Egregor ransomware (virus) - Decryption Methods Included
Egregor virus Removal Guide
What is Egregor ransomware?
Egregor ransomware is a particular file-encryption virus that gives victims 3 days to pay up
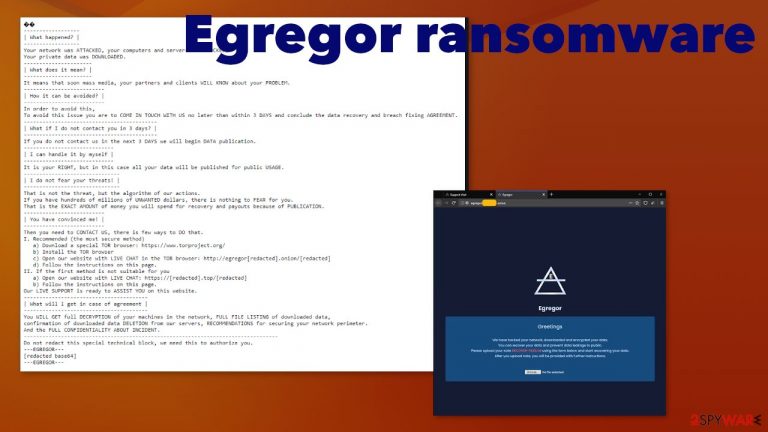
The ransomware virus is pretty much identical to the version of cryptovirus that was released back in April. Based on that, there is no reason to believe the possibility of getting those files back or receiving the decryption tool after payment even. Cybercriminals focus on extortionist behavior, and your belongings are not in their heads. You need to remove the malware as soon as the ransom demanding message is delivered to you so that the system can be salvaged still, and the damage is not going to permanently corrupt the computer. The threat claims to publish stolen data, so the victim thinks about paying the ransom. Threats can easily exfiltrate various files from the system before encrypting and storing needed information in remote servers. This is a feature that ransomware[2] creators started to adapt more recently.
| Name | Egregor ransomware |
|---|---|
| File marker | This threat relies on random appendix formation. .egregor is the possible appendix, but not the only one used |
| Ransom note | RECOVER-FILES.txt |
| Issues | This is the threat from money-driven criminals, so the hacker group behind this virus can create problems. You might bet more dangerous malware via email or messaging apps or even pay and still don't get files repaired |
| Family | File-locker virus family. This virus is the version of Sekhmet ransomware |
| Distribution | The infection can be easily spread with the use of malicious files and malware distributing sites, other threats that plant payload of the ransomware on the system directly |
| Elimination | The ransomware removal is the process that should be performed quickly. It also requires anti-malware tools, so the virus can be terminated properly |
| Recovery | There are some issues that ransomware creates. It manages to directly damage files in system folders, change settings, and trigger alterations to keep the persistence. Get a proper tool capable of repairing such issues. FortectIntego can be the one for this job |
There are many issues regarding such infection. The encryption and the money-demanding message is not the only problem that cryptovirus distributors and makers create. Egregor ransomware is a threat that can interfere with the system by affecting particular functions and files in folders like:
- %Windows%
- %SystemDrive%
- %Local%
- %ProgramData%
- %Temp%.
These issues affect the persistence of the ransomware virus, significantly interfering with termination and cleaning processes. Viruses may start from conducting files and data possibly valuable in the future, so the claims about publications and exposure could work as an encouragement to pay the ransom.
It is a common technique, so experts[3] recommend removing the threat once the message as a text file appears in folders and on the desktop. It is not easy, especially when the threat can be running on the background for a while until you note encryption or other Egregor file-locker virus symptoms.
Egregor ransomware creators can spread worldwide and successfully affect various machines that run on Windows OS, so funds get collected from victims. Creators determine possible actions by listing and contacting them and paying the required amount as the only solution for the infection.
