Nobu ransomware (Virus Removal Instructions) - Free Guide
Nobu virus Removal Guide
What is Nobu ransomware?
Nobu ransomware – malicious program developed for money extortion
Nobu ransomware is a virus that encrypts[1] all non-system files on a computer that it gets access to and then demands a ransom in cryptocurrency for a decryption tool. This virus derives from a constantly increasing family of Djvu ransomware, which consists of over 260 versions – it is one of the most prominent strains that targets regular computer consumers.
The Nobu virus is almost exclusively spread via software cracks, pirated program installers, and similar files typically placed on torrent or similar sites, so users download the payload themselves. Once instilled on the computer, the malware first alters Windows settings, inserts new modules, and only then proceeds with data encryption.
During this process, ransomware uses RSA[2] encryption algorithm and appends each file with .nobu extension. Suchlike modified data becomes inaccessible until a necessary decryption tool is used. Unfortunately, the decryptor is only accessible to the attackers, and they are not willing to give it away for free.
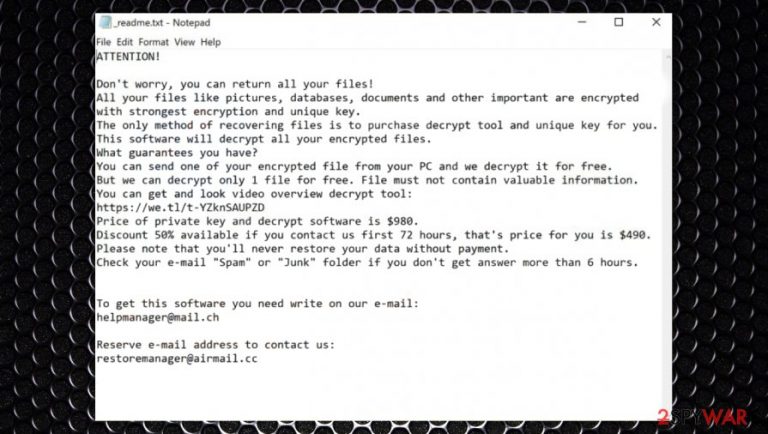
When the data is locked and renamed, just like its previous versions like Lisp, Weui, Iiss, and all others, .nobu file virus creates and places text file ransom notes, titled _readme.txt, which claims that victims need to contact the malicious actors via helpmanager@mail.ch or restoremanager@airmail.cc email and pay the ransom of $980/$490 for the decryptor.
| name | Nobu ransomware, .nobu files virus |
|---|---|
| Type | Ransomware |
| Family | Djvu ransomware family |
| File marker | .nobu extension that appears at the end of every encoded file |
| Ransom note | _readme.txt |
| Ransom amount | Cybercriminals are asking for $490 to be paid within 72 hours. If the victims fail to do that, then the price will be $980. |
| Criminal contact details | Two emails are given to make contact – helpmanager@mail.ch, restoremanager@airmail.cc |
| File Decryption | There is a small chance of file decryption with the help of Emsisoft's decryptor. Otherwise, without backups, chances of a successful recovery are slim, but never zero, so check the alternative methods below |
| MALWARE REMOVAL | Any malware infection should be removed with the help of a trustworthy anti-malware software. If required, you could access Safe Mode as explained below |
| System fix | System repair tool like the FortectIntego software should be used right after malware elimination to fix the system registry and other core settings |
The ransom note of Nobu ransomware is long and quite informative, although it doesn't really differ from all other ransom notes of related cryptoviruses. First of all, the cybercriminals explain to the victims that all their files were encrypted and that the only way to regain access to their data is to purchase a decryption tool, aka pay the ransom.
To convince their victims, the attackers suggest sending them one file for free decryption – this suggestion should prove that the ransomware decryptor exists and works as intended. If the free decryption guarantee doesn't persuade the victim to pay the ransom, the criminals add a link to a video where the promised decryption tool can be seen in action.
In other words, the hackers are bending over backward to convince the victims that they will hold their end of the bargain. They promise discounts and claims to have the one and only one existing Nobu ransomware decryption tool. While they might be right about the tool being accessible only to them, there are other options that just might work for you.
The benevolence of the Nobu virus makers doesn't end there. They offer a 50% discount for the ransom amount if their victims act quickly and contact them within 72 hours of the cyberattacks. Then the price would be $490. If the users are not hasty, they would have to lighten their wallets by $980.
At the end of the ransom note, two emails are given to reach out to the cybercriminals – helpmanager@mail.ch and restoremanager@airmail.cc. Also, an appointed personal victim ID is specified, which should be sent went contacting the perpetrators.
As always, we advise against paying the ransom, and suggest that our readers should focus on Nobu ransomware removal instead. Meeting the demands of the criminal's victims just motivates them to increase the number of attacks and finance them to research new, more effective ways to distribute their created ransomware.
Although manual removal is possible, we advise leaving this work to professionals. Remove Nobu virus with a push of a button with any of these two powerful security apps – SpyHunter 5Combo Cleaner or Malwarebytes. If kept updated regularly, they can serve as excellent tools that could prevent future malware attacks.
It is important to note that malware sample was detected under the following names, according to Virus Total:[3]
- Trojan.MalPack
- Hacktool.Win32.Shellcode.3!c
- Win32:DropperX-gen [Drp]
- Trojan/Win32.Glupteba.R357174
- Trojan.TR/AD.InstaBot.gzfzd
- Gen:Variant.Ransom.Stop.18 (B).
