I Do Know Your Passwords (Simple Removal Guide) - Improved Instructions
I Do Know Your Passwords Removal Guide
What is I Do Know Your Passwords?
I Do Know Your Passwords – an email scam letter that fakes to have recorded a private video of the user and threatens to load it up on the web

I Do Know Your Passwords is a typical sextortion scam that urges for a $1000 worth BTC payment to cancel the release of a compromising video clip. The false message claims that there was malware installed on the user's computer system which provoked the affected browser to act as an RDP and keylogger[1] and the hacker was supposedly able to record a private video of the victim by accessing his camera and computer screen remotely.
I Do Know Your Passwords scam claims to have recorded a double video where you can see what type of adult content the victim was watching and what he was doing while viewing it. Continuously, the crooks try to scare the victim by claiming to have got hold of the contact lists that are saved in the user's Facebook, Messenger, and email accounts.
| Name | I Do Know Your Passwords |
|---|---|
| Type | Email scam/sextortion scam |
| Aim | The hackers who spread this message aim to threaten gullible users that they will release a private video if the victims do not agree to transfer the demanded sum of money |
| Danger | The criminal might add specific attachments to the scam message such as various PDF files or Word documents that might carry dangerous malware inside. Also, by paying the crooks, you risk transferring a big sum of money for nothing |
| Wallet | 13ajfLBScsUNSJ3t65fsCmT1TRkQCUMYA1 is the Bitcoin wallet address provided in the email scam message where the victims are supposed to transfer the money |
| Ransom | Hackers are a LITTLE BIT greedy – they urge for $1000 in BTC to be transferred in a 48-hour duration, otherwise, the recorded private video will be sent to all accessed contacts of the victim accounts |
| Removal | Once you receive this message, you should get rid of it immediately. DO NOT believe in any information it provides you with and DO NOT open any attached files |
| Repair | If you have scanned your computer with reliable antivirus and the program has detected some malicious infections on your computer, the malware might have compromised some system files of yours. Try repairing them by employing a tool such as FortectIntego |
The deliverers of I Do Know Your Passwords email scam threaten to send the recorded private video to each person that is found on the accessed contact lists and humiliate the victim who supposedly has been involved in private activities while watching adult-related video clips on the Internet sphere. This will happen if the affected user does not agree to pay the $1000 ransom within 2 days:
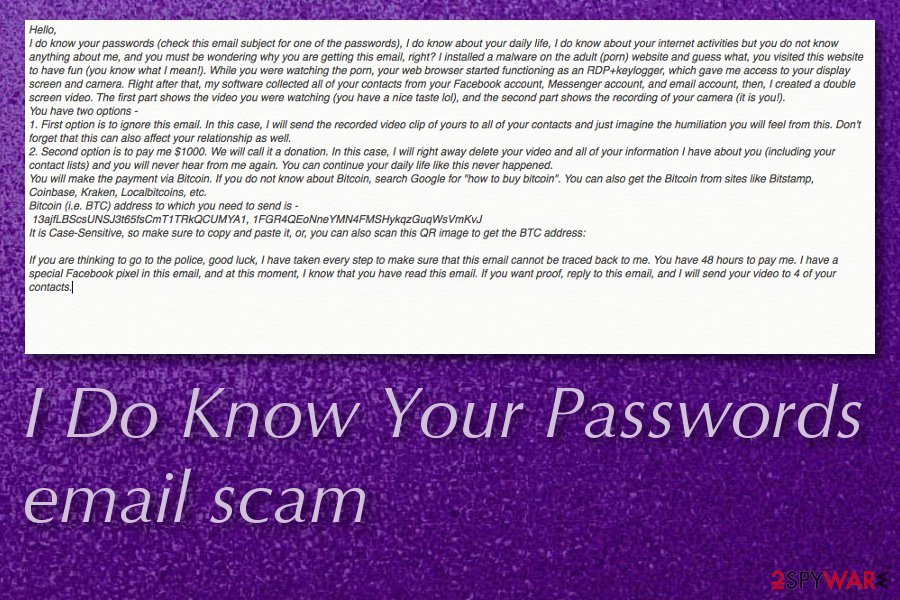
Hello,
I do know your passwords (check this email subject for one of the passwords), I do know about your daily life, I do know about your internet activities but you do not know anything about me, and you must be wondering why you are getting this email, right? I installed a malware on the adult (porn) website and guess what, you visited this website to have fun (you know what I mean!). While you were watching the porn, your web browser started functioning as an RDP+keylogger, which gave me access to your display screen and camera. Right after that, my software collected all of your contacts from your Facebook account, Messenger account, and email account, then, I created a double screen video. The first part shows the video you were watching (you have a nice taste lol), and the second part shows the recording of your camera (it is you!).
You have two options –
1. First option is to ignore this email. In this case, I will send the recorded video clip of yours to all of your contacts and just imagine the humiliation you will feel from this. Don't forget that this can also affect your relationship as well.
2. Second option is to pay me $1000. We will call it a donation. In this case, I will right away delete your video and all of your information I have about you (including your contact lists) and you will never hear from me again. You can continue your daily life like this never happened.
You will make the payment via Bitcoin. If you do not know about Bitcoin, search Google for “how to buy bitcoin”. You can also get the Bitcoin from sites like Bitstamp, Coinbase, Kraken, Localbitcoins, etc.
