Efji ransomware (Virus Removal Instructions) - Free Guide
Efji virus Removal Guide
What is Efji ransomware?
Efji ransomware – a file renaming virus that will lock down all your data asking for money to recover your docs
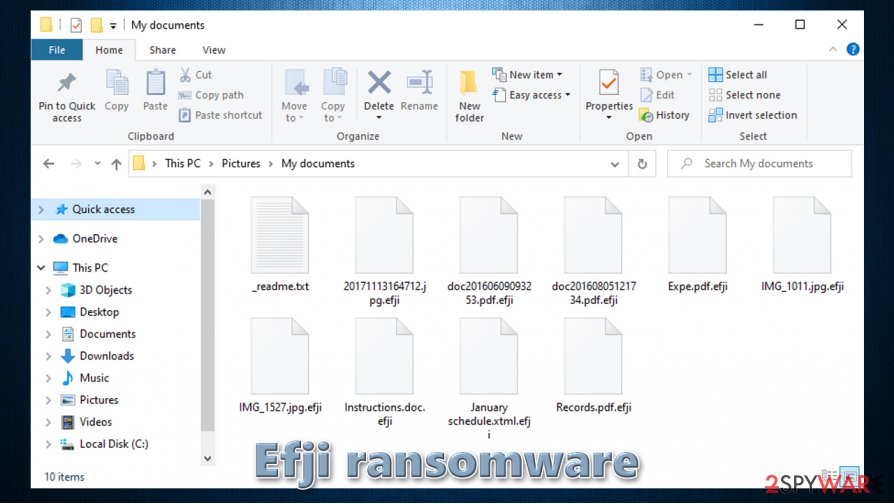
Efji ransomware is a computer virus that is designed to encrypt all pictures, music, documents, databases, and other files on users' machines by appending .efji extension to them. Suchlike files can no longer be modified or opened and lose original icons. The malware belongs to a well-known family of Djvu – it is known to be spread via fake installers, cracks, and malicious websites hosting pirated software. This variant was first spotted in the second half of October 2020 and is an addition to other 257 versions released so far.
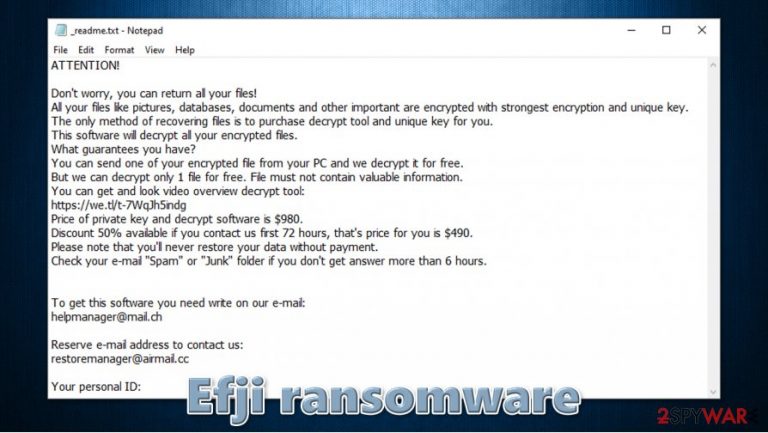
Once installed, the Efji virus drops a ransom note _readme.txt, which explains to victims what happened to their files. Crooks claim that only they have access to a decryption key that is required to unlock all the files and ask for $980/$490 for it, to be paid in bitcoin. To establish communication, hackers provide two email addresses – helpmanager@mail.ch or restoremanager@airmail.cc, although security experts recommend avoiding all contact. Since the Efji ransomware virus is a part of Djvu, users whose files were encrypted with an offline ID could recover their files with a free decryptor available from Emsisoft.
