Koobface (Improved Instructions) - updated Apr 2021
Koobface Removal Guide
What is Koobface?
Koobface is a worm-type infection that can be set to perform various actions like information stealing

Koobface is a relatively old cyber infection that targets Windows, Mac OS X, and Linux platforms.[1] Operating as a worm, this malware is capable of intercepting traffic,[2] inducing ads, stealing sensitive information, downloading secondary payloads, and many other malicious activities.
The virus is also a worm that is capable of spreading via social media and email networks, in particular, Facebook, Twitter, Skype, Gmail Yahoo Mail, and others. As soon as the infection is populated, it checks if there are cookies of social networks[3]. If it locates them, it infects the victim’s profile[4].
If the virus can’t find evidence of social networking websites, it merely erases itself and then loads pop-ups that look like MS Windows error messages. The pop-ups contain the following details: “Error installing Codec. Please contact support.” The threat is flagged by different vendors as Gen:Variant.Koobface.4, Trojan/Win32.Agent, Boface, and many more.
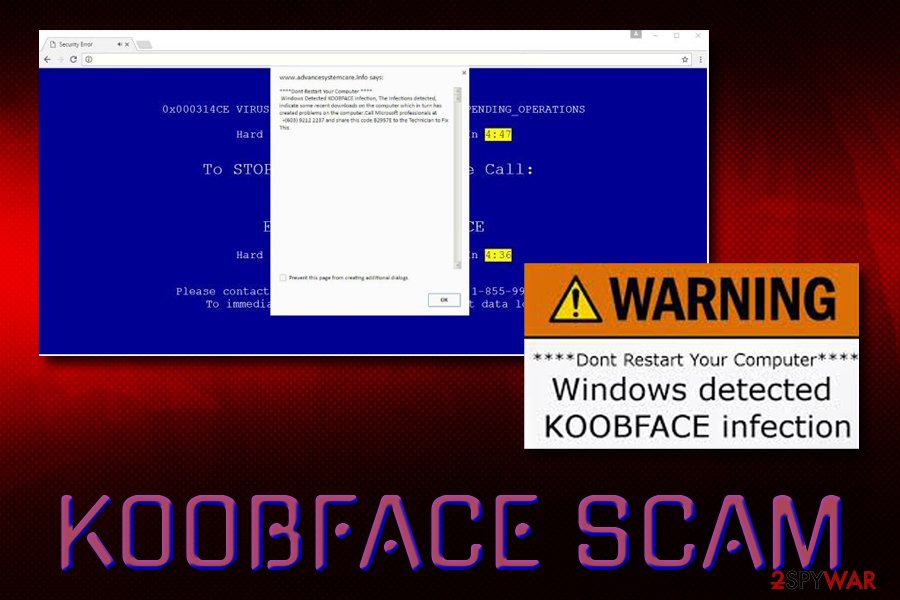
Additionally, the name of this computer worm is often used by technical support scams and other phishing attempts, such as Windows Detected Koobface Infection, Your System is infected with 3 viruses, and others. If you noticed notifications that note the infection of this virus on Google Chrome or another browser, make sure you scan your device with security software as all these claims are most likely fake. Nevertheless, you will have to remove the threat as soon as possible if the infection is real – check the bottom section to find out how.
| Name | Koobface |
| Type | Worm, Trojan |
| Platforms | Windows, Mac OS X, and Linux |
| Infiltration | Networking websites and services, such as Skype, Facebook, Twitter, etc. Pay-per-click ads to generate revenue while directing traffic to spoofed websites |
| Capabilities | Installing additional payloads, stealing confidential data, injecting advertisements into browsers, redirects, blocking access to certain sites, stealing license keys, modifying system files, intercepting internet traffic, etc. |
| Also known as | Associated malicious files include Fbtre6.exe, Mstre6.exe, Freddy35.exe, Websrvx.exe, Captcha6.exe, Bolivar28.exe, Ld05.exe, Ld11.exe, and Ld12.exe. Aliases: Dursg, VBInject, Usuge, VBKrypt, Koobfa, Autorun |
| Termination | Use powerful anti-malware software |
| Recovery | To restore system files to normal, scan your device with FortectIntego |
If a computer user actively uses social media networks, the threat detects particular cookies and collects the victim's login information of all social media websites that he or she visits. Then it sends messages to people on the victim's friend list, asking to view a video.
This message includes a malicious hyperlink. If people click on this hyperlink, they are going to be redirected to a harmful website, which states that an update of Flash is required in order to review the content. The download links include flash_player.exe file. If the person allows installing the update, he/she gives access to an installer of this worm. It means that this .exe file is going to silently download and install infection files.
Koobface hacking worm[5] allows the cyber-criminals to track and record sensitive data about the victim, for example, it can see what passwords do you enter on particular websites, what are your logins and it can even find out credit card info and banking information!
