Remcos / Virus Removal Guide - Improved Instructions
Remcos Removal Guide
What is Remcos?
Remcos RAT is a dangerous info-stealing trojan that abuses the Coronavirus as a theme for the malicious spam attacks
Remcos or Remote Control and Surveillance[1] are promoted as a customizable remote administration tool by its developer Breaking Security. However, in 2016 cybersecurity researchers detected this tool being sold in hacking forums[2] in various anonymous digital currencies by an Italian malware developer known as Viotto. Since then up till now, Remcos trojan is regularly reported for the active distribution via aggressive malspam campaigns.
It's an extremely dangerous cyber infection, which falls for the Remote Access Trojan (RAT) category. In general, it's task is to infiltrate a Windows PC with high-level administrative privileges and gain access to user's credentials, such as passwords, logins, and banking information. For this purpose, it runs filename1.vbs and filename1.exe scripts and starts taking screenshots, logging keystrokes both offline and in realtime, as well as recording information transmitted via a microphone or camera. It keeps harvested data in a file named logs.dat within %AppData%\Local\Temp\onedriv directory, which is regularly transmitted to the remote C2 server.
| Summary of the RAT | |
| Name | Remcos |
| First emerged | Experts first detected it in 2016 sold on the hack forums. New campaigns emerge up till now |
| The actor behind the malware | Experts have revealed the hacker with a pseudonym Viotto as the main developer and seller of this remote access tool who is infamous for Viotto keylogger, Octopus Crypter, Poseidon Mailer, Viotto Binder, and other malware development |
| Type of malware | Remote Access Trojan (RAT), keylogger, spyware, a banking trojan |
| Distribution | The trojan is actively distributed via aggressive malspam campaigns that leverage diverse themes based on what's trending worldwide. The latest campaign spotted in March 2020 takes advantage of the Coronavirus pandemic and tricks people into opening malicious CoronaVirusSafetyMeasures_pdf attachment |
| Goal | The virus seeks to gain full control over the system in order to steal the user's credentials and send them to remote control servers for a hacker |
| Behavior | Bypasses anti-virus programs, maintains persistence, takes control over legitimate Windows processes, gains high-level administrative privileges, disables User Account Control, self-destructs when sufficient information is harvested |
| Related directories | HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce C:\Users\\Subfolder %AppData%\Local\Temp\onedriv |
| Countries targeted | Japanese, Turkey, U.S., Germany, South Corea, and others. The main target – business and organizations |
| Removal | Remcos removal requires a professional anti-virus tool. The trojan is capable of bypassing AV engines and can turn the software useless by overruling its processes. Therefore, before running a scan, restart the system into Safe Mode |
| Damage | Despite the fact that the RAT targets sensitive information, it can also severely compromise system integrity and security. Typically, it rewrites registry entries and legitimate processes, which are not automatically restored upon virus removal. Therefore, a full system's repair is subsequently needed. For this purpose, use tools like FortectIntego. |
Remcos RAT is not a novel cyber infection. Currently, experts mark a significant increase in the activity of suchlike security threats since in 2020 alone aggressive campaigns of Cerberus, Agent Tesla, Emotet, Trickbot, etc. have been revealed.
Banking trojans such as the Remcos virus utilize social engineering techniques when criminals leverage trending topics. Legitimate-looking email messages with malicious email attachments are typically spread by bots en masses or oriented to a particular target.
Multiple malspam campaigns promoting Remcos dropper has been spotted on the landscape since 2016. Three years ago Fortinet warned[3] users about obfuscated Microsoft Office documents under filenames Quotation.xls or Quotation.doc, which once opened bypass Microsoft UAC security and runs the malware with high privileges. However, the criminals behind the RAT put effort to attack companies for bigger financial benefits. An attack registered in 2018 was oriented to defense contractors in Turkey, international news agencies, Diesel equipment manufacturers, HVAC service providers, and other sectors.
Despite the target, Remcos trojan RAT seeks to gain full control over the system to leak as much personally identifiable information as possible. The malicious email attachment carrying a RAT dropper runs XTM code, which executes the malware without any warning or notifications enabling criminals to perform malicious activities. Immediate Remcos removal is needed to prevent the following:
- Banking information stolen
- Logins, passwords stolen
- Detailed system logs leaked
- Digital coins stolen
- Backdoor to other cyber infections opened
Knowing the dangers and capabilities of Remcos, users should take precautionary measures to secure themselves. Since the malware spreads via malicious emails that carry PDF, XSL, DOC, etc. that ask for user's permission to enable Macros, users have to be extremely cautious and avoid opening any content that they are not expecting.
The attachments are archives that ask for a grant to enable supposed Macros function, which is, in fact, a connection with the attacker's command and control (C&C) server. With this permission, Remcos trojan gains permission and starts its malicious keylogging and data-stealing activities.
It's difficult to recognize the trojan since it's developed in a way to remain unrecognized for as long as possible. It decontaminates the anti-virus system and compromises legitimate Windows system files, thus preparing itself a clear patch to take screenshots, log keystrokes, copy printed documents, register passwords, and initiate other tasks that step-by-step push the potential victim into the money loss.
