Flow Dark browser hijacker (Free Guide)
Flow Dark browser hijacker Removal Guide
What is Flow Dark browser hijacker?
Flow Dark is a browser hijacker that spreads using misleading distribution techniques
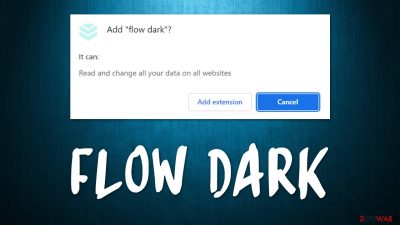
Flow Dark is a potentially unwanted application that you might have installed accidentally together with freeware[1] from third-party websites. You might also come across its deceptive advertisement on a dubious website, where it is said that you need to install the extension in order to proceed to view the page.
Once on the system, the app may or may not change the homepage and new tab functionality by replacing it with the getsins.com address – it usually depends on various configuration settings of a particular machine. This address would then redirect all search queries to websearches.club or Yahoo search provider, which would show alternative results.
The Flow Dark hijack would also result in an increased number of sponsored links and ads that are shown at the top of search results, making users more likely to interact with them. If you have found this app on your system, remove it immediately – we explain how before.
| Name | Flow Dark |
|---|---|
| Type | Browser hijacker, potentially unwanted browser extension |
| Distribution | Software bundles, ads, redirects |
| Symptoms | The infected users commonly notice their browsers changing the default homepage and search provider; search results are generated by redirecting through several URLs; an overall increase in ads, redirects, scams, phishing messages, etc. |
| dangers | Installation of other potentially unwanted programs/malware, personal data disclosure to unknown parties, monetary loss |
| Removal | To remove the unwanted browser extension, you should access your browser's settings section. Do not forget to check your system for other potentially unwanted programs and malware with SpyHunter 5Combo Cleaner |
| Other Tips | Clean your browsers from cookies and other web data with FortectIntego to prevent data tracking. The app can also find and fix corrupted system sections that could otherwise cause crashes and errors |
Is the dark theme worth it?
Some users might install Flow Dark intentionally because it is presented as an app that is capable of providing dark mode to all the pages while browsing the web. In fact, this is just one of many extensions that are rebranded from its previous versions. Not only the functionality but also the names are almost identical – Mini Dark, Moon Darker, and Real Dark are just a few examples we've already covered before.
While it may seem like a great addition to the customization capabilities of your browser, it is relatively useless. Most modern browsers, such as Google Chrome, MS Edge, or Safari, all have customization settings as such built-in. In other words, you could simply access browser settings and pick the dark mode from there.
That being said, the function of the Flow Dark browser extension becomes rather useless. In the meantime, you would have to endure intrusive ads, homepage changes, data tracking by third parties, and other unwanted side effects of having a browser hijacker installed on your device.
Distribution and avoidance
If you did not install the potentially unwanted app intentionally, it must have happened whenever you were downloading freeware from third-party sources (software bundling) or after you were tricked by a misleading advertisement.
Software bundles
Whenever you choose to visit a third-party website that distributes software, there is a chance that you may end up installing adware, a browser hijacker, or even malware on your system (depending on how trustworthy the source is). Software bundling[2] is a profitable practice that has been used for years and is one of the main reasons for users installing PUPs on their systems by accident.
In order to avoid this, you should always prefer more trustworthy websites to download new apps from. Even when using seemingly well-known websites, you should always be aware that the installed may include optional programs, and your job is to decline them promptly before they manage to slip in. To do that, always pick Advanced/Custom settings, read the fine print, watch out for pre-ticked checkboxes, and never rush through the installation steps.
Fake ads
Fake updates or other misleading advertisements are also prominent when it comes to potentially unwanted application distribution. You might end up on one of these phishing pages by accident while browsing the web; upon entry, you might be told that some popular software (such as Flash Player) is out of date and needs to be updated in order to proceed.
In other cases, you might be told that an installation of an extension or an application is required to proceed, which would result in the same outcome – you would end up installing potentially unwanted or even malicious software on your system.
How to correctly get rid of Flow Dark hijacker
As evident, to get rid of the browser hijacker and its effects on your device, you need to find and eliminate the extension from your browser. Usually, this can be done by clicking the “Extensions” button next to the URL bar and selecting “Uninstall.” If that is not possible for some reason, you can follow the steps below:
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.
![Remove extensions from Firefox Remove extensions from Firefox]()
MS Edge
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.
![Remove extensions from Chromium Edge Remove extensions from Chromium Edge]()
MS Edge (legacy)
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.
![Remove extensions from Edge Remove extensions from Edge]()
Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.
![Remove extensions from Safari Remove extensions from Safari]()
Protect your privacy by cleaning browser chaches
Upon installation, a browser hijacker implements tiny files known as cookies, which are then stored locally. If not removed, these files can remain on your device for years, continuing their data tracking activities and sending it to third parties. Therefore, you should make sure that you clear your browser caches to ensure that these files are eliminated.
For that, you can employ manual instructions, although you can do that much quicker with the FortectIntego recovery solution. It can fix system file corruption caused by infections and clean your web browsers or other OS sectors for you.
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
MS Edge (legacy)
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.
![Clear Edge browsing data Clear Edge browsing data]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
Other security tips
First of all, we strongly recommend you employ a powerful anti-virus application and perform a full system scan with it. Third-party solutions such as SpyHunter 5Combo Cleaner or Malwarebytes provide an extra layer of protection so that you always get a warning if a malicious payload is trying to break into your machine.
The biggest mistake one can make is to ignore warnings shown by security software – this happens relatively often when users visit torrents and similar sites to download software cracks/pirated application installers. We recommend refraining from visiting such places in the first place, as they are used by cybercriminals to spread dangerous malware such as ransomware.[3]
How to prevent from getting browser hijacker
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Freeware. Wikipedia. The free encyclopedia.
- ^ Bundled Software. Techopedia. Professional IT insight.
- ^ Ransomware. FBI. Federal Bureau of Investigation.










