MegaCortex ransomware (Removal Guide) - updated May 2019
MegaCortex virus Removal Guide
What is MegaCortex ransomware?
MegaCortex is a sophisticated crypto-locking malware that employs both automated and manual components for its infection
MegaCortex is a ransomware-type virus that targets corporations for money extortion purposes and is another example of large scale attacks that incorporate the “big game hunting”[1] technique, which is only used in targeted attacks. The threat is not new, and has been infecting organizations since January 2019, but become especially active at the start of May of the same year, infecting corporations around the world. Recently, malware reappeared with .m3g4c0rtx extension.
Initially, Sophos researchers claimed[2] that MegaCortex ransomware operates together with Emotet and Qakbot viruses, as these threats were also present during the first samples that experts examined. Nevertheless, further research that was published a week later[3] uncovered that this strain also uses the same Common Name (CN) on the digital certificate as Rietspoof malware, although no other connections to the latter were found.
Once the main executable rstwg.exe, winnit.exe, or other is launched, MegaCortex ransomware performs file encryption with the help of encryption algorithm[4] and then appends .aes128ctr file extension, although different types of appendixes were noticed in the wild.
Soon after that, the malware drops !!! _ READ_ME _ !!!.txt ransom note, in which hackers offer a decryption tool for a price, as well as the alleged tips on how to improve the company's security levels and a guarantee that it will remain safe from further MegaCortex virus attacks.
| Name | MegaCortex |
|---|---|
| Type | Ransomware/ crypto virus |
| Malware executable | rstwg.exe, winnit.exe, or other |
| File marker | .aes128ctr, .m3g4c0rtx |
| Contact emails | shawhart1542925@mail.com, anderssperry6654818@mail.com |
| main target | Businesses, worldwide companies, home users |
| Already affected |
76 confirmed attacks from these countries:
|
| Ransom note | !!! _ READ_ME _ !!!.txt |
| Distribution | Infected documents, PSExec utility |
| Main damage | Locks data, leads to money loss or damaged data, can also install a password-stealing virus |
| Elimination | Use SpyHunter 5Combo Cleaner for MegaCortex removal. Get FortectIntego to repair virus damage |
MegaCortex malware gets delivered using Windows domain controllers. According to recent reports, attackers gain remote access to the chosen network and configure the domain controller to distribute a copy of PsExec – the service running executable of the malware.[2]
Additionally, MegaCortex ransomware gets on the system and disables security services or programs to keep on running without interruption. Encryption starts and quickly ends with files marked with .aes128ctr extension. This marker may change from sample to sample. As Sophos has reported, the virus has infected its clients from the United States, Canada, Australia, Hong Kong, Indonesia, the Netherlands, France, Ireland, Argentina, and Italy. Beware that home users may also be infected in the future!
MegaCortex samples were discovered on May 1, 2019. It is known that the virus compromises the domain controller and when the Cobolt Strike is dropped and launched, it launches the main executable designed to start the main process of the cryptovirus. Additionally to these processes, the specific batch of files get executed to disable 44 particular processes and more than 200 Windows services.
Changes initiated by MegaCortex ransomware can also include:
- changed startup preferences;
- added or altered registry entries;
- installed or disabled programs;
- added files and malware.
When MegaCortex ransomware ends the encryption process, encoded files get marked with either .aes128ctr or the recent .m3g4c0rtx extension. Also, the virus creates other data on the affected system, like DLL with the list of encrypted file names and drops the ransom note on the desktop and in various folders on the computer.
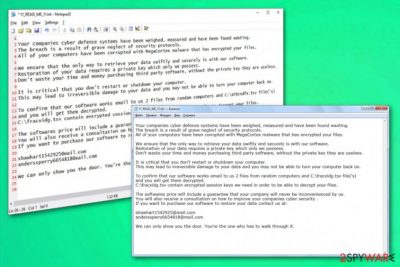
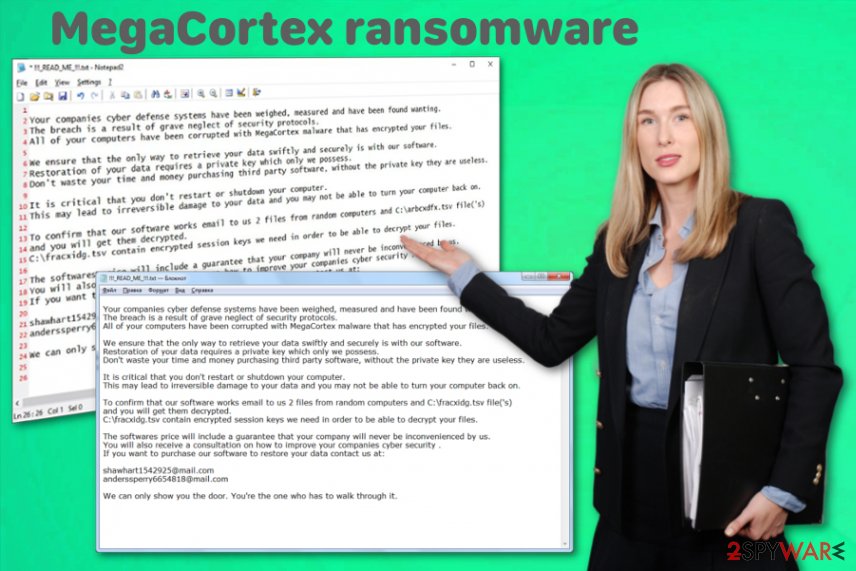
The MegaCortex ransomware ransom note !!! _ READ_ME _ !!!.txt reads the following:
Your companies cyber defense systems have been measured, measured and have been found wanting.
