STOP ransomware (virus) - 2021 update
STOP virus Removal Guide
What is STOP ransomware?
STOP virus is one of the mote popular ransomware because it is active and constantly evolving
.STOP ransomware is a data locker that first made its appearance in December 2017. The malware uses a combination of AES and RSA algorithms to encrypt data and add .STOP file extension. However, new versions have been emerging almost every month and at the moment the virus is appending the following extensions: .shadow, .keypass, .tocue, .daris, .gusau, .madek, .lapoi, .todar, .dodoc, .novasof, .bopador, .ntuseg, .ndarod, and many others.
The most active variants are Keypass ransomware and Djvu ransomware that made headlines[1] when they targeted victims from over 20 countries. Viruses have been demanding a ransom of $300 – $600 for data decryptor, and using _openme.txt, !readme.txt or similar ransom notes that urge users to contact crooks via restoredjvu@firemail.cc, stopfilesrestore@bitmessage.ch, helpshadow@india.com or similar email addresses.
| Summary of the cyber threat | |
|---|---|
| Name | .STOP ransomware |
| Type | Cryptovirus |
| Encryption algorithm | AES and RSA-1024 |
| Appended file extensions | .STOP, .SUSPENDED , .WAITING, .CONTACTUS, .DATASTOP, .PAUSA, .KEYPASS, .WHY, .SAVEfiles, .DATAWAIT, .INFOWAIT, .puma, .pumax, .pumas, .shadow, .djvu. .djvuu. .djvus, .udjvu, .uudjvu, .kroput1, .charck, .kropun, .doples, .luces, .luceq, .chech, .pulsar1, .proden, .tocue, .daris, .gusau, .madek, .lapoi, .todar, .dodoc, .novasof, .bopador, .ntuseg, .ndarod |
| Ransom notes |
!!! YourDataRestore !!! txt, |
| The size of the ransom | $300 – $600 |
| Contact email addresses |
stopfilesrestore@bitmessage.ch |
| Distribution methods | Malicious spam emails, hacked websites, exploits, brute-force attacks, etc. |
| Decryptor | Download from here. Note that it does not work for all versions of this ransomware |
| To get rid of the ransomware, use anti-spyware software and run a full system scan using FortectIntego to repair damaged files | |
STOP ransomware was initially discovered in December 2017. However, new variants appeared in August 2018 and some previous months. All of them behave similarly but append new file extensions to the targeted data, provide slightly different ransom notes, and use new contact email addresses. That being said, malware has significantly evolved over the years – for example, creators changed the encryption algorithm from AES to a more secure RSA.
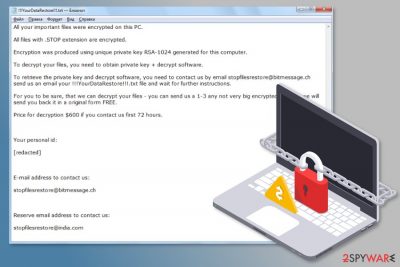
The original version of malware[2] adds .STOP file extension to make files inaccessible on the affected Windows computer. As soon as the virus finishes the encryption procedure, it delivers a ransom note in the “!!! YourDataRestore !!! txt” file. Inside lies the information about the attack, and it becomes clear that they want payment in Bitcoin within 72 hours.
Initially, cybercriminals demanded $600 as a fee for a decryption tool that can be used to unlock personal files. In order to provide proof that they are capable of decrypting data, hackers allow sending 1-3 “not very big” files for free test decryption to stopfilesrestore@bitmessage.ch or stopfilesrestore@india.com. However, even if you receive working files back, there is no guarantee that they will deliver the tool to recover the rest of your pictures, videos, documents, etc.
We want to stress out that paying the demanded ransom to cybercriminals is a very risky process that may lead to a huge money loss. Once you pay the money, you might be asked to pay for more. If you disagree or be left without promised decryption option, no one will help you trace the criminals and get your money. So better avoid any contact with the crooks and check out the official decryptor you can find below this article. Note that it only works for older malware versions.
