OnyxLocker ransomware (Virus Removal Instructions) - Quick Decryption Solution
OnyxLocker virus Removal Guide
What is OnyxLocker ransomware?
OnyxLocker ransomware is a file locker that encrypts data with XXTEA cipher, and targets mainly Russian users
OnyxLocker is malware that belongs to the ransomware group – it focuses on file encryption. This consequently prevents victims from opening pictures, music, videos, documents, and other personal data located on the local drive or any connected devices. The goal of ransomware authors is to blackmail users into paying ransom demands – they are asking for $100 in Bitcoin.
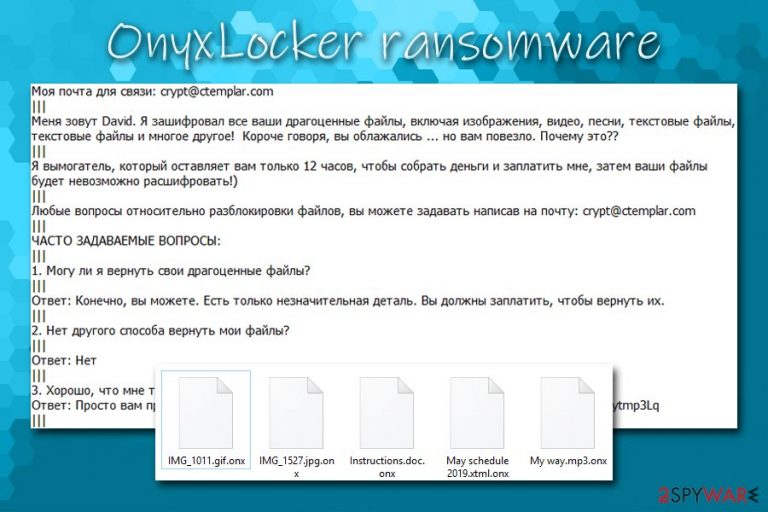
In order to be able to extort money, the OnyxLocker virus is programmed to search for the most relevant file types on the machine and encrypted them by using XXTEA block cipher.[1] Each file modified by ransomware acquires a .onx marker at the end, and victims can no longer access the data. Instead of dropping a predetermined text file, this ransomware opts to inserting 10 ransom notes on the system (Прочти меня! 0 .txt, Прочти меня! 1 .txt, Прочти меня! 2 .txt, etc.).
The note is written in Russian, which immediately brings to the conclusion that OnyxLocker ransomware authors are aiming to infect Russian users. Nevertheless, it does not mean that the infection can not occur anywhere else in the world, so users from other countries should keep an eve on spam email messages that hold attachments like goload_1008_1569853988.doc, as malspam[2] is the most likely cause of OnyxLocker ransomware infection.
| Name | OnyxLocker |
|---|---|
| Type | Ransomware, Cryprovirus |
| Distribution methods | It is known that the infected opened a contaminated email attachment; nevertheless, the malware could be spread via other methods, such as software cracks, exploits, unprotected RDP connections, fake updates, web injects, fake installers, etc. |
| Symptoms | Files appended with a particular extension, and none of them can be opened; ransom note demanding payment in cryptocurrency dropped on the system; victims may have difficulties operating security software or navigating to certain websites |
| File extension | Each of the personal files located on local HDD or connected devices is appended with .onx extension |
| Cipher used | XXTEA |
| Ransom note | OnyxLocker drops 10 ransom notes Прочти меня! 0 .txt, Прочти меня! 1 .txt, Прочти меня! 2 .txt, etc., all of which have identical content |
| Contact | Contact email crypt@ctemplar.com is provided inside the ransom note |
| AV detections |
|
| Related files | OnyxLocker.exe, goload_1008_1569853988.doc |
| Malware termination | To successfully delete ransomware from your machine, you should employ reputable anti-malware software. We also recommend employing a good system optimization tool like FortectIntego since it may find and fix those altered directories and registry entries |
| File recovery | OnyxLocker does not encrypt all files on the system, so it is worth checking which ones were not affected by the malware. The locked data, however, can only be deciphered successfully after acquiring a unique key from criminals. However, there is a chance that third-party recovery software might be useful or security researchers will create a decryption tool sometime in the future |
OnyxLocker is a new ransomware strain, and it was first spotted by security specialist Alex Svirid on October 7, 2019. It does not seem like it is connected to any other ransomware families, so it might be that crooks behind this malware are new to the cybercriminal world. This also implies that there is a chance that OnyxLocker ransomware has some bugs[3] that might be exploited by security experts to create a free decryptor.
