Oxar ransomware / virus (Removal Instructions) - updated Apr 2018
Oxar virus Removal Guide
What is Oxar ransomware virus?
Oxar is an ordinary ransomware that uses AES cipher and demands a ransom in Bitcoins
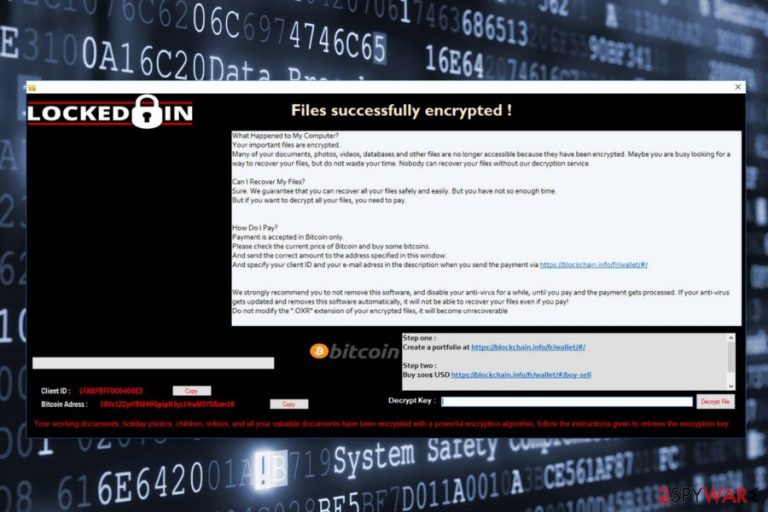
Oxar is a ransomware virus[1] that targets English-speaking users and seeks to lock their files to foist paid decryptor. It relies on AES-256 cryptography to encrypt files and generates a ransom note, which urges the victim to pay $100 in Bitcoins for a decryption software within 72 hours. The initial Oxar ransomware version appends .OXR file extension, but people can meet its modified versions that use .PEDO, .ULOZ, .FDP, and other extensions. The latest Oxar ransomware version has been found at the beginning of April 2018. It appends .FUCK file extension and is, therefore, dubbed as .Fuck file extension virus. It's built on a free HiddenTear ransomware source code, meaning that it can be decrypted.
| Name | Oxar |
|---|---|
| Type | Ransomware |
| Versions | .ULOZ, .PEDO, .FDP, Kappa, Fake Oxar, .FUCK |
| Danger level | High. Locks files, roots deeply into OS |
| Related files | Data Locker.exe, File Decryptor.exe, Cryptear.exe, Kappa Ransomware.exe, ransomware.exe |
| Decryptable | No |
| OS targeted | Windows |
| Ransom note | 1 What Happens with my files.txt |
| Download FortectIntego and run a scan to eliminate ransomware. Manual Oxar removal is not possible. | |
Following data encryption, crypto-malware triggers a pop-up window where it provides data recovery instructions. It seems that cyber criminals want to make users believe that they are dealing with the Locked-In ransomware virus. However, we can assure you that these viruses are entirely different.
Oxar malware is executed on the computer from Data Locker.exe or File Decryptor.exe file which spreads via infected email messages, bogus software, fake updates, etc. On the affected device, malware makes important changes in order to run with Windows startup. It might install malicious files and infect system process.
What is more, Oxar gives each of the victims a unique ID number that is provided in the ransom note. Once the preparatory work is over and malware strengthens its presence, it starts scanning the system looking for targeted files. Just like plenty other ransomware, this one also aims at 72 file extensions:
- Microsoft Office;
- OpenOffice;
- pictures;
- audio;
- video;
- documents;
- text files;
- databases;
- archives;
- etc.
Following data encryption process, Oxar ransomware delivers a ransom note in the program window. The latest Oxar version is known for injecting a text file What happens with my files.txt. The message informs about encrypted data and assures that victims can only recover the files using particular decryption software.
According to the ransom note, victims have “not so enough time” to get Bitcoins and transfer them to the provided address. People are asked to pay $100 in order to use decryption software. However, doing that is not recommended. No one can guarantee that criminals are willing to keep their promise and have working decryptor.
Crooks want to stop victims from scanning the system with antivirus. Undoubtedly, security software such as FortectIntego, SpyHunter 5Combo Cleaner, Malwarebytes can easily remove Oxar from the device. Unfortunately, malware removal tools are not designed to recover encrypted data. Thus, in this case, crooks do not lie. It’s nearly impossible to restore data without specific decryptor.
Currently, the only effective way to recover your files is to use backups.[2] If you do not have them, please check our suggested alternative recovery options. Keep in mind that you need that you need to complete Oxar removal first. Only then you can safely look up for the best recovery solution.