Therefore, we highly recommend forgetting about data recovery at the moment. The most important task is to remove the ransomware from the computer in order to make the system safe. However, after using anti-malware software, ensure no corrupted files on the affected machine using repair software like FortectIntego.
It's crucial to use professional security tools because this cyber threat might alter Windows Registry,[3] create new keys, install malicious files or affect legitimate system processes. It means that manual termination is nearly impossible. If you try to located and delete these entries yourself, you might cause damage to your machine. Hence, do not risk!
Once you take care of the proper ransomware removal, you can safely plug in an external storage drive with backups or export needed files from cloud storage. If you haven't backed up your files yet and cannot perform full data recovery, you should try the third-party tools that we mentioned at the end of the article. Hopefully, some of the files will be rescued. Furthermore, experts recently released an original decryptor for this ransomware that can recover some data, and we have provided it below the article.
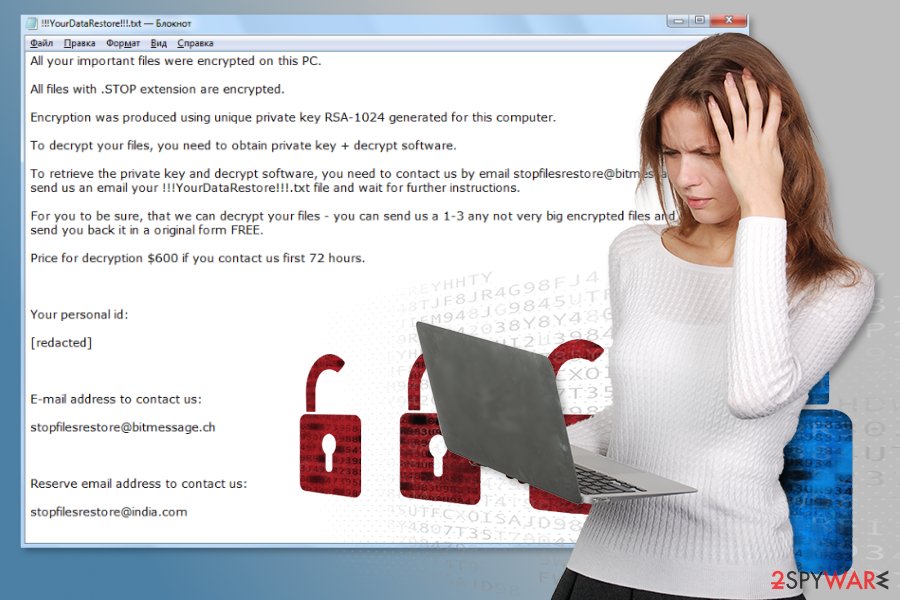
New variants of ransomware have been appearing almost every month in 2020
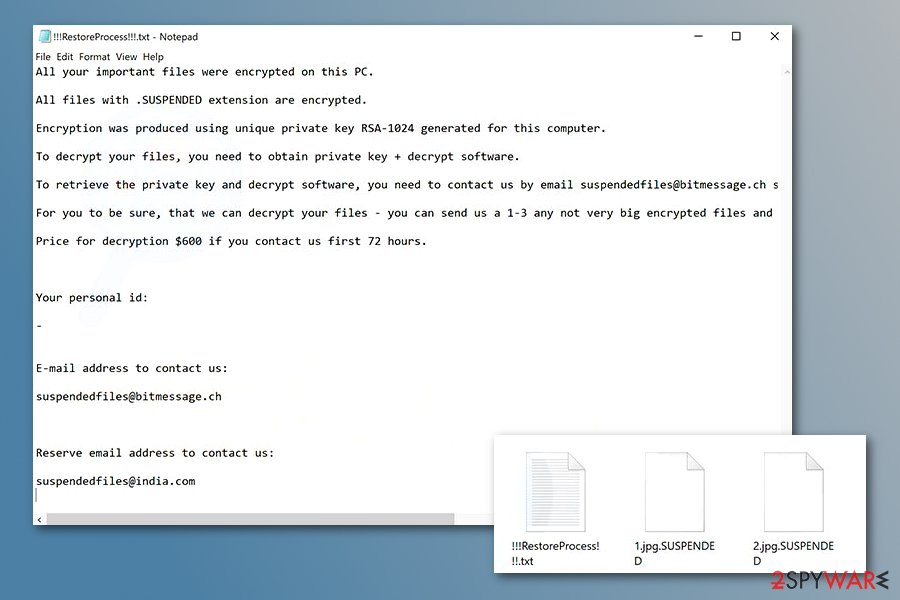
Suspended ransomware
At the beginning of the year, in February, malware researchers reported about STOP variant that uses .SUSPENDED file extension to lock documents, multimedia, databases, archives, and many other files. The behavior of ransomware is similar to the previous version, but it downloads a different ransom note after file encryption.