| Name | Efji ransomware / efji virus / .efji files virus |
| Type | File locking virus, crypto-malware |
| Malware family | Djvu/STOP |
| Distribution | Software cracks, pirated programs, and other malicious installers downloaded from insecure sites |
| Encryption method | RSA |
| File extension | .efji; an example of an encrypted file – “picture.jpg.efji” |
| Ransom note | _readme.txt is delivered to several computer locations |
| Contact | helpmanager@mail.ch or restoremanager@airmail.cc |
| Malware removal | To completely terminate malware from the infected computer, a full system scan with powerful anti-malware should be performed |
| Data recovery |
The only secure method to recover files safely is by copying them from backups. Other options include:
|
| Windows fix | In some cases, ransomware or other threats might seriously damage Windows systems to the point that the OS needs to be reinstalled. To avoid that, we recommend trying to fix the virus damage instead with tools such as FortectIntego |
Efji ransomware targets almost all versions of 64 and 32-bit Windows machines – its primary executable can be named as anything, although, since malware is distributed via software cracks, it is likely to be named as such. This particular variant can be detected by most security applications, so users should never ignore these warnings (in other words, Efji removal will be performed before malware managers to encrypt any files). On Virus Total, the virus is detected as follows:[1]
- HEUR:Trojan.Win32.Bsymem.gen
- Ransom:Win32/STOP.BS!MTB
- Trojan.GenericKDZ.70771
- Win32:MalwareX-gen [Trj]
- Generic.mg.033215ae5330dc16, etc.
As soon as the Efji virus manages to access the computer, it modifies the Windows registry, deletes Shadow Copies, drops many malicious files, modifies Windows “hosts” file, establishes background connections, and performs other system changes, which are meant to prepare the system from the encryption process to be successful. These modifications might be difficult to reverse with regular anti-malware tools, so we recommend using FortectIntego for this process.
Computer modifications are then following with data encryption – Efji ransomware targets the most commonly-used personal file types, including PDF, RAR, JPG, DOC, and many others. It is evident that the attackers intend to cause maximum damage to victims to increase the possibility of a ransom payment.
Once the encryption is complete, the Efji virus delivers the following ransom note:
ATTENTION!
Don't worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-7WqJh5indg
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don't get answer more than 6 hours.To get this software you need write on our e-mail:
helpmanager@mail.chReserve e-mail address to contact us:
restoremanager@airmail.ccYour personal ID:
Crooks offer you a decryption tool for $980, although they also say that they are willing to drop that price by 50% if you contact them fast enough. They also provide a seemingly “free” test decryption that is meant to serve as proof that the .efji file extension can be removed with the help of the tool they have. Despite all this, security experts[2] advise avoiding all contact with criminals, as they might never provide the required decryptor, despite the payment.
Many ransomware self-delete after the encryption is performed, although you should still remove Efji ransomware with powerful anti-malware tools, such as SpyHunter 5Combo Cleaner or Malwarebytes. This is because there is still a possibility that malware will continue to encrypt the incoming files, and it is also known to drop a data-stealing module on the PC (you might disclose your sensitive information, such as logins and banking information, to the attackers). Besides, variants of Djvu were previously spread with other malware, so additional infections could be present as well.
How to deal with .efji extension files without backups
As evident, the best way to recover .efji files is by using backups. Unfortunately, most users infected with ransomware never had to deal with it before and never kept the backups for unforeseen circumstances like that. Please keep in mind that ransomware is not the only way you can lose your important files, so it is vital to prepare reliable backups regularly.
So, how can you recover .efji virus files without backups? The answer is not that simple, as the recovery options and the probability depend on many factors. Just to make it clear, anti-malware software will not help you recover your files, despite the popular belief. In other words, you can delete malware-related files, but your personal data will remain encrypted. Security software is simply not designed to restore files encrypted by ransomware.
Ransomware authors use a sophisticated RSA encryption algorithm[3] to lock data, which means that even the most powerful computers would not be able to compute the required key. And unfortunately, only the attackers have access to the unique key needed to unlock .efji files.
Several other methods might be able to help some victims, which include:
- Using Emsisoft decryptor. This tool will only work if your files were locked with an offline ID, i.e., static key. However, somebody with the same ransomware version needs to pay the ransom, retrieve the key, and then share it with Emsisoft researchers. Thus, even if your data is encrypted with an offline ID, it might take some time before you can recover it using the decryptor.
- Third-party recovery programs might sometimes be useful, although they are unlikely to restore all your files.
- In case malware failed to delete built-in Windows backups, you can employ Windows Previous Versions and other methods listed below.
How to use Djvu decryptor from Emsisoft?
Keep in mind that Efji file virus might not be decryptable even for those who have their data encrypted with an offline ID for quite some time. One of the users who got encrypted with this variant needs to retrieve the offline key from the attackers and then share it with Emsisoft security researchers. Thus, if the tool does not work for you yet, you should wait some time and try it later.