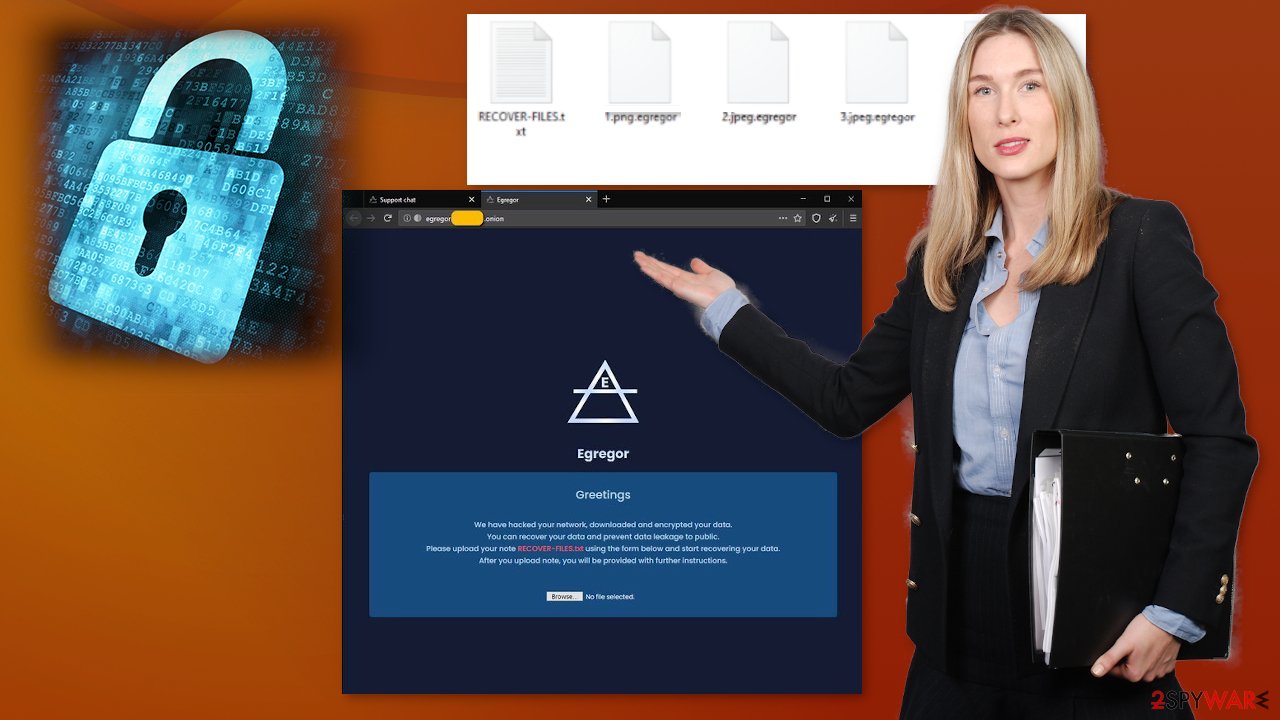
The particular Tor link listed in the ransom note leads to a living chat and a site that shows another message with instructions encouraging to pay the ransom. The message states that you should upload the ransom note file, so the particular identification from the file is received, and your files can be separated from other victims. However, this is not the option to solve the infection issue.
The ransomware payment site contents:
Egregor
Greetings
We have hacked your network, downloaded and encrypted your data.
You can recover your data and prevent data leakage to public.
Please upload your note RECOVER-FILES.txt using the form below and start recovering your data.
After you upload note, you will be provided with further instructions.
Egregor ransomware removal should be performed instead of any of these steps because there are no guarantees that your files really can get decrypted and recovered after the infection distributors receive the payment. The best way to fight ransomware is to clear the machine.
When you rely on an anti-malware program and try to remove the threat automatically, you can receive the report about all the possible intruders, malicious programs, or applications, and properly clear the machine from any supposed infections. SpyHunter 5Combo Cleaner or Malwarebytes tools should work for this procedure and help you significantly. Also, remember to run FortectIntego, so system functions get repaired.
