Devicespam-shield.com ads (scam) - Free Instructions
Devicespam-shield.com ads Removal Guide
What is Devicespam-shield.com ads?
Devicespam-shield.com is a malicious site that shows fake malware infection messages and asks to enable notifications
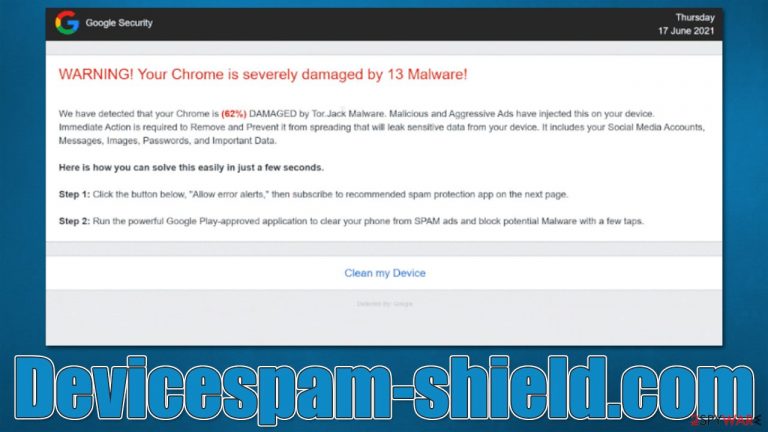
Devicespam-shield.com is a fraudulent website that most users come across whenever they browse high-risk sites or if their system is infected with adware[1] or other malicious software. Upon entry, users are shown various fake messages which claim that Chrome has been infected and damaged by malware. They are then promised a solution for this “problem,” which people directly to an affiliated download link for various software.
You should never trust any website which claims your device is infected and personal information stolen, as there is no way for such a site to find out about this in any way. Only reputable anti-malware installed on your system could provide you with such information.
Devicespam-shield.com also asks users to enable push notifications, which would expand the monetization of scammers even more. Those who accept the request would later suffer from more unwanted ads that would not go away unless the website is blocked via browser settings. We explain how to do that below.
| Name | Devicespam-shield.com |
| Type | Scam, phishing, fraud, fake alert |
| Operation | Claims that Chrome browser has been damaged by malware and that an alleged removal software needs to be downloaded and installed to remediate the issue |
| Risks | Fake messages usually aim for users to download potentially unwanted or malicious programs, steal their personal information or trick them into subscribing to useless services |
| Removal | You should not interact with the content shown by a scam website. Instead, check your system for adware or malware infections with SpyHunter 5Combo Cleaner security software |
| Other tips | After removal of adware and other PUPs, you should take your time to clean your browser from cookies and other trackers – FortectIntego can help you with that |
Scam message analysis
It is evident that people would not intentionally visit scam websites. However, they are willing to engage with places that are considered insecure, including torrents, YouTube video converters, X-rated, and similar websites. After a quick redirect occurs due to a fake link or an automated script, users are hit with a lot of information at once, which is one of the social engineering[2] tricks used by scammers.
Visitors are shown a pop-up message which claims that “Immediate action is required” and that “The device has been compromised.” If the “OK” button is clicked, users are exposed to the following misleading message:
WARNING! Your Chrome is severely damaged by 13 Malware!
We have detected that your Chrome is (62%) DAMAGED by Tor.Jack Malware. Malicious and Aggressive Ads have injected this on your device.
Immediate Action is required to Remove and Prevent it from spreading that will leak sensitive data from your device. It includes your Social Media Accounts, Messages, Images, Passwords, and Important Data.Here is how you can solve this easily in just a few seconds.
Step 1: Click the button below, “Allow error alerts,” then subscribe to recommended spam protection app on the next page.
Step 2: Run the powerful Google Play-approved application to clear your phone from SPAM ads and block potential Malware with a few taps.
Evidently, the crooks make use of a fictitious malware Tor.Jack, which we already described previously. Claiming that the device's personal data is being compromised in various ways is one of the scare tactics used by scammers. It is important to note that everything claimed in this message is a lie, and the main goal of crooks is to make users download software.
A small commission fee is automatically assigned to cybercriminals via the affiliated program with each click users make. Since it is not always possible to track how affiliates advertise products, even legitimate tools might be victims of such schemes. However, there is also a chance that those who would download software from Devicespam-shield.com might get their system infected with various malware, so we strongly recommend not downloading anything.
Removal steps
If you are wondering whether you are infected with a virus just because you were shown a fake message, it is not the case. You might be affected by adware or other PUPs if you notice the increase of ads and other suspicious material you encounter online. However, not all adware show infection symptoms, so we recommend checking the instructions below to remove redirects to Devicespam-shield.com and other phishing websites.
1. Get rid of adware on your device
Before you proceed, we highly advise you to scan your system with SpyHunter 5Combo Cleaner or Malwarebytes security s software. This can eliminate the most aggressive adware and malware on your system, which would otherwise be invisible to you. If you want to check for unwanted programs manually, proceed with the following:
Windows
- Enter Control Panel into the Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

Mac
While moving apps into Trash is usually how you delete most normal applications, adware tends to create additional files for persistence. Thus, you should look for .plist and other files that could be related to the virus. If you are not sure, skip this step entirely.
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
Note that adware can also be installed on the browser as an extension, so please remember to check the installed add-on section, removing everything suspicious. After that, we recommend cleaning the web browsers from cookies and other trackers – FortectIntego can help you do that quicker. The app can also help you fix virus damage if such has occurred due to various infections.
2. Remove Devicespam-shield.com push notifications
Push notifications from malicious websites can also be a huge problem. Upon entry, a pop-up would show, asking whether or not users would allow notifications. If they click the “Allow” button, permission is immediately granted to show any type of information within a special pop-up window, which can be shown at any time, as long as the browser is running.
Since the origins of the request were made by a scam site, those who allow notifications might be exposed to further malicious and misleading content – get-rich-quick schemes, tech support or survey scams,[3] etc. We recommend not to interact with these links and instead perform the following steps to remove them:
Google Chrome
- Open the Google Chrome browser and go to Menu > Settings.
- Scroll down and click on Advanced.
- Locate the Privacy and security section and pick Site Settings > Notifications.
- Look at the Allow section and look for a suspicious URL.
- Click the three vertical dots next to it and pick Block. This should remove unwanted notifications from Google Chrome.

Mozilla Firefox
- Open Mozilla Firefox and go to Menu > Options.
- Click on Privacy & Security section.
- Under Permissions, you should be able to see Notifications. Click the Settings button next to it.
- In the Settings – Notification Permissions window, click on the drop-down menu by the URL in question.
- Select Block and then click on Save Changes. This should remove unwanted notifications from Mozilla Firefox.

Safari
- Click on Safari > Preferences…
- Go to the Websites tab and, under General, select Notifications.
- Select the web address in question, click the drop-down menu and select Deny.

MS Edge (Chromium)
- Open Microsoft Edge, and go to Settings.
- Select Site permissions.
- Go to Notifications on the right.
- Under Allow, you will find the unwanted entry.
- Click on More actions and select Block.

How to prevent from getting adware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Adware. Wikipedia. The free encyclopedia.
- ^ Social Engineering. Imperva. Application and data security.
- ^ Anatomy of a survey scam – how innocent questions can rip you off. Sophos. Naked Security Blog.