Here's how to use it:
- Download Emsisoft's decryptor for Djvu [download link].
- Click on the decrypt_STOPDjvu.exe file at the bottom-left of your browser tab.
- Agree to License Terms.
- Click OK when Disclaimer window shows up.
- The Decryptor should automatically populate the encrypted file folders, although you can add them manually as well by pressing Add folder.
- The tool will run for sometime and report whether your files can be decrypted.
From here, there are three outcomes that are available:
- “Decrypted!” will be shown under files that were decrytped successfully – they are now usable again.
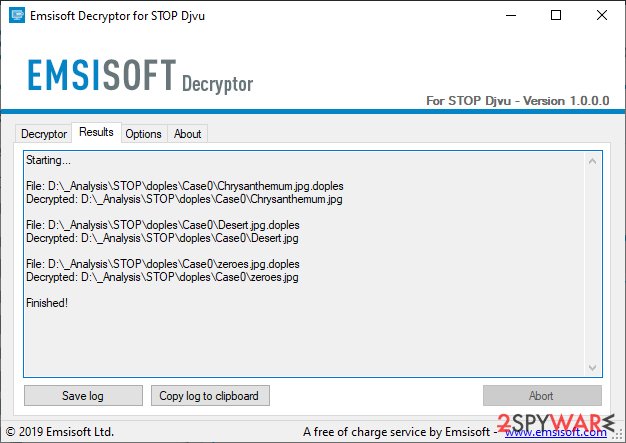
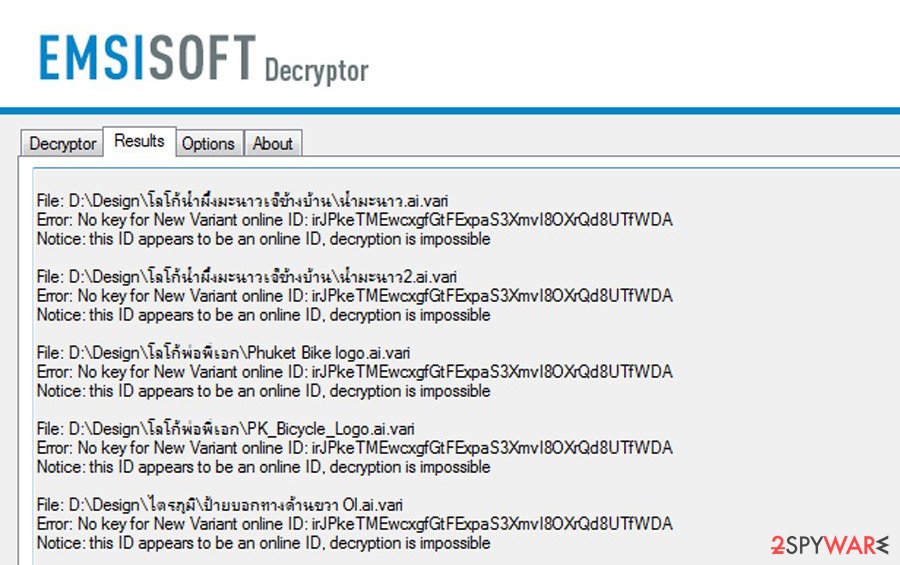
- “Error: Unable to decrypt file with ID:” – this means that the offline keys for this version of Djvu has not been recovered yet (should try later).
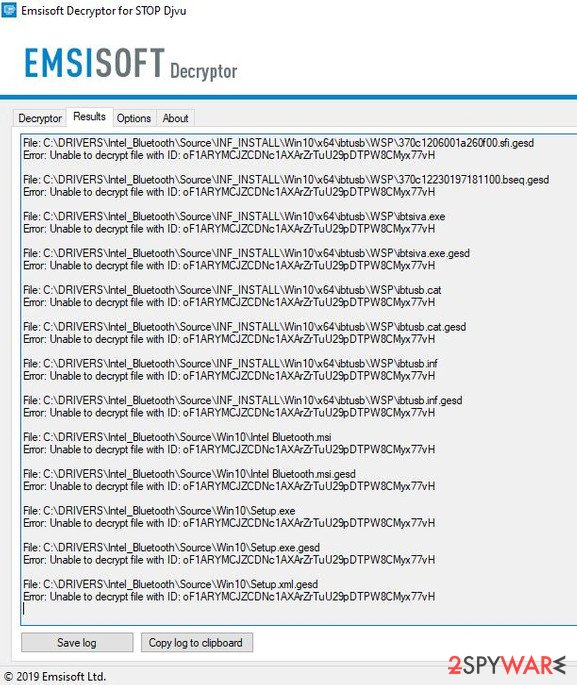
- “This ID appears to be an online ID, decryption is impossible” – as description explains, decryption is not possible with the decryptor.