This once again highlights the importance of a robust security application – it can use behavioral analysis to detect danger within certain files with high accuracy. Unfortunately, many users choose to ignore these warnings and end up infecting their computers with the .nobu virus.
Once you've deleted the Nobu file virus from an infected device, it's time to take care of overall system health. Since malware usually modifies system files and settings to help it thrive within the targeted computer, experts[4] recommend using the FortectIntego system tune-up tool to revert any changes that the virus might have caused.
The message that the ransomware virus makers send to their victims after successful encryption:
Don't worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-Dz5odBd07y
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don't get answer more than 6 hours.To get this software you need write on our e-mail:
helpmanager@mail.chReserve e-mail address to contact us:
restoremanager@airmail.ccYour personal ID:
Difference between decryptable and non-decryptable .nobu file virus versions
Previously, this Djvu ransomware family was easily decryptable and many victims got their files recovered after attacks and encryption rounds. However, since August 2019 the ransomware creators got their coding techniques updated and managed to rely on more persistent methods, different victim ID formation techniques. Since .nobu is the extension that came out recently, decryption is barely possible.

Let's explain why and what is the difference. Offline IDs and encryption keys that were previously used by attackers, so researchers managed to obtain one decryption key and recover all the files locked using the same encryption method and the appendix. That worked for a while, but STOPDecrypter is no longer in use for these newest variants like the Nobu virus.
Right now, since the summer of 2019, Djvu creators managed to rely on the RSA algorithm and online ID forming. During such an encryption process the unique ID and decryption key gets chosen. Unfortunately, to recover files affected by the Nobu ransomware, you or the researcher need to get that key and use a tool accordingly.
Even the existing Emsisofts' decrypter works for offline IDs only and only a handful of versions can be decrypted. It shows that the best .nobu file recovery option could be copies of those files stored in backups. You can possibly wait for the new decryption tool or the hacker database leak. That takes time, so our research shows that data backup creation needs more attention.
Possible recovery methods for .Nobu virus affected data
Usually, Djvu family ransomware gets on everyday computer users' devices when they're visiting and downloading something from torrent websites, such as The Pirate Bay, BitTorrent, 1337x, and others. So for your own safety, please don't use these types of file-sharing platforms no matter what to avoid infections like the Nobu virus.
There aren't many choices for data recovery methods after the ransomware attack. If you had backups, then great news! Remove the infection, perform a system tune-up, and restore your data. If you aren't that lucky, then you might want to try our suggestions at the bottom of this article.
Whatever the case might be, be sure to check back with us in the near future as we always update our readers with the latest news on spyware, tech, ransomware, decryption tools, and so much more. We keep various updates on decryption tools and other issues regarding the family of Djvu that the Nobu virus belongs to.
Remove Nobu ransomware from all infected devices with the help of anti-malware software
Having your computer encrypted by the Nobu virus is a total nightmare – especially for those who never encountered such a computer threat before. Virus termination isn't the same as data recovery, but let's take one step at a time.
Contrary to popular belief, you should not proceed with Nobu ransomware removal immediately if you have no backups available. Instead, you should first copy all the most important files onto a separate medium and only then delete the infection from the system. Best results are achieved when a trustworthy anti-malware app is used to do it, such as SpyHunter 5Combo Cleaner or Malwarebytes. In case malware is interfering with these tools, you could access Safe Mode with Networking and perform a full scan from there – we explain how below.

It is important to note that Djvu variants are known to compromise users' ability to access certain security-related websites, including 2-spyware. Therefore, if you never dealt with Windows “hosts” file before, you should access the following directory and delete it – Windows will recreate it automatically, and you will be able to navigate through the internet freely again:
- C:\Windows\System32\drivers\etc\
Before trying to decrypt or retrieving your files from the backups, users who suffered from the Nobu ransomware virus attack should run a full system scan with a powerful system tune-up tool like FortectIntego to check (and fix) for any system irregularities caused by the attack.
Getting rid of Nobu virus. Follow these steps
Manual removal using Safe Mode
Safe Mode with Networking might be able to delete the infection if regular mode fails
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Nobu using System Restore
Removing ransomware with the help of System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Nobu. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Nobu from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Nobu, you can use several methods to restore them:
Data Recovery Pro a tool that might restore files
This third party app might be able to restore locked files.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Nobu ransomware;
- Restore them.
Using Windows Previous Version feature for data recovery
Users might be able to recover .Nobu extension files one at a time when using Windows Previous Version feature.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Shadows Explorer is a powerful tool but he depends on Shadow Volume Copies
If these copies are still intact, meaning that the virus didn't encrypt or remove them, Shadow Explorer might restore lost data.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Possible decryption methods and tools
Emisoft is working their butts off to stop people from paying ransoms. They constantly update their decryption tools, but since Nobu ransomware is brand new, it's questionable that the decryptor would work. But you still can download it and try it out.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Nobu and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Encryption. Wikipedia. The free encyclopedia.
- ^ RSA Algorithm in Cryptography. Geeksforgeeks. A computer science portal for geels.
- ^ 5af0f5b0bada5b7aaa681eddebc47734267af06eb39610590a625315f449d4de. Virus Total. File and URL analysis.
- ^ Dieviren. Dieviren. Spyware and security news.