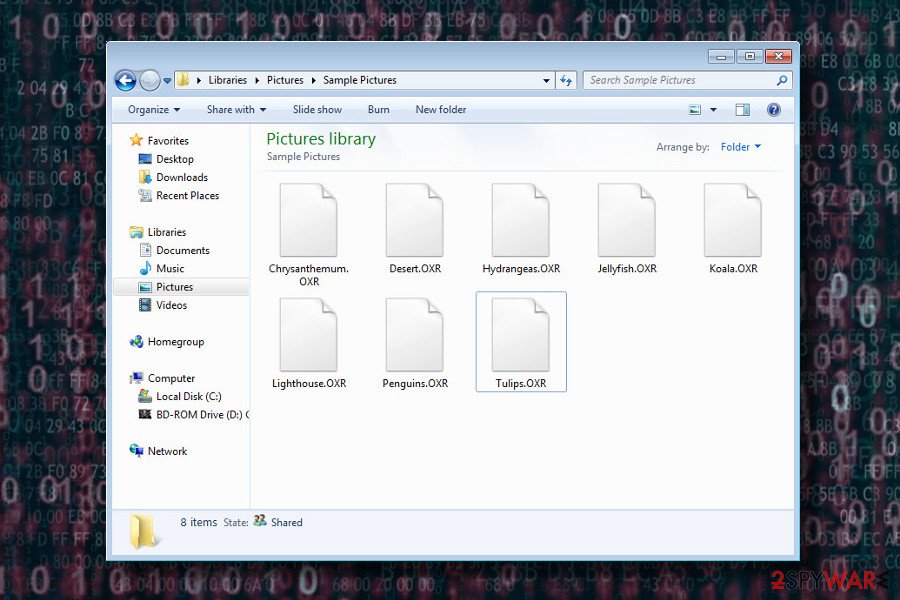
Variants and imposters of Oxar ransomware
.ULOZ file extension virus. This variant of Oxar acts similarly to its predecessor: it uses AES encryption algorithm and demands to pay the ransom in the pop-up window. The only significant difference is an appended file extension. It adds .ULOZ suffix to the targeted data.
.PEDO file extension virus. Though the former impersonates Ableton Live Suite software as it functions via Ableton-live-Suite-v95-WiN-x86-x64.exe, the latter contains more intriguing features. .PEDO file extension malware transmits certain details of a victim's PC system to a remote File Transfer Protocol (FTP) server.
It also shares a similar feature as the former version of Cerber: it drops an audio message to the affected users. Guidelines how to recover the files are delivered in Instructions.txt and 1 What Happens with my files.txt. If you tend to check system processes in the Task Manager, you may cease further activity of the ransomware by shutting the task under Cryptear.exe file.
.FDP file extension virus. On August 8th, cyber security researchers spot a new virus' version that uses .FDP file extension for the encrypted records. The name of the ransom note wasn't changed in this Oxar variant – it still remains 1 What happens with my files.txt.
So far, malware analysts could not find a way to decrypt any version of encrypted files. At the moment, the virus remains undecryptable (using third-party tools). If you are wondering whether it is worth paying the ransom, we can answer this question for you – it is not.
Kappa ransomware virus. On August 21, researchers discovered a new test version of Oxar that runs on the computers from Kappa Ransomware.exe. Just like the original version, it also appends .OXR file extension to the targeted data. The malware works on the computer only if user’s operating system is installed on Drive C. Therefore, if your OS is installed on drive D, you should not worry about this ransomware attack.
Once all the files are encrypted, ransomware opens a black ransom-demanding window that answers three major questions. Developers explain about data encryption and claim that the only way to decrypt files is to pay the ransom in Bitcoins.
Users are supposed to send their Client ID number as soon as the payment is made. Crooks claim to send the decryption key in return. However, you should never pay the ransom for cyber criminals because it most of the time ends up with money loss.
