EMPg296LCK ransomware (virus) - Free Guide
EMPg296LCK virus Removal Guide
What is EMPg296LCK ransomware?
EMPg296LCK ransomware is a dangerous malware that attempts to extort money from users
EMPg296LCK is a ransomware-type program, which means that it encrypts all files located on the target machine. The main goal of the attackers is to hold the files hostage so that victims would pay them money to retrieve the important data. Affected files range from pictures to databases – everything that can be useful to users.
This malware was first spotted in early June 2022, and it was immediately determined that it stems from MedusaLocker – a family that has been around for at least three years at the time of the writing. It is rather expansive and we have already covered several of its variants, including Marlock and Ako.
This version doesn't differ much from its predecessors – it encrypts files with AES + RSA encryption[1] algorithms and appends .EMPg296LCK extension to each of them. This results in users not being able to open or modify their files – they require a unique key accessible only to the attackers.
According to the ransom note !_HOW_RECOVERY_FILES_!.HTML, users are meant to send an email to assist1122@protonmail.com or assist112233@cock.li to communicate the price.
| Name | EMPg296LCK virus |
|---|---|
| Type | Ransomware, file-locking malware |
| File extension | .EMPg296LCK, appended |
| Malware family | MedusaLocker ransomware |
| Ransom note | !_HOW_RECOVERY_FILES_!.HTML |
| Contact | assist1122@protonmail.com or assist112233@cock.li |
| File Recovery | The only secure way to restore files is by using data backups. If such is not available or were encrypted as well, options for recovery are very limited – we provide all possible solutions below |
| Malware removal | Disconnect the computer from the network and internet and then perform a full system scan with SpyHunter 5Combo Cleaner or Malwarebytes security software |
| System fix | Once installed on the system, malware might seriously damage some system files, resulting in crashes, errors, and other stability issues. You can employ FortectIntego PC repair to fix any of such damage automatically by replacing system corruption |
The ransom note analysis
The main goal of ransomware is not to harm the system but rather to affect user files in a way that they wouldn't be recoverable. With the help of this process, hackers can then demand money from victims – ransomware became a very profitable business,[2] with thousands of strains luring on the web.
Ransom note serves a vital role when it comes to monetization, as users wouldn't know who or how to contact. The note provides initial explanations of what happened to user files and how to retrieve them and, most importantly for cybercriminals – provides contact details:
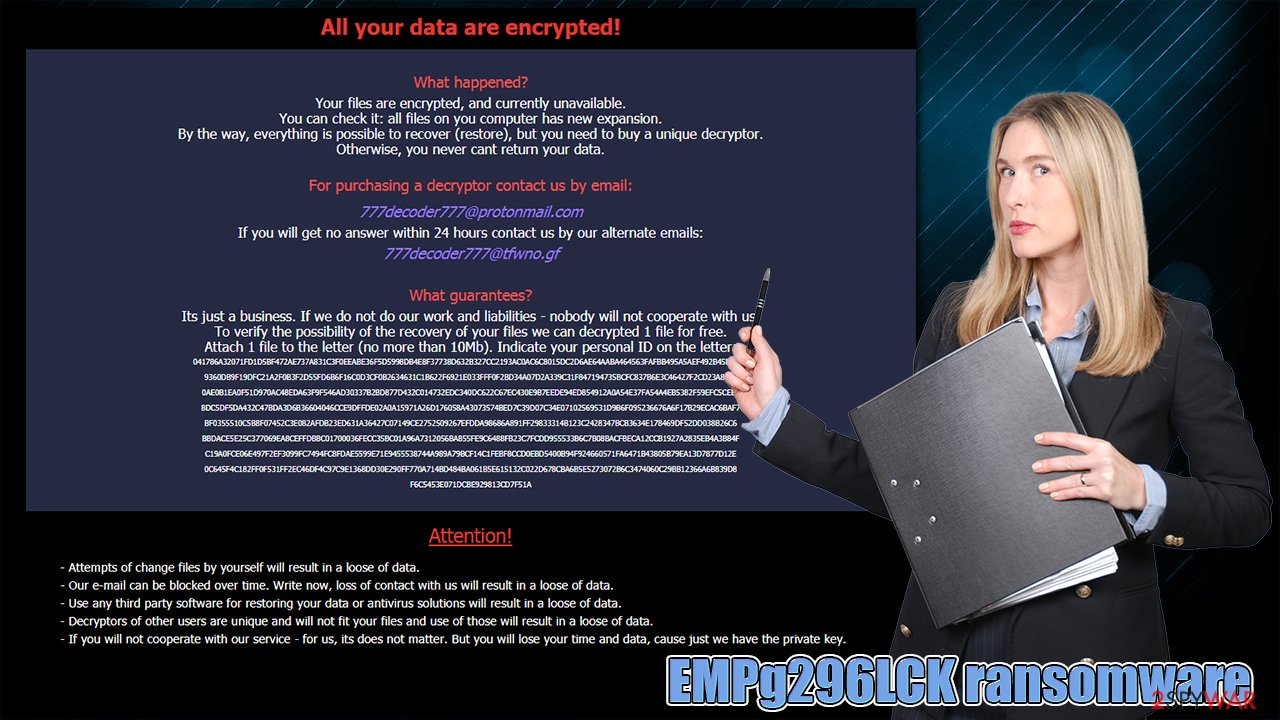
Your files are encrypted!