What else can you do to restore your files?
Efji encrypts all files on the system, including video, music, and others. Since Djvu only encrypts the first 150KB of each of the files, some media players will be capable of playing some of such files, just without the first few seconds that were locked. Besides, you can re-download files such as MP3s from the internet.
You should also not forget about other data recovery methods that should be available for you personally. For example, if you sent an important Excel sheet to your coworker, you can retrieve it from your email. You should also check strage devices such as your phone, USB sticks, and similar – you might find at least some of the important files. Likewise, if you have set the OneDrive or Google Drive backup, you can retrieve your data easily.
Employ correct tools for Efji ransomware removal
First of all, if you were infected with the virus, you will not be able to access most security-focused websites that attempt to help users with Efji ransomware removal, all because of the “hosts” file modification by malware. Therefore, you should go to the following location and delete this file, as it will be re-created automatically without any restrictions (alternatively, if you used the “hosts” file before and added some entries, delete the ones that were added by the malware):
C:\Windows\System32\drivers\etc\
Next, you should copy all the personal files before you remove Efji ransomware from the system. Malware termination might sometimes permanently corrupt files, so it is better to back them up. Note that encrypted data does not hold any malicious code, so it is safe to copy.
You can then delete Efji virus from the computer by using powerful anti-malware solutions, such as SpyHunter 5Combo Cleaner or Malwarebytes (while manual elimination is possible, it is way too difficult for regular computer users). If required, you can also access Safe Mode with Networking as explained below, although this step is not always needed. If you spot that your Windows machine is crashing, lagging, delivering errors and suffering from similar stability issues, it means that some of the system files were damaged. To fix this damage, we recommend using an automated repair tool FortectIntego.
Finally, you can then attempt to retrieve your .Efji files with the help of the instructions we provide in our recovery section below, although keep in mind that chances of success are relatively low (but never zero!). We have also prepared a video guide for you to see the steps of Efji virus removal visually. The video will help you for better understanding of the virus itself and hopefully, you might try recovering the files without paying the ransom.
We also highly recommend you contact your local law enforcement agency if you suffered a ransomware attack – it could help with finding the culprits one day. Here are a few links for particular countries:
- U.S – On Guard Online;
- UK – Action Fraud;
- Germany – Bundesamt für Sicherheit in der Informationstechnik;
- France – Agence nationale de la sécurité des systèmes d’information;
- Australia – SCAMwatch;
- New Zealand – Consumer Affairs Scams;
- Canada – Canadian Anti-Fraud Centre.
If your country is not listed above, visit a police office or a website of the agency dealing with online scams and fraud.
Video guide for Efji ransomware removal and data recovery solutions
Getting rid of Efji virus. Follow these steps
Manual removal using Safe Mode
Use Safe Mode with Networking in case malware is tampering with your security software:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Efji using System Restore
System Restore might have not been delete by the infection:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Efji. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Efji from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Efji, you can use several methods to restore them:
Make use of Data Recovery Pro
Recovery tools might sometimes help you recover at least some of the encrypted files.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Efji ransomware;
- Restore them.
Windows Previous Versions might be useful in some cases
If Efji failed to delete Shadow Copies, you can restore files one-by-one.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Automate data recovery with ShadowExplorer
This tool can quicken the recovery process if malware did not delete Shadow Copies.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Employ a free Djvu decryption tool
Emsisoft provides a free decryption tool that could help victims with offline IDs. Download the decrytpor and scan your machine – the tool should state whether your files can be decrypted or not.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Efji and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ 8fe3cfbb740175ab87865c15e1bdc6178fae520aae9487f9766e9533ef7bddd1. Virus Total. File and URL analysis.
- ^ Dieviren. Dieviren. Cybersecurity advice and malware insights.
- ^ RSA (cryptosystem). Wikipedia. The free encyclopedia.







