IndexerClient Mac virus (Free Instructions)
IndexerClient Mac virus Removal Guide
What is IndexerClient Mac virus?
IndexerClient is a malicious Mac application that attempts to steal your banking information and other details
IndexerClient is a Mac virus you may encounter running on your device one day. Unlike many other adware infections that plague macOS users, this one is a bit more serious. It stems from a well-established malware family known as Adload, which has hundreds of versions under its belt since its release by unknown cybercriminals back in 2017.
Variants of this malware strain and not only relatively widespread by also quite evasive. Upon entering the system via fake Flash Player updates or pirated software installers, IndexerClient runs on the system with higher permissions, which allows it to control the device how it pleases. This means that Mac's security systems lay dormant while users have to deal with the infection running on their computers as soon as they are turned on.
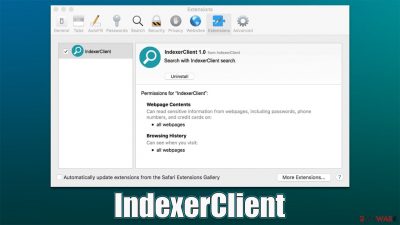
One of the first infection symptoms most people notice is the change to their Safari, Chrome, or another web browser. The installed extension, which uses a unique magnifying glass icon, would change the browser's homepage and alter the search provider, resulting in alternative search results filled with ads and sponsored links (those infected will also experience more redirects to malicious websites and more ads overall while browsing).
This IndexerClient virus component is also used to collect various personal user data, including credit card details or login credentials. Among other issues, users may find other potentially unwanted applications installed on their devices without permission, which can be a serious security threat. We recommend not delaying the removal of this threat.
| Name | IndexerClient |
| Type | Mac virus, adware, browser hijacker |
| Malware family | Adload |
| Distribution | Software bundles of illegal apps, peer-to-peer networks, fake Flash Player updates |
| Symptoms | A new extension is installed on the browser, along with an application of the same name; search and browsing settings altered to an alternative search provider; new profiles and login items set up on the account; intrusive ads and redirects |
| Removal | The easiest way to remove Mac malware is to perform a full system scan with SpyHunter 5Combo Cleaner security software. We also provide a manual guide below |
| Other tips | Potentially unwanted applications often leave traces within web browsers – cookies, for example, are used for tracking. You should get rid of these leftovers with FortectIntego or employ our manual guide |
How Adload malware is spread and how to avoid it
Adload is a relatively established strain, and it achieved this by using effective distribution methods. The first and the most commonly-used one consists of showing fake Flash Player update prompts to users on various websites. People usually encounter them after clicking a malicious link on an already high-risk site or because adware is already running on their systems.
The scheme is very simple – Users are told that they need to update or install Flash Player in order to access some type of multimedia content. Since the plugin has been used for multimedia for so long that it is regarded as something required for this day. The truth is, Flash was discontinued a few years ago by its developer[1] and requests to install it are fake.
The other popular method for Adload distribution is malicious installers from peer-to-peer[2] networks and similar pirated software distributors. We recommend never using these, as they are known to be one of the main reasons why users get infected with malware.