Bitcoin (i.e. BTC) address to which you need to send is –
13ajfLBScsUNSJ3t65fsCmT1TRkQCUMYA1, 1FGR4QEoNneYMN4FMSHykqzGuqWsVmKvJ
It is Case-Sensitive, so make sure to copy and paste it, or, you can also scan this QR image to get the BTC address:If you are thinking to go to the police, good luck, I have taken every step to make sure that this email cannot be traced back to me. You have 48 hours to pay me. I have a special Facebook pixel in this email, and at this moment, I know that you have read this email. If you want proof, reply to this email, and I will send your video to 4 of your contacts.
According to I Do Know Your Passwords criminals, if the victim tends to cooperate and decides to transfer the demanded sum, the recorded video, and all private information will be eliminated permanently right away and the hacker will leave the user alone. Additionally, the message requires the transfer process to be completed by Bitcoin cryptocurrency.
Usually, bad actors require some type of cryptocurrency[2] payment as this currency guarantees the anonymity of the process and allows the cyber crooks to stay untrackable. However, we recommend declining any demands that you receive from I Do Know Your Passwords message as all the provided information is false and the cybercriminals are trying to make the victims freak out and transfer the money faster.
Continuously, it is known that the scammers try to avoid their messages being sent to the Spam section as frequent as possible. These people manage to place the written information in a PDF document and attach it to the email message itself so that it travels straight to the inbox section. This way the crooks are sure that I Do Know Your Passwords virus reaches the targeted victims.

Keep in mind that you should be careful with these types of attachments as some of them might carry malicious products inside. The hackers might try to benefit in even a more advanced way and hide a Trojan virus or other type of malware in a particular attached file or document and deliver it to the user clipped to the I Do Know Your Passwords email scam message.
In addition, if you start reading I Do Know Your Passwords, the first thing you should notice is that the criminals threaten that the victim's passwords have also been accessed and they seem to provide on of the passwords in the email's subject line. Check if your email address was truly compromised during some data breach activity by visiting haveibeenpwned.com.
We recommend avoiding transferring any money to the 13ajfLBScsUNSJ3t65fsCmT1TRkQCUMYA1 Bitcoin wallet address and opting for the I Do Know Your Passwords removal instead. Also, check if your system is still secured as there is a risk of some type of malware sneaking into your computer system via such email messages. For this purpose, try scanning your machine with a reliable antivirus program. If the tool alerts to have found dangerous malware, you should investigate your system for corrupted files or entries. If you find some, try repairing them with a tool such as FortectIntego.
You need to remove I Do Know Your Passwords from your email box and make sure to change your email account password in case it got leaked or compromised somehow. While creating passwords, ensure that they contain multiple numbers, letters, and some symbols. Additionally, you can also secure your accounts with two-factor or multi-factor authentication.
I Do Know Your Passwords is not the only type of scam seeking to swindle the user's money and threatening that private content will get exposed if the payment demands are refused. Other similar email scam examples include:
- Jeanson J. Ancheta email scam.
- I sent you an email from your account scam.
- I infected you with my private malware (RAT) email scam.
Sextortion scams are one of the most popular email scam variants that have appeared to be successful for some criminals regarding their frequent distribution. Malwarebytes Labs has reported this autumn about a new way of such scamming messages coming from ChaosCC hacker group that also claimed to hold the victims' private videos and demanded Bitcoins in exchange for not releasing them. The scammers used the 1KE1EqyKLPzLWQ3BhRz2g1MHh5nws2TRk BTC address to which already around $2500 worth transfers were performed.[3]
Malware delivery techniques
Regarding the findings of cybersecurity experts from LosVirus.es,[4] various malicious software gets delivered through email spam campaigns. Mostly, hackers add infectious payload as an attachment of a Word, PDL, or Excel document/file to the questionable email messages.
You always have to be aware of such content and not open any clipped payload if you are not sure about its safety. Also, scan the attached data with an antivirus program to make sure that it does not include any malicious content. The same is valid for bogus hyperlinks inserted – you should not enter them.
Continuously, always check the sender and his email address. Make sure that it does not sound suspicious or irrelevant. Also, check the content of the received email message for possible grammar or style mistakes. Official companies will not send you emails filled with mistakes or misunderstandings.
Removal instructions for I Do Know Your Passwords and potential malware
Remove I Do Know Your Passwords immediately if you ever received it in your email box. There is no need for keeping a questionable email message that seeks to swindle your money by providing you with false claims. Also, avoid opening any attached files or documents that might come clipped to the sextortion email scam.
If you have failed to perform the I Do Know Your Passwords removal and opened clipped objects or entered some suspicious hyperlinks that might have come within the message, you should scan your computer system for possible infections with software such as SpyHunter 5Combo Cleaner or Malwarebytes. If these antivirus programs discover any malware, there might be some compromised components on your system. Try repairing them with a tool such as FortectIntego.
Getting rid of I Do Know Your Passwords. Follow these steps
Manual removal using Safe Mode
In case some type of malware managed to sneak into your Windows computer system and performed some malicious activities, you should boot your machine to Safe Mode with Networking:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove I Do Know Your Passwords using System Restore
If you have spotted some questionable or malicious changes on your machine, you can try reversing them by launching the System Restore feature on your affected PC:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of I Do Know Your Passwords. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from I Do Know Your Passwords and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting malware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ What is a Keylogger?. McAfee. Security blog.
- ^ Understanding the Different Types of Cryptocurrency. Bit Degree. Tutorials.
- ^ The lucrative business of Bitcoin sextortion scams (updated). Malwarebytes Blog. Scams.
- ^ LosVirus.es. LosVirus. Security and spyware news source.





















