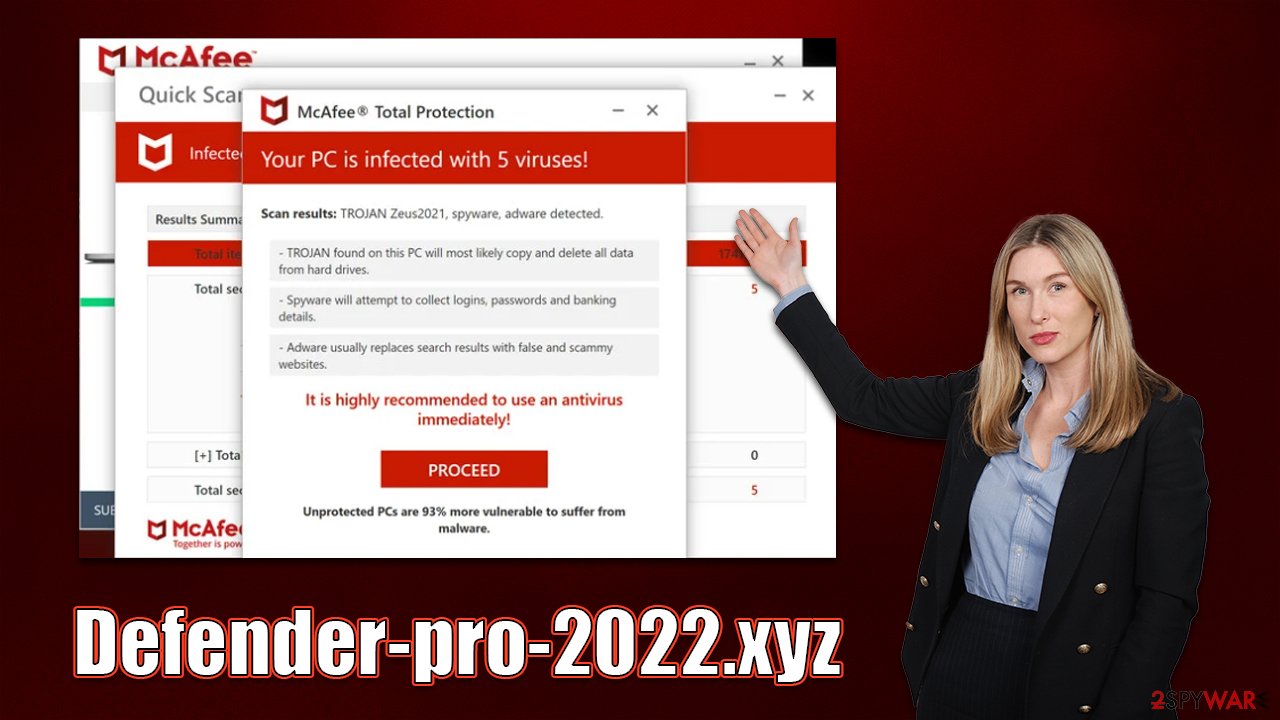
The moment customers arrive at the Defender-pro-2022.xyz website, they are faced with what appears to be authentic McAfee security software that launches an immediate scan and displays a number of “detection” windows to the users. Following that, they are shown fake results that state:
Your PC is infected with 5 viruses!
ACTION REQUIRED
Your McAfee Subscription Has Expired!
Renew now to keep your PC protected.
If your PC is unprotected, it is at risk for viruses and other malware.
Once again, the security vendor has nothing to do with this scheme, which is fabricated by culprits. All users who visit the site are presented with these results, which by no means represent the real state of one's computer security state.
It directs users to the download page by stating that five viruses have been identified and that the security software license has expired. Please be aware that any statements concerning internet virus infections are untrue, as only a reliable anti-malware program installed on the computer can identify installed infections.
How to deal with the situation
Even though the Defender-pro-2022.xyz message is utterly untrue and without merit, you shouldn't completely rule out the possibility of computer infection. Adware infections are known to make users more likely to come across phishing content online and to experience heavy ad load while browsing the web.
We strongly advise checking your device even if you are not experiencing any symptoms of infection because malware is quite effective at concealing its presence. The simplest way to accomplish this is to run a complete system scan with SpyHunter 5Combo Cleaner, Malwarebytes, or another powerful anti-malware program. You can also check for unwanted programs yourself, although keep in mind that manual removal may not always be effective:
Windows
- Enter Control Panel into the Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

Mac
While moving apps into Trash is usually how you delete most normal applications, adware tends to create additional files for persistence. Thus, you should look for .plist and other files that could be related to the virus. If you are not sure, skip this step entirely.
