Tech Support Scam virus (Virus Removal Guide) - Feb 2019 update
Tech Support Scam virus Removal Guide
What is Tech Support Scam virus?
Tech Support Scam is a virus-related application that takes advantage of naive computer users
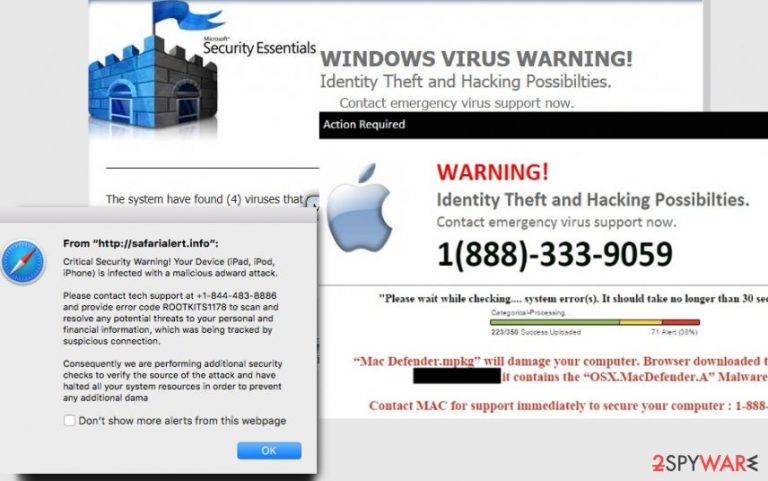
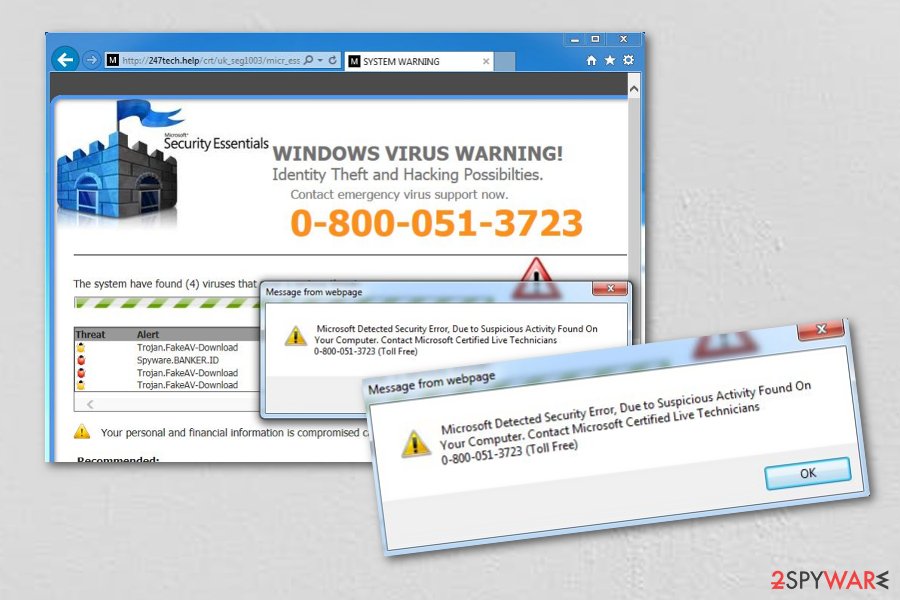
Tech Support Scam virus – a cyber threat which relies on social engineering. The scam has been operating as a deceptive message claiming that the user's computer is infected, compromised or blocked due to different reasons. However, we can assure you that these pop-ups are fake and that your system is targeted by Tech Support scammers who are willing to trick you into contacting them via the given number. This type of scam involves both computer and phone technologies to extort money from computer users. The criminals involved in such scams usually employ tech knowledge and also human psychology to involve their victims into their fraudulent calls. After being contacted, Tech Support scammers either install suspicious software or simply sign up victims to services which they don't need.
| Name | Tech Support Scam |
|---|---|
| Sub-type | PUP/adware |
| Danger level | Medium |
| Distribution | Infected sites, rogue programs |
| Prevention | Avoid suspicious websites, do not install software from unknown sources, use Custom mode while installing freeware to deselect questionable additions |
| Detection | FortectIntego can detect the PUP and related entries |
| Removal | Remove the rogue app by using manual or automatical technique |
Even though the scammers might invent fake companies, they typically work under famous names, such as Microsoft Tech Support, Apple Support, etc. They try to trick the users into obtaining unnecessary products or services which may not even exist. If they do exist, though, they may be merely non-functional or also hazardous to the PC.
Therefore, if you ever see a notification on your computer, claiming that your system is infected with malware or some other system malfunction has unexpectedly occurred, carefully inspect and evaluate this message before taking action[1]. Note that you cannot get a Tech Support Scam refund if the criminals manage to swindle money from you.
Likewise, the smartest choice would be ALWAYS to use professional anti-malware software to help you avoid phishing attacks and protect your system from real cyber infections. For that, we suggest using FortectIntego since it is developed to ensure a quick and safe Tech Support Scam removal for regular computer users.
Additionally, we will attach manual elimination instructions which will show you how to remove the Tech Support Scam virus from both, Windows and Mac operating systems. The only thing we ask is to follow the guide attentively to avoid any misunderstandings and computer damage.
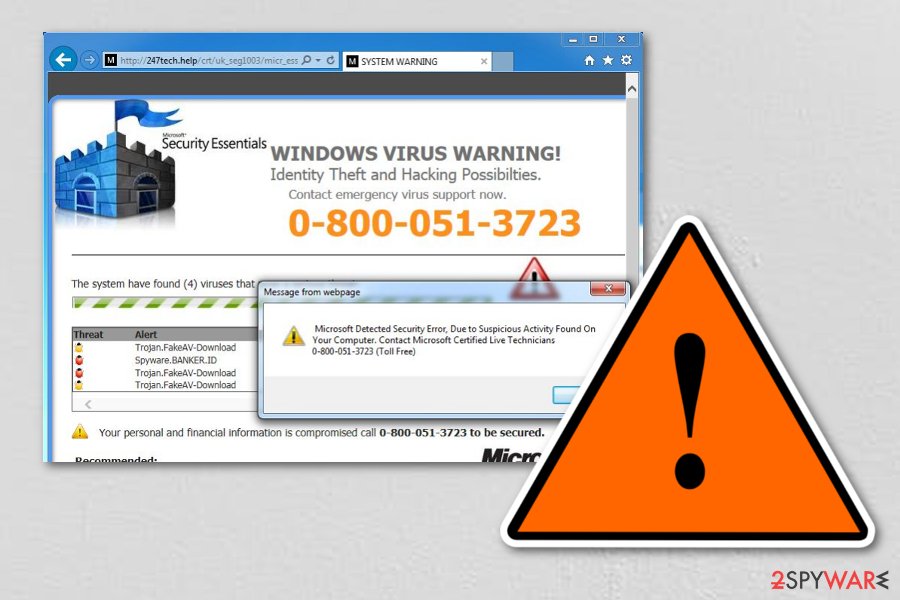
The peculiarities of how Tech Support Scam virus functions
This Tech Support Scam popup begins with a computer infection. Usually, people unconsciously infiltrate a potentially unwanted program called adware[2] on their systems. It might reach your computer via software-bundles or other deceptive distribution techniques.
Adware program starts delivering Tach Support Scam warnings not only on suspicious websites but they might appear on your frequently visited sites as well. So, there is actually no way of indicating what websites you should avoid. Of course, it is always recommended to keep away from obscure and less than reputable sites, but remember, there are no guarantees that such dubious ads will not pop-up on your favorite news page or social networking site as well.
It is difficult to pinpoint what exactly do these ads claim because there are numerous different versions and Tech Support Scam numbers currently roaming the Internet and every one of them may use their tricks to outwit you. The scammers may pretend to be representatives of Windows Helpdesk, Windows Service Center, Microsoft Support or similar supposedly Apple Help Center.
What is know for sure, though, is that these notifications may feature security-related warnings about malware infections or offer you to obtain a subscription to remote technical support to solve your computer’s issues. These notifications always indicate a Tech Support phone number which the user should call to receive or purchase these services.
