ElvisPresley ransomware (Virus Removal Guide) - Bonus: Decryption Steps
ElvisPresley virus Removal Guide
What is ElvisPresley ransomware?
ElvisPresley ransomware – a data locking virus that stems from a well-known malware family
ElvisPresley ransomware is a file locking virus that first started attacking users around the world in early June of 2020 and was first spotted by security researcher Jack. The malware belongs to a relatively old family, Jigsaw, and uses the celebrity name of Elvis as a theme. Just as many other viruses of this kind, it's primary goal is to extort money from victims by locking all personal files on the device with the help of a sophisticated encryption algorithm.
Once inside the system, the ransomware looks for a particular file type (pictures, documents, PDF, videos, etc.) and appends them with .ElvisPresley extension, restricting user access, and removing the original icons. To make sure that users are aware of the infection, cybercriminals deliver an untitled pop-up window, which serves as a ransom note. In it, hackers are asking for $100 into the 1C1pAkwpvuxr4ZxzqHSeTLpFGQMDMJKS3U bitcoin wallet for the decryption tool. For communication purposes, ElvisPresley virus authors ask users to write an email at zemblax@protonmail.com.
| Name | ElvisPresley ransomware |
| Type | File locking virus, cryptomalware |
| Family | Jigsaw |
| Related files | Zembla.exe |
| File extension | Most of the files are appended with .ElvisPresley extension and can no longer be opened. An example of an encrypted file: “document.doc.ElvisPresley” |
| Contact | Crooks ask victims to email them at zemblax@protonmail.com |
| Ransom size | $100 in Bitcoin, which doubles after 24 hours. Some files are deleted every hour if ransom is not paid |
| Bitcoin wallet | 1C1pAkwpvuxr4ZxzqHSeTLpFGQMDMJKS3U |
| Detection |
Some of the malware's malicious executables can be detected under the following names on Virus Total:
|
| File recovery | Data can be recovered with the help of Emsisoft's decryption tool or by using alternative solutions provided in our recovery section below |
| Elimination | Make sure that the infection is terminated promptly with the help of powerful security software such as SpyHunter 5Combo Cleaner or Malwarebytes. If required, access Safe Mode as explained in the instructions below |
| System fix | Ransomware can not only affect personal files by might also negatively impact system-related data. As a result, even after the infection is terminated, it can cause serious damage or reduce computer performance. If you suffer from lag, errors, crashes, or similar issues, fix your Windows with FortectIntego |
Jigsaw is one of the most notorious ransomware families that was first started its distribution in April 2016 and is widely known for its incorporation of the Billy the Puppet from the Saw movies. Since then, malware came back with multiple versions, such as Hydra, Badut Clowns, DeltaSEC, and many others.
ElvisPresley ransomware is yet another variant of the virus that uses a well-established AES encryption algorithm[1] to lock personal files on the system. However, it does not perform the data locking process immediately, as it first needs to prepare the system for that to be successful. Here are some changes that the malware performs:
- Places a malicious executable such as Zembla.exe into %AppData% or %Temp% folder;
- Deletes Shadow Volume Copies to prevent a quick data recovery;
- Modifies Windows registry keys for persistence purposes;
- Creates CryptSvc service with performs the file deletion in intervals;
- Drops hundreds of malicious files on the system, etc.
Once the preparations are complete, ElvisPresley ransomware would begin the encryption procedure, which typically takes only seconds (although victims with exceptionally large HDDs/networks should expect longer encryption times, which can be stopped by shutting down the machine). Victims can later see that typical icons of files became blank and that none of them can be opened. Additionally, each of such files is appended with .ElvisPresley extension.
While ransomware usually leaves system files intact, some Jigsaw variants are known to encrypt Master Boot Record (MBR)[2] data, which complicates ElvisPresley ransomware removal. Nevertheless, accessing Safe Mode with Networking is likely to remove the difficulties with the process. Note: to remediate the Windows machine after a ransomware infection, we recommend using FortectIntego.
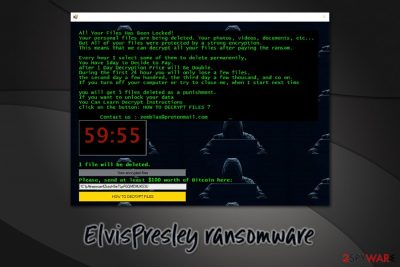
To ensure that users are aware of what happened, they are presented with a pop-up window without a title, which claims the following:
All Your Files Has Been Locked!
Your personal files are being deleted. Your photos, videos, documents, etc…
But all of your files were protected by a strong encryption.
This means that we can decrypt all your files after paying the ransom.Every hour I select some of them to delete permanently,
You have 1day to Decide to Pay.
after 1 Day Decryption Price will be Double.
During the first 24 hour you will only lose a few files,
the second day a few hundred, the third day a few thousand, and so on.
If you turn off your computer or try to close me, when I start next timeyou will get 5 files deleted as a punishment.
If you want to unlock your data
You Can Learn Decrypt Instructions
click on the button: HOW TO DECRYPT FILES ?Contact us : zemblax@protonmail.com
1 file will be deleted.