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
Then, you might look for any installed extensions in the browser. Because it is simple to build, adware is frequently distributed via browser extensions. By selecting the “Extensions” button next to your browser's menu, you can quickly and easily remove any unwanted add-ons. Then, using FortectIntego, you can clean your web browsers and fix corrupt system files.
In addition to a deceptive message that displays fake virus infections, users are offered the option to enable push notifications upon entering the website. Even if you unintentionally hit the “Allow” button in the notification box, it would result in unsolicited push notifications being displayed at random intervals and would bring unwanted and harmful links.
If you have already checked your system for infections and are sure that they are all taken care of, you should also make sure you block Defender-pro-2022.xyz from displaying unwanted ads via the push notification prompt – follow the instructions below.
Getting rid of Defender-pro-2022.xyz ads. Follow these steps
Stop browser notifications
Remove unwanted notifications from Google Chrome (desktop):
- Open Google Chrome browser and go to Menu > Settings.
- Scroll down and click on Advanced.
- Locate Privacy and security section and pick Site Settings > Notifications.
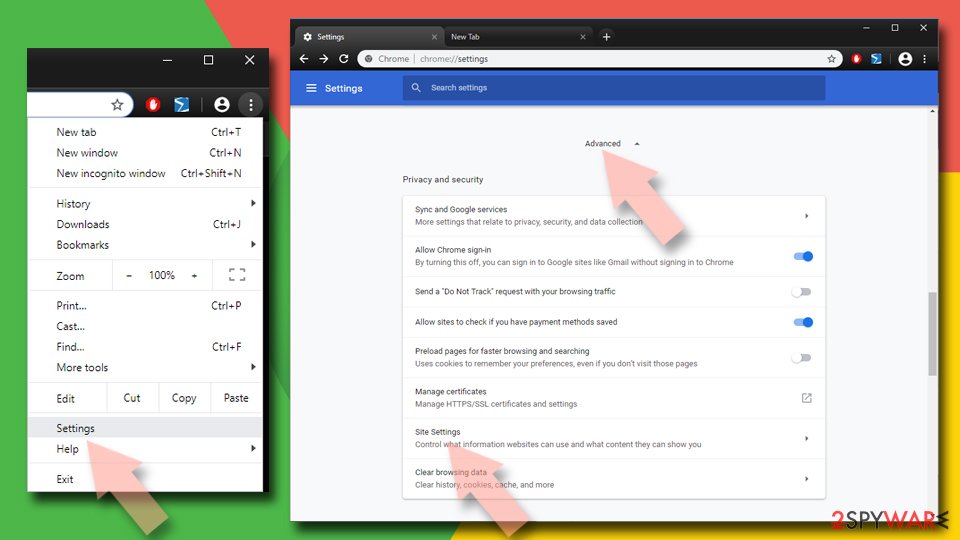
- Look at the Allow section and look for a suspicious URL.
- Click the three vertical dots next to it and pick Block. This should remove unwanted notifications from Google Chrome.

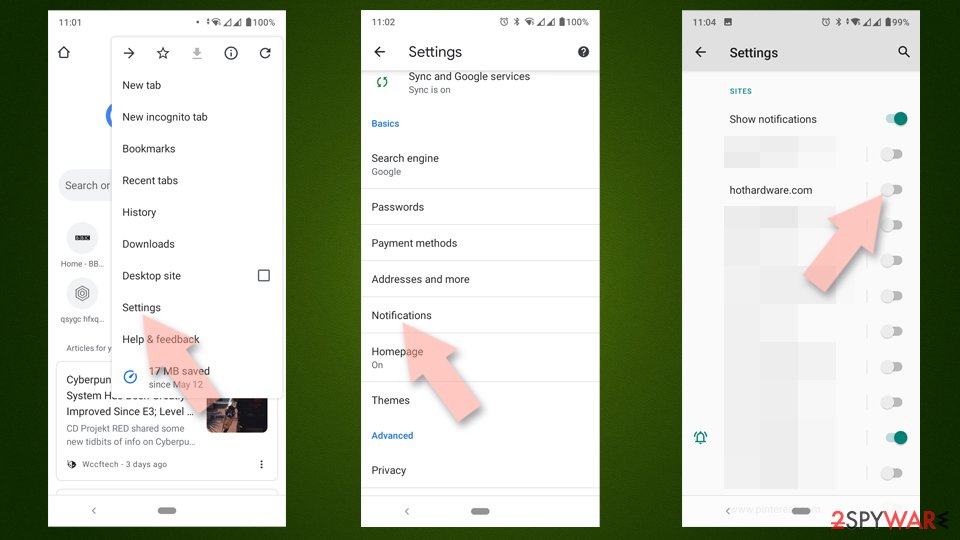
Remove unwanted notifications from Google Chrome (Android):
- Open Google Chrome and tap on Settings (three vertical dots).
