Krypton ransomware (Free Instructions) - Quick Decryption Solution
Krypton virus Removal Guide
What is Krypton ransomware?
Krypton ransomware threatens to delete your files permanently
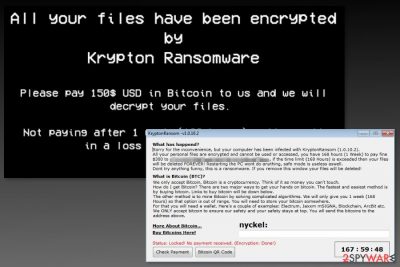
Krypton is a dangerous ransomware virus that sneakily invades your machine, encrypts all your files. After encryption, this HiddenTear[1] based virus appends .kryptonite file extension to the targeted data and demands to pay the ransom in exchange for decryption software.
Krypton virus can affect a variety of popular files, including .doc, .exe, .xls, .jpg, .png, .gif, .mp3, .html and similar. Malware uses a sophisticated encryption algorithm to make files inaccessible by appending a specific file extension. Thus, after the attack, the file called “video.mpg” would be turned into “video.mpg.kryptonite.”
Following data encryption, malware places “KRYPTON_RANSOMWARE.txt” file into each folder that contains encrypted files, changes computer’s desktop picture and shows a pop-up message. The new wallpaper displays the following text:
All your files have been encrypted by Krypton Ransomware. Please pay 150$ USD in Bitcoin to us and we will decrypt your files. Not paying after one week (168 hours) will result in a loss of all your files.
Additionally, the pop-up window called “KryptonRansom -v1.0.10.2” appears. It explains what happened to your system (ironically, it apologizes for the inconvenience caused) and how to pay ransom in bitcoin cryptocurrency. It will place a timer for 168 hours, which, upon expiration, would delete your files permanently.
However, the wallpaper states the ransom demand is 150$ while the pop-up – 300$. Hence, it is very unclear what the actual requirement is. Regardless, we highly advise you not to engage with these cybercriminals[2] as there is no guarantee that you will recover your files, even after paying the ransom.
Quite often, users are ignored and not provided with the promised decryption key. Hence, it is a waste of money and time. Additionally, it encourages hackers to create and distribute more ransomware.
Keep in mind that the only way to keep your data safe is to have an external backup source (like Cloud, for example). Hence, it is critical to back up your files regularly. If you have them, you can call yourself lucky because developers of the Krypton cannot cause you any harm. Otherwise, you are in trouble.
Unfortunately, there is no official software which would decrypt your files at the moment. However, at the end of the article, you can find our alternative suggestions that might help you to get back at least some of your files. But you should try them after Krypton removal.
In order to remove Krypton entirely, you have to uninstall the virus and all files or programs related to it using reputable and professional malware removal software. We recommend completing task using FortectIntego. However, you can choose your preferred software as well.
Stealthy virus spreads in various ways
There are many different ways ransomware can invade victims’ computer. Most common source for such infection is through spam e-mails. Users tend to be very careless when it comes to computer safety. Therefore, victims open the malicious e-mail and click on the attached file (various file types can be used, such as .doc, .xls, .txt, .zip and many others). To avoid that, users should always be vigilant while going through their mailbox.
Peer-to-peer (P2P) networks can be potentially dangerous as hackers might upload their virus as a file which might seem like free software, a security team from lesvirus.fr[3] say. Therefore it is highly recommended avoiding third-party websites and only download software from official sites.
Additionally, fake updates and redirects can lead to ransomware infection. Therefore, we advise always downloading updates from official sources and be alert when being redirected to a third-party website. You should leave the suspicious websites immediately.
Krypton virus removal and file recovery
The very first step after the cyber attack is to remove Krypton virus from your machine. Afterwards, you can proceed with file recovery.
The Krypton ransomware is a severe infection so you should NOT try eliminating it manually. Please be aware that manual Krypton removal requires an in-depth knowledge of system files and registries. Otherwise, accidental Windows system files deletion could lead to permanent computer damage.
To proceed with Krypton ransomware removal, make sure you run a full system scan using FortectIntego or similar anti-malware software. Please be aware that ransomware virus might block the software to protect itself from deletion. Hence, you should use one of your guides which explains how to deal with this problem.
Once you delete Krypton, please proceed with the file recovery. As mentioned above, there is no official software capable of decrypting your files, but we suggest you some alternative ways which might help if you do not have backups.
Getting rid of Krypton virus. Follow these steps
Manual removal using Safe Mode
Rebooting the computer to Safe Mode with Networking can help to disable the virus and run automatic removal smoothly.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Krypton using System Restore
System Restore can also help to disable the virus and perform its elimination.
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Krypton. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Krypton from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If you do not have data backups, your chances to get back encrypted data are not high. However, you should still not pay the ransom, try the additional software and wait for the official decryptor to be released soon.
If your files are encrypted by Krypton, you can use several methods to restore them:
Data Recovery Pro – third-party tool that might restore some of the lost data
This professional software might help to restore some of the files encrypted by Krypton ransomware. However, it's not an official decryptor, so you should not expect full data recovery.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Krypton ransomware;
- Restore them.
Windows Previous Versions feature might help to recover the most important files
If System Restore was enabled before the cyber attack, you can copy individual versions of files by following these steps:
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Try ShadowExplorer if malware left Shadow Volume Copies untouched
In order to use ShadowExplorer for data recovery, you have to make sure that Krypton did not delete Shadow Volume Copies of the targeted data.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
The official Krypton decryptor is not released yet.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Krypton and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Hidden Tear Project: Forbidden Fruit Is the Sweetest. Tripewire. News, trends, and insights.
- ^ Harold Stark. When Attacked By Ransomware, The FBI Says You Shouldn't Pay Up. Forbes. Business, investing, technology, entrepreneurship, leadership, and lifestyle website.
- ^ Les Virus. Les Virus. Malware research data and cyber security news.





















