Mzop ransomware (virus) - Free Instructions
Mzop virus Removal Guide
What is Mzop ransomware?
Mzop ransomware holds files hostage until a ransom in bitcoin is paid
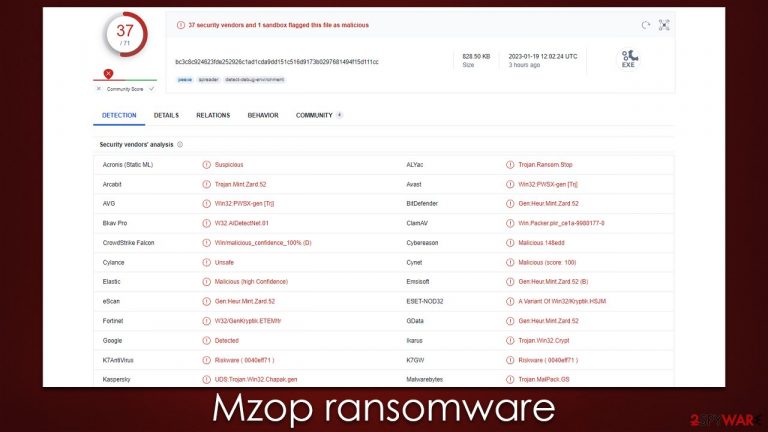
Mzop is a ransomware-type virus that targets computers and devices in order to extort money from victims. Belonging to the large family of Djvu, this version was released by cybercriminals in the second half of January 2023.
The Mzop virus is typically distributed through cracked software installers from illegal websites, yet other means of transmission can be used by malicious hackers. Despite the method for distribution, all victims unintentionally download it without realizing that something could be wrong until they observe the first signs of infection.
Once the ransomware successfully infiltrates a device or system, it will begin to encrypt all of the data stored on that device or network. Encryption locks out any legitimate user from accessing the data until a ransom is paid for a decryption key.
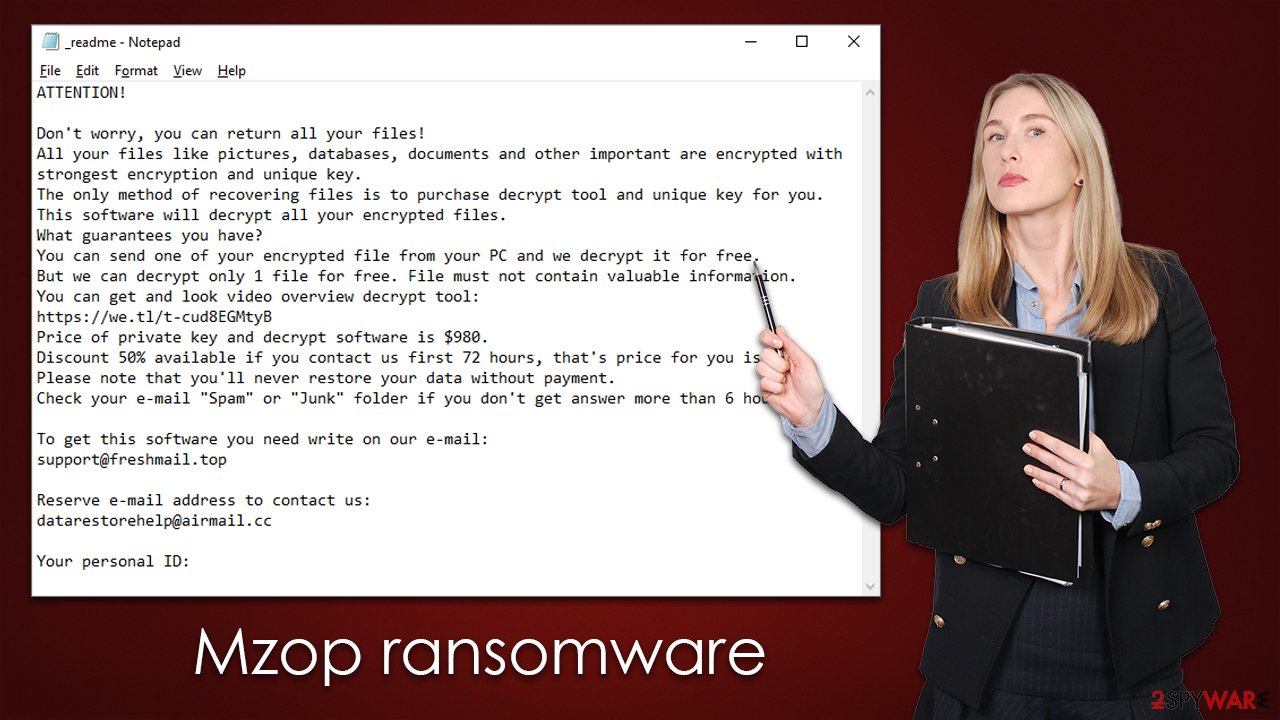
Mzop ransomware usually displays a ransom note _readme.txt on the infected system or device, informing victims of the data encryption and demanding payment in exchange for decryption. According to the note, victims have to pay $980 (or $490 with a discount) in bitcoin for a decryption tool that should help users restore all files back to normal. They also provide two emails for communication – datarestorehelp@airmail.cc and support@freshmail.top.