Suspended ransomware provides recovery instructions in ”!!RestoreProcess!!!.txt file and asks to send unique victim's ID and preferred sample files for the decryption to suspendedfiles@bitmessage.ch or suspendedfiles@india.com email addresses. The size of the ransom and deadline remain the same.
CONTACTUS ransomware
At the end of May, another variant of .STOP ransomware virus hit the surface. This version is using .CONTACTUS file extension to lock targeted files. Not only the appended suffix was changed. Crooks also renamed data recovery instructions, and now the document where all recovery options are provided is called !!!RESTORE_FILES!!!.txt. The contact email addresses were changed to decryption@bitmessage.ch and decryption@india.com:
All your important files were encrypted on this PC.
All files with .CONTACTUS extension are encrypted.
Encryption was produced using unique private key RSA-1024 generated for this computer.To decrypt your files, you need to obtain private key + decrypt software.
To retrieve the private key and decrypt software, you need to CONTACTUS us by email decryption@bitmessage.ch send us an email your !!!RESTORE_FILES!!!.txt file and wait for further instructions.
For you to be sure, that we can decrypt your files – you can send us a 1-3 any not very big encrypted files and we will send you back it in a original form FREE.
Price for decryption $600 if you contact us first 72 hours.Your personal id:
[redacted 40 characters]E-mail address to contact us:
decryption@bitmessage.chReserve e-mail address to contact us:
decryption@india.com
SaveFiles ransomware
SaveFiles is a variant that showed up in September 2018. After using urpress.exe file as the main executable, this ransomware encrypts your data and marks locked files with .SAVEfiles appendix. Like other versions, this threat does this with the help of AES and RSA encryption methods. After the file modification, ransomware places a ransom note called !!!SAVE_FILES_INFO!!!.txt on every file that contains encrypted data.
The ransom note contains the following text:
WARNING!
Your files, photos, documents, databases and other important files are encrypted and have the extension: .SAVEfiles
The only method of recovering files is to purchase an decrypt software and unique private key.After purchase you will start decrypt software, enter your unique private key and it will decrypt all your data.
Only we can give you this key and only we can recover your files.You need to contact us by e-mail BM-2cXonzj9ovn5qdX2MrwMK4j3qCquXBKo4h@bitmessage.ch send us your personal ID and wait for further instructions.
For you to be sure, that we can decrypt your files – you can send us a 1-3 any not very big encrypted files and we will send you back it in a original form FREE.
Price for decryption $500.
This price avaliable if you contact us first 72 hours.E-mail address to contact us:
BM-2cXonzj9ovn5qdX2MrwMK4j3qCquXBKo4h@bitmessage.chReserve e-mail address to contact us:
savefiles@india.comYour personal id:
As you can see, virus developers claim they have the tool for file recovery and decryption and encourage people to contact them via savefiles@india.com email. You shouldn't do that because criminals are not worthy of your trust. Better follow a provided guide to remove STOP ransomware. For that, you can use programs like FortectIntego or SpyHunter 5Combo Cleaner. Perform a full system scan to clean your system further. Then, try data recovery tools or programs and restore your files.