Talking about bugs, OnyxLocker ransomware does not encrypt all files located on the host system. Therefore, those lucky ones might still find some of the data usable, even after the infection occurs. Unfortunately, other files that do get encrypted, are impossible to return without a unique key that is held on a remote Command & Control server – it is, unfortunately, only accessible to the attackers behind OnyxLocker ransomware.
Infection and file encryption of OnyxLocker
Once the infection vector is triggered, OnyxLocker ransomware creates a new folder inside the %TEMP% directory and places OnyxLocker.exe or a randomly-generated name for the dropper – an executable that starts the infection process. This file is then automatically opened, and multiple changes are performed to the Windows OS. Some of them include:
- Shadow Volume Copies deleted with “vssadmin Delete Shadows / all / quiet” command;
- Multiple malicious files dropped on in various places on the OS;
- Various processes (such as WMI Provider Host[4] – this could complicate OnyxLocker ransomware removal) terminated and new ones created;
- Shell commands executed;
- Windows registry keys deleted, created and modified, etc.
After the required preparation, the OnyxLocker virus starts to process personal files with the encryption cipher. As a result, the victim would see a particular file with .onx extension, and no regular icon visible. For example, a picture.jpg would be turned into picture.jpg.onx, and would no longer be accessible.

In each of the affected file folders, users can see ten identical ransom notes which all claims the same:
Моя почта для связи: crypt@ctemplar.com
|||
Меня зовут David. Я зашифровал все ваши драгоценные файлы, включая изображения, видео, песни, текстовые файлы, текстовые файлы и многое другое! Короче говоря, вы облажались … но вам повезло. Почему это??
|||
Я вымогатель, который оставляет вам только 12 часов, чтобы собрать деньги и заплатить мне, затем ваши файлы будет невозможно расшифровать!)
|||
Любые вопросы относительно разблокировки файлов, вы можете задавать написав на почту: crypt@ctemplar.com
|||
ЧАСТО ЗАДАВАЕМЫЕ ВОПРОСЫ:
|||
1. Могу ли я вернуть свои драгоценные файлы?
|||
Ответ: Конечно, вы можете. Есть только незначительная деталь. Вы должны заплатить, чтобы вернуть их.
|||
2. Нет другого способа вернуть мои файлы?
|||
Ответ: Нет
|||
3. Хорошо, что мне тогда делать?
Ответ: Просто вам придется заплатить 100 $ на этот биткойн-адрес: 3LV85h9s2y5c5DLi3YiACDKaR3tytmp3Lq
|||
4. Что за хрень биткойн?
|||
Ответ: Биткойн – это криптовалюта и цифровая платежная система. Вы можете увидеть больше информации здесь: hxxps://en.wikipedia.org/wiki/Bitcoin.
|||
5. Здесь вы можете оплатить, выбрав самый выгодный курс.
|||
Вставьте эту ссылку в адресную строку вашего браузера: hxxps://www.bestchange.ru/visa-mastercard-rur-to-bitcoin.html
In the note, OnyxLocker ransomware authors claim that users need to pay $100 ransom within 12 hour period, or otherwise, they will delete the key, which can regain access to the locked data. However, malware developers can not be trusted, as they can say whatever they want to make victims pay the ransom.
While ransom is not high, you should think twice before paying: crooks might not even have a working OnyxLocker decryptor – you may end up losing your money as well. Besides, it would only prove to criminals that their efforts to infect people are not in vain and some are willing to pay, which would only fuel their will to infect more victims.