| Name | Mzop virus |
|---|---|
| Type | Ransomware, file-locking malware |
| File extension | .mzop extension affixed to all personal files, rendering them useless |
| Family | Djvu |
| Ransom note | _readme.txt dropped at every location where encrypted files are located |
| Contact | datarestorehelp@airmail.cc, support@freshmail.top |
| File Recovery | There is no guaranteed way to recover locked files without backups. Other options include paying cybercriminals (not recommended, might also lose the paid money), using Emisoft's decryptor (works for a limited number of victims), or using third-party recovery software |
| Malware removal | After disconnecting the computer from the network and the internet, do a complete system scan using the SpyHunter 5Combo Cleaner security program |
| System fix | As soon as it is installed, malware has the potential to severely harm some system files, causing instability problems, including crashes and errors. Any such damage can be automatically repaired by using FortectIntego PC repair |
Ransom note
As soon as malware infiltrates the system and successfully encrypts all data on it, it provides a ransom note that is supposed to help victims get bitcoin and transfer money to the attackers:
ATTENTION!
Don't worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-cud8EGMtyB
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don't get answer more than 6 hours.To get this software you need write on our e-mail:
support@freshmail.topReserve e-mail address to contact us:
datarestorehelp@airmail.ccYour personal ID:
As we said many times, please do not pay the ransom, as there is no guarantee that the attackers will keep their promises or that the decryptor will actually work. Even if it does, the act of paying cybercriminals only supports their malicious activity, prompting them to create more advanced versions of malware and spread it to as many users as possible.
Djvu: one of the most prominent malware families out there
The Djvu malware family is arguably one of the most notorious trojans out there, giving rise to Mzop ransomware. Despite attempts to eradicate it, this threat continues to plague home users across numerous iterations. It's estimated that hundreds of people fall prey to its maliciousness every single day.
While there may be slight distinctions between the released versions, their encryption methods are all based on RSA cipher, and they similarly provide identical ransom notes and demand a similar amount of money in bitcoin cryptocurrency. Notably, criminals alter contact emails regularly to elude discovery by law enforcement agencies.
Cybercriminals are known to use four random letters in the virus name, a notable trait among its many versions, including Poqw, Bozq, and Zouu. Despite slight differences between versions, the primary aim remains unchanged – locking personal data and seeking ransom until payment is made by victims.
Remove the infection
When ransomware has seized control of your files, it is not uncommon to feel panicked. All the same, try and stay composed – as adhering to these essential steps in their exact order will help protect you against further damage as well as help restore your data. To begin with, strive for the complete removal of Mzop ransomware from your system.
To protect your network, devices, and data from potential malicious activities, it is imperative to unplug the infected computer from any internet connection. By doing this, you will stop malware communication with its Command & Control server that could potentially cause unwanted harm. Disconnecting completely not only preserves the integrity of your digital assets but also provides peace of mind knowing that no attacks are taking place in the background.
When offline, you can start the ransomware removal process. Manually eliminating these threats is a possibility but necessitates excellent IT skills and should thus be avoided at all costs. To ensure an effective clean-up of your system, use automated malware removal applications such as SpyHunter 5Combo Cleaner or Malwarebytes, which will detect and erase malicious files quickly.
To safeguard your system from unexpected crashes, errors, and other technical issues triggered by malware intrusion, make sure to perform a routine scan with PC repair software, such as FortectIntego. It's the swiftest way of avoiding all kinds of problems that may arise in the future without needing to endure the tedious task of reinstalling Windows.
Data recovery explained
As the final step, we must now uncover our locked files without paying a hefty fee to cybercriminals. Most people aren't familiar with data encryption and are unaware of their options when it comes to restoring encrypted files – some may believe simply running an anti-virus scan is enough, while others assume that once they're lost, there's no way back. However, in this instance, neither of these assumptions stands true.
There are a few ways if recovering your data, including:
- Use a recent backup to restore your files. This is the most reliable method, but it only works if you have a current backup.
- Use file recovery software to scan your hard drive and attempt to recover deleted or damaged files. These programs may be able to recover some of your encrypted files.
