Performdevelopedgreatlythefile.vip ads (Free Instructions)
Performdevelopedgreatlythefile.vip ads Removal Guide
What is Performdevelopedgreatlythefile.vip ads?
Performdevelopedgreatlythefile.vip is a malicious phishing website you should not trust
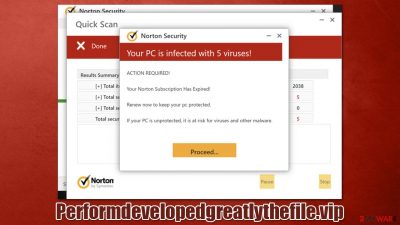
Performdevelopedgreatlythefile.vip is a fake website created by scammers. Users typically come across it while browsing highly dangerous websites (e.g., torrents or illegal video streaming ones), so their encounter with it is always accidental. Once there, people are quickly shown fake alerts and warnings, which might be a cause of concern for many, making them proceed with the request to download malicious software.
Performdevelopedgreatlythefile.vip displays a fake system scan process that looks like it's coming from a Norton security vendor. It then claims that the system is infected with viruses and that the antivirus subscription has expired, hence malware can't be removed unless it's renewed.
Please do not interact with this scam site, as you might install a fake version of Norton and infect your system that way. We recommend checking the device for adware or other malware, however, redirects to phishing[1] websites are a sign of an infection. We also explain how to mitigate the impact of being scammed online.
| Name | Performdevelopedgreatlythefile.vip |
|---|---|
| Type | Scam, adware, redirect |
| Distribution | Software bundles, malicious redirects, ads |
| Scam content | Claims that the subscription for security software has expired and that it needs to be renewed immediately. Asks to download malicious software and enable push notifications |
| removal | You should not interact with the content shown by a scam website. Instead, check your system for adware or malware infections with SpyHunter 5Combo Cleaner security software |
| Other tips | After the removal of PUPs and malware, we recommend scanning the system with FortectIntego to clean browser caches and fix virus damage automatically |
Scam message and other details
Performdevelopedgreatlythefile.vip uses a type of online fraud that plays on a very strong human emotion – fear, making it extremely effective. In recent times, we have noticed a huge rise in websites that distribute misleading messages seemingly coming from Norton or McAfee – reputable security vendors – some examples include Protectorofpower.xyz, Bluecodemc1.club, and Defender-scan.xyz.
Upon entry to one of these websites, users are shown what seems to be a scan by anti-malware software. Just after a few brief moments, the fake scan comes up with the following message:
Norton Security
Your PC is infected with 5 viruses!
ACTION REQUIRED!
Your Norton Subscription Has Expired!
Renew now to keep your pc protected.
If your PC is unprotected, it is at risk for viruses and other malware.
Performdevelopedgreatlythefile.vip can not perform a real system scan – it imitates it instead. A website can not detect malware installed on your system, as only a dedicated security application installed on the system can do it. The main goal of scammers is to earn pay-per-install revenue, which might be associated with malicious programs.
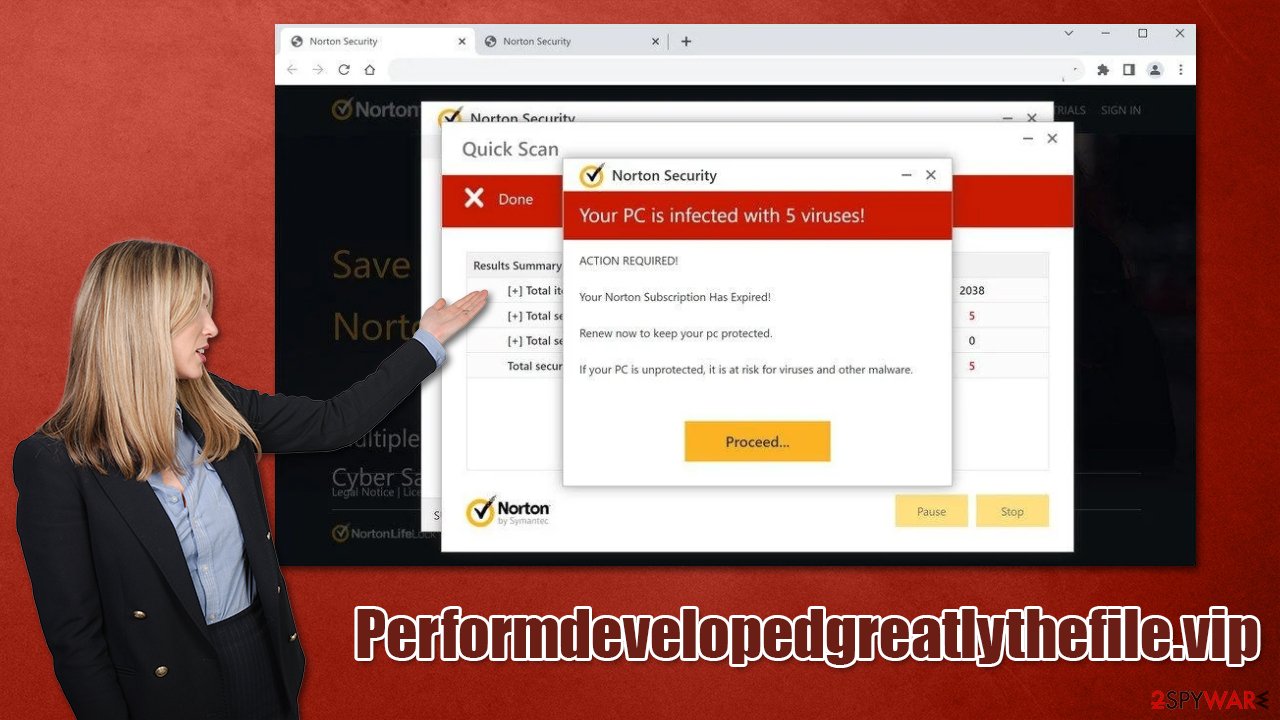
Therefore, never believe any claims online about your device being infected, as you are likely to install malicious software on your device if you listen. Instead, you should check the system for infection using legitimate tools.