Please send at least $100 worth of Bitcoin here:
1C1pAkwpvuxr4ZxzqHSeTLpFGQMDMJKS3U
As evident, the ElvisPresley file virus claims that consequences for not paying the ransom are disastrous: the ransom size would double within 24 hours (the pop-up window also includes a timer which is showing the time remaining), and files will be deleted exponentially.
This particular trait is very common in Jigsaw malware versions, as it creates pressure and anxiety among victims, especially since important files could be deleted during the process. However, paying cybercriminals is not recommended, as they might simply scam you and never provide the needed ElvisPresley ransomware decryption tool.
Instead, you should rely on alternative methods for data recovery – Emsisoft even released a decryption tool specifically designed for ElvisPresley ransomware. In case it does not work, you can also use third-party recovery software as per the instructions provided below.
While many ransomware threats would self-delete after encryption is performed, the ElvisPresley virus will remain on the system to be able to delete a predetermined number of files and encrypt all the incoming ones. Therefore, it is important to remove ElvisPresley ransomware from the computer as soon as possible. You should make a copy of the encrypted files if you had no backups available, however.
Watch out for spam email attachments and protect your computer in comprehensive ways to repel ransomware attacks
Jigsaw ransomware and its versions are known to be spread via contaminated spam email attachments. This technique is rather old but very effective, as email spam is used by countless criminal groups to deliver even the most devastating malware to victims, as noted by security researchers from dieviren.de.[3]
Email providers such as Google, Hotmail, and others, implemented various security scanners that could filter email spam. However, these precautionary measures are not perfect, as some legitimate emails end up in Spambox, while malicious emails still manage to break into users' inboxes.
When dealing with fraud and phishing, the most important thing is to stay vigilant and keep in mind that such a threat exists in the first place. In other words, each of the received emails should be treated with suspicions, unless you are absolutely sure who it is coming from. This only applies to emails that include attachments or links, as you will not get infected with malware just by opening an email itself.
Even though hyperlinks can be used to direct users to malicious domains were malware is downloaded from, this attack vector is in decline, and email attachments are much more popular. To check whether the link is legitimate, put your mouse cursor over it and check the real destination on the bottom-left corner of the browser.
When it comes to attachments, you should never allow a macro to be run on the document, such as .doc or .xlsm, as this would trigger a chain of events that would install malware on the system automatically. Remember: if you are not sure if the email is legitimate, delete it and do not interact with any components inside.
You should also ensure that your computer is adequately protected, as ransomware could access your machine in other ways. Thus, install a powerful anti-malware program to protect your from the incoming threats, patch your system, and the installed apps with security updates regularly to avoid software vulnerability[4] exploitation, use strong passwords for all your accounts and never download software cracks/pirated programs on your PC.
Delete ElvisPresley ransomware safely
ElvisPresley ransomware removal might prove difficult due to its advanced traits, such as MBR encryption. Therefore, an attempt should be made to access Safe Mode with Networking, as explained below, and a full system scan should be performed from there. Additionally, malware might also attempt to disable or corrupt the installed security application if it programmed to do so.
If you do not remove ElvisPresley ransomware, it will keep encrypting all the incoming files, and will also delete more and more files as the time goes on. Nonetheless, you should also prepare a backup of encrypted data as a precautionary measure.
Once you are sure that the ElvisPresley virus is eliminated completely, you can begin the data recovery process. You will find all the detailed instructions below. The good news is that decryption tools provided by security researchers almost always recover victims' files without any issues.
Getting rid of ElvisPresley virus. Follow these steps
Manual removal using Safe Mode
In case ElvisPresley ransomware is interfering with your security software, you should go to Safe Mode with Networking and initiate the scan from there:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove ElvisPresley using System Restore
Safe Mode can also be used for malware elimination process:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of ElvisPresley. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove ElvisPresley from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by ElvisPresley, you can use several methods to restore them:
Save your files with Data Recovery Pro
Data recovery software can be effective in some cases when trying to restore files encrypted by ransomware. However, the chances of restoring files successfully diminish over time.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by ElvisPresley ransomware;
- Restore them.
Make use of Previous Versions Feature
Microsoft included an automated recovery feature called Previous Versions. It might sometimes help victims of ransomware to recover files one-by-one.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer might be able to save all your files
In case ElvisPresley ransomware failed to eliminate Shadow Volume Copies, you have a high chance of recovering your data successfully with tools like ShadowExplorer.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Try Emsisoft's decryptor
Download and install Emsisoft's decryptor to recover all your files safely.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from ElvisPresley and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Advanced Encryption Standard. Wikipedia. The free encyclopedia.
- ^ MBR. Computer Hope. Computer help since 1998.
- ^ Dieviren. Dieviren. Cybersecurity advice and malware insights.
- ^ Thomas Holt. What Are Software Vulnerabilities, and Why Are There So Many of Them?. Scientific American. Science News, Articles, and Information.





