When it comes to Remcos removal, there is only one way out – a full system scan with a comprehensive anti-virus system. Excessive CPU consumption, slow system performance, doubtful error messages, and similar symptoms may exhibit a trojan infection, so we strongly recommend people to restart the system into Safe Mode and run a full scan.
The latest Remcos campaign leverages Coronavirus pandemic theme
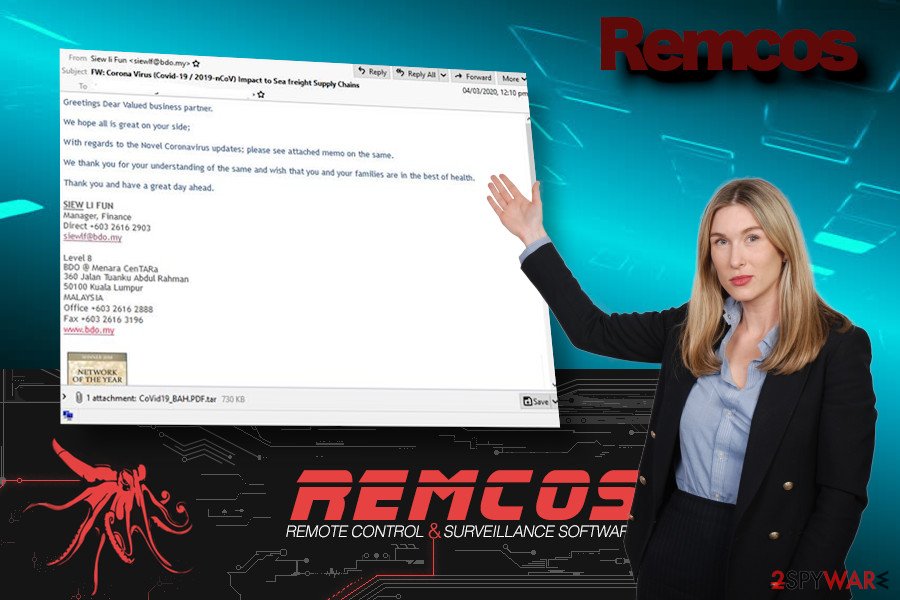
The trojan reappears on the landscape annually with a new malspam campaign taking advantage of the trending worldwide topics and problems. Coronavirus or Covid-19 infodemic is one of the main topics that criminals use nowadays and that's for a reason since millions of people all over the world are trying to keep the pace with the latest pandemic-related news.
Yoroi Security company[4] was the first that spotted the new Remcos campaign targeting Japanese users at the end of 2019. According to experts, the social engineering technique used by criminals attempts to convince people to open a CoronaVirusSafetyMeasures_pdf file, which is a rogue PDF supposedly outlining the measures that have to be taken to protect themselves from the virus.
However, the file contains a Remcos RAT dropper, which establishes a TSL connection with the C&C server, downloads a malicious file, which enables filename1.vbs and files in C:\Users\\Subfolder. Besides, it creates a Windows startup entry HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce, which enables the trojan to run upon the system's restart. All the gathered information allows criminals to harvest system-related, user-related, and process-related information, which may subsequently be used for identity theft and money loss.
However, Japanese users are not the only target. Microsoft's researchers detected[5] the whole series of COVID-19 themed spam emails that spread Remcos dropper in the disguise of ISO, IMG, or ZIP file attachments. The initial inspection reveals that the attack is targeting US small businesses looking for loans impersonating fake SBA emails or the American Institute of CPA.
Although such attacks are common, experts claim that usage of ISO files as attachments or trojan droppers are not very common, as well as the main purpose of the current attacks. However, cybersecurity experts presume that Remcos trojan may be used as a backdoor for future attacks compromising business and causing big losses.
Infected emails trick users into granting access to malicious trojans
Cybercriminals have been persistent and keep launching multiple spam campaigns to trick gullible PC users into launching viruses on the systems. Spam is a widely used social engineering technique that allows attackers to impersonate trustful sources, such as FedEx, SBA, RedCross, or even U.S. president Trump.
