Netlock ransomware (virus) - Free Instructions
Netlock virus Removal Guide
What is Netlock ransomware?
Netlock ransomware is a money-extortion-based malware that shouldn't be underestimated
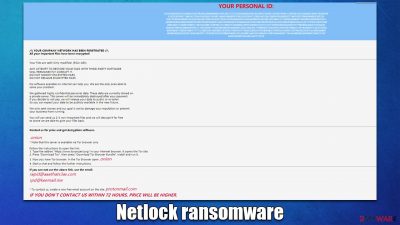
Netlock is a Windows computer virus that operates by locking all files located on local and networked drives. Most commonly, users get infected with ransomware accidentally or when they open a spam email attachment or download an infected file that pretends to be a cracked program. Other distribution methods are also popular.
Netlock ransomware operates similarly to any other malware of this type: deletes Shadow Volume Copies,[1] disables Windows repair functions, and drops numerous malicious files on the system. This helps the malware to continue its operation at all times, making a recovery a particularly difficult task for users.
However, the main task of the virus is to ensure that all videos, pictures, documents, databases, and other files are thoroughly locked by a combination of sophisticated encryption algorithms AES and RSA.[2] The data would immediately become inaccessible to victims, and all the files would be appended with the .netlock extension. In the how_to_back_files.html ransom note, hackers would explain to users that they must pay a ransom to restore their files.
| Name | Netlock |
|---|---|
| Type | Ransomware, file-locking malware, cryptovirus |
| File extension | .netlock |
| Ransom note | how_to_back_files.html |
| Encryption | AES + RSA |
| Data Recovery | If no backups are available, recovering data is almost impossible. However, we suggest you try the alternative methods that could help you in some cases – we list them below |
| Malware removal | Manual virus removal is not recommended, as it might be difficult for regular users. Instead, SpyHunter 5Combo Cleaner or other anti-malware tools should be used |
| System fix | Malware can seriously impact a Windows computer's performance and stability after it is removed. We recommend scanning the system with FortectIntego to remedy it and avoid significant stability issues |
What are MedusaLocker variants?
Instead of harming the system, ransomware's primary objective is to affect user files so that they are unrecoverable. Through this method, hackers may then demand money from their victims. With hundreds of strains circulating online, ransomware has grown to be a very lucrative industry.
The Netlock virus stems from a relatively established family known as MedusaLocker, which has been active since at least 2019. We have previously discussed some variants of the strain, including Farlock, EMPg296LCK, and Revenlock. Instead of delivering a usual TXT file, malware versions usually employ a pop-up message which shows up as soon as the ransomware finishes the file encryption process.
In the note, cybercriminals typically explain what happened to users' files and then claim that they should not look for alternative solutions to recover their data. They offer a service of free decryption as proof that they indeed have a working decryption tool they are not going to give away for free.

As usual, we recommend staying away from any communications with the attackers, as there is never a guarantee that you will receive the decryptor after you pay the demanded sum of money. As a result, you risk losing your funds as well. Instead, follow the instructions below to remove Netlock ransomware from your system and rely on other methods for data recovery.
Remove malware from your device to prevent further data locking
You should unplug the computer(s) from the network to stop the attackers from exchanging ransomware communications over it. Through it, malware developers may distribute further payloads or upgrade ransomware with fresh code. While it is possible just to unplug the internet wire, this may not always be practical. Instead, you should do the following actions:
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet
- Click Network and Sharing Center
- On the left, pick Change adapter settings
![Network and internet 3 Network and internet 3]()
- Right-click on your connection (for example, Ethernet), and select Disable
![Network and internet 4 Network and internet 4]()
- Confirm with Yes.
Although it is feasible, manual virus removal is not advised; security software is the best choice. You can use SpyHunter 5Combo Cleaner or Malwarebytes to automatically detect and eliminate all harmful components from your system. Your primary line of defense against malware attacks should be security software, however, it's always preferable to attempt to prevent infection in the first place.
If malware is interfering with its removal (which might be very possible, as it prevents users from using Windows recovery tools), we recommend accessing Safe Mode, which would terminate the operation of the virus.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
![Windows XP/7 Windows XP/7]()
Windows 10 / Windows 8
- Right-click on the Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find the Advanced Startup section.
- Click Restart now.
![Recovery Recovery]()
- Select Troubleshoot.
- Go to Advanced options.
- Select Startup Settings.
![Startup settings Startup settings]()
- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.
![Press F5 to enable Safe Mode with Networking Press F5 to enable Safe Mode with Networking]()
Fix damaged system files
When a computer becomes infected with malware, the way its operating system functions is altered. For instance, an infection may remove crucial DLL[3] files or harm essential bootup and other registry database parts. Users may face speed or stability issues, as well as usability concerns, as soon as system components are infected by malware. Antivirus software cannot remedy these issues, and users may need to completely reinstall Windows.
In order to discover any damaged components and fix them all at once, we advise conducting a scan using strong PC repair software. The program may also assist with a number of technical difficulties unrelated to malware attacks and clear the computer of junk and third-party trackers.
- Download FortectIntego
- Click on the ReimageRepair.exe
![Reimage download Reimage download]()
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
![Reimage installation Reimage installation]()
- The analysis of your machine will begin immediately
![Reimage scan Reimage scan]()
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
![Reimage results Reimage results]()
How to recover .netlock files?
Files that have been encrypted cannot be read without a key, which is frequently kept on a server that hackers run. They can then determine which key decrypts which victim's data using the user ID. Since each victim is given a unique key, there is no universal password in this scenario.
Both data encryption and virus infection are independent occurrences that should be treated separately. This means that by using antivirus software to check your computer, you will be able to delete any harmful files that would otherwise be operating on your system and, for example, encrypt any incoming documents. Files would stay locked, and this would not be able to restore them. This is among the most hazardous characteristics of ransomware.
Although it is likely that hackers have the password to decrypt data encrypted by the Netlock ransomware, paying the ransom is never worth the risk since you might lose both your money and your contents. As a result, even if taking the other path might not always be effective, we advise doing so.
Once the virus has been removed from your device, you can recover your data if you have data backups. To avoid irreparable data corruption, you should first make copies of encrypted files if you don't have them before moving on to the next step. After that, you may begin using data recovery software as follows:
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![Netlock ransomware Netlock ransomware]()
- Follow on-screen instructions to install the software.
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
![Select what to recover Select what to recover]()
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
![Scan Scan]()
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
Waiting for a functional decryption tool, which may or may not be created by security experts, is another option for file restoration. Malware researchers successfully developed a large number of decryptors that allow users to retrieve ransomware-encrypted data without paying a fee. The key here is patience because it can be weeks, months, or even years before this happens. We advise visiting the following links while seeking a decryptor tool:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Shadow Copy. Wikipedia. The free encyclopedia.
- ^ Ron Franklin. AES vs. RSA Encryption: What Are the Differences?. Precisely. Data integrity company.
- ^ Tim Fisher. What Is a DLL File?. Lifewire. Tech News, Reviews, Help & How-Tos.














