Nypd ransomware (Virus Removal Guide) - Decryption Steps Included
Nypd virus Removal Guide
What is Nypd ransomware?
Nypd ransomware – malware that locks your files and blackmails you for decryption software
Nypd file virus is a malicious program that originates from a notorious STOP/Djvu ransomware family, which already released over 230 versions, most of which are distributed via pirated program installers or software cracks. Nonetheless, this version of the virus was spotted being proliferated via infected download links of the VST (Virtual Studio Technology) plugin.[1]
As soon as the Nypd ransomware payload is launched, it manifests itself by locking all personal files on the machine with the help of a sophisticated RSA encryption algorithm. During this process, MS Office documents, pictures, videos, databases and other files are appended with .nypd file extension, and user access is restricted from that point. To retrieve their files, users need to acquire a unique key that is stored on the attackers' remote servers.
Criminals behind this malware clarify the situation by presenting their victims with the _readme.txt ransom note, which can be found on the desktop, as well as other non-system Windows folders. Crooks demand their victims to pay the $490/$980 ransom payment within 72 hours, but first, they have to email them via gorentos@bitmessage.ch or gorentos@firemail.cc.
| Name | Nypd |
| Type | Ransomware or file-encrypting malware |
| Genealogy | It's a variant of the STOP/Djvu ransomware family |
| Distribution | According to users, this virus is actively distributed via infected software download links (e.g. VST plugin) on peer-to-peer networks and spam email attachments. However, it may also be pushed via unprotected RDPs, so admins should ensure a strong password protected service |
| File extension | The ransomware appends the .nypd extension to encrypted files |
| Ransom note | _readme.txt |
| Contact email address | gorentos@bitmessage.ch or gorentos@firemail.cc |
| Ransom | Djvu classic – $490 if the victim pays the ransom within 72 hours. Later, the price for the decryptor gets doubled – $980 |
| File decryption | Djvu versions launched after August 2019 can only be decrypted if an offline key is used. In this case, victims can rely on Emisoft's STOP decryptor. |
| Virus removal options | There's only one away to remove Nypd ransomware virus – restart Windows in Safe Mode and run a full scan with a robust antivirus program |
| Windows repair is needed upon ransomware attacks. For recovery of Windows registries, startup processes, and other system components, try using FortectIntego repair tool. | |
The Nypd ransomware is a clone of other Djvu variants launched recently (Zipe, Nlah, Zwer, Pezi, etc.). Upon infiltration, it restricts user's access to most of the personal files stored on the machine using the .nypd file virus marker. Up until August 2019, criminals behind Djvu ransomware have been using offline IDs for encoding people's data, so cybersecurity experts managed to crack the code down and represented the victims with a free decryption software known as STOPDecrypter.
However, since September last year, the Djvu ransomware has been improved and all the new strains generate online IDs that cannot be decrypted without paying the redemption. If you received an ID number, which has the t1 compound at the end of the key, it means that the virus is using offline keys[2] and you can use free decryption software upon complete Nypd ransomware removal.
If, however, the virus locked your files with .nypd file virus using an online key, there are not many options to recover your files. You can either pay the criminals or remove the ransomware and try alternative data recovery options, such as data backups or third-party software.
The new .nypd ransomware manifests its presence on the machine right upon infiltration. Victims can hardly feel the symptoms of PC's hack during the first infection phase because the virus functions in the background to take control of the system.
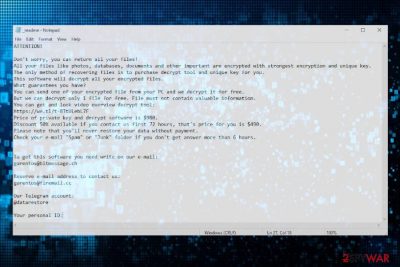
During the second phase, the system may be automatically rebooted. Upon that, all personal files are loaded with the novel .nupd file virus extension, which prevents the data from being opened or otherwise used. The whole information about an attack can be found in the _readme.txt file, which contains the following information:
ATTENTION!
Don't worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-dIIHZji8hl
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don't get answer more than 6 hours.To get this software you need write on our e-mail:
gorentos@bitmessage.chReserve e-mail address to contact us:
gorentos@firemail.cc
According to LosVirus.es[3], people should not pay the ransom for Djvu managers. These guys are not worth any financial support. The best option in this unpleasant situation is to remove Nypd ransomware virus using SpyHunter 5Combo Cleaner, Malwarebytes, or similar antivirus program and then apply data recovery tools, for instance, Data Recovery Pro.
.nypd file virus: decryption options are limited

In this case, NYPD is not an abbreviation of the New York Police Department, so don't get confused. If you see your files locked by .nypd extension, it's obvious that your machine is hacked by a ransomware virus. As we have pointed out above, this file-encoder is the latest variant of Djvu ransomware, so there are very few chances that you will be able to get your files back without paying for the criminals unless you have data backups.
The most recent versions of this data locker are known for using online IDs, thus leaving the victims helpless. However, since this latest variant hasn't yet been anatomized, you can check whether your ID is online or offline by yourself. For this purpose, navigate to the C: drive and look for the SystemID.txt or PersonalID.txt entry. Open the file and check whether any of the entries listed ends up with the t1. In case you found at least one entry ending with the t1 suffix, then try to download Emsisoft's decryption tool to recover .nypd files.