What happened?
Your files are encrypted, and currently unavailable.
You can check it: all files on you computer has new expansion.
By the way, everything is possible to recover (restore), but you need to buy a unique decryptor.
Otherwise, you never cant return your data.For purchasing a decryptor contact us by email:
assist1122@protonmail.com
If you will get no answer within 24 hours contact us by our alternate emails:
assist112233@cock.liWhat guarantees?
Its just a business. If we do not do our work and liabilities – nobody will not cooperate with us.
To verify the possibility of the recovery of your files we can decrypted 1 file for free.
Attach 1 file to the letter (no more than 10Mb). Indicate your personal ID on the letter:Attention!
• Attempts of change files by yourself will result in a loose of data.
• Our e-mail can be blocked over time. Write now, loss of contact with us will result in a loose of data.
• Use any third party software for restoring your data or antivirus solutions will result in a loose of data.
• Decryptors of other users are unique and will not fit your files and use of those will result in a loose of data.
• If you will not cooperate with our service – for us, its does not matter. But you will lose your time and data, cause just we have the private key. •Otherwise, they will fall into the open access of the Internet! Use any third party software for restoring your data or antivirus solutions will result in a loose of data.
• Please be sure that we will find common languge. We will restore all the data and give you recommedations how to configure the protection of your server.
•Check the spam folder in the mail !!!
We do not recommend negotiating or even contacting malware authors. There is no guarantee that they would provide a decryption tool, even if you pay the requested money. Besides, paying the ransom only signifies that the illegal business scheme works well – it will only encourage crooks to develop ransomware further and infect more people.
Remove the virus
In order to prevent the attackers from communicating with EMPg296LCK ransomware via the network, you should disconnect the computer(s) from it. Malware authors could send additional payloads or update ransomware with new code through it. While you can simply plug out the internet cable, it might not always be convenient, so you should proceed with the following steps instead:
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet
![Network and internet Network and internet]()
- Click Network and Sharing Center
![Network and internet 2 Network and internet 2]()
- On the left, pick Change adapter settings
![Network and internet 3 Network and internet 3]()
- Right-click on your connection (for example, Ethernet), and select Disable
![Network and internet 4 Network and internet 4]()
- Confirm with Yes.
The only secure way to remove an infection as serious as ransomware from the system is by scanning it with SpyHunter 5Combo Cleaner, Malwarebytes, or another powerful anti-malware. While some malware of this type removes themselves after data encryption, it is unlikely to be the case with Spark ransomware due to their threats of corrupting data.
Since crooks threatened to corrupt data, we recommend performing a scan in Safe Mode, which you can access by following these steps:
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
![Windows XP/7 Windows XP/7]()
Windows 10 / Windows 8
- Right-click on the Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find the Advanced Startup section.
- Click Restart now.
- Select Troubleshoot.
![Choose an option Choose an option]()
- Go to Advanced options.
![Advanced options Advanced options]()
- Select Startup Settings.
![Startup settings Startup settings]()
- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.