Puma ransomware
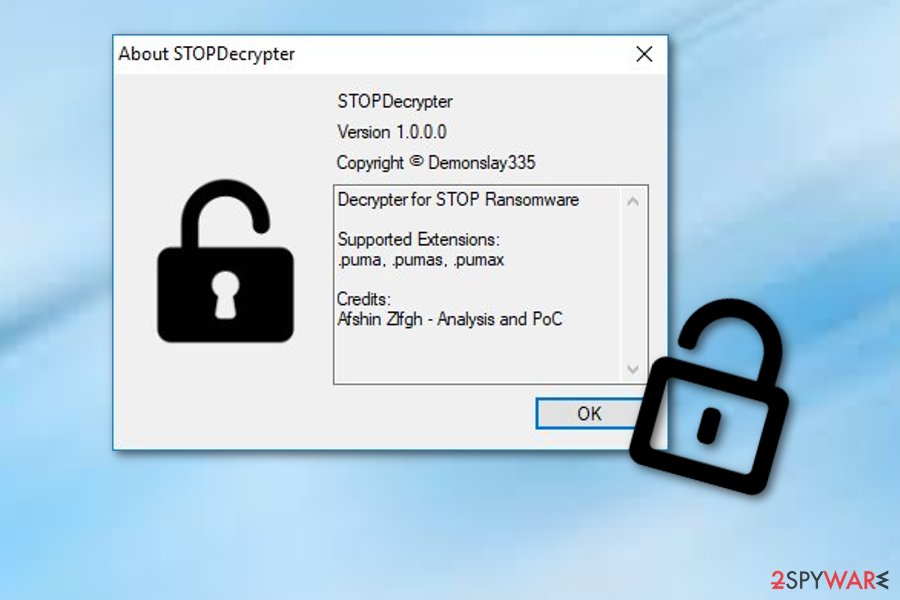
Puma ransomware is a decryptable virus. If you got infected, you can call yourself luckier than other victims because you have a chance to recover your encrypted files. However, only data having the .puma, .pumas, and .pumax appendixes can be unclocked by using a special decrypter (direct link provided) from virus experts. However, make sure you try this decrypter only after you remove malware from the system at first. Otherwise, the encryption procedure can be launched once again.
When inside the system, the virus drops !readme.txt ransom note to inform its victim about the current situation. Before that, the malware launches the encryption procedure (for that, it uses AES and RSA algorithm) to make all files installed on the system useless. The victim is given 72 hours to contact hackers. However, you should never do that to prevent further problems with your computer.
Shadow ransomware
At the beginning of December 2018, researchers discovered a variant that appends .shadow extension to the infected files. This file extension was firstly used by the BTCWare ransomware virus back in 2017, and now it seems like malware authors adopted it as well.
Shadow ransomware virus is using a ransom note !readme.txt that explains how to proceed with the payment in Bitcoin. Crooks offer to decrypt one file for free to prove that the decryptor is actually working. The contact emails helpshadow@india.com or helpshadow@firemail.cc should help with the communication. Allegedly, the 50% discount on the ransom price is valid within the first 72 hours of the infection.
As usual, we recommend avoiding any contact with threat actors. While this .shadow file virus is not decryptable at the time of the writing, you should wait till a free decryptor is released, just as it happened with Puma ransomware.
Djvu ransomware
The latest major virus version is Djvu ransomware which has been appending several extensions: .djvu, .djvus, .djvuu, .udjvu, .uudjvu, .djvuq, .djvur, and many others. Currently, this version of malware is considered to be the most prevalent ransomware targeting home computer users.
The virus has already affected thousands of users worldwide by using the of the most popular schemes used by ransomware to sneak into the target system – software cracks and websites that host them. Users get infected after they launch an executable of what they believe to be a cracked application but instead get their data encrypted almost instantaneously.
