Pony virus (Removal Guide) - Aug 2018 update
Pony virus Removal Guide
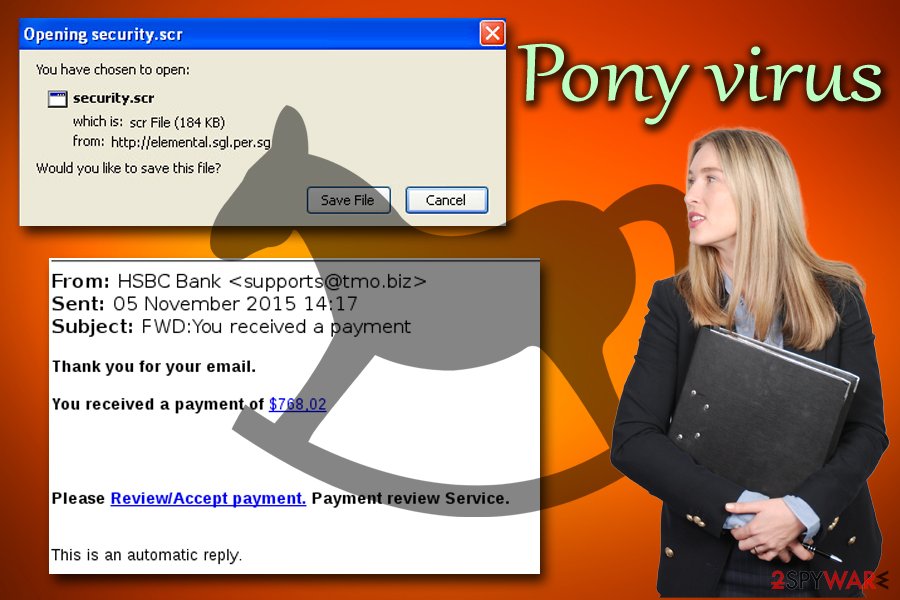
What is Pony virus?
Pony virus – a dangerous malware that can harvest personal data

Pony virus is a trojan that infiltrates computers using deceptive techniques, such as fake Adobe Flash updates,[1] The HoeflerText Font Wasn't Found scam, spam emails, or as a drive-by download.[2] As soon as the user initiates the code, it loads Pony Loader into Windows, which is the main executable of malware (it is automatically terminated after the execution). The malicious application has one goal – to steal sensitive information and send it to hacker's hands. While losing personal data to cybercrooks is quite devastating, dealing with additional malware downloaded by Pony virus can be frustrating, to say the least.
| SUMMARY | |
| Name | Pony virus |
| Type | Trojan |
| Main functionality | Steals personal data and sends it to hackers |
| Main dangers | Money loss and additional malware infections |
| Symptoms | Rarely any, although users might experience system or software crashes |
| Distribution | Fake Adobe Flash updates, spam emails, The HoeflerText Font Wasn't Found scam, etc. |
| Elimination | Use anti-spyware software like FortectIntego or Malwarebytes |
Pony virus was designed in order to steal personal passwords that are saved on more than a hundred apps and social media, games, banking and other accounts. As soon as the data is harvested, it is sent to Command & Control Server – a remote server that is only accessible to the attackers. This is precisely how ransomware infection behaves when it tries to send the generated key to criminals.
Similarly to ransomware, Pony virus has only one goal – to retrieve money from unsuspecting victims illegally. For example, stolen banking credentials can be used to access users' money directly. Additionally, any other personal data (such as name, address, email, Social Security number, driver's license number, etc.) can be sold on the Dark Web or used for identity theft. As you can see, the consequences can be catastrophic. To prevent malware from causing more harm, you should remove Pony virus ASAP.
Another terrifying trait of Pony virus is that it is connected to a botnet[3] which can make the targeted computer into malicious malware spreading tool. For example, the infamous Rustock botnet was capable of sending out 192 phishing emails per compromised PC per minute. And of course, the more people click on the contaminated attachment, the more infected machines distribute malware automatically.
Furthermore, Pony virus serves as a backdoor to other malware. It is not uncommon for trojans to distribute ransomware. For example, one of the most prominent botnets – Necrus – is delivering such treats as Locky or GlobeImposter. These malicious applications are capable of completely locking up personal files and demanding a ransom to be paid in Bitcoin or another crypto.
Pony virus is also capable stealing of digital wallets that contain cryptocurrency. According to reports,[4] the malware targets different currencies, such as Bitcoin, Litecoin, and others. Victims are known to suffer more than $220,000 in damages caused by Pony trojan.
If you suspect that you could be infected with the malware (for example, you recently opened a suspicious attachment in the spam email), make sure you scan your computer using FortectIntego, Malwarebytes or other reliable anti-malware software. This action will guarantee a prompt Pony virus removal.
Ways trojans can enter machines
Trojans can be attached to almost anything: free games, illegal programs, malicious browser plug-ins, and other questionable software. Such programs are a perfect distribution mechanism for viruses, so there is no surprise that hackers are usually using them for spreading their threats around.
How could you avoid malware? First of all, make sure you don't download any executables (they might be disguised under different extensions, such as .pdf, .html, .scr, etc.) from spam emails. Clicking links inside questionable messages would result in the infection as well. Therefore, make sure the email you are viewing is legitimate and comes from the person it is supposed to be.
When downloading and installing programs, it is advised to do a small research about them and check how your desired program is reviewed online. You should look for comments and similar reviews that could let you know about the trustworthiness of the application. Also, make sure you avoid fraudulent websites that might be filled with misleading/illegal/malicious content.
For users who are using digital currencies, security experts[5] strongly advice to store them in safe and encrypted e-wallets. In this case, the best solution would be choosing an offline storing device that guarantees better protection.
Finally, install powerful anti-spyware that is capable of preventing infiltration of such threats like this one. If you think that the virus has already infiltrated your computer and now is trying to steal your money, you should follow the guidelines below and check the system for this virus.
Ways to remove Pony virus
Pony virus removal should be your top priority, as it can cause more damage as the time goes on (e.g., additional malware infiltration). Therefore, download and install reputable security software an perform a full system scan. We recommend using FortectIntego or Malwarebytes, as these security applications are capable of detecting malware and eliminating all its tracers on the computer.
Security experts do not recommend trying to remove Pony virus manually. Such action can lead to severe damage to system files and will ultimately fail to get rid of the malicious application entirely. Only trained IT professionals are capable of such action.
Getting rid of Pony virus. Follow these steps
Manual removal using Safe Mode
To disable the Pony virus safely, enter Safe Mode with networking:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Pony using System Restore
You can also use System Restore for malware elimination:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Pony. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Pony and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting trojans
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Val S. Fake Adobe Flash Update Installs Ransomware, Performs Click Fraud. Symantec. Cybersecurity researchers.
- ^ Drive-by download. Wikipedia. The Free Encyclopedia.
- ^ Chris Hoffman. What Is a Botnet?. How-to Geek. Site that explains technology.
- ^ FastFlux. Pony stealer takes $220k worth of Cryptocurrency. ZeroSecurity. Tech and cybersecurity news.
- ^ Virusai. Virusai. Lithuanian security experts.





















