Lok ransomware (virus) - Free Instructions
Lok virus Removal Guide
What is Lok ransomware?
Lok ransomware locks your files and demands ransom for their return
If your files can no longer be opened and have a .lok extensions attached to them, you have been infected with ransomware. Ransomware is one of the most dangerous computer infections out there because it commonly results in users losing their pictures, documents, videos, and other personal data forever, although the outcome can be completely different under particular circumstances.
Lok ransomware is a new strain that was first noticed in January of 2022 and didn't seem to be connected to any previous strain. Just like any other malware of this type, it is likely to be spread via the most common distribution methods such as fake updates, malspam,[1] software vulnerabilities,[2] repacked software, cracks, and similar. Regardless of which method is used, users are always ticked into installing malware without realizing what they have done.
Once installed, the malware begins to initiate changes within the Windows machine before it proceeds to its main goal. These modifications serve as grounds that enable data encryption, during which all personal files are stripped of their regular icons and appended with the .(ID)(pedarsaggg@onionmail.org).lok extension. Suchlike data can no longer be accessed or modified by the users.
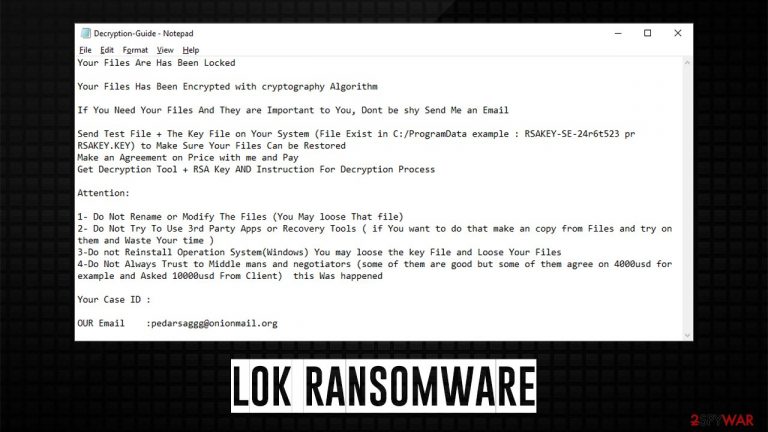
After that, the virus drops two ransom notes – Decryption-Guide.HTA and Decryption-Guide.txt. Both are meant to serve as the first communication between cybercriminals and victims. Within the note, crooks explain what has happened with users' files and ultimately tell them that they need to pay up to restore the currently inaccessible data:
Your Files Are Has Been Locked
Your Files Has Been Encrypted with cryptography Algorithm
If You Need Your Files And They are Important to You, Dont be shy Send Me an Email
Send Test File + The Key File on Your System (File Exist in C:/ProgramData example : RSAKEY-SE-24r6t523 pr RSAKEY.KEY) to Make Sure Your Files Can be Restored
Make an Agreement on Price with me and Pay
Get Decryption Tool + RSA Key AND Instruction For Decryption ProcessAttention:
1- Do Not Rename or Modify The Files (You May loose That file)
2- Do Not Try To Use 3rd Party Apps or Recovery Tools ( if You want to do that make an copy from Files and try on them and Waste Your time )
3-Do not Reinstall Operation System(Windows) You may loose the key File and Loose Your Files
4-Do Not Always Trust to Middle mans and negotiators (some of them are good but some of them agree on 4000usd for example and Asked 10000usd From Client) this Was happenedYour Case ID :
OUR Email :pedarsaggg@onionmail.org
While it is true that you should never trust what malicious actors say, there are facts that simply can't be denied, and that is the encrypted data. Once the system is infected, the malware uses a sophisticated RSA encryption algorithm to lock all files, which renders them unusable, and only the attackers have access to the required key to decipher them.
That being said, there is no guarantee that Lok virus authors would deliver the promised tool after you pay, so you are risking losing your money, along with your files. While it is true that some crooks keep their promises, remember, regardless of what the truth is, you should never trust cybercriminals, as there were plenty of people who suffered more damages because of it.
Instead, we recommend following through with the instructions below in order to remove malware and attempt to recover data using alternative solutions. Likewise, we also provide tips along the way to ensure this horrible scenario would not happen in the future.
| Name | Lok virus |
|---|---|
| Type | Ransomware, file-locking malware, cryptovirus |
| File extension | .lok, appended to each of the non-system and non-executable files |
| Ransom note | Decryption-Guide.HTA and Decryption-Guide.txt, placed on the desktop |
| Contact | pedarsaggg@onionmail.org |
| Data Recovery | If no backups are available, recovering data is almost impossible. However, we suggest you try the alternative methods that could help you in some cases – we list them below |
| Malware removal | Manual virus removal is not recommended, as it might be difficult for regular users. Instead, SpyHunter 5Combo Cleaner or other anti-malware tools should be used |
| System fix | Malware can seriously tamper with Windows systems, causing errors, crashes, lag, and other stability issues after it is terminated. To remediate the system and avoid its complete corruption, we recommend scanning it with the FortectIntego repair tool |
Ransomware is as successful as its delivery methods, as there are thousands of new strains that rise and manage only infect a few victims, which is by no means beneficial for the attackers. Unfortunately, the success of ransomware such as Yber or Zaqi (both of which are Djvu variants) means that more users suffer the consequences of the infection.
Thus, it is important to secure your computer from malware and correctly prepare for the incoming malware attacks if such would occur in the future. Here are a few tips from security experts:
- Do not open attachments of emails of unknown origin and beware of spoofed emails[3] that might look like they are coming from somebody you know – the “From” email can be faked;
- Never download software cracks or pirated programs from torrent sites;
- Employ an ad-blocker to stop malicious scripts from being executed;
- Use strong passwords for all your accounts and never reuse them (or use a powerful password manager);
- Install all the latest updates for your operating system and all programs;
- Ensure that a powerful anti-malware, such as SpyHunter 5Combo Cleaner or Malwarebytes, is always running in the background and never ignore its warnings.
Removal steps
1. Disconnect from the internet
Once ransomware is installed on the device, it can no longer be considered safe to operate. The virus might spread to other computers via the network (if such is available) and even compromise the system further for implementation of other malware. Remote connection over the internet can also provide crooks remote access to users' PCs under certain circumstances, thus removing this connection is important before proceeding with Lok ransomware removal.
If the infected PC is not connected to a network, you can simply disconnect it by plugging out the ethernet or using the WiFi symbol in the taskbar. However, if a large network is affected, you should proceed with the following to disconnect all machines at once:
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet
- Click Network and Sharing Center
- On the left, pick Change adapter settings