Djvu ransomware is not decryptable, so the only way to recover encrypted data is to remove the virus first and then try third-party tools. Of course, if you have been backing your files before they got encrypted, you should find no worries. Just remove encrypted files from the system and install the good ones.
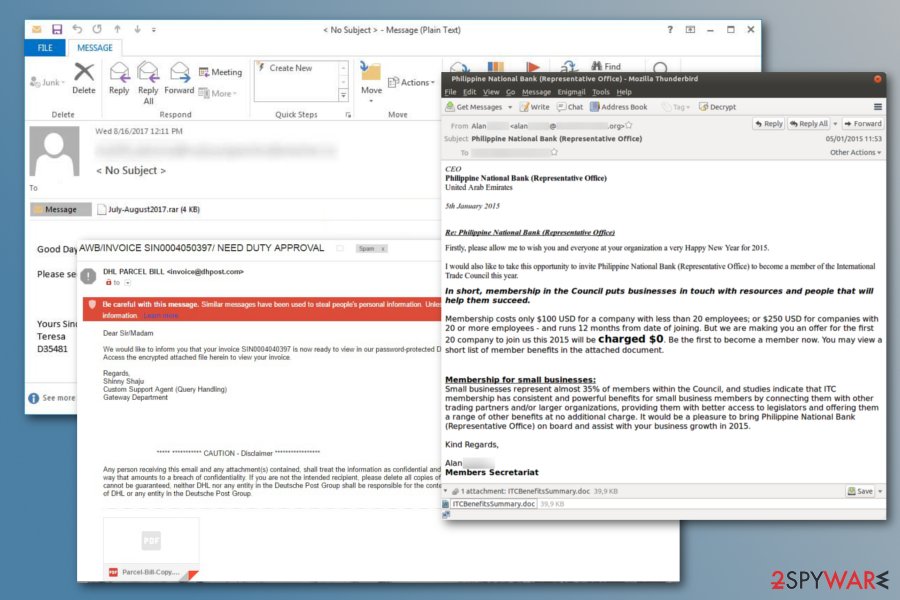
Crypto-virus might get into the system as soon as you open a malicious spam email
The executable of a file-encrypting virus typically spreads via malicious spam emails[4] that include attachments. With the help of social engineering, criminals trick victims into opening obfuscated attachments and letting malware into the system. You can spot a dangerous email from these signs:
- You did not expect to get this email (e.g., you haven't ordered anything from Amazon, and you do not expect a FedEx courier to bring any parcel).
- The letter lacks credentials, such as company logo or signature.
- The email is full of mistakes or weirdly structured sentences.
- The letter does not have a subject line, the body is empty and it includes only an attachment.
- The content of the email urges to check the information in the attachment.
- Sender's email address seems suspicious.
However, specialists from NoVirus.uk[5] tell that malware can also sneak into the system when a user clicks on a malicious ad, downloads a corrupted program or its update, and applying any other techniques.
For this reason, internet users should learn to identify potential risks that might be lurking on the web. We want to remind you that no security software[6] can fully protect you from a ransomware attack. For this reason, watching your clicks and downloads, as well as creating and regularly updating backups, are a must!
Make sure to remove the STOP ransomware virus to restore the machine to a previous state
First of all, we want to discourage you from removing ransomware manually. This cyber threat includes numerous files and components that might look like legitimate system processes. Therefore, you can easily delete wrong entries and cause more damage. For this reason, you have to opt for automatic STOP ransomware removal.
The virus might block access to security software which is needed for the removal, so you should disable the virus first by booting to Safe Mode with Networking. The instructions below will explain to you how it's done. It doesn't matter which version of malware affected your PC, the removal guide remains the same.
When in Safe Mode, download, install and update Malwarebytes or SpyHunter 5Combo Cleaner. Then, run a full system scan with FortectIntego and wait until the program finishes repairing the system and helps you to restore Windows into its working state. Later you can plug in backups to recover your files or try alternative methods presented below.