In case it turns out that the Nypd ransomware virus is using online IDs and no free decryptor is capable of breaking it down, then try taking advantage of alternative data recovery means:
- If you have data backups, then there's nothing to worry about. Remove Nypd virus from the system and recover the files using the backups.
- In addition, you can try to export locked files using Shadow Volume Copies or Windows Previous Versions feature.
- Upon ransomware removal, take advantage of third-party data recovery tools, such as Data Recovery Pro. Although they may not be capable of retrieving the whole package of .nypd files, you may get back at least a part of important documents.
Fake Nypd decryption tool can be used to lock your files a second time
At the beginning of June 2020, cybersecurity experts started sharing the warnings about a fake Djvu decryptor. Criminals are taking advantage of the Djvu victims who are looking for a solution to get their files back without paying the ransom to criminals.
Crooks started spreading a malicious piece of software on various channels, including some underground forums and some third-party download websites claiming that the decryption tool has been found capable to unlock .nypd virus files and other Djvu versions that are using online IDs.
IMPORTANT: do not fall for downloading free Nypd decryptor from shady sources because you can end up with another ransomware on your machine. It has been found that the fake decryption tool carries Zorab ransomware payload, which once launched double encrypts encrypted files. Consequently, Djvu file virus is replaced by .zorab extension appendixes and the victims get a new ransom note called –DECRYPT–ZORAB.txt.ZRB.
Although it's not yet clear whether it's possible to recover double encrypted files, experts presume that it may be much difficult to ever the changes.

Do not rely on shady download sites that promote pirated software
The members of this infamous ransomware group are extremely prevalent for several years already. The reason for that – sophisticated distribution techniques applied. In most of the cases, hackers inject virus payloads into the links for downloading pirated or untrustworthy third-party software (e.g. cracked Virtual Studio Technology plugins).
Alternatively, people can get infected with a file-encrypting virus on P2P and torrenting sites. Hackers can easily participate in file-sharing websites as registered users, who may offer software cracks for Adobe Acrobat, Photoshop, and others. Although bypassing license restrictions may be fun for users for as long as their personal files are not locked.
Another perfect medium for hackers to exploit is spam email messages. Since people cannot handle their curiosity, criminals keep inventing appealing spam campaigns, such as Covid-19 protection measures or Black Lives Matter anonymous voting. Thus, every time your inbox gets a new email message from an unknown sender and you are seduced to open the attachment, check for grammar mistakes, google the sender and think twice before opening it. If the email requires enabling Macros, it's an immediate sign that you may be on the verge of launching ransomware.
Get rid of Nypd ransomware and proceed with file recovery options
Nypd virus might not only cause permanent file loss but also trigger serious Windows system malfunctions. Even more, it may download a malicious trojan virus on the system as a secondary payload, thus exposing you to a high risk of identity theft and money losses.
There's only one option for Nypd ransomware removal, i.e. access Safe Mode with Networking and enabling the scanner of a robust antivirus program. There are multiple malicious processes that belong to this ransomware (e.g. dfile.su[4]), which cannot be quarantined manually in any way.
Once you successfully remove Nypd virus, launch a scan with FortectIntego repair tool to fix the damage that the virus initiated on Windows registries and other system components. Finally, when the malicious entries are gone and the system is fully functional again, try to recover the data that have been locked.
Getting rid of Nypd virus. Follow these steps
Manual removal using Safe Mode
If Nypd ransomware is interfering with your security software, enter Safe Mode with Networking to perform its termination without interruptions:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Nypd using System Restore
If you can't access Safe Mode for some reason, try to enable System Restore to get rid of the infection:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Nypd. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Nypd from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Nypd, you can use several methods to restore them:
Data Recovery Pro might be a useful tool when trying to recover ransomware-locked data
Data Recovery Pro might be capable of helping you restoring at least some portion of .nypd files.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Nypd ransomware;
- Restore them.
Windows Previous Versions method
This feature allows you to restore a file to its previous state if you had System Restore enabled. However, you can only retrieve one file at the time, so the recovery of a large amount of data might not be possible.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer may help if the virus fails to launch command to remove Shadow Volume Copies
If Nypd file virus failed to delete Shadow Volume Copies, ShadowExplorer should be able to recover all your files.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Make use of STOPDecrypter
Download and employ STOPDecrypter software it might be able to retrieve your data in some cases.
If you checked the ID model and it turns out to be offline, give Emsisoft's Djvu Decryptor a try.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Nypd and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Developing Story: COVID-19 Used in Malicious Campaigns. Trend Micro. Enterprise data security and cybersecurity solutions.
- ^ mado virus (STOP Djvu) Please help. Emsisoft. The official customer support forum.
- ^ NOTICIAS SOBRE SEGURIDAD Y VIRUS. LosVirus. Virus and spyware news.
- ^ dfile.su. VirusTotal. Free URL and file scanner.





