- Attempt to restore encrypted files using Emsisoft's decryption tool that was specially crafted for Djvu ransomware victims. Keep in mind that this method may not always work for everyone, but it is still recommended to try it.
Let's start with Emsisoft decryptor because if you're lucky, you might be able to restore all Mzop files.
- Download the app from the official Emsisoft website.
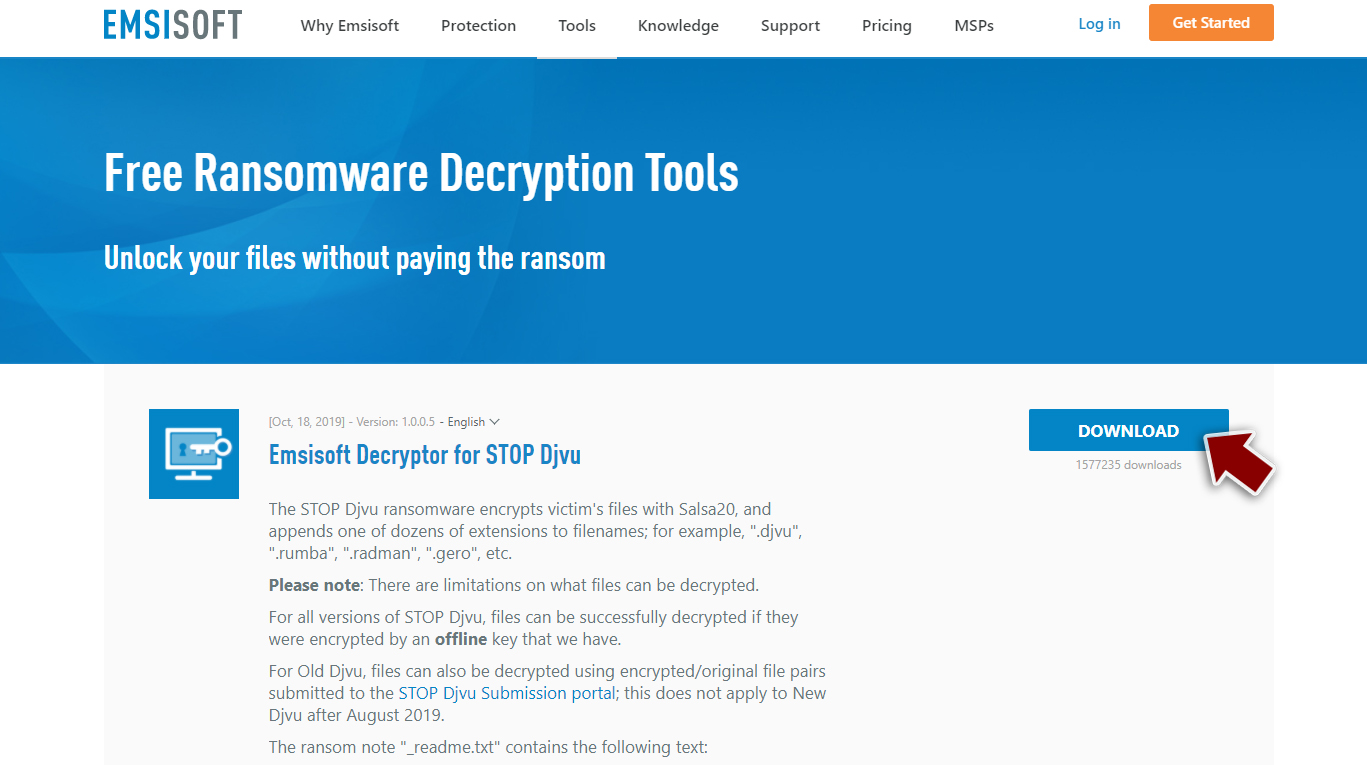
- After pressing Download button, a small pop-up at the bottom, titled decrypt_STOPDjvu.exe should show up – click it.

- If User Account Control (UAC) message shows up, press Yes.
- Agree to License Terms by pressing Yes.
- After Disclaimer shows up, press OK.
- The tool should automatically populate the affected folders, although you can also do it by pressing Add folder at the bottom.

- Press Decrypt.

From here, there are three available outcomes:
- “Decrypted!” will be shown under files that were decrypted successfully – they are now usable again.
- “Error: Unable to decrypt file with ID:” means that the keys for this version of the virus have not yet been retrieved, so you should try later.
- “This ID appears to be an online ID, decryption is impossible” – you are unable to decrypt files with this tool.
If this method is unsuccessful, you could always resort to specialized data recovery software.
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders which you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
Decryption tools for ransomware strains might be created eventually because of the work security researchers do. In a few instances, law authorities have taken over servers from malicious actors, which allowed the keys to be released – this is often done by reputable security vendors. The following links may help you:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