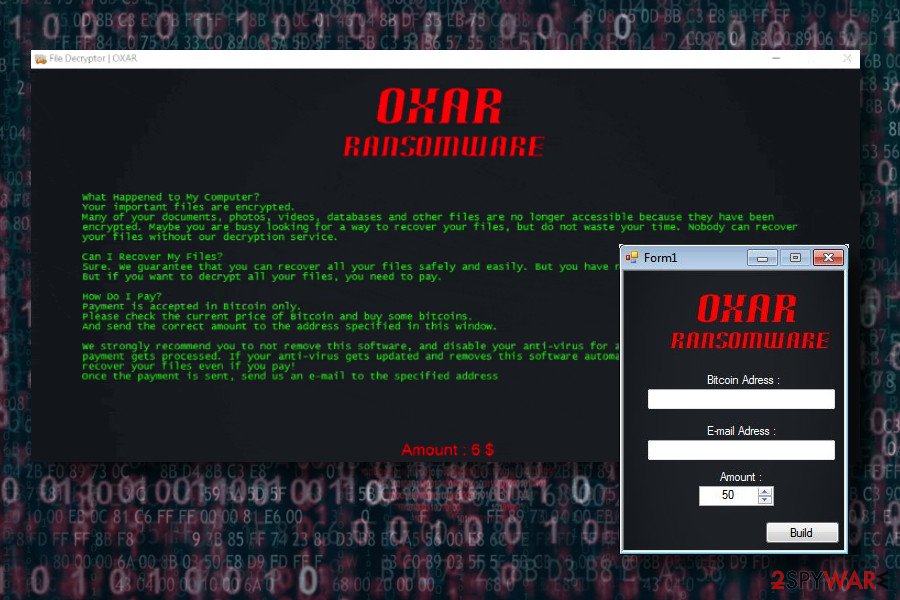
Fake Oxar ransomware virus. On August 21, malware analysts have noticed a fake version of the Oxar ransomware. It spreads as ransomware.exe and appends .OXR file extension. However, the research has shown that these two viruses have nothing in common. The recent discovery is just an imposter.
Following data encryption, it installs instructions.exe file and delivers “File Decryptor | OXAR” window that includes an identical information from the original Oxar’s ransom note. However, this piece of malware demands to pay $20 and after the payment send an email to maitregauillaume@protonmail.com.
Nevertheless, the ransom is small; you should not waste your money and motivate some hacker-wannabes. You’d better remove the virus with reputable antivirus.
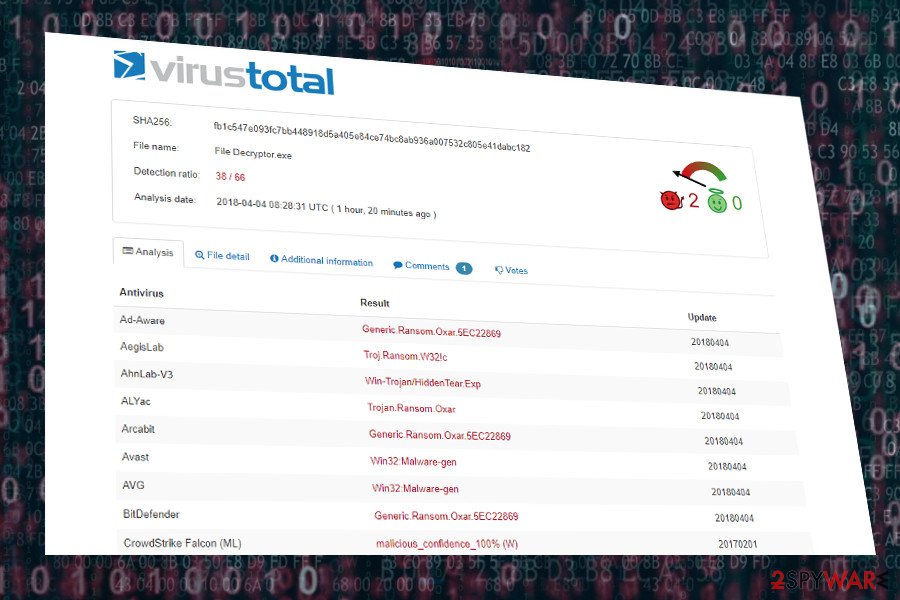
.FUCK file extension virus. At the beginning of April 2018, ransomware researchers spotted a new Oxar version in the wild. Dubbed as .FUCK file extension virus, the ransomware differs from the rest of other versions as it's based on HiddenTear source code.[3]
The payload is downloaded once the potential victim runs a File Decryptor.exe file. Upon successful infiltration, it targets the most popular file types and locks them with .Fuck file extension. Besides, it generates a ransom note What happens with my files.txt, which contains the following information:
What Happened to My Computer?
Your important files are encrypted.Many of your documents, photos, videos, databases and other files are no longer accessible because they have been encrypted. Maybe you are busy looking for a way to recover your files, but do not waste your time. Nobody can recover your files without our decryption service.
Can I Recover My Files?
Sure. We guarantee that you can recover all your files safely and easily. But you have not so enough time. But if you want to decrypt all your files, you need to pay.
How Do I Pay?
Payment is accepted in Bitcoin only. Please check the current price of Bitcoin and buy some bitcoins. And send the correct amount to the address specified in this window.
We strongly recommend you to not remove this software, and disable your anti-virus for a while, until you pay and the payment gets processed. If your anti-virus gets updated and removes this software automatically, it will not be able to recover your files even if you pay!
