Faust ransomware (Free Guide)
Faust virus Removal Guide
What is Faust ransomware?
Faust ransomware – a type of malware that can cause maximum damage
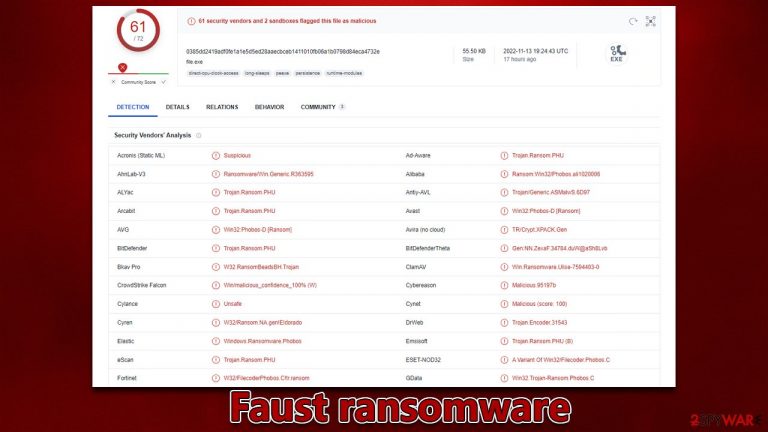
Faust is a type of virus that is designed for file locking. Every non-system file located on a PC or a network is encrypted[1] and is held hostage – the cybercriminals demand payment to be transferred in bitcoin in return for a decryption tool. This type of operational scheme makes it a perfect tool for crooks to extort money from home users and companies alike.
One can quickly notice that their system is infected with Faust ransomware by looking at pictures, videos, databases, and other files, as each of them, would have a “.faust” extension, along with cybercriminals' email address and a unique ID assigned to each of the users individually.
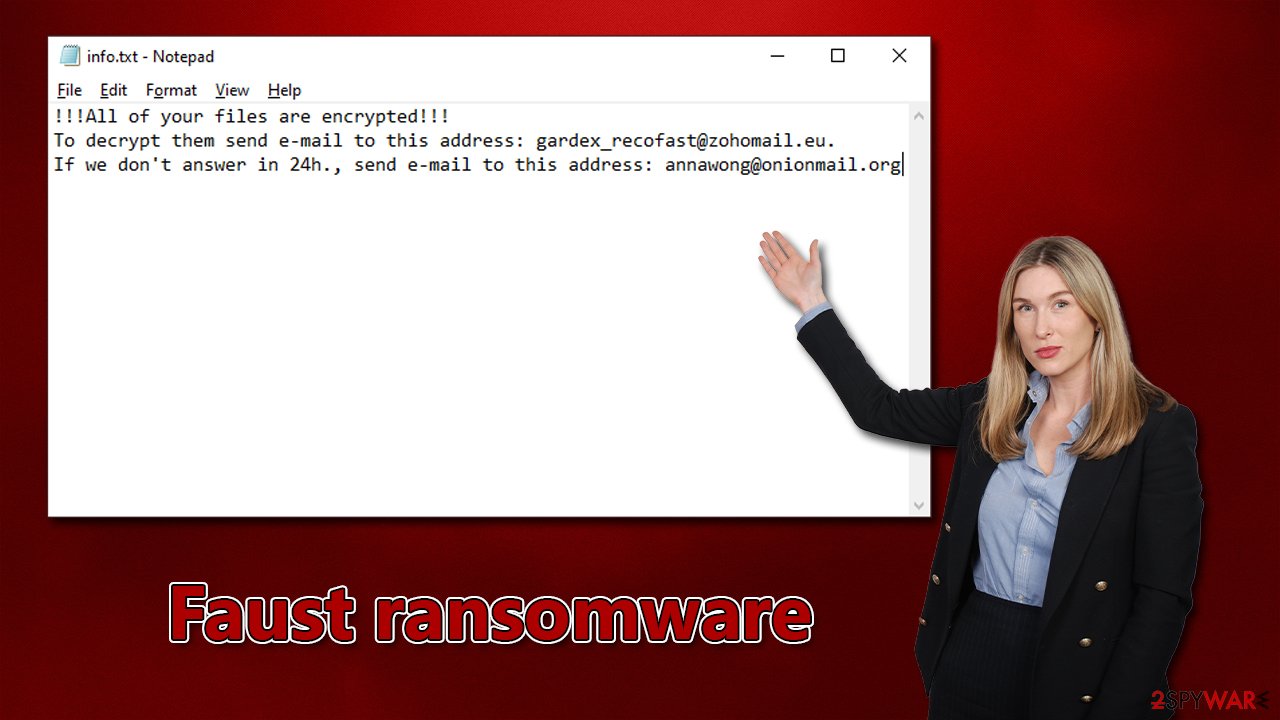
Soon after the data encryption event, malware delivers two ransom notes – info.txt and info.hta. Both of these files are used by criminals to explain to victims what has happened to their files and that they need to email them to gardex_recofast@zohomail.eu or annawong@onionmail.org.
The ultimate goal here is making users transfer bitcoin to crooks' crypto-wallets, and they would allegedly restore encrypted files. We do not recommend talking or negotiating with hackers, as they would always try to convince you that paying them is the best option. Instead, follow the guide below to remediate your system.
| Name | Faust virus |
|---|---|
| Type | Ransomware, data locking malware, cryptovirus |
| File extension | [user_ID].[email].faust |
| Ransom note | info.txt and info.hta |
| Contact | gardex_recofast@zohomail.eu and annawong@onionmail.org |
| File Recovery | If no backups are available, recovering data is almost impossible. Nonetheless, we suggest you try the alternative methods that could help you in some cases – we list them below |
| removal | Make sure to run a system scan with SpyHunter 5Combo Cleaner or another reliable anti-malware program before proceeding with data recovery methods |
| System fix | Windows computers may still be damaged by malware even after it has been removed, causing issues like crashes, lags, and other stability concerns. To fix the operating system, we advise running FortectIntego on it |
How ransomware spreads
Ransomware can be spread in several ways. The most common method is spam email attachments, where a malicious document will execute code once it is opened. Another way ransomware can be spread is through links within spam emails, so you should avoid clicking on anything that seems suspicious.
It is also very common to find ransomware on websites specialized in distributing software cracks and pirated applications, which are usually not well-regulated. Some of these pages have been created to infect people's devices with all sorts of malware (they are made to look like original torrent sites).
Sometimes, hackers use more complicated methods to deliver ransomware, like exploiting security vulnerabilities.[2] This is why we recommend always running updated security software and making sure your operating system (OS) and all applications are up-to-date with the latest patches.
Ransom note
The Faust virus is part of the Phobos family – ransomware that has been around for years. Like its other versions, it delivers two ransom messages: a brief message enclosed in a TXT file and an extended message with more details about the situation. The extended message reads as follows:
All your files have been encrypted!
All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail gardex_recofast@zohomail.eu
Write this ID in the title of your message –
In case of no answer in 24 hours write us to this e-mail:annawong@onionmail.org
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the tool that will decrypt all your files.Free decryption as guarantee
Before paying you can send us up to 5 files for free decryption. The total size of files must be less than 4Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)How to obtain Bitcoins
The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click 'Buy bitcoins', and select the seller by payment method and price.
https://localbitcoins.com/buy_bitcoins
Also you can find other places to buy Bitcoins and beginners guide here:
http://www.coindesk.com/information/how-can-i-buy-bitcoins/Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
We highly advise against paying or contacting cybercriminals, as they often lie about their promises and never send the decryptor – even after receiving payment. It would be wiser to make copies of your encrypted files and attempt to restore them using data recovery software or wait for a decryption tool designed specifically for this Phobos variant.
Recover from a ransomware attack
1. Disconnect from the network
After ransomware encrypts your data, it will connect to a remote server (called Command and Control).[3] This is how crooks can send extra commands for malware execution or even include extra payloads. All affected machines must be disconnected from the network and internet to stop this from happening. Furthermore, be sure to disconnect from any cloud storage services like OneDrive.
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet
- Click Network and Sharing Center
- On the left, pick Change adapter settings