IndexerClient removal
Below you will find everything you need to remove malware from your system effectively. Adload is one of the more persistent threats for Macs, so we would highly recommend you avoid the manual method. Upon infiltration, it employs the built-in AppleScript to grant itself elevated permissions, exempting itself from detection of local Mac defenses such as XProtect[3] and dropping dozens of items on the system.
This may severely complicate the elimination process, so we strongly recommend that regular users employ automatic removal tools such as SpyHunter 5Combo Cleaner or Malwarebytes. With the help of third-party security software, you can avoid malware's evasion mechanisms that affect Mac's security tools and ensure that no infections happen in the future. Nonetheless, you can pick the manual removal method too.
Delete the main application and the extension
Your first task is to find the malicious app and remove it – you should start by stopping its background processes via the Activity Monitor.
- Open Applications folder
- Select Utilities
- Double-click Activity Monitor
- Here, look for suspicious processes and use the Force Quit command to shut them down
- Go back to the Applications folder
- Find the malicious entry and place it in Trash.
![Uninstall from Mac 1 Uninstall from Mac 1]()
Upon infiltration, the virus might establish new User profiles and Login items for persistence. This might be the reason why you can't get rid of the app or the extension.
- Go to Preferences and select Accounts
- Click Login items and delete everything suspicious
- Next, pick System Preferences > Users & Groups
- Find Profiles and remove unwanted profiles from the list.
Finally, you should get rid of the extension that is used by crooks to harvest various personal data. Proceed with the following steps (note: if you can't perform this step, skip it for now):
Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.
![Remove extensions from Safari Remove extensions from Safari]()
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
Remove leftover files or reset your browsers
Leftover files known as PLIST hold various important configuration settings and might hold a virtual role in malware's operation. Remove them as follows:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and delete all the related .plist files.
![Uninstall from Mac 2 Uninstall from Mac 2]()
You should also clean your web browsers to remove various trackers and other caches to ensure proper NetDivision removal. You can employ FortectIntego for this job, or you can follow the manual steps below:
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
If you were unable to remove malware components within your web browser, you could simply reset it as we explain below. Your bookmarks and other preferences will not get lost as long as you remember your account details. Proceed with the following to reset your browser:
Safari
- Click Safari > Preferences…
- Go to the Advanced tab.
- Tick the Show Develop menu in the menu bar.
- From the menu bar, click Develop, and then select Empty Caches.
![Reset Safari Reset Safari]()
Google Chrome
- Click on Menu and select Settings.
- In the Settings, scroll down and click Advanced.
- Scroll down and locate Reset and clean up section.
- Now click Restore settings to their original defaults.
- Confirm with Reset settings.
![Reset Chrome 2 Reset Chrome 2]()
You can find the instructions for MS Edge and Mozilla Firefox below.
Getting rid of IndexerClient Mac virus. Follow these steps
Remove from Microsoft Edge
Delete unwanted extensions from MS Edge:
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.

Clear cookies and other browser data:
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.

Restore new tab and homepage settings:
- Click the menu icon and choose Settings.
- Then find On startup section.
- Click Disable if you found any suspicious domain.
Reset MS Edge if the above steps did not work:
- Press on Ctrl + Shift + Esc to open Task Manager.
- Click on More details arrow at the bottom of the window.
- Select Details tab.
- Now scroll down and locate every entry with Microsoft Edge name in it. Right-click on each of them and select End Task to stop MS Edge from running.

If this solution failed to help you, you need to use an advanced Edge reset method. Note that you need to backup your data before proceeding.
- Find the following folder on your computer: C:\\Users\\%username%\\AppData\\Local\\Packages\\Microsoft.MicrosoftEdge_8wekyb3d8bbwe.
- Press Ctrl + A on your keyboard to select all folders.
- Right-click on them and pick Delete

- Now right-click on the Start button and pick Windows PowerShell (Admin).
- When the new window opens, copy and paste the following command, and then press Enter:
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register “$($_.InstallLocation)\\AppXManifest.xml” -Verbose

Instructions for Chromium-based Edge
Delete extensions from MS Edge (Chromium):
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.

Clear cache and site data:
- Click on Menu and go to Settings.
- Select Privacy, search and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

Reset Chromium-based MS Edge:
- Click on Menu and select Settings.
- On the left side, pick Reset settings.
- Select Restore settings to their default values.
- Confirm with Reset.

Remove from Mozilla Firefox (FF)
Remove dangerous extensions:
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

Reset the homepage:
- Click three horizontal lines at the top right corner to open the menu.
- Choose Options.
- Under Home options, enter your preferred site that will open every time you newly open the Mozilla Firefox.
Clear cookies and site data:
- Click Menu and pick Settings.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

Reset Mozilla Firefox
If clearing the browser as explained above did not help, reset Mozilla Firefox:
- Open Mozilla Firefox browser and click the Menu.
- Go to Help and then choose Troubleshooting Information.

- Under Give Firefox a tune up section, click on Refresh Firefox…
- Once the pop-up shows up, confirm the action by pressing on Refresh Firefox.

How to prevent from getting adware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Tim Brookes. Adobe Flash is Dead: Here’s What That Means. How-to Geeks. Site that explains technology.
- ^ Peer-to-peer. Wikipedia. The free encyclopedia.
- ^ Phil Stokes. How AdLoad macOS Malware Continues to Adapt & Evade. SentinelOne. Autonomous AI Endpoint Security Platform.




