- Right-click on your connection (for example, Ethernet), and select Disable

- Confirm with Yes.
2. Perform a full system scan
Once your computer is successfully segregated from the rest of the network and the internet, you should now remove the infection from your device. While it is true that some ransomware simply self-destructs after they complete the data-locking process, there could be additional payloads or modules that might be implemented by it.
For a secure and effective elimination, you should run a full system scan with SpyHunter 5Combo Cleaner, Malwarebytes, or another powerful security application. In case you can't run anti-malware for some reason (the threat might be tampering with it), you can reboot your system in Safe Mode and perform a full scan from there:
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on the Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find the Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.
- Go to Advanced options.
- Select Startup Settings.

- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.
Once you get into the Safe Mode, use powerful security software to perform a full system scan. You might have to have the installer of the program within the thumb drive, execute it, install, update, and only then run a scan.
3. Restore your files
While the principle of ransomware operation is rather simple on paper, the encryption element is something rather complex. Since users find their files inaccessible, they might think that they are permanently corrupted, although it is not true at all. If the encryption was performed correctly, the files are simply locked behind a unique, complex password that consists alphanumeric character string.
This password, generally known as the key, is only accessible to the crooks behind Lok ransomware, thus making the whole operation work well. If users want it, they need to pay a fee, and they might or might not send it to them. As we already mentioned, paying criminals is not only risky, but it also proves that the illegal business model works well, and they will continue infecting other users all over the world.
It is also important to mention that running a scan with security software would not restore .look files, and they will remain locked even after the virus is deleted. This trait of ransomware is what makes it so devastating and also effective. Of course, if you had backups for your files, you have already mitigated the most damaging issue, and you can simply recover data with ease.
Unfortunately, many home users choose not to back their files and end up regretting this decision once ransomware strikes. We show how to backup files for the future at the bottom of this post.
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