- Right-click on your connection (for example, Ethernet), and select Disable

- Confirm with Yes.
2. Remove the virus
Disconnect your computer from the network, then run a full system scan with SpyHunter 5Combo Cleaner, Malwarebytes, or another anti-malware software to get rid of the ransomware. Although it's true that ransomware might delete itself after encrypting your files, this isn't always guaranteed. Ransomware is often distributed with other PC infections (usually data-stealing Trojans), which can lead to even more privacy and security damage. If Faust ransomware interferes with the removal process, access Safe Mode as follows:
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on the Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find the Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.
- Select Startup Settings.
- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.
3. Fix damaged system files
After malware infection, Windows is no longer the same, as some system files might get damaged or even destroyed. This can result in system instability – crashes, failure to launch programs, BSODs,[1] and many other issues. If you are suffering from these problems after eliminating the infection, use data recovery software as explained below.
- Download FortectIntego
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

4. Restore your data
While file encryption and ransomware infection are two different processes, the former always follows the latter. After a virus infiltrates a computer system, it encrypts data files. During this time frame, the virus creates a unique user ID that also affects the decryption key. The decryption key is needed to unlock files, but only cybercriminals have access to this sequence of randomly-generated alphanumeric characters.
It is common to believe that locked data will be back to normal after a security software scan, but this is not the case – the files will remain locked. Although there are ways of recovering your data without paying the criminals, they may not be 100% effective. We explore some methods below.
Before you do anything else, make copies of all the locked files and store them on a separate hard drive or USB. Encrypted files can't contain harmful code, so they're safe to transfer. If you skip this step, you might permanently damage data – and then not even a working recovery tool could decrypt it.
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders which you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
Decryption tools for ransomware strains might be created eventually because of the work security researchers do. In a few instances, law authorities have taken over servers from malicious actors, which allowed the keys to be released – this is often done by reputable security vendors. The following links may help you:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Encryption. Investopedia. Sharper insight, better investing.
- ^ Thomas Holt. What Are Software Vulnerabilities, and Why Are There So Many of Them?. Scientific American. Science Magazine.
- ^ Command and Control [C&C] Server. Trend Micro. Security blog.