Unfortunately, if you tried calling the number, you would be immediately connected to a Tech Support scammer rather than a remote professional technician or the Microsoft[3] representative. In such a case, you should hang up at once and scan your computer for malware responsible for generating these warning messages.
Learn how to identify an attack by scammers
Recently, we have received a report about new Tech Support Scam India warning — the user has received a pop-up claiming that his personal information might be leaked. Following that, he was encouraged to call via the provided number to fix this “issue.”
The person behind the phone claimed that he is a Microsoft representative and asked to give remote access to the computer. Later, the user was asked to pay $90 for a three-month support subscription. However, this was merely a phishing attempt which led to considerable financial loses.
Note that giving remote access[4] to your system is extremely dangerous — criminals can easily infiltrate various computer hazards to force you to continue using their fraudulent services. Also, by calling them, you unconsciously provide your phone number which might be later used for further phishing attacks.
Therefore, follow these steps to identify a scam popup:
- Check the URL in the address box it should differ from https://www.microsoft.com/ or https://www.apple.com/;
- Copy the provided so-called support number and check it online (Usually, such numbers have a vast of negative reviews and reports;
- See if you can just close the tab/window and the alert disappears;
- If you called the “support,” any demands to access your system remotely or purchase an expensive security software indicate a scam.
Ways to protect your computer from adware
Since such deceptive alerts appear due to the presence of an adware program, the distribution of this virus is similar to other potentially unwanted programs'. You can easily infect your system by not paying attention when you download/install free applications online.
To prevent this, you should take your time when installing newly downloaded software and always choose the Advanced/Custom installation mode. Also, remember that you must opt out suspicious or unnecessary software package components in the program’s setup if there are any.
Also, be security-cautious online as well. Refrain from visiting unreputable sites, do not click on suspicious links and advertisements. This will help you stay a few steps further from getting infected with such malware. However, do not cross out the possibility of getting infected and equip your system with tools capable of indicating and removing the infection.
The list of Tech support scam virus strains
Adobe Flash Tech Support Scam virus has recently emerged on the cyberspace with the same goal — to swindle money from gullible people. According to the research, it spreads together with freeware or comes as a fake Adobe Flash Update. Once it settles on the system, users receive a message claiming that Windows has been blocked due to suspicious activity and the phishing attack begins.
Pretending to be representatives from Microsoft, these scammers will urge the user to dial 1-888-322-9655 in order to contact remote technicians and “fix” the supposed issue. In reality, the extortionists are simply trying to gain full access and control of the user's computer or attempting to swindle out sensitive information such as credit card details or online banking credentials.
In case you suspect you have become a victim of Adobe Flash Tech Support Scam, cut the network connection immediately and block bank accounts you've provided the scammers the access to.
Microsoft Inc Warning! Support scam virus. Just like most tech support scams, this parasite also operates on behalf of Microsoft technical support. The program is designed to drop notifications alerting the victim about a Trojan virus infection, tricking the user into believing that his/her sensitive information, including banking details, credit card information and account passwords are at risk.
To stop this supposed invasion, the user has to ring up the “Microsoft technicians” with a toll-free number 1-844-507-3556. Of course, the purpose of such a call is entirely different to what the users are made to believe. During the conversation, the scammers may try to convince the victim that his/her computer state is critical and that he/she must buy some security utility to repair it.