Security researchers are constantly working on battling malicious actors and helping victims by creating free decryptors. Unfortunately, such a tool is not yet developed for this malware family. There are several places where you could look for decryptors in the future:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

4. Repair damaged system components
Once you remove any type of malware from your system with security software, some of the system files might remain damaged, as anti-malware is unable to restore them to their previous state. As a result, you might later experience system crashes, BSODs, random restarts, registry errors, and more issues. If that is the case, we strongly recommend running a PC repair software that would get rid of leftover files and repair damaged system components automatically for you.
- Download FortectIntego
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

Getting rid of Lok virus. Follow these steps
Create data backups to avoid file loss in the future
One of the many countermeasures for home users against ransomware is data backups. Even if your Windows get corrupted, you can reinstall everything from scratch and retrieve files from backups with minimal losses overall. Most importantly, you would not have to pay cybercriminals and risk your money as well.
Therefore, if you have already dealt with a ransomware attack, we strongly advise you to prepare backups for future use. There are two options available to you:
- Backup on a physical external drive, such as a USB flash drive or external HDD.
- Use cloud storage services.
The first method is not that convenient, however, as backups need to constantly be updated manually – although it is very reliable. Therefore, we highly advise choosing cloud storage instead – it is easy to set up and efficient to sustain. The problem with it is that storage space is limited unless you want to pay for the subscription.
Using Microsoft OneDrive
OneDrive is a built-in tool that comes with every modern Windows version. By default, you get 5 GB of storage that you can use for free. You can increase that storage space, but for a price. Here's how to setup backups for OneDrive:
- Click on the OneDrive icon within your system tray.
- Select Help & Settings > Settings.

- If you don't see your email under the Account tab, you should click Add an account and proceed with the on-screen instructions to set yourself up.

- Once done, move to the Backup tab and click Manage backup.

- Select Desktop, Documents, and Pictures, or a combination of whichever folders you want to backup.
- Press Start backup.

After this, all the files that are imported into the above-mentioned folders will be automatically backed for you. If you want to add other folders or files, you have to do that manually. For that, open File Explorer by pressing Win + E on your keyboard, and then click on the OneDrive icon. You should drag and drop folders you want to backup (or you can use Copy/Paste as well).
Using Google Drive
Google Drive is another great solution for free backups. The good news is that you get as much as 15GB for free by choosing this storage. There are also paid versions available, with significantly more storage to choose from.
You can access Google Drive via the web browser or use a desktop app you can download on the official website. If you want your files to be synced automatically, you will have to download the app, however.
- Download the Google Drive app installer and click on it.

- Wait a few seconds for it to be installed.

- Now click the arrow within your system tray – you should see Google Drive icon there, click it once.

- Click Get Started.

- Enter all the required information – your email/phone, and password.

- Now pick what you want to sync and backup. You can click on Choose Folder to add additional folders to the list.
- Once done, pick Next.

- Now you can select to sync items to be visible on your computer.
- Finally, press Start and wait till the sync is complete. Your files are now being backed up.
Report the incident to your local authorities
Ransomware is a huge business that is highly illegal, and authorities are very involved in catching malware operators. To have increased chances of identifying the culprits, the agencies need information. Therefore, by reporting the crime, you could help with stopping the cybercriminal activities and catching the threat actors. Make sure you include all the possible details, including how did you notice the attack, when it happened, etc. Additionally, providing documents such as ransom notes, examples of encrypted files, or malware executables would also be beneficial.
Law enforcement agencies typically deal with online fraud and cybercrime, although it depends on where you live. Here is the list of local authority groups that handle incidents like ransomware attacks, sorted by country:
- USA – Internet Crime Complaint Center IC3
- United Kingdom – ActionFraud
- Canada – Canadian Anti-Fraud Centre
- Australia – ScamWatch
- New Zealand – ConsumerProtection
- Germany – Polizei
- France – Ministère de l'Intérieur

If your country is not listed above, you should contact the local police department or communications center.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Lok and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Malspam: A simple and traditional attack technique that continues to be favorite among bad actors. Cyware. Threatt Intelligence Solutions.
- ^ Vulnerability (computing). Wikipedia. The free encyclopedia.
- ^ What is Email Spoofing?. Proofpoint. Security research blog.