Once the payment is sent, send us an e-mail to the specified address specifying your “Client ID”, you will be sent your decryption key in return.
How to buy Bitcoins?
Step 1 : Create a portfolio on the Blockchain website at the address : https://blockchain.info/fr/wallet/#/signup
Step 2 : Sign in to your account you just created and purchase the amount shown : https://blockchain.info/wallet/#/buy-sell
Step 3 : Send the amount to the indicated Bitcoin address, once this is done send us an email with your “Client ID” you can retreive this in the file “instruction.txt” or “Whats Appens With My File.s.txt” in order to ask us the key of decryption of your data.Contact us at : spaghetih@protonmail.com
Send 20$ to Bitcoin at 1MFA4PEuDoe2UCKgabrwm8P4KztASKtiuv if you want decrypt your files !
Your Client ID is : [id]
The .fuck ransomware asks the victim to send 20 USD in Bitcoins. Before that, he or she is asked to email the crooks and provide a “Client ID.” Even though the ransom is funny if compared to, for instance, Vurten ransomware which demands to pay 10, 000 USD, we do not recommend paying it anyway.
According to the experts, this Oxar ransomware .Fuck version is decryptable. You can find a decryptor in NoMoreRandom.
DIstribution and infiltration methods of the ransomware virus
Malware mostly aims at English-speaking computer users. Thus, British,[4] Australian and American users should read this part of the article carefully. In order to drop malicious executable on the system, developers apply several strategies:
- infected email attachments;
- malicious links;
- illegal downloads;
- fake updates;
- malware-laden ads;
- exploit kits.
One of the main distribution methods is misleading emails[5] that include malicious attachment, link or button. Such letters usually urge to open infected content due to some serious issue. Typically, crooks pretend to be from financial institutions, banks, and other reputable companies. Before opening such content, you need to inspect the email carefully.[6]
Furthermore, in order to avoid Oxar, you should also stay away from suspicious file-sharing sites, P2P networks and other online sources that offer to download free content. We also recommend staying away from gaming, gambling, and adult-themed sites and keeping away from suspicious ads.
Keeping software and operating system up-to-date also minimize the risk of encounter file-encrypting virus. This cyber threat might use security vulnerabilities in order to sneak into a device.[7]
Elimination of the Oxar ransomware
The correct way to remove Oxar virus from the system is to use reputable security software. Crypto-malware is a complicated infection that might affect various system processes, download dangerous files and cause other serious problems.
To avoid bigger damage, you need to scan the device with FortectIntego, Malwarebytes or another malware removal program. These tools can locate all malicious components and uninstall them gently from the PC.
If you cannot install or run your chosen security tool, please scroll down below. At the end of the article, you will find the detailed explanation how to run automatic Oxar removal.
Getting rid of Oxar virus. Follow these steps
Manual removal using Safe Mode
If you cannot run or install security software, you need to disable the virus first by rebooting the PC to Safe Mode with Networking. Then try again.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Oxar using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Oxar. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Oxar from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.Files having .OXR extension can only be recovered if you have backups. Some of the third-party software may help to restore some of the files. Thus, you should try it. It's better to get back some of your files than loose the money to cyber criminals.
If your files are encrypted by Oxar, you can use several methods to restore them:
Data Recovery Pro – automatic way to restore files
This professional tool has helped numerous people to recover lost, deleted, corrupted and encrypted files. Thus, you should try this tool as well.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Oxar ransomware;
- Restore them.
Travel back in computer's time using Windows Previous Versions feature
If System Restore has been enabled before ransomware attack, you should try this method and copy the most important individual files.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer might help to recover files encrypted by Oxar ransomware
This tool helps to recover files from Shadow Volume Copies. Thus, if malware hasn't corrupted or deleted them, we suggest using this tool as well.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Oxar Decryptor is not available yet.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Oxar and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Nate Lord . A history of ransomware attacks. Digital Guardian. Technology news.
- ^ Lincoln Spector. How to stop ransomware: Backup can protect you, but only if you do it right. PCWorld. News, tips and reviews from the experts on PCs, Windows, and more.
- ^ estroying The Encryption of Hidden Tear Ransomware. Utku Sen. Blog.
- ^ NoVirus. NoVirus. British site about cyber threats, protection and virus removal instructions.
- ^ Recognizing and Avoiding Email Scams. US-CERT. United States Computer Emergency Readiness Team.
- ^ Ian Paul. Three warning signs that email is malicious. PCWorld. News, tips and reviews from the experts on PCs, Windows and more.
- ^ Forrest Williams. Understanding Exploit Kits: How They Work and How to Stop Them. Barkly Endpoint Security Blog. The latest endpoint security news, tips, and actionable insights.