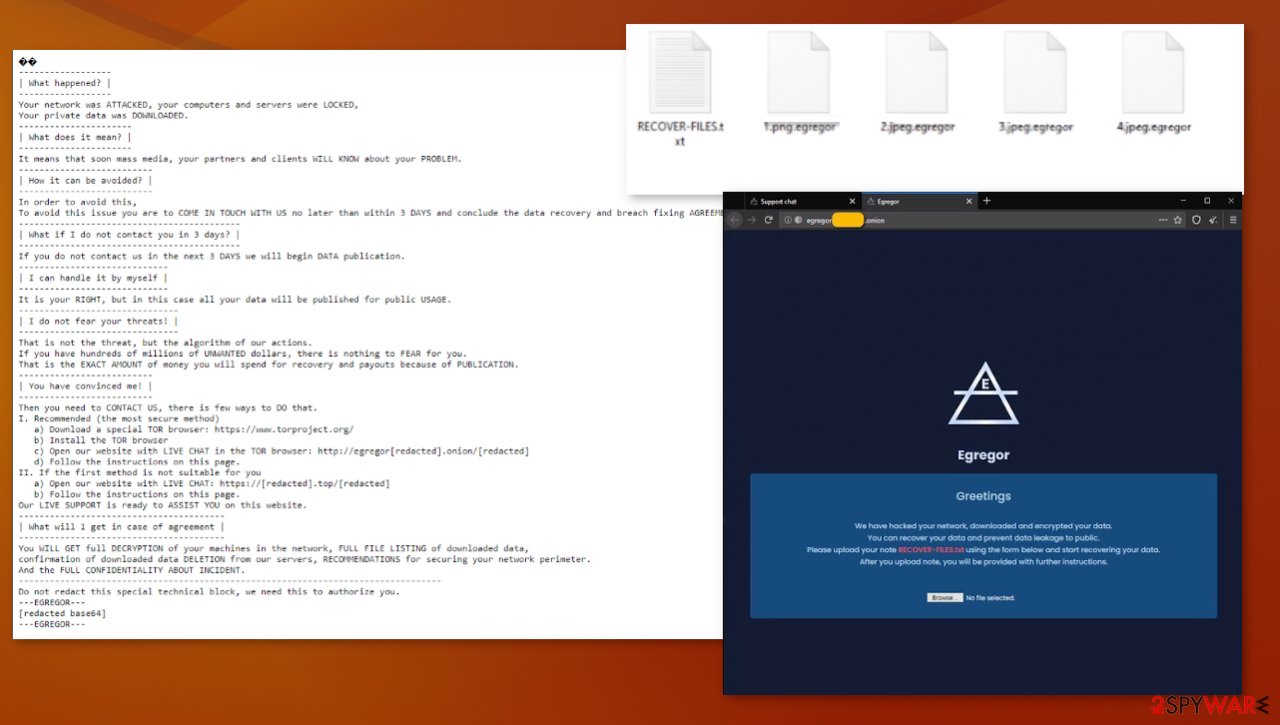
Malare can be distributed with the help of malicious files or direct links
Links to websites that directly distribute malware payloads and can lead to other issues. In most cases, infection is triggered by the payload executable or a different type of file that users allow unknowingly. Such files can be included in software cracks, pirated application packages, licensed versions of programs, and so on.
These malicious files come from torrent services or even direct malicious copies of legitimate sites that resemble trusted platforms. However, more criminals often rely on email campaigns that use Microsoft documents to form a malicious payload distributor. These notifications also can have links to sites with malicious purposes. You need to avoid shady sites online and keep the machine safe from malware this way.
Remove the Egregor file virus and stop additional processes
Try to remove Egregor ransomware immediately after getting the ransom-demanding message. This is how you can clean the machine and prepare the system for data recovery and other procedures needed for the proper system repair. File decryption is not possible since researchers haven't released the official tool yet.
The notorious ransomware removal gives the best results when SpyHunter 5Combo Cleaner or Malwarebytes gets used to fully scan the machine. Once you launch the security tool, you can rely on, that the program finds and eliminates all threats, possibly malicious apps, and ransomware payload. When you recover files on the infected machine, you risk getting them permanently damaged, eliminating the virus before any file restoring.
After the Egregor ransomware virus infection, the file recovery tries to focus on cleaning the device, repairing functions with programs like FortectIntego, and then trying to find reputable backups of your data. This is the best option since decryption is not possible yet. You can find alternative variants below the article.
Getting rid of Egregor virus. Follow these steps
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Egregor using System Restore
System Restore can be used to eliminate the threat because it allows the computer to get recovered to a previous state when the threat was not active
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Egregor. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Egregor from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Egregor, you can use several methods to restore them:
Data Recovery Pro – option for the file recovery procedure
You can rely on Data Recovery Pro and restore some of the files encrypted by the ransomware virus or affected by your own actions and other malware
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Egregor ransomware;
- Restore them.
Windows Previous Versions can be the future used for the data recovery
The System Restore future enabling allows Windows Previous Versions function to activate as a file restoring option
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer – feature recovering files
You can rely on ShadowExplorer when Shadow Volume Copies are not damaged by the ransomware virus
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Decrtyption options are limited for this ransomware. The particular tool has not been released yet
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Egregor and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Encryption. Wikipedia. The free encyclopedia.
- ^ Catalin Cimpanu. Here's a list of all the ransomware gangs who will steal and leak your data if you don't pay. ZDNet. Technology news.
- ^ Virusai. Virusai. Spyware related news.







