R00t ransomware (Free Guide) - Virus Removal Instructions
R00t virus Removal Guide
What is R00t ransomware?
R00t ransomware – a malicious threat that resides from the Paradise ransomware family
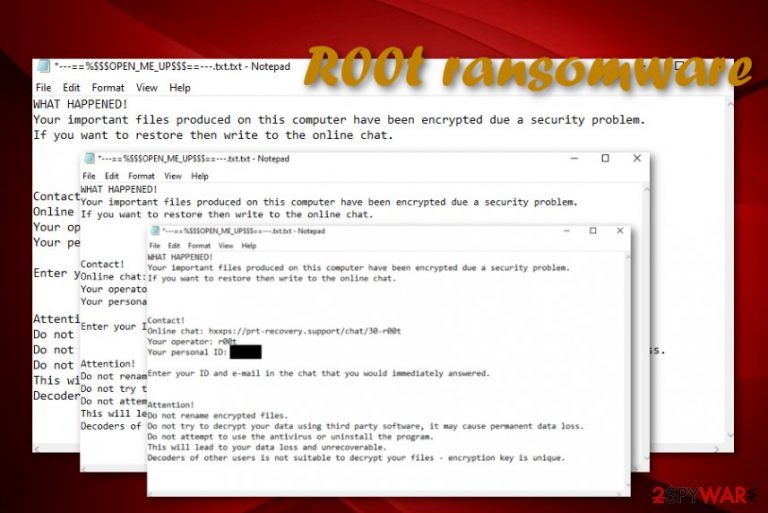
R00t ransomware is considered to be a very dangerous malware form that aims to encrypt all data that is found on the infected Windows computer system. Belonging to Paradise ransomware, this parasite uses unique ciphers to encrypt each file and document. Afterward, the ._r00t_{random string}.njkwe appendix is attached to each filename and the —==%$$$OPEN_ME_UP$$$==—.txt ransom note is dropped on the computer's desktop. The rogue message claims that all files have been encrypted due to some security problems and the only way to restore them is to include yourself in some type of online chat. The criminals provide the direct link to the chat and encourage users to enter their IDs and emails there. R00t ransomware will try to scare you to convince you to purchase a decryption tool from the hackers. Even though there are no particular details stated about the ransom price, it is very likely to be an inadequate one that can come up to $2000 or more.
| Name | R00t ransomware |
|---|---|
| Type | Ransomware virus/malware |
| Appendix | The dangerous malware locks all files and documents that are found on the targeted computer system by using a unique cipher. Afterward, the ransomware adds the ._r00t_{random string}.njkwe appendix to each filename |
| Ransom note | The criminals provide all required details in the —==%$$$OPEN_ME_UP$$$==—.txt ransom note. These people urge to get involved in some type of online chat and claim that this is the only way to restore locked data |
| Ransom price | Even though there are no particular details about the ransom demands, the price can vary anywhere between $50 and $200 or more. The crooks are also very likely to urge for some type of cryptocurrency (mostly Bitcoin) as these types of transfers grant anonymity |
| Processes | Once the ransomware virus ends up on the Windows computer, it can start running bogus processes in the Windows Task Manager section, inject questionable entries into the Windows Registry, etc. This way the malware is able to scan the system for encryptable components, enable itself within each startup process, disable some antimalware protection, delete Shadow Copies, damage the hosts file, and many more |
| Danger level | Very high. This cyber threat holds a highly-increased danger level as it locks all files and documents that are found on the infected Windows computer, can cause severe damage, and install additional malware |
| Family | This malware string is known to come from the Paradise ransomware family |
| Removal | If you have been looking for ways to eliminate the parasite, we suggest using only antimalware products as this type of software will ensure that the entire process will be completed safely and successfully |
| Fix | If you have spotted some damage on your Windows computer system, you can try fixing it with FortectIntego |
R00t ransomware is a dangerous cyber threat that can bring damage to your Windows computer and files. Even though the main purpose of this infection is to lock up files and demand money for their release, there can be other things that the malware is capable of. For example, infiltrating other computer viruses.
R00t virus makes your computer vulnerable to other infections and can bring various malicious material to the system. It might clear the path for trojans, spyware, worms, and other parasites. This way you might experience serious system damage, private data exposure, monetary losses, software struggles, overheating CPU,[1] etc.
According to VirusTotal,[2] R00t ransomware has been spotted by 23 AV engines out of the total 71. In some cases, ransomware viruses can launch specific modules that allow them to evade antimalware detection. This way the infection can appear on the computer unnoticed and stay silent for a while.
However, you will definitely spot that something is odd when you see encrypted documents on your desktop. R00t ransomware targets any types of images, audios, videos, databases, excel sheets, and other files. It leaves them with a rogue appendix and the user is no longer capable of accessing the components properly.
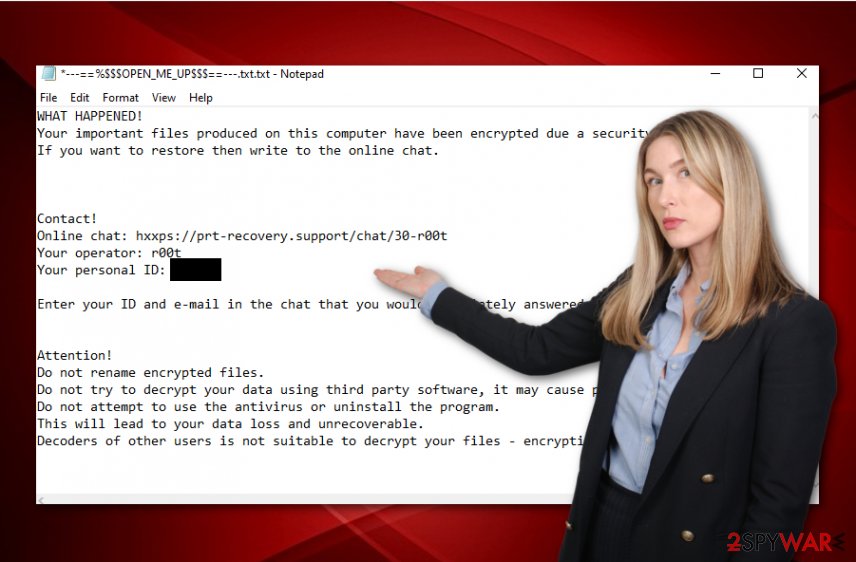
Afterward, R00t ransomware demands that the victims include themselves in online chatting and discuss all the details about the ransom. In addition to that, the criminals provide various threats like not to use antimalware software, not to decrypt data by using third-party tools as it will result in permanent data loss:
WHAT HAPPENED!
