Malicious.moderate.ml.score (Removal Instructions) - Free Guide
Malicious.moderate.ml.score Removal Guide
What is Malicious.moderate.ml.score?
Malicious.moderate.ml.score is an AV detection name for malware, although might also mean a false positive
Malicious.moderate.ml.score is a heuristic detection[1] name for suspicious files used by Trapmine security software. Users reported that several files that they uploaded to analysis engines like Virus Total, were detected as such, although some of these executables were harmless.[2] General detection names are typically used for unrecognized malware, i.e., files that might be potentially malicious. Nevertheless, it is also worth mentioning that Malicious.moderate.ml might also indicate that a virus or a Trojan is trying to get into your machine, so caution should always be practiced.
| Name | Malicious.moderate.ml.score |
| Type | Heuristic detection name for malware (possibly a false-positive) |
| Detected by | Trapmine security software |
| Infection means | Threat actors can infect your computer by using many different malware distribution methods, including fake updates, software cracks, exploits, drive-by-downloads, phishing messages, etc. |
| Symptoms | Since Malicious.moderate.ml.score is a heuristic detection, it can represent a variety of different malware types; the symptoms depend on the type of malware that infected your computer. Some malware infection signs include computer slowdowns, errors, crashes, high CPU/memory usage, etc. |
| Fix | You only need to remove Malicious.moderate.ml.score if the file is malicious; in case of a false positive, add the file or path to the exclusion list |
| Recovery | To remediate your Windows and fix crashes, and other issues that may arise post-infection, scan your computer with FortectIntego |
If you start analyzing the name Malicious.moderate.ml.score, you will see that it includes the word “moderate,” which means that the .dll, .exe or another file was marked as a medium probability of being malicious, based on the AI (artificial intelligence) score.
Many anti-malware programs are using machine-learning technology, which includes a lot of data gathered by end-point protection products. These security applications often employ multiple engines in order to analyze files – some of which might be immediately detected as malicious, while others might not. In the case when the object was never seen before by AV, and never analyzed by other engines, a generic, i.e., heuristic detection is used – and that is what Malicious.moderate.ml.score is.
While the heuristic detection exists to flag Trojans, worms, ransomware, and other dangerous malware, it may sometimes confuse the user. For example, if you download a legitimate software installer which is flagged by your anti-virus software as Malicious.moderate.ml.score, you will most likely ask the question “why?”.
The truth is that even legitimate websites and servers sometimes get hacked, and malicious executables replace original ones (for example, in January 2019, the official ASUS Live Update Utility pushed backdoor malware after a server compromise).[3] Therefore, even if the executable comes from a trusted source, it does not mean it is secure.
In such a case, it is important to remove Malicious.moderate.ml.score virus as soon as possible, as it may be set to perform various malicious activities on your system, such as:
- mining cryptocurrency
- logging keystrokes
- encrypting personal files
- sending spam, etc.
However, it is important to remember that Malicious.moderate.ml.score removal should not be rushed if the detection was flagged by the security software, and you are confident that the file is most likely safe. To make you decide, you should upload it to Virus Total to see if multiple other AV engines detect it as well. If so, you should terminate the file immediately.
However, if the detection rate of Malicious.moderate.ml.score is low, you can add it to the exclusions list, which will allow you to proceed with the installation of the app or usage of a file. Just to be sure, you should contact the developer or distributor, as well as the AV vendor you are using if you have any doubts.