Getting rid of STOP virus. Follow these steps
Important steps to take before you begin malware removal
File encryption and ransomware infection are two independent processes (although the latter would not be possible without the former). However, it is important to understand that malware performs various changes within a Windows operating system, fundamentally changing the way it works.
IMPORTANT for those without backups! →
If you attempt to use security or recovery software immediately, you might permanently damage your files, and even a working decryptor then would not be able to save them.
Before you proceed with the removal instructions below, you should copy the encrypted files onto a separate medium, such as USB flash drive or SSD, and then disconnect them from your computer. Encrypted data does not hold any malicious code, so it is safe to transfer to other devices.
The instructions below might initially seem overwhelming and complicated, but they are not difficult to understand as long as you follow each step in the appropriate order. This comprehensive free guide will help you to handle the malware removal and data recovery process correctly.
If you have any questions, comments, or are having troubles with following the instructions, please do not hesitate to contact us via the Ask Us section.
IMPORTANT! →
It is vital to eliminate malware infection from the computer fully before starting the data recovery process, otherwise ransomware might re-encrypt retrieved files from backups repeatedly.
Scan your system with anti-malware
If you are a victim of ransomware, you should employ anti-malware software for its removal. Some ransomware can self-destruct after the file encryption process is finished. Even in such cases, malware might leave various data-stealing modules or could operate in conjunction with other malicious programs on your device.
SpyHunter 5Combo Cleaner or Malwarebytes can detect and eliminate all ransomware-related files, additional modules, along with other viruses that could be hiding on your system. The security software is really easy to use and does not require any prior IT knowledge to succeed in the malware removal process.
Repair damaged system components
Once a computer is infected with malware, its system is changed to operate differently. For example, an infection can alter the Windows registry database, damage vital bootup and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by malware, antivirus software is not capable of doing anything about it, leaving it just the way it is. Consequently, users might experience performance, stability, and usability issues, to the point where a full Windows reinstall is required.
Therefore, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it is also capable of removing malware that has already broken into the system thanks to several engines used by the program. Besides, the application is also capable of fixing various Windows-related issues that are not caused by malware infections, for example, Blue Screen errors, freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

By employing FortectIntego, you would not have to worry about future computer issues, as most of them could be fixed quickly by performing a full system scan at any time. Most importantly, you could avoid the tedious process of Windows reinstallation in case things go very wrong due to one reason or another.
Restore Windows "hosts" file to its original state
Some ransomware might modify Windows hosts file in order to prevent users from accessing certain websites online. For example, Djvu ransomware variants add dozens of entries containing URLs of security-related websites, such as 2-spyware.com. Each of the entries means that users will not be able to access the listed web addresses and will receive an error instead.
Here's an example of “hosts” file entries that were injected by ransomware:
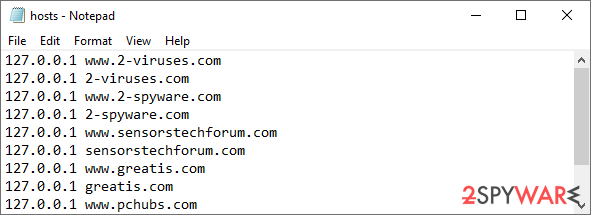
In order to restore your ability to access all websites without restrictions, you should either delete the file (Windows will automatically recreate it) or remove all the malware-created entries. If you have never touched the “hosts” file before, you should simply delete it by marking it and pressing Shift + Del on your keyboard. For that, navigate to the following location:
C:\\Windows\\System32\\drivers\\etc\\
Restore files using data recovery software
Since many users do not prepare proper data backups prior to being attacked by ransomware, they might often lose access to their files permanently. Paying criminals is also very risky, as they might not fulfill the promises and never send back the required decryption tool.