Also, they may try to gain the computer's administrative, steal the sensitive information stored on it or install some malicious keylogging software to spy on the victim even after the Microsoft Inc Warning! Support scam virus is eliminated from the computer.
Error 268D3-XC00037 Tech Support scam virus generates pop-ups that issue the message claiming that “YOUR COMPUTER HAS BEEN BLOCKED.” At the end of this warning notification, the user is provided a phone number (+18886098597) to call for help.
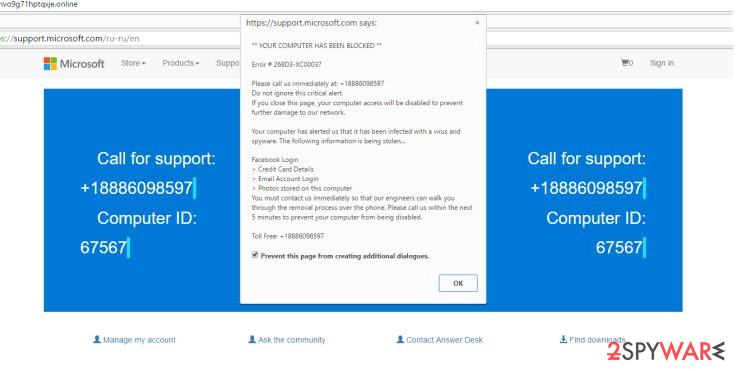
Again, instead of being put through to the technicians from Microsoft, the users who call this number fall into the trap of the fraudulent salespeople that only try to sell them fake products or services. On top of it all, the virus blocks the victim from accessing security sites and downloading security-related software.
Such program must be terminated without hesitation or delay. In case you provided some of your personal details to the scammers, you should also contact the corresponding institutions, to protect yourself from identity theft or financial loss.
Uninstall Tech Support Scam virus and avoid phishing attacks in the future
If you have followed the steps provided above to identify Tech Support Scam virus and found one on your system, not NOT call via the provided number. In case you are asked to give some personal details, do NOT do that as well. Remember, any personal information might be used to gain money from you.
If it is too late for that and you have already given your details and free access to your computer to the criminals, there might still be time to prevent further damage. If the scammers are still connected to your system, terminate the connection immediately. Close the remote access application or reboot the computer.
You can quickly get rid of Tech Support Scam popup by uninstalling the adware from your computer. However, you should first scan the system with a robust anti-malware software to identify whether hackers managed to infiltrate other high-risk computer infections on your PC.
Experts from NoVirus.uk[5] warn that criminals may have installed some key-loggers, Trojans or worms on your computer to spy on you in the future and steal your data. In this case, it would be impossible to detect and remove all potentially dangerous programs on your own. In fact, by doing that you might even permanently damage your system.
Likewise, you should remove Tech Support Scam with professional security software and let it scan your system for other infections. After that, it is important to make sure that criminals won't be able to use the gathered personal information (If they have collected it) in the future. For that, change your system passwords, all the social, email login details, and your online banking passwords.
If you went even further and provided the criminals with your credit card information, inform the credit card company or related bank about it, and they will inform you about the further steps that need to be taken to protect your account. Also, if the crooks are now aware of your sensitive information, such as SSN, home address, date of birth, etc., you should contact the FTC’s and inform them about the potential identity theft.
Finally, after Tech Support Scam removal, you might need to reset your browser settings. We have prepared the instructions on how to do that for all most popular browsers, such as Google Chrome, Mozilla Firefox, Safari, Microsoft Edge, Internet Explorer, etc. You can find them at the end of this article.
You may remove virus damage with a help of FortectIntego. SpyHunter 5Combo Cleaner and Malwarebytes are recommended to detect potentially unwanted programs and viruses with all their files and registry entries that are related to them.
Getting rid of Tech Support Scam virus. Follow these steps
Uninstall from Windows
Since there are numerous versions of Tech Support Scam virus, it might be using different names. You should check your Windows system for any suspicious programs.
Instructions for Windows 10/8 machines:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

