R980 ransomware / virus (Free Guide)
R980 virus Removal Guide
What is R980 ransomware virus?
R980 ransomware – what is it for and how does it work?
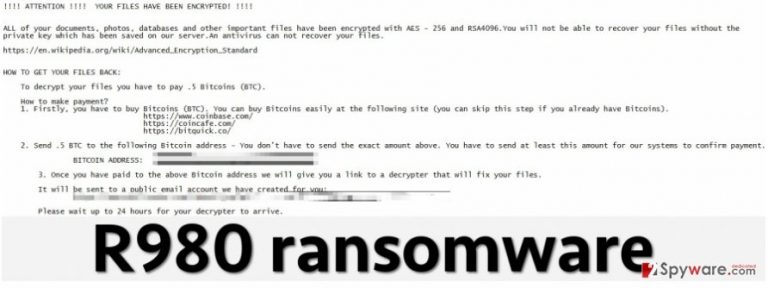
R980 virus is a specific malware variant, which uses an asymmetric encryption algorithm to render victim’s files useless. This computer threat scans the entire computer system, goes through every single folder except system folders and corrupts all data that it is programmed to find. Victims who have their computers affected by this virus report that it encrypts videos, music, documents, presentations, images, and other file types, and scrambles their filenames, renaming them with a random set of characters. However, there were some reports stating that this virus did not encrypt the data, which means that this malicious piece of software has been created with several bugs and might still be under development at the moment. After a successful infection, this virus creates a ransom note and saves it as a .txt file on the computer desktop, and also changes desktop wallpaper with an image that includes the same information that the ransom note provides.
The letter from authors of this ransomware is a traditional ransom note. It contains information about the infection, what encryption algorithms were used (in this case – both AES-256 and RSA-4096), how to recover the files and what is the price of the ransom. R980 malware warns the user that an antivirus program can not retrieve the data, which, unfortunately, is true. However, a strong anti-malware application can prevent this virus from encrypting your files, so it is highly advisable to install one on the computer system. This virus demands half of a Bitcoin for the decryption key, which is approximately 328 USD. The ransom has to be sent to a provided Bitcoin address, and this payment method is used in order to protect cybercriminals from being detected. Then the victim has to wait up to 24 hours until R980 decrypter arrives.
If you have become a victim of R980 ransomware, we heartily recommend you not to pay the ransom. That is the only way to stop cyber criminals who create these viruses every single day. The list of ransomware examples includes Locky, CryptoWall, CryptXXX, Petya, and hundreds of similar viruses. It hurts to lose your precious files, but sometimes malware researchers succeed to defeat these viruses and come up with free decryption tools. Meanwhile, it is recommended to remove R980 virus with a help of a malware-removal tool. You can use FortectIntego for that.
How did this virus enter my computer system?
Typically, ransomware distribution methods don’t change. Crooks tend to distribute them via malvertising, drive-by downloads, and mostly malicious email campaigns. These threats are often concealed as safe-looking files and sent directly to victims via email, or added to bogus software updates and advertised via shady Internet sites. It is important to understand that criminals do everything to deceive computer users, so it is important to stay cautious at all times and always think before clicking on a flashy ad or a “download” button, as this can lead to sad consequences. We advise you to download software or updates ONLY from verified and secure Internet sites, never open emails that are sent by unknown individuals, and install a reliable anti-malware software to keep your computer protected. You should also keep all your programs up-to-date to prevent frauds from exploiting security vulnerabilities in them.
How to remove R980 ransomware?
R980 virus is a hard-to-defeat computer program, so we greatly advise you to allow an advanced virus removal program to scan your computer system and automatically detect malignant components of it. It is not a regular computer program, and its developers have done everything to make it harder to remove. This threat might also try to stop you from running your malware removal program, so in such case, follow instructions that are given below:
Getting rid of R980 virus. Follow these steps
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove R980 using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of R980. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from R980 and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.