While this might sound terrible, not all is lost – data recovery software might be able to help you in some situations (it highly depends on the encryption algorithm used, whether ransomware managed to complete the programmed tasks, etc.). Since there are thousands of different ransomware strains, it is immediately impossible to tell whether third-party software will work for you.
Therefore, we suggest trying regardless of which ransomware attacked your computer. Before you begin, several pointers are important while dealing with this situation:
- Since the encrypted data on your computer might permanently be damaged by security or data recovery software, you should first make backups of it – use a USB flash drive or another storage.
- Only attempt to recover your files using this method after you perform a scan with anti-malware software.
Install data recovery software
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

Find a working decryptor for your files
File encryption is a process that is similar to applying a password to a particular file or folder. However, from a technical point of view, encryption is fundamentally different due to its complexity. By using encryption, threat actors use a unique set of alphanumeric characters as a password that can not easily be deciphered if the process is performed correctly.
There are several algorithms that can be used to lock data (whether for good or bad reasons); for example, AES uses the symmetric method of encryption, meaning that the key used to lock and unlock files is the same. Unfortunately, it is only accessible to the attackers who hold it on a remote server – they ask for a payment in exchange for it. This simple principle is what allows ransomware authors to prosper in this illegal business.
While many high-profile ransomware strains such as Djvu or Dharma use immaculate encryption methods, there are plenty of failures that can be observed within the code of some novice malware developers. For example, the keys could be stored locally, which would allow users to regain access to their files without paying. In some cases, ransomware does not even encrypt files due to bugs, although victims might believe the opposite due to the ransom note that shows up right after the infection and data encryption is completed.
Therefore, regardless of which crypto-malware affects your files, you should try to find the relevant decryptor if such exists. Security researchers are in a constant battle against cybercriminals. In some cases, they manage to create a working decryption tool that would allow victims to recover files for free.
Once you have identified which ransomware you are affected by, you should check the following links for a decryptor:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

If you can't find a decryptor that works for you, you should try the alternative methods we list below. Additionally, it is worth mentioning that it sometimes takes years for a working decryption tool to be developed, so there are always hopes for the future.
Use Emsisoft decrytor for Djvu/STOP
If your computer got infected with one of the Djvu variants, you should try using Emsisoft decryptor for Djvu/STOP. It is important to mention that this tool will not work for everyone – it only works if data was locked with an offline ID due to malware failing to communicate with its remote servers.
Even if your case meets this condition, somebody from the victims has to pay criminals, retrieve an offline key, and then share it with security researchers at Emsisoft. As a result, you might not be able to restore the encrypted files immediately. Thus, if the decryptor says your data was locked with an offline ID but cannot be recovered currently, you should try later. You also need to upload a set of files – one encrypted and a healthy one to the company's servers before you proceed.
- Download the app from the official Emsisoft website.

- After pressing Download button, a small pop-up at the bottom, titled decrypt_STOPDjvu.exe should show up – click it.

- If User Account Control (UAC) message shows up, press Yes.
- Agree to License Terms by pressing Yes.

- After Disclaimer shows up, press OK.
- The tool should automatically populate the affected folders, although you can also do it by pressing Add folder at the bottom.

- Press Decrypt.

From here, there are three available outcomes:
- “Decrypted!” will be shown under files that were decrypted successfully – they are now usable again.
- “Error: Unable to decrypt file with ID:” means that the keys for this version of the virus have not yet been retrieved, so you should try later.
- “This ID appears to be an online ID, decryption is impossible” – you are unable to decrypt files with this tool.
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from STOP and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Lindsey O'Donnell. New Variant of KeyPass Ransomware Discovered. Threat Post. Independent cybersecurity news site.
- ^ Tim Fisher. What Is Malware?. Lifewire. Tech how-to guides and tutorials.
- ^ Registry. Computer hope. Free computer help since 1998.
- ^ Email spam. Wikipedia. The free encyclopedia.
- ^ NoVirus. NoVirus. British cyber security news.
- ^ Vangie Beal. Security Software. Webopedia. Tech terms.