Be aware because it can lead to a financial loss. In addition to that, this malicious worm can display vague ads convincing you to install fake anti-virus programs. Do not install any software promoted by a virus hoax – most likely you will infect your computer even more.

For removal, you should employ reputable security software and terminate all the malicious files from your computer. Additionally, to recover from virus damage, make sure you scan your computer with FortectIntego – it can fix all the infected system files and make the machine operate normally again.
Beware of tech support scammers who claim that your computer has been infected with KoobFace malware. Technical support scammers make victims install a malicious program that displays pop-up messages via the user's default web browser, stating that the system has been compromised.
Such malicious programs can display a lock screen and prevent the user from accessing the PC or pose as a phony Windows Update. All of these deceptive programs are designed to showcase the technical support number that the user supposedly needs to call in order to get help from “certified technicians.”
If your computer is telling you that the system is infected with Koobface, and urges you to contact the tech support team, better scan the system for malware. We also strongly recommend reading this article – Tech Support Scam virus.
A worm usually spread via social media messages
Koobface is usually spread via social engineering. It means that it is spread via social media messages. If your friend has sent you a link that looks suspicious (looks unfamiliar and contains a lot of random symbols), you should double-ask your friend if he/she really sent that. Such spam usually includes such and similar lines:
- “I saw your silly face in that movie, check it!”;
- “Why do you look so stupid? xD See yourself”;
- “You look just awesome in this new movie”;
- “My friend caught you on hidden cam.”
If you can remember clicking any of these messages, make sure that you double-check your computer for malware. Also, you should scan your computer with the powerful anti-spyware if you have been tricked into downloading a fake version of Flash Player, which was disguised as “flash_player.exe”.
Otherwise, Koobface can try to overtake your HTTP traffic, steal your personal information and infect your PC system with additional malware. If you think that you are infected, please, scan your computer with FortectIntego. You can find more about removal below.
The gang behind malware shows off their earnings online
While the majority of cyber criminals tend to stay underground and not brag about the money[6] they earn in illegal ways, criminals behind viruses behave in an entirely different way. According to research, cyber criminals who have created Koobface project have earned thousands of US dollars daily – up to $10,000 a day.
These criminals were so proud of themselves and loved money so much so that they all have set their phones to deliver a message telling how much money has been earned in the previous 24 hours every morning. Bad actors have also been spotted swaggering on social media and posting pictures next to money piles and Porsches.
Do not let scammers take advantage of you and protect your computer in advance to avoid malware attack. Please, do not click on suspicious-looking links while browsing social media websites, and do not open links sent by your friends that point to a video that has nothing to do with you.
Koobface prevention tips:
- Do not browse unreliable websites. If you have opened a website that asks to update your Flash Player, and you know that it was possible to open other videos before, you should know that the site is suspicious. Close it immediately.
- If you have at least the smallest suspicion that your friend did not send the suspicious message with a hyperlink, ask him or her twice.
- Keep an anti-malware program on your computer to prevent infectious computer threats; we recommend FortectIntego.
Manual removal of a computer worm is not recommended
You can check if you have this infection by opening the Task Manager and looking for such processes: freddy79.exe, fbtre6.exe, mstre6.exe, ld08.exe, Ld12.exe. You must remove this malicious threat from your computer and stop the spread of it. You can perform removal manually, and we have provided the instructions on how to do it below this article. This worm has a lot of background processes, manual removal of the Koobface computer worm is not recommended as it may lead to a system crash.
Nonetheless, we strongly advise you to remove Koobface worm automatically by employing a reputable security tool, such as SpyHunter 5Combo Cleaner or Malwarebytes. After termination, perform a scan with FortectIntego to fix virus damage and change your social media/banking passwords to ensure that the cyber-criminals will not use them again.
Getting rid of Koobface. Follow these steps
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Koobface using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Koobface. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Koobface and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting worms
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Koobface. Wikipedia. Free encyclopedia.
- ^ Elie Bursztein. Understanding the prevalence of web traffic interception. Elie.net Tech security blog.
- ^ John P. Mello Jr.. Suspects Behind Facebook Koobface Hack Named. PC World. News, tips, and reviews from the experts on PCs, Windows and more.
- ^ Adam Ostrow. Koobface Virus Gets Smarter; Targets Twitter and Facebook Users [Alert]. Mashable. IT news and comments.
- ^ Danny Palmer. After a decade of silence, this computer worm is back and researchers don't know why. ZDNet. Technology News, Analysis,Comments and Product Reviews.
- ^ Cybercrime a huge threat to economy. Cyprus Mail. Cyprus Mail News and More.





















