GandCrab 3 ransomware (Removal Instructions) - Jul 2018 update
GandCrab 3 virus Removal Guide
What is GandCrab 3 ransomware?
GandCrab v3 – dangerous ransomware virus hailing from the infamous GandCrab family
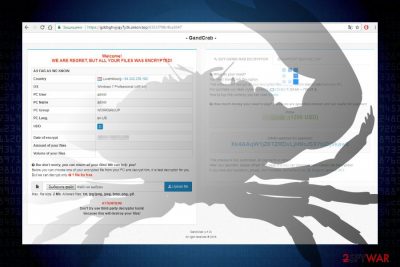
GandCrab 3 is a crypto-virus[1] virus that functions as a third version of the notorious GandCrab ransomware. At the end of April 2018, only a couple of month after the release of GandCrab2, hackers struck again with a new strength targeting Russia, Belarus, Kazakhstan, and Ukraine PC users in particular. GandCrab v3 renders AES-256 (CBC mode) + RSA-2048 encryption to hardcode personal files and subsequently mark them with .CRAB file extension. The file CRAB-DECRYPT.txt stands for a ransom note, which contains an explicit guide on how the victim has to pay the ransom. Bitcoins accepted only.
| Name | GandCrab 3 |
|---|---|
| Versions | GandCrab, GandCrab 2 |
| Classification | Ransomware |
| File extension | .CRAB |
| Ransom note | CRAB-DECRYPT.txt |
| Main symptoms | Personal files inaccessible, ransom note created on the desktop, slow PC, compromised desktop's wallpaper, browser redirects to payment website |
| Main dangers | It compromises the system and can cause severe crash. Personal files may be permanently deleted. Money loss |
| Removing ransomware manually is not possible. To get rid of it, you should render a professional anti-malware like FortectIntego | |
At the very end of April 2018, cybersecurity experts detected a sample of the GandCrab v3 ransomware. Genealogically, its predecessors are GandCrab and GandCrab 2 versions, both of which appeared to be extremely successful from the perspective of the crooks.[2] The initial release managed to collect more than 600,000 USD within less than four months.
While the initial variant can already be decrypted, the v2 does not. GandCrab 3 decryptor is not yet available either.
Currently, it's not yet hundred percent clear what distribution techniques cybercriminals exploit to spread this malware around. However, based on the information collected about this malware, the following methods can be applied:
- Magnitude Exploit Kit;
- Rig Exploit Kit;
- GrandSoft Exploit Kit;
- Seamless malvertising campaign;
- Receipt Feb-21310 [random numbers] attachment of spam email;
- Fake Hoefler text font updates;
- Hacked Remote Desktop Services, etc.
Upon encryption, the GandCrab 3 virus changes boot sequence eliminates Volume Shadow Copies using Command Prompt and PowerShell as admin, and the unravels the AES-256 (CBC mode) + RSA-2048 encryption algorithm. In the background of the system, the malware runs random.exe. It may also hijack the explorer.exe file and force the system to restart to finish up the encryption.
Just like the previous version, it appends .CRAB file extension to the encoded files. It's targets more than 250 file types, including the most popular (.jpg, .png, .doc, .pdf, .avi, .docx, etc.). Once the files are encrypted, the virus generates a ransom note called CRAB-DECRYPT.txt. It says:
—= GANDCRAB V3 =—
Attention!
All your files documents, photos, databases and other important files are encrypted and have the extension: .CRAB
The only method of recovering files is to purchase a private key. It is on our server, and only we can recover your files.
The server with your key is in a closed network TOR. You can get there by the following ways:
0. Download Tor browser – https://www.torproject.org/
1. Install Tor browser
2. Open Tor Browser
3. Open link in TOR browser:
4. Follow the instructions on this page
On our page, you will see instructions on payment and get the opportunity to decrypt 1 file for free.
The alternative way to contact us is to use Jabber messanger. Read how to:
0. Download Psi-Plus Jabber Client: https://psi-im.org/download/
1. Register new account: http://sj.ms/register.php
0) Enter “username”: 21b1a2d1729f0695
1) Enter “password”: your password
2. Add new account in Psi
3. Add and write Jabber ID: ransomware@sj.ms any message
4. Follow instruction bot
ATTENTION!