Your important files produced on this computer have been encrypted due a security problem.
If you want to restore then write to the online chat.Contact!
Online chat: hxxps://prt-recovery.support/chat/30-r00t
Your operator: r00t
Your personal ID: pJFM2qEnter your ID and e-mail in the chat that you would immediately answered.
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Do not attempt to use the antivirus or uninstall the program.
This will lead to your data loss and unrecoverable.
Decoders of other users is not suitable to decrypt your files – encryption key is unique.
We want to assure you that R00t ransomware developers are keen on only their own benefits and do not care about your well-being. Following their commands does not necessarily mean that you would be provided with decryption software and everything will be okay. This people are very likely to scam gullible victims.
Rather than paying inadequate amounts of money and getting lured in other scams, you should perform the R00t ransomware removal by using automatical software. Afterward, you can try some other data recovery software that might be helpful. Find the equipment and their descriptions at the end of this article.
There are plenty of reasons to remove R00t ransomware from your machine. First, you will not be able to restore data without eliminating the parasite. Second, it can bring other infections to your computer. Third, you can experience various system damage. If any corruption has occurred, try fixing it with FortectIntego.
Nevertheless, R00t ransomware might be capable of various other activities. Due to its complex module, encrypting files might only be one thing that the malware is able to do. In order to support this process and make it easier, the parasite can:
- Damage the Windows hosts file and prevent users from accessing security-related forums.
- Delete the Shadow Volume Copies[3] of encrypted data and decrease the users' chances of recovering their files.
- Enable itself within every Windows computer startup process.
- Scan the system for encryptable data in repeated time intervals.
- Inject other bogus processes and entries into the Task Manager and Registry.
Distribution tactics of ransomware infections
Security experts from NoVirus.uk[4] state that ransomware viruses are most commonly distributed through email spam. The criminals drop messages that are pretended to be from reputable healthcare, banking, or shipping organizations such as FedEx, DHL and encourage users to open some type of clipped attachment or inserted hyperlink.
Our recommendation would be to always carefully look through your emails, especially those that fall in the “Spam” section. If you were not expecting anything important to receive at the moment, you should better delete all the bogus emails as a reputable company would manage to contact you via mobile phone later.
Also, always try to identify the sender, check if the message is coming from a normally-looking address. Continuously, do not open any attached files that look suspicious to you or without scanning them with antivirus software.
In addition, ransomware infections can get delivered through cracked software that comes from piracy networks such as The Pirate Bay, BitTorrent, eMule, and others. If you are looking for a program or service to download, better select original sources or get the product/service straight from the official developer.
Last but not least, it is important not to click on every ad and hyperlink that you see. Do not fall for suspicious software upgrades that might approach you while browsing. Always make sure that your antivirus is turned and properly updated. This way you will have automatical protection and be notified when something malicious tries to invade your PC.
R00t ransomware removal guidelines (automatical)
R00t ransomware can be removed only by employing automatical software, otherwise, you might not succeed in the process. This malware is a complex one and needs proper elimination. If you do not clean your entire Windows computer system from malicious and bogus content, the ransomware virus can easily return.
If you are still having a hard time to take care of the R00t ransomware removal, there might be some malicious processes stopping you from deleting this cyber threat. What you can do is diminish various malicious activities by applying Safe Mode with Networking or System Restore when restarting your Windows computer.
Now, remove R00t ransomware properly by launching your AV tool. After the program finishes its job, it is time to search for possible damage with software such as SpyHunter 5Combo Cleaner or Malwarebytes. If these programs spot any compromised components on your computer system, you can try repairing them with a system repair tool such as FortectIntego.
Getting rid of R00t virus. Follow these steps
Manual removal using Safe Mode
To disable malicious changes on your Windows computer, apply the following guiding steps and boot your machine in Safe Mode with Networking.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove R00t using System Restore
To deactivate the malware, you should opt for the System Restore feature. You can accomplish such a task by completing the below-provided guidelines.
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of R00t. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove R00t from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by R00t, you can use several methods to restore them:
Employ Data Recovery Pro for file restoring.
Use this software if you have been looking for equipment that might help you to bring some valuable files back to their primary positions.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by R00t ransomware;
- Restore them.
Use Windows Previous Versions feature and recover some data.
Employ this type of software if you are looking for a way to recover lost items. However, you should have booted your Windows machine in System Restore if you want this method to work properly.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Using Shadow Explorer might help with data recovery.
If the ransomware virus did not touch the Shadow Volume Copies of your encrypted data, you should give this method a try as it might unlock some files of yours.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Currently, the cybersecurity specialists are working on the decryption tool.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from R00t and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Central Processing Unit (CPU). Techopedia. Tech terms and definitions.
- ^ 23 engines detected this file. Virus Total. File information.
- ^ Shadow Copy. Wikipedia. The free encyclopedia.
- ^ NoVirus. NoVirus. Spyware news.