Check your system thoroughly
Since users do not access phishing websites intentionally, there's always an element of surprise involved. Since they are caught off guard, they are more likely to make mistakes without thinking about their actions thoroughly. This is precisely why such scams work so well, and they are not going away anywhere, so you should always be wary.
That being said, redirects to Performdevelopedgreatlythefile.vip and similar websites can be caused by adware or other malicious software installed on the device. In order to check it easily, we recommend performing a full system scan with SpyHunter 5Combo Cleaner or Malwarebytes security software. If you would rather look for PUPs yourself, you can start by removing all unwanted extensions from your browser and then uninstalling apps from the system level as follows:
Windows
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
Mac
While moving apps into Trash is usually how you delete most normal applications, adware tends to create additional files for persistence. Thus, you should look for .plist and other files that could be related to the virus. If you are not sure, skip this step entirely.
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)
![Uninstall from Mac 1 Uninstall from Mac 1]()
To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
After you are sure that your system is fully cleaned from potentially unwanted programs and malware, you should also take your time to clean your browsers from trackers such as cookies. These items can stay on the system for years if not removed, continuing to track clicked links, visited websites, timestamps, search queries, and more, which are delivered to third parties.
To avoid privacy risks and increased possibility of session hijacking[2] attacks, you should delete these files on a regular basis – you can do that automatically with FortectIntego maintenance utility which can also fix any malware damage on your system.
Remove unwanted push notifications
Upon entering Performdevelopedgreatlythefile.vip website, you may also be asked to enable push notification via the prompt. If the “Allow” is pressed, the site would later send you intrusive pop-ups that would include malicious links. Do not interact with these links and instead block the website from sending you them:
Google Chrome
- Open the Google Chrome browser and go to Menu > Settings.
- Scroll down and click on Advanced.
- Locate the Privacy and security section and pick Site Settings > Notifications.
- Look at the Allow section and look for a suspicious URL.
- Click the three vertical dots next to it and pick Block. This should remove unwanted notifications from Google Chrome.
![Stop notifications on Chrome PC 2 Stop notifications on Chrome PC 2]()
Mozilla Firefox
- Open Mozilla Firefox and go to Menu > Options.
- Click on Privacy & Security section.
- Under Permissions, you should be able to see Notifications. Click the Settings button next to it.
- In the Settings – Notification Permissions window, click on the drop-down menu by the URL in question.
- Select Block and then click on Save Changes. This should remove unwanted notifications from Mozilla Firefox.
![Stop notifications on Mozilla Firefox 2 Stop notifications on Mozilla Firefox 2]()
Safari
- Click on Safari > Preferences…
- Go to the Websites tab and, under General, select Notifications.
- Select the web address in question, click the drop-down menu and select Deny.
![Stop notifications on Safari Stop notifications on Safari]()
MS Edge (Chromium)
- Open Microsoft Edge, and go to Settings.
- Select Site permissions.
- Go to Notifications on the right.
- Under Allow, you will find the unwanted entry.
- Click on More actions and select Block.
![Stop notifications on Edge Chromium Stop notifications on Edge Chromium]()
Avoidance tips
Security experts[3] provide several tips that should help you avoid being scammed online, as well as reduce the chance of installing potentially unwanted applications by accident:
- Always check the URL of the site that shows you various suspicious claims;
- Be aware that all the logos or messages can be fabricated very easily;
- Install a reliable ad-blocker that would stop the execution of malicious scripts;
- Use powerful anti-malware software to prevent malware infections;
- When possible, install apps from official sources instead of third parties;
- Always choose Advanced/Custom settings instead of Recommend ones to repel all the offers to install optional software.
How to prevent from getting adware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Phishing attacks. Imperva. Application and data security.
- ^ Allie Johnson. Session hijacking: What is a session hijacking and how does it work?. Norton. Security research blog.
- ^ Novirus. Novirus. Cybersecurity news and malware insights.