It is a bot! It's fully automated artificial system without human control!
To contact us use TOR links. We can provide you all required proofs of decryption availibility anytime. We are open to conversations.
You can read instructions how to install and use jabber here http://www.sfu.ca/jabber/Psi_Jabber_PC.pdf
CAUGHTION!
Do not try to modify files or use your own private key. This will result in the loss of your data forever!
Unlike the two previous versions that accepted DASH cryptocurrency, the latest version demands victims to pay the ransom in Bitcoins. Besides, malware researchers found out that the provenance of the GandCrab-3 is Romania.
If you have the slightest suspicion that you're infected with this ransomware, make sure to remove GandCrab 3 from the system ASAP. For that, we recommend using FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes antivirus tools. As long as you keep it installed, you won't be able to recover your files without paying the ransom.
Upon GandCrab v3 removal, you should try to retrieve files locked with .CRAB file extension with the help of third-party data recovery tools or try to enable a previous Windows version. You can find a full guide on how to recover files encrypted by ransomware at the end of this article.
Criminals may use multiple techniques to spread malware
Bedynet.ru[3] team claim that this particular ransomware is not very likely to confine itself to one distribution method. While it did reach the mainstream distribution yet, it's difficult to name the whole list of techniques precisely.
Nevertheless, people should be careful with Receipt Feb-21310 [ random numbered] attachment sent from [random name ]@cdkconstruction.org. As soon as you spot a suspicious email from the unknown sender, we highly recommend you to report it as spam immediately.
Exploit Kits, including Magnitude, RIG, and GrandSoft are also known for being widely used ransomware carriers. To prevent malicious software from exploiting your PC's vulnerabilities, make sure to install all system's updates and patches.
Last, but not least, be careful with a free download on the net. It has been found that many suspicious and illegal websites contain fake software update downloads. One of the examples used to spread the ancestor of this ransomware is fake Hoefler TextFont. The potential victim is being redirected to a hacked website, which displays scrambled text, and displays a pop-up alert urging to download the latest font update to see the content.
GandCrab-3 removal options
There's only one possibility to remove GandCrab v3 ransomware from the system. It's called automatic since it requires the usage of a professional anti-malware program. Manual removal, when you try to get rid of malicious files by yourself, is practically impossible unless you don't mind damaging the system and the encrypted files permanently.
Instead of that, we would strongly recommend you to use a professional security program, for example FortectIntego, for elimination malicious files manually. Upon successful Gandcrab 3 removal, try to recover your files using data recovery methods listed down below.
Note that each of Gandcrab ransomware's versions has been trying to disable anti-virus/anti-malware scanners to prevent their removal from the system. No matter which version you have on your computer, try following the guide below to know what should be done if you want to create a safe environment for virus removal:
Getting rid of GandCrab 3 virus. Follow these steps
Manual removal using Safe Mode
The ransomware can block you from removing the ransomware. In this case, you should restart your PC into Safe Mode with Networking. For this purpose, do the following:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove GandCrab 3 using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of GandCrab 3. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove GandCrab 3 from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.Unfortunately, your files won't be recovered after GandCrab 3 removal. Upon virus elimination, you should employ third-party data recovery tools. Our recommended options are provided here:
If your files are encrypted by GandCrab 3, you can use several methods to restore them:
Employ Data Recovery Pro
The Data Recovery Pro is a reliable software utility capable of recovering data lost due to ransomware attack, accidental deletion or system's crash.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by GandCrab 3 ransomware;
- Restore them.
Enable Previous Windows version
In case you are using SystemRestore function, the system should automatically create System Restore Points. Of course, you can create these points by yourself. To check whether it's possible to recover files using the previous version feature, follow these steps:
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer
ShadowExplorer won't help since the ransomware deletes the Volume Shadow Copies.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
No decryptor available for Gandcrab v3
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from GandCrab 3 and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Why is Ransomware a dangerous form of cyber threat?. CSO from IDG. Security news site.
- ^ Ugnius Kiguolis. GandCrab evolution 2018: Agile ransomware with real-time updates. 2-Spyware. Cybersecurity news, articles, trends, and virus blog.
- ^ Bedynet. Bedynet. Russian virus and spyware news.





