Fix the operating system
After the malware is deleted from your system, it is time to take care of its health. Once installed, it can seriously tamper with various files and corrupt them in the process – this damage can't be removed by anti-malware software. As a result, those affected start experiencing crashes, BSODs,[3] errors, and other stability issues, which can significantly diminish the usability of the device.
Thus, we recommend using specialized software capable of fixing these issues easily, without you having to reinstall your operating system after a malware attack.
- Download FortectIntego
- Click on the ReimageRepair.exe
![Reimage download Reimage download]()
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
![Reimage installation Reimage installation]()
- The analysis of your machine will begin immediately
![Reimage scan Reimage scan]()
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
![Reimage results Reimage results]()
Data recovery
As soon as ransomware breaks into the device, it encrypts all the eligible files, excluding the system and some other file types. This is done to cause maximum damage to the user so that they would be more inclined to pay. File encryption uses a unique, alphanumeric string of characters as a decryption key – it's like a password that's unique for every victim.
This is why ransomware infection can be so devastating – even if EMPg296LCK ransomware removal is performed, the files would remain unusable. Paying criminals is risky, as they might never fulfill their promises, making users risk their money along with files.
Thus, we recommend you take an alternative route. Before you proceed with alternative solutions for data recovery, make sure you make backups of the encrypted data, as, otherwise, it might be permanently damaged in the process.
Getting rid of EMPg296LCK virus. Follow these steps
Restore files using data recovery software
Since many users do not prepare proper data backups prior to being attacked by ransomware, they might often lose access to their files permanently. Paying criminals is also very risky, as they might not fulfill the promises and never send back the required decryption tool.
While this might sound terrible, not all is lost – data recovery software might be able to help you in some situations (it highly depends on the encryption algorithm used, whether ransomware managed to complete the programmed tasks, etc.). Since there are thousands of different ransomware strains, it is immediately impossible to tell whether third-party software will work for you.
Therefore, we suggest trying regardless of which ransomware attacked your computer. Before you begin, several pointers are important while dealing with this situation:
- Since the encrypted data on your computer might permanently be damaged by security or data recovery software, you should first make backups of it – use a USB flash drive or another storage.
- Only attempt to recover your files using this method after you perform a scan with anti-malware software.
Install data recovery software
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

Find a working decryptor for your files
File encryption is a process that is similar to applying a password to a particular file or folder. However, from a technical point of view, encryption is fundamentally different due to its complexity. By using encryption, threat actors use a unique set of alphanumeric characters as a password that can not easily be deciphered if the process is performed correctly.
There are several algorithms that can be used to lock data (whether for good or bad reasons); for example, AES uses the symmetric method of encryption, meaning that the key used to lock and unlock files is the same. Unfortunately, it is only accessible to the attackers who hold it on a remote server – they ask for a payment in exchange for it. This simple principle is what allows ransomware authors to prosper in this illegal business.
While many high-profile ransomware strains such as Djvu or Dharma use immaculate encryption methods, there are plenty of failures that can be observed within the code of some novice malware developers. For example, the keys could be stored locally, which would allow users to regain access to their files without paying. In some cases, ransomware does not even encrypt files due to bugs, although victims might believe the opposite due to the ransom note that shows up right after the infection and data encryption is completed.
Therefore, regardless of which crypto-malware affects your files, you should try to find the relevant decryptor if such exists. Security researchers are in a constant battle against cybercriminals. In some cases, they manage to create a working decryption tool that would allow victims to recover files for free.
Once you have identified which ransomware you are affected by, you should check the following links for a decryptor:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

If you can't find a decryptor that works for you, you should try the alternative methods we list below. Additionally, it is worth mentioning that it sometimes takes years for a working decryption tool to be developed, so there are always hopes for the future.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from EMPg296LCK and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Ron Franklin. AES vs. RSA Encryption: What Are the Differences?. Precisely. Data protection company.
- ^ Ransomware: The most profitable malware in history. Valeo Networks. IT services, cybersecurity, compliance, and cloud solutions.
- ^ Chris Hoffman. Everything You Need To Know About the Blue Screen of Death. How-to Geek. Site that explains technology.


