The breach is a result of the security protocols.
All of your computers have been corrupted with MegaCortex malware that has encrypted your files.
We must ensure that your data is swiftly and securely.
Restoration of your data requires a private key.
They are useless.
It is critical that you restart or shutdown your computer.
It can lead to irreversible damage to your computer back.
To confirm that our software works email to us 2 from random computers files is and the C: \ fracxidg.tsvfile ( 's)
and you will of the get Them decrypted.
C: \ fracxidg.tsv
It will never be inconvenienced by us.
Cyber security.
If you want to contact us at
shawhart1542925@mail.com
anderssperry6654818@mail.com
We can only show you the door. Through one.
The developers of MegaCortex seem to be struggling to look more credible, so they offer to test their decryption service (two files precisely) for free. Even if they recover those files without any pay, you shouldn't trust them and provide the demanded ransom. Get the professional anti-malware tools and get rid of the virus instead.
For the best MegaCortex ransomware removal results, you should rely on a reliable tool designed to fight malware. You can base your choosing on malware detection rate.[5] Make sure to avoid any unsafe installations and get the tool from reputable sources.

Various specialists from the cybersecurity field[6] have been offering using FortectIntego or SpyHunter 5Combo Cleaner for the proper job. Remove MegaCortex ransomware completely and make sure to clean the system from other possible programs or virus damage. Perform a full scan on the infected PC and follow with suggested steps.
The same solution is offered for companies since ransomware has mostly been targeting networks of corporations. The professional IT specialist should employ an antivirus tool to clean the entire network and then use backups to recover files encrypted by MegaCortex ransomware.
An operating system doesn't require permission when ransomware gets installed in the background
Emails often get ignored and this way cyber infections happen on the machine because file attachments or hyperlinks included, spreads malicious scripts. When the payload is dropped on the system, various malware can be launched and automatically installed.
Once this is done, trojans, malware or even ransomware itself starts running needed processes immediately. Since this particular virus gets delivered with the help of trojans and malware, it is not easy to spot cyber infections because the virus runs in the background. However, the appearance of rstwg.exe in your Task Manager should make you worried.
However, you can avoid such processes by paying more attention to the emails you receive in your email box. When any suspicious or questionable email appears in the box to make sure to delete it and exit the notification if any files get attached to that. One click on the included hyperlink or accidental installation of a document can lead to automatic ransomware infiltration, and then you risk getting your files damaged.
Terminate MegaCortex ransomware and make sure to clean the machine fully
To remove MegaCortex ransomware from the affected computer or even the network, you need to disconnect your PCs from the Internet and run a full system scan with a professional anti-virus. If you go for a free tool, you risk getting PUPs or more dangerous cyber threats.
Make sure to learn about MegaCortex virus features and potential risks before attempting any processes. Also, rely on file backups and data recovery software when trying to restore encrypted files. This can only be achieved after profer system cleaning.
Automatic MegaCortex removal using anti-malware tools like FortectIntego, SpyHunter 5Combo Cleaner, or Malwarebytes can give the advantage of detecting other malware besides the cryptovirus and eliminating corrupted files, PUPs from the machine.
Getting rid of MegaCortex virus. Follow these steps
Manual removal using Safe Mode
Rely on system reboot in Safe Mode with Networking and then scan the system with AV tool to remove MegaCortex ransomware
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove MegaCortex using System Restore
You can benefit from System Restore feature that allows recovering the system in a previous state
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of MegaCortex. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove MegaCortex from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by MegaCortex, you can use several methods to restore them:
Data Recovery Pro is the program designed to replace file backups in the data restoring process
It is possible to restore files encrypted by MegaCortex ransomware without having backed up files. Try Data Recovery Pro for accidentally deleted files or data encrypted
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by MegaCortex ransomware;
- Restore them.
Windows Previous Versions feature allows recovering files after MegaCortex ransomware intervension
When System Restore gets enabled, Windows Previous Versions can get used in file recovery
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer is the feature replacing file backups in the data recovery process
Shadow Volume Copies should be untouched by the ransomware, for ShadowExplorer to work
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Decryption is not possible for MegaCortex ransomware
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from MegaCortex and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Olivia Morelli . Pinchy Spider group takes up Big game hunting with GandCrab. 2-spyware. Cybersecurity news and articles.
- ^ Andrew Brandt. “MegaCortex” ransomware wants to be The One. Sophos. Naked security news.
- ^ Andrew Brandt. MegaCortex, deconstructed: mysteries mount as analysis continues. Sophos. Naked security news.
- ^ Advanced Encryption Standard. Wikipedia. The free encyclopedia.
- ^ Malware sample detection rate. VirusTotal. Online malware scanner.
- ^ Virusi. Virusi. Spyware related news.





