Remcos trojan developers keep rearranging their attacks though the principle remains the same. The attackers insert a malicious trojan dropper into the rogue PDF, ISO, ZIP or EXE attachments and present them in a tricky way. The following are the most notable examples:
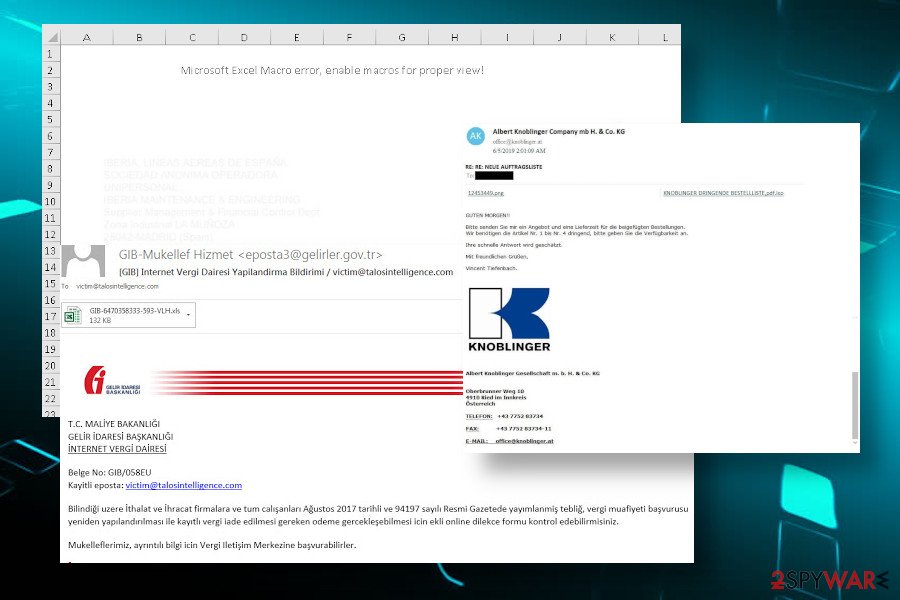
- The infected Microsoft office attachments named as Quotation.xls or Quotation.doc have been sent to millions of users in 2017. The potential victim is not allowed to “read” the document as long as Macros is not enabled. At the top of the screen, the victim sees a notification “Security warning: Macros has been disabled” with an options button aside, which once clicked launched the virus.
- In 2018, defense contractors and other businesses in Turkey have been actively attacked, Talos reported[6]. Crafted in the Turkish language, the emails imitated Turkish governmental institutions reporting taxes.
Thank you for your participation in the e-mail notification system of [the] Department of Revenue Administration's e-mail service. This message has been sent to you by GIB Mail Notification System. Please do not reply to this message.
- CheckPoint noted[7] a flow of attacks in 2019 targeting Germany companies across all industries. The emails contained obfuscated invoices or urgent orders named like KNOBLINGER DRINGENDE BESTELLLISTE,pdf.ISO.
- The latest Remcos campaign took a start at the end of 2019 and keeps evolving in 2020. The attackers misuse the COVID-19 pandemic theme as a topic of malicious emails. Currently, the most visible trojan dropper is CoronaVirusSafetyMeasures_pdf attachment.
The ZLab-Yoroi Cybaze researchers claim people should protect themselves by carefully evaluating the trustfulness of the emails received even from the well-known companies and organizations.
Maintain a high attention level when receiving or treating communications claiming to be related to the CoronaVirus phenomenon, to avoid panic clicking on the link coming from unattended source and to contact trusted experts in case of the doubts.
Weak protection of the Windows system allows uninterrupted trojan access. Unfortunately, even though the system runs a powerful AV engine, criminals have programmed this malware in a way to decontaminate security tools and infiltrate without any warnings. Therefore, the only way to stay safe is to restrain from opening questionable emails before scanning them for viruses.
Eliminate Remcos to protect your credentials and the system from subsequent attacks
Trojans, in general, are the most stealthy cyber infections, which with a slight help of PC users manage to infiltrate systems without being noticed and can operate silently for a long period. Beware that the longer period Remcos virus manages to persist, the more chances its developers have to initiate big information theft and give backdoor commands. It can continuously transmit user profile, names, domain, keystrokes, print screens, and computer/processor related information to C&C servers thus causing a high risk of identity theft and money loss.
Remcos removal is important to prevent the installation of other viruses, such as ransomware. Trojans or RAT, for example, LokiBot, often carry the second payload of ransomware. Consequently, not only leakage of credentials, but also loss of personal data stored on the system can be lost.
The only way to remove Remcos is to launch the scanner of the anti-virus program. In many cases, trojans block security programs. To bypass malicious processes, the system has to run in Safe Mode. How to switch to this mode you can find out by following the steps listed below. Besides, experts from dieviren.de[8] actively promote the community to perform the system's recovery with a tool like FortectIntego upon Remcos removal to restore compromised Windows OS components.
How to prevent from getting remote administration tools
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Remcos Professional. Breaking Security. CyberSecurity technology and services.
- ^ Catalin Cimpanu. New Remcos RAT Available for Purchase on Underground Hacking Forums. Softpedia. Daly news on cybersecurity and technologies.
- ^ THREAT RESEARCH. Fortinet. Cyberthreat research.
- ^ New Cyber Attack Campaign Leverages the COVID-19 Infodemic. Yoroi. Cyber security experts.
- ^ Catalin Cimpanu. Microsoft warns of multiple malspam campaigns carrying malicious disk image files. ZDnet. Business technology news.
- ^ Picking Apart Remcos Botnet-In-A-Box. Cisco Talos. The biggest threats each week and other security news.
- ^ Kobi Eisenkraft, Moshe Hayun. Check Point’s Threat Emulation Stops Large-Scale Phishing Campaign in Germany. Check Point. Cyber security solutions.
- ^ SICHERHEIT- UND SPYWARE-NEUIGKEITEN. Dieviren. Virus and spyware news.