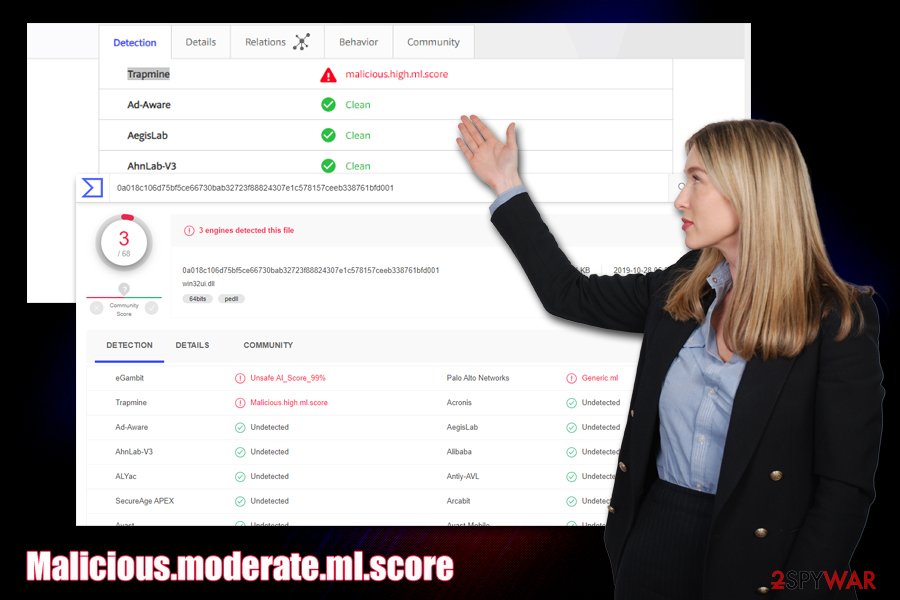
There are also two similar detection names that you may encounter if you use Trapmine security software – Suspicious.low.ml.score and Malicious.high.ml.score. These detections represent the probability of the file or object being malware, so you should not ignore the evaluation score that is marked as “high.”
In case you did get infected with malware, and Malicious.moderate.ml.score was not a false positive, get rid of it with your security software. In case you notice your computer lagging, crashing, or bothering you with errors, you should employ PC repair utility FortectIntego – it can get rid of malware damage immediately and remediate your Windows system.
Security tips to stay safe online
At present, malware is versatile and sophisticated, although there are also plenty of buggy and failed creations in the wild. Nevertheless, you do not want either on those on your system, as even buggy malware might negatively impact your computer.
If you think that “being careful online” is enough to protect your computer, you are very wrong, as some malware distribution techniques are so advanced that you will not even know about them. For example, AI-based malware can hide inside applications without disclosing its prescience,[4] fileless malware[5] can inject malicious code directly into memory and avoid detection, and ransomware developers may employ innocently-looking Super Mario picture to infect your computer instantaneously.
To start with, you should always employ automated tools that are capable of analyzing samples in real-time – most of the antivirus vendors provide such functionality, although many free versions only offer this functionality with the full version of the software only – so make sure real-time protection is enabled.
You should also ensure that you update your software/Windows regularly, do not open malicious spam email attachments, protect all your accounts with strong passwords (use two-factor authentication where possible), employ ad-block, and never download software cracks.
Malicious.moderate.ml.score removal solution
As mentioned above, you should only remove Malicious.moderate.ml.score if you are confident that it is actually malicious. In some cases, this might require some judgment from your part. Nevertheless, sometimes this might be easier said than done, as there are millions of files deployed from various websites every day.
If you believe that the file might be a false positive, we highly advise you contact the developer or the website author that distributes it and ask about the detection. In many cases, false positives are already known by app developers, although it does take some time for the definitions to be updated. Thus, you should simply wait a few days after you report a false positive for testing. In other cases, you can also contact the vendor of your AV – the support should help each case individually.
Only if you confirm that the detection is not a false positive, you can proceed with Malicious.moderate.ml.score removal. Simply use anti-malware software to get rid of the file for you. However, if you already had Malicious.moderate.ml.score virus installed, you should employ a security tool to detect all the malicious files as well.
Getting rid of Malicious.moderate.ml.score. Follow these steps
Manual removal using Safe Mode
In case Malicious.moderate.ml.score virus is tampering with your security software, access Safe Mode with Networking and perform a scan from there:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Malicious.moderate.ml.score and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting malware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Heuristic analysis. Wikipedia. The free encyclopedia.
- ^ Virustotal Trapmine suspicious.low.ml.score. StackOverflow. Question and answer site.
- ^ Ryan Whitwam. Asus Live Update Pushed Malware to 1 Million PCs. ExtremeTech. Top destination for Tech News.
- ^ Kevin Townsend. IBM Describes AI-powered Malware That Can Hide Inside Benign Applications. SecurityWeek. Internet and enterprise news, insights & analysis.
- ^ Allie Mellen. Fileless malware 101: Understanding non-malware attacks. Cybereason. Endpoint Protection, Detection, and Response.