- Select Notifications.
- Scroll down to the Sites section.
- Locate the unwanted URL and toggle the button to the left (Off setting).
Remove unwanted notifications from Mozilla Firefox:
- Open Mozilla Firefox and go to Menu > Options.
- Click on Privacy & Security section.
- Under Permissions, you should be able to see Notifications. Click the Settings button next to it.
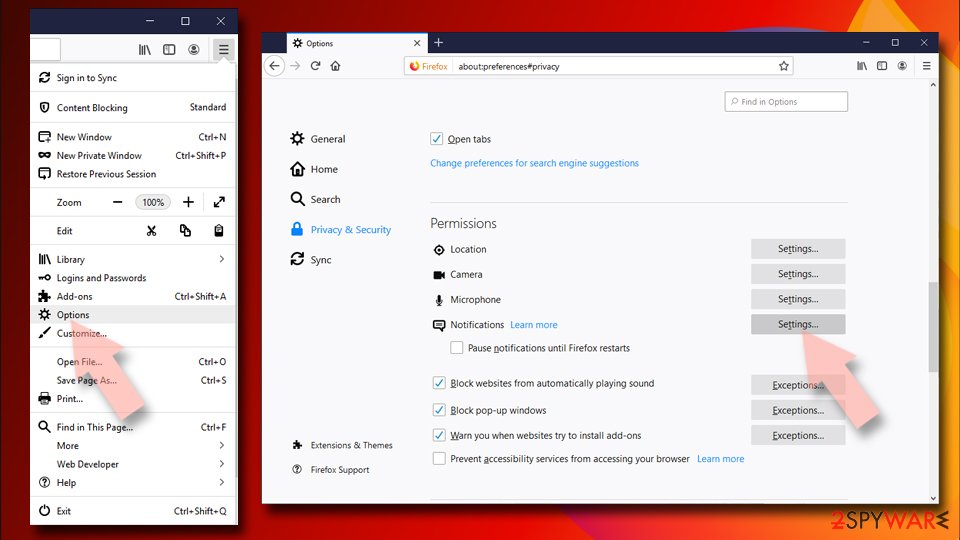
- In the Settings – Notification Permissions window, click on the drop-down menu by the URL in question.
- Select Block and then click on Save Changes. This should remove unwanted notifications from Mozilla Firefox.

Remove unwanted notifications from Safari:
- Click on Safari > Preferences…
- Go to the Websites tab and, under General, select Notifications.
- Select the web address in question, click the drop-down menu and select Deny.

Remove unwanted notifications from MS Edge:
- Open Microsoft Edge, and click the Settings and more button (three horizontal dots) at the top-right of the window.
- Select Settings and then go to Advanced.
- Under Website permissions, pick Manage permissions and select the URL in question.
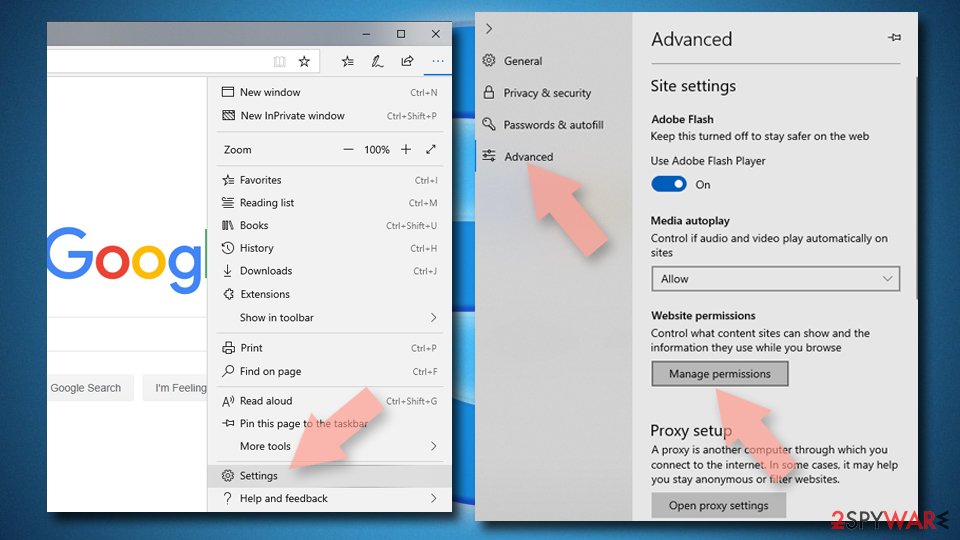
- Toggle the switch to the left to turn notifications off on Microsoft Edge.