If you are Windows 7/XP user, proceed with the following instructions:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.

- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Delete from macOS
Users who think that Mac computers are less targeted by scammers should rethink this option — there are a vast of fake messages delivered by adware programs on Mac OS X. You should search for suspicious names which might be related to adware.
Remove items from Applications folder:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

Remove from Mozilla Firefox (FF)
If you have received a fraudulent warning on Mozilla, search for new entries which might be linked to the adware. Later, remove them and reset your browser.
Remove dangerous extensions:
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

Reset the homepage:
- Click three horizontal lines at the top right corner to open the menu.
- Choose Options.
- Under Home options, enter your preferred site that will open every time you newly open the Mozilla Firefox.
Clear cookies and site data:
- Click Menu and pick Settings.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

Reset Mozilla Firefox
If clearing the browser as explained above did not help, reset Mozilla Firefox:
- Open Mozilla Firefox browser and click the Menu.
- Go to Help and then choose Troubleshooting Information.

- Under Give Firefox a tune up section, click on Refresh Firefox…
- Once the pop-up shows up, confirm the action by pressing on Refresh Firefox.

Remove from Google Chrome
If you want to clean Chrome and stop delivering fake popups, you must check for the components of the adware and uninstall them. Since they might hide under different names, it is important to be attentive.
Delete malicious extensions from Google Chrome:
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Clear cache and web data from Chrome:
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Change your homepage:
- Click menu and choose Settings.
- Look for a suspicious site in the On startup section.
- Click on Open a specific or set of pages and click on three dots to find the Remove option.
Reset Google Chrome:
If the previous methods did not help you, reset Google Chrome to eliminate all the unwanted components:
- Click on Menu and select Settings.
- In the Settings, scroll down and click Advanced.
- Scroll down and locate Reset and clean up section.
- Now click Restore settings to their original defaults.
- Confirm with Reset settings.

Delete from Safari
Remove unwanted extensions from Safari:
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Clear cookies and other website data from Safari:
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

Reset Safari if the above-mentioned steps did not help you:
- Click Safari > Preferences…
- Go to Advanced tab.
- Tick the Show Develop menu in menu bar.
- From the menu bar, click Develop, and then select Empty Caches.

After uninstalling this potentially unwanted program (PUP) and fixing each of your web browsers, we recommend you to scan your PC system with a reputable anti-spyware. This will help you to get rid of Tech Support Scam registry traces and will also identify related parasites or possible malware infections on your computer. For that you can use our top-rated malware remover: FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting adware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Paul Davis. How to Recognize a Fake Virus Warning. Business Know-How. Small Business Strategies & Ideas That Work.
- ^ Margaret Rouse. Adware. Tech Target. Computer Glossary, Computer Terms.
- ^ Microsoft. Wikipedia. The free encyclopedia.
- ^ Remote Access. Techopedia. Tech terms and definitions.
- ^ NoVirus. NoVirus. Security and Spyware News.