Instead, remove OnyxLocker ransomware with anti-malware software and fully clean the machine with optimizing and system repair tools like FortectIntego. You need to get an anti-malware program or another reputable security tool for the initial termination, and then use alternative solutions for file decryption if you did not have backups prepared.
Spam emails – primary infection vector for multiple malware strains
Email spam, or so-called malspam, is an old trick that has been used by cybercriminals for decades now. Most computer users have a dedicated or work email, so spreading computer infections via the service makes sense. Crooks compile email lists and use bots to send out these malicious messages to as many people as possible. Nevertheless, in some cases, such a process can also be performed manually if targeted attacks are what cybercriminals are doing.
The phishing email often contains some form of social engineering tricks – users are intimidated by allegedly unpaid taxes, credit card intrusion claims, etc. Additionally, malicious actors often use email addresses that resemble well-established companies, such as UPS, Amazon, etc. Note that email spoofing[5] is another technique that may confuse many and make them believe that the message is legitimate.
Thus, never open .doc, .html, .txt, .pdf or other attachments inside these emails. A definite no-no is allowing macros to be run on these documents – that is what usually starts the infection process. To be safe, scan such documents with tools like Virus Total if in doubt.
Additionally, you should always protect your machine with anti-malware software, patch Windows with the latest security updates, never download software cracks/keygens, use ad-blocker, avoid high-risk sites, and always backup your important data on drives that are not connected to your PC.
Get rid of OnyxLocker before you proceed with data recovery process
Most of the ransomware viruses delete themselves after the encryption process is finished, although some may keep the file encryption module running. Therefore, it is vital to make sure that all of the malware's elements are deleted, and a full OnyxLocker ransomware removal is performed.
To remove OnyxLocker ransomware successfully, you may have to enter Safe Mode with Networking, as some malware is known to be tampering with security software in order to prevent its termination. If that is the case, we provide detailed instructions on how to access the mode below. Once eliminated, you should try alternative file recovery methods for the OnyxLocker virus – you can find them in the recovery section below.
There are some users that might want not to risk it and pay the criminals to recover .onx locked files. While it is one of the options available to you, it is also highly discouraged by the infosec community and security advisers.[6] As we already mentioned, you may not only lose your files but also money. However, if none of the decryption methods helped you, you might try this as your last resort (perform it at your own risk!).
Getting rid of OnyxLocker virus. Follow these steps
Manual removal using Safe Mode
If OnyxLocker is preventing your security software from operating properly, access Safe Mode with Networking as explained here:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove OnyxLocker using System Restore
You can also terminate the virus with the help of System Restore:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of OnyxLocker. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove OnyxLocker from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by OnyxLocker, you can use several methods to restore them:
Data Recovery Pro is one of the methods that may help you with .onx file recovery
Although chances are low, Data Recovery Pro may be able to retrieve copies of healthy files located on your drive.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by OnyxLocker ransomware;
- Restore them.
Restore individual files with Windows Previous Versions feature
This option is available for those who were careful and used System Restore feature before malware managed to get in.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer might be the answer to your problem
As mentioned above, ransomware is programmed to delete all Shadow Copies. Nevertheless, researchers observed some instances where malware failed to do so. In such a case, ShadowExplorer is your best bet when it comes to OnyxLocker file recovery.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
No decryption tool is currently available
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from OnyxLocker and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ XXTEA. Wikipedia. The free encyclopedia.
- ^ Juraj Jánošík. Russia hit by new wave of ransomware spam. WeLiveSecurity. ESET research blog.
- ^ Software Bug. Techopedia. Where IT and Business Meet.
- ^ Chris Hoffman. What Is the WMI Provider Host (WmiPrvSE.exe), and Why Is It Using So Much CPU?. How-To Geek. Site that explains technology.
- ^ Paul Gil. Email Spoofing: What It Is and How To Protect Yourself From It. Lifewire. Tech Untangled.
- ^ NoVirus. NoVirus. Cybersecurity advice from the UK.