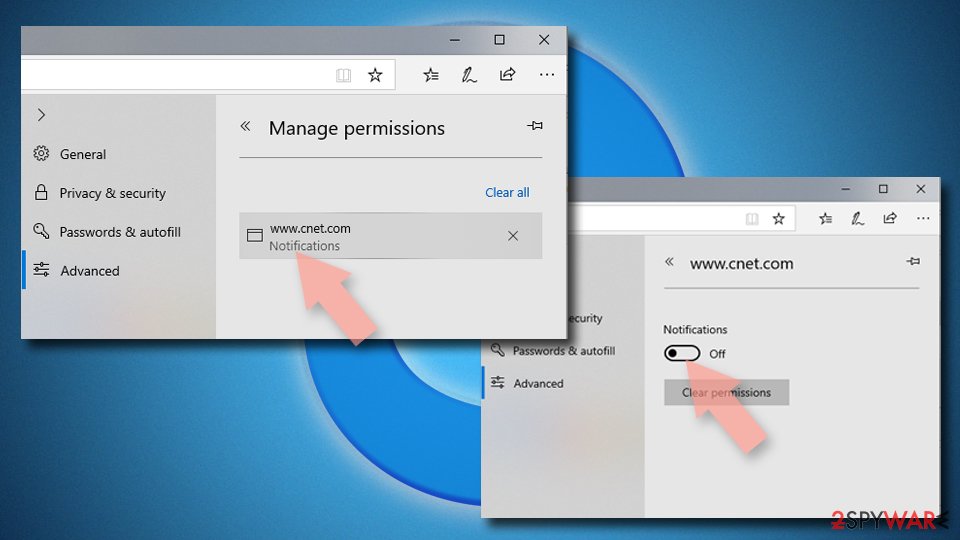
Remove unwanted notifications from MS Edge (Chromium):
- Open Microsoft Edge, and go to Settings.
- Select Site permissions.
- Go to Notifications on the right.
- Under Allow, you will find the unwanted entry.
- Click on More actions and select Block.

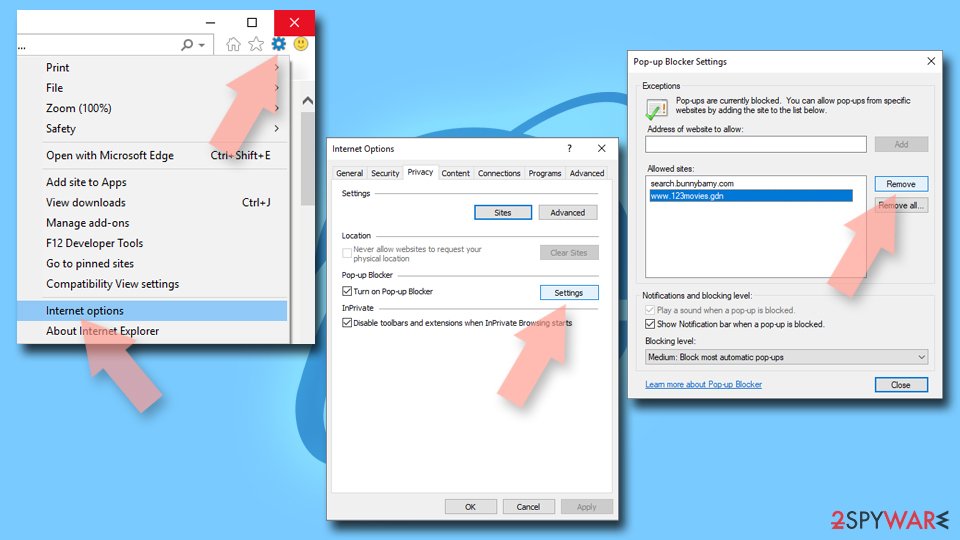
Remove unwanted notifications from Internet Explorer:
- Open Internet Explorer, and click on the Gear icon at the top-right of the window.
- Select Internet options and go to the Privacy tab.
- In the Pop-up Blocker section, click on Settings.
- Locate web address in question under Allowed sites and pick Remove.
How to prevent from getting adware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ James Cope. What's a Peer-to-Peer (P2P) Network?. Computerworld. IT news, careers, business technology, reviews.
- ^ Phishing. Wikipedia. The free encyclopedia.
- ^ Bundled software. Computer Hope. Free computer help.